The vulnerability CVE-2023-32233 is described as a use-after-free issue in the Netfilter nf_tables in the Linux kernel up to version 6.3.1. This problem arises during the processing of batch requests, which can be exploited to perform arbitrary read and write operations on kernel memory. Unprivileged local users can exploit this vulnerability to gain root privileges, due to the mishandling of anonymous sets1.
To detect this vulnerability, one approach would be to check the kernel version and the status of the nf_tables. If the kernel version is up to 6.3.1 and nf_tables is in use, there's a potential for this vulnerability to exist.
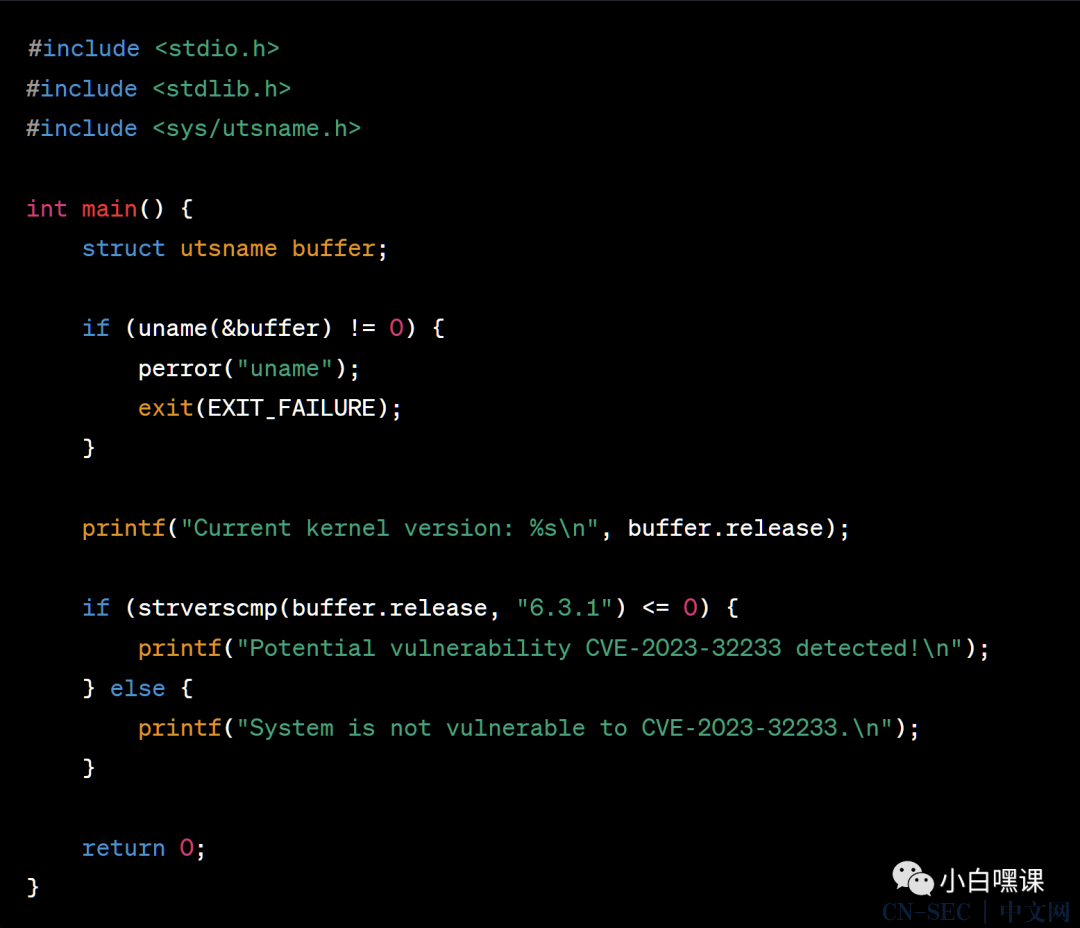
Here is a simple C program that checks the kernel version:
This program calls the uname function to get system information, including the kernel version. It then checks if the version is less than or equal to 6.3.1, in which case it reports a potential vulnerability.
Please note that this is a very rudimentary check and might not be accurate if the kernel has been patched. This program also does not check whether nf_tables is in use or not. For a more comprehensive check, you may want to use a vulnerability scanning tool which can accurately detect whether a system is vulnerable or not.
To compile and run this program, you can use the gcc compiler like so:
here are the Python and Go versions of the program to check the Linux kernel version.
Python version:
You can run this Python script by using the command: python check_vuln.py.
Go version:
You can run this Go script by first building the program with go build check_vuln.go and then running the output binary with ./check_vuln.
Again, please note that these scripts only check the kernel version and do not check if nf_tables is in use. Also, they might not be accurate if the kernel has been patched. For a more comprehensive check, you should use a vulnerability scanning tool.
原文始发于微信公众号(小白嘿课):CVE-2023-32233 Poc(C/Python/Go)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






评论