漏洞作者:
详细说明:
/interface/order.php
$ptitle,$tsn都可控,直接带入insert。
正常提交
来看看accept()
这里会把提交的数据转义,但是当$tsn不是数组的时候是这样的
$temp = "wooyun"
$temp[0]的值为w
playload构造:
$tsn参数提交一个' daddslashes(espcms重写的addslashes)将其转义成/'
取$tsn[0],为/
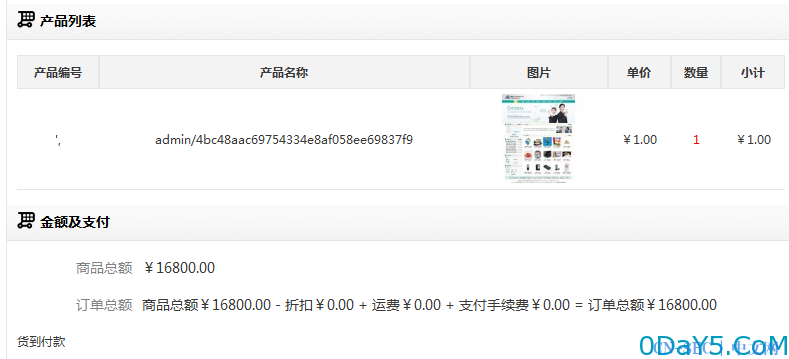
查看订单:
![易思ESPCMS sql注入漏洞(绕过阿里云盾demo站成功拿下shell)]()
sql语句相当于
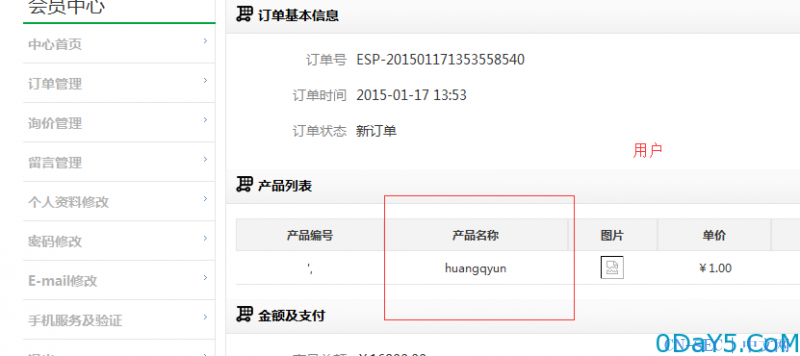
官方DEMO测试:
由于官方demo有阿里的防火墙,我就分两次来获取
![易思ESPCMS sql注入漏洞(绕过阿里云盾demo站成功拿下shell)]()




评论