漏洞文件/controllers/seller.php
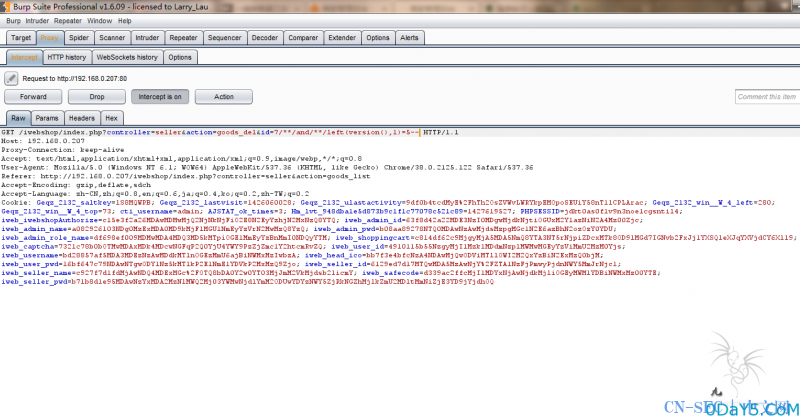
public function goods_del() { //post数据 $id = IFilter::act(IReq::get('id')); //生成goods对象 $goods = new goods_class(); $goods->seller_id = $this->seller['seller_id']; if($id) { if(is_array($id)) { foreach($id as $key => $val) { $goods->del($val); } } else { $goods->del($id); } } $this->redirect("goods_list"); }
还是一样的获取方式,跟入del看下
public function del($goods_id) { $goodsWhere = " id = {$goods_id} "; if($this->seller_id) { $goodsWhere .= " and seller_id = ".$this->seller_id; } //删除商品表 $tb_goods = new IModel('goods'); if(!$tb_goods ->del($goodsWhere)) { return; } }
继续跟入
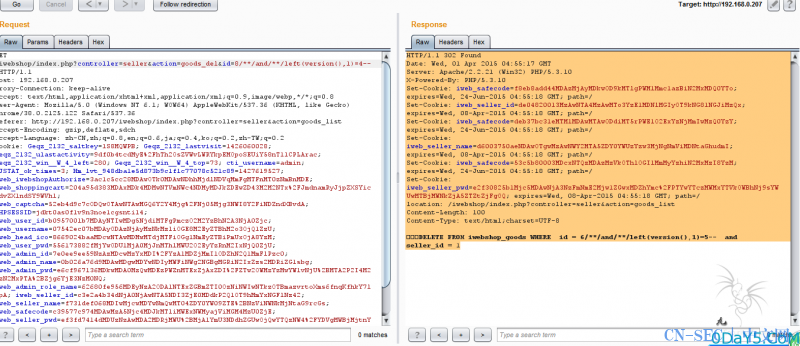
public function del($where) { $where = (strtolower($where) == 'all') ? '' : ' WHERE '.$where; $sql = 'DELETE FROM '.$this->tableName.$where; echo $sql; return $this->db->query($sql); }
payload还是一弹的那个商铺可以权限可以采用爆破的方式或者通过xss
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论