在渗透检测中,经常需要搜集目标网站的域名信息,比如搜集二级域名、三级域名,以及一些注册信息等等,今天我在这里再造个粗糙的轮子,写篇关于获取二级域名的脚本文章,供参考。
后续会更新二级、三级域名的爆破,有什么好的思路请留言给我,谢谢!
=============分割线=============
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# @Author: IcySun
# 脚本功能:爆破网站的二级域名
from Queue import Queue
import threading,sys
import dns.resolver
def use():
print '#' * 50
print '\t python subDoman.py xxx.com'
print '\t\t\t Code By: IcySun'
print '#' * 50
def subDoman(domain):
try:
ns = dns.resolver.query(domain)
for i in ns.response.answer:
for j in i.items:
if j.to_text().count('.') == 3:
print domain + '\t\t' + j.to_text()
with open(dname + '.txt','a+') as name:
name.write(domain + '\t\t' + j.to_text() + '\n')
except Exception, e:
passclass MyThread(threading.Thread):
def __init__(self):
threading.Thread.__init__(self)
def run(self):
global queue
while not queue.empty():
domain = queue.get()
subDoman(domain)def main():
global domain,queue
queue = Queue()
dname = sys.argv[1]
namelist = open('subnames.txt','r')
for name in namelist.readlines():
domain = name.strip() + '.' + dname
queue.put(domain)for i in range(100):
c = MyThread()
c.start()if __name__ == '__main__':
if len(sys.argv) != 2:
use()
else:
main()
直接截图:
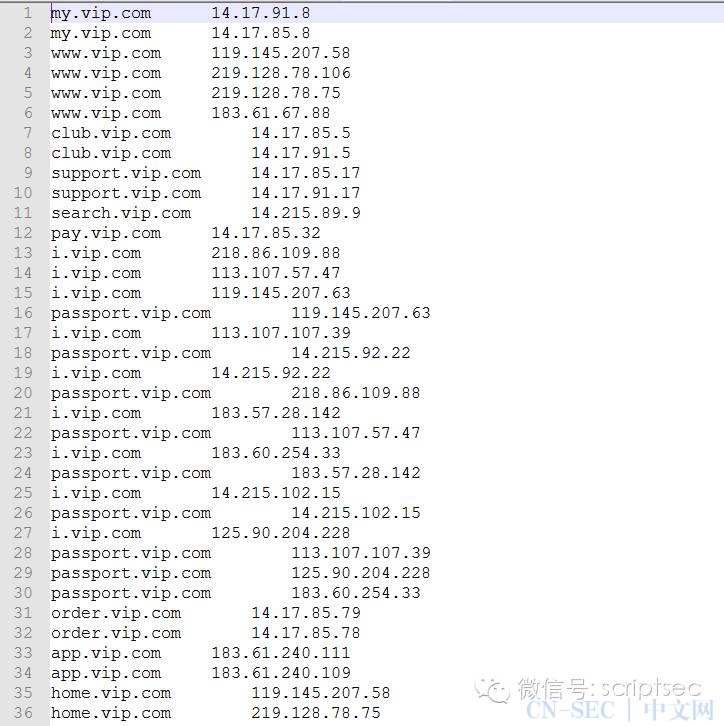
附上 oschina 的git地址:
http://git.oschina.net/icysun/subDomain/
参考:
1、字典:http://fuzz.wuyun.org/scanlist/Discovery/DNS/
2、比较优秀的轮子:https://github.com/lijiejie/subDomainsBrute
如果你感觉此脚本对你有所帮助,请扫描二维码赞助,谢谢!
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-








评论