一
flutter的证书校验
起因:
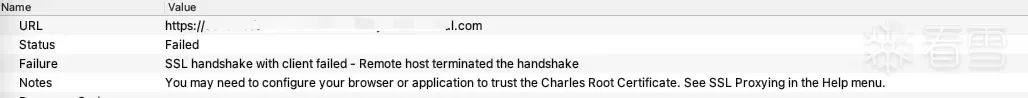


然后就开始各种找,https://bbs.kanxue.com/thread-261941.htm


adb install --abi armeabi-v7a <path to apk>



二
写脚本绕过
32位:
function hook_ssl_verify_result(address) {
Interceptor.attach(address, {
onEnter: function(args) {
console.log("Disabling SSL validation")
},
onLeave: function(retval) {
console.log("Retval: " + retval);
retval.replace(0x1);
}
});
}
function hookFlutter() {
var m = Process.findModuleByName("libflutter.so");
var pattern = "2D E9 F0 4F 85 B0 06 46 50 20 10 70";
var res = Memory.scan(m.base, m.size, pattern, {
onMatch: function(address, size){
console.log('[+] ssl_verify_result found at: ' + address.toString());
// Add 0x01 because it's a THUMB function
// Otherwise, we would get 'Error: unable to intercept function at 0x9906f8ac; please file a bug'
hook_ssl_verify_result(address.add(0x01));
},
onError: function(reason){
console.log('[!] There was an error scanning memory');
},
onComplete: function() {
console.log("All done")
}
});
}

64位
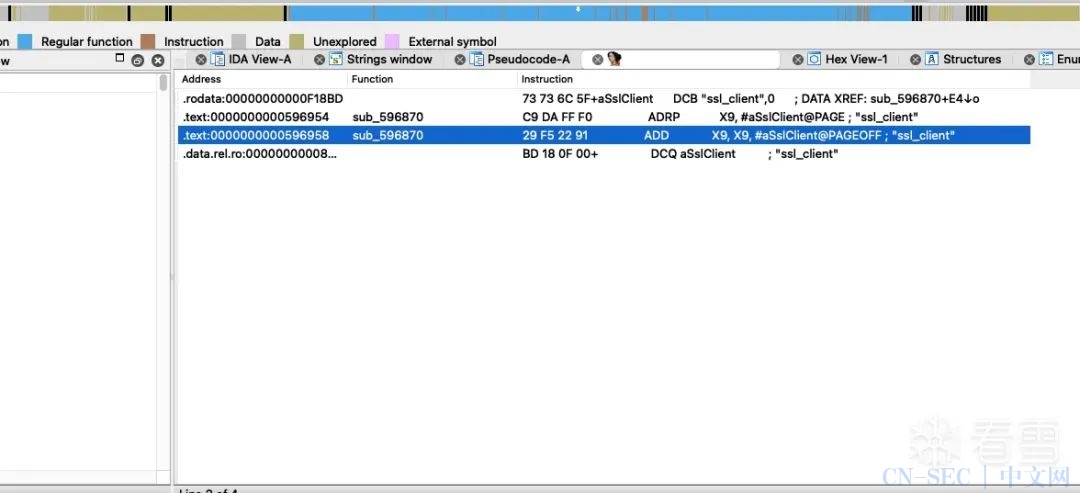


.text:0000000000596870 FF C3 01 D1 SUB SP, SP, #0x70
.text:0000000000596874 FD 7B 01 A9 STP X29, X30, [SP,#0x70+var_60]
.text:0000000000596878 FC 6F 02 A9 STP X28, X27, [SP,#0x70+var_50]
.text:000000000059687C FA 67 03 A9 STP X26, X25, [SP,#0x70+var_40]
.text:0000000000596880 F8 5F 04 A9 STP X24, X23, [SP,#0x70+var_30]
.text:0000000000596884 F6 57 05 A9 STP X22, X21, [SP,#0x70+var_20]
.text:0000000000596888 F4 4F 06 A9 STP X20, X19, [SP,#0x70+var_10]
.text:000000000059688C 08 0A 80 52 MOV W8, #0x50
.text:0000000000596890 48 00 00 39 STRB W8, [X2]
function hook_ssl_verify_result(address) {
Interceptor.attach(address, {
onEnter: function(args) {
console.log("Disabling SSL validation")
},
onLeave: function(retval) {
console.log("Retval: " + retval);
retval.replace(0x1);
}
});
}
function hookFlutter() {
var m = Process.findModuleByName("libflutter.so");
var pattern = "FF C3 01 D1 FD 7B 01 A9 FC 6F 02 A9FA 67 03 A9 F8 5F 04 A9 F6 57 05 A9 F4 4F 06 A9 08 0A 80 52 48 00 00 39";
var res = Memory.scan(m.base, m.size, pattern, {
onMatch: function(address, size){
console.log('[+] ssl_verify_result found at: ' + address.toString());
// Add 0x01 because it's a THUMB function
// Otherwise, we would get 'Error: unable to intercept function at 0x9906f8ac; please file a bug'
hook_ssl_verify_result(address.add(0x01));
},
onError: function(reason){
console.log('[!] There was an error scanning memory');
},
onComplete: function() {
console.log("All done")
}
});
}


三
参考资料
-https://mp.weixin.qq.com/s/pXpfXK-Ez0n70f3bqFuuFg
-https://bbs.kanxue.com/thread-261941.htm
-https://blog.nviso.eu/2019/08/13/intercepting-traffic-from-android-flutter-applications/
看雪ID:puppet_w
https://bbs.kanxue.com/user-home-929264.htm

#
原文始发于微信公众号(看雪学苑):Flutter抓包绕过
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论