Discover how cybercriminals behave in Dark Web forums- what services they buy and sell, what motivates them, and even how they scam each other.
了解黑暗网络论坛中网络犯罪分子的行为方式-他们购买和出售什么服务,是什么激励了他们,甚至是他们如何欺骗彼此。
Clear Web vs. Deep Web vs. Dark Web
明网 vs. 深网 vs. 暗网
Threat intelligence professionals divide the internet into three main components:
威胁情报专家将互联网分为三个主要组成部分:
-
Clear Web - Web assets that can be viewed through public search engines, including media, blogs, and other pages and sites.
明网 - 可通过公共搜索引擎查看的Web资产,包括媒体,博客和其他页面和站点。
-
Deep Web - Websites and forums that are unindexed by search engines. For example, webmail, online banking, corporate intranets, walled gardens, etc. Some of the hacker forums exist in the Deep Web, requiring credentials to enter.
深网 - 未被搜索引擎索引的网站和论坛。例如,网络邮件,网上银行,企业内部网络,墙围花园等。一些黑客论坛存在于深网中,需要凭据才能进入。
-
Dark Web - Web sources that require specific software to gain access. These sources are anonymous and closed, and include Telegram groups and invite-only forums. The Dark Web contains Tor, P2P, hacker forums, criminal marketplaces, etc.
暗网 - 需要特定软件才能访问的Web资源。这些来源是匿名和封闭的,包括Telegram群组和仅限邀请的论坛。暗网包含Tor,P2P,黑客论坛,犯罪市场等。
According to Etay Maor, Chief Security Strategist at Cato Networks, "We've been seeing a shift in how criminals communicate and conduct their business, moving from the top of the glacier to its lower parts. The lower parts allow more security."
根据Cato Networks的首席安全策略师Etay Maor的说法,“我们注意到犯罪分子在如何沟通和开展业务方面发生了变化,从冰山的顶部移动到了其底部。底部提供更多的安全性。”
Spotlight: What is Tor?
焦点:Tor是什么?
Tor is a free network, built upon open-source, that allows for anonymous communication. While Tor was originally developed by the United States Naval Research Laboratory, it has become an increasingly popular solution for illegal activities.
Tor是一个基于开源构建的免费网络,可以进行匿名通信。虽然最初是由美国海军研究实验室开发的,但它已成为越来越受欢迎的用于非法活动的解决方案。
Conducting these activities on the Clear Web can lead to law enforcement monitoring and allow tracing back to the criminal. But through Tor, communication is encrypted across three layers that are peeled off at every node jump until exiting the network. Law enforcement agencies monitoring Tor will not see the criminal's IP, but the Tor exit node, making it harder to trace back to the original criminal.
在明网上进行这些活动可能导致执法部门监控并追踪到犯罪分子。但通过Tor,通信被加密,通过三层跳转每个节点,直到退出网络。监视Tor的执法机构将看不到犯罪分子的IP,而是Tor退出节点,使追溯到原始犯罪分子变得更困难。
Tor communication architecture:
Tor通信架构:
Etay Maor adds "In the 2000s, a celestial alignment of digital capabilities boosted criminal efforts. First, the Dark Web emerged. Then, hidden and secure services through Tor. Finally, cryptocurrency allowed for secure transactions."
Etay Maor补充说“在2000年代,数字能力的天体对鼓励犯罪活动产生了推动作用。首先,暗网出现了。然后,通过Tor提供了隐藏和安全服务。最后,加密货币允许进行安全交易。”
Criminal Services Available on the Dark Web
暗网上提供的犯罪服务
Here are a few examples of services that were available on the dark web in the past. Today, many of these have been taken down. Instead, criminals are moving towards the Telegram messaging platform, due to its privacy and security features.
以下是过去在暗网上提供的几种服务的示例。如今,这些服务中的许多已被取缔。取而代之的是,犯罪分子开始转向 Telegram 消息平台,因为它具有隐私和安全功能。
Example include -
示例包括:
Drug selling:
毒品销售:
Fake identity services:
虚假身份服务:
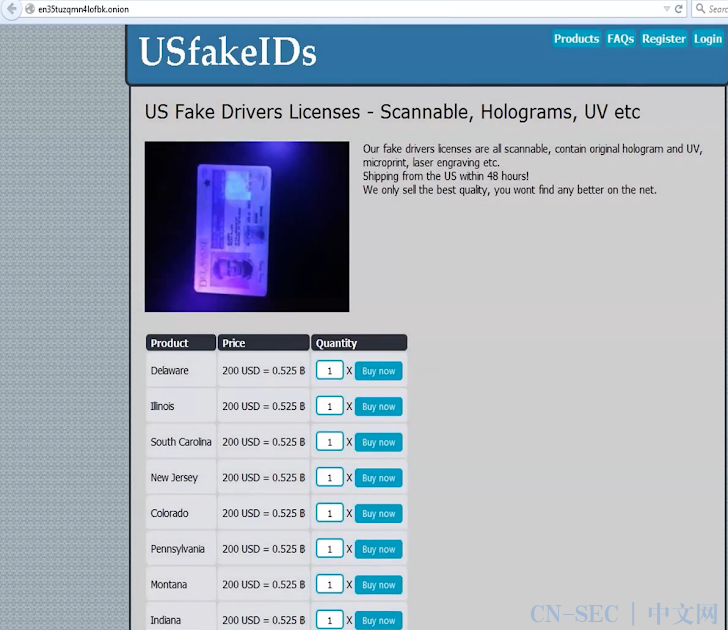
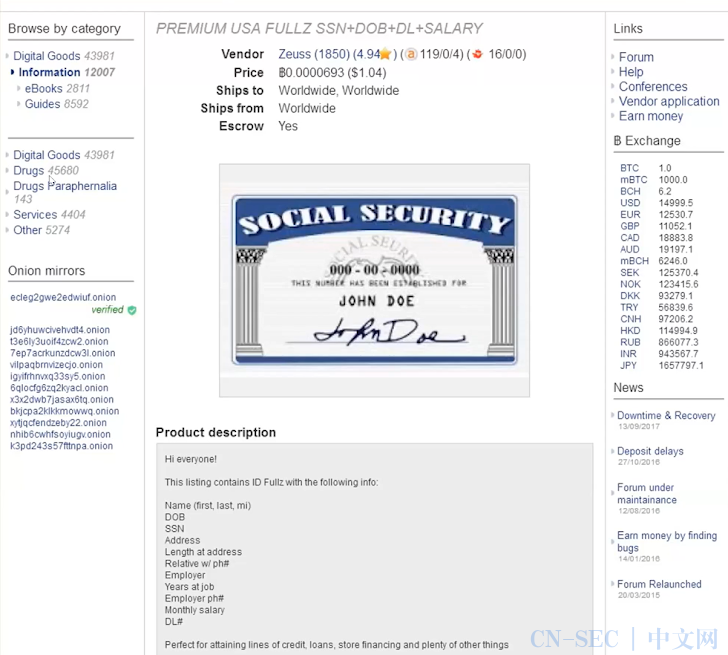
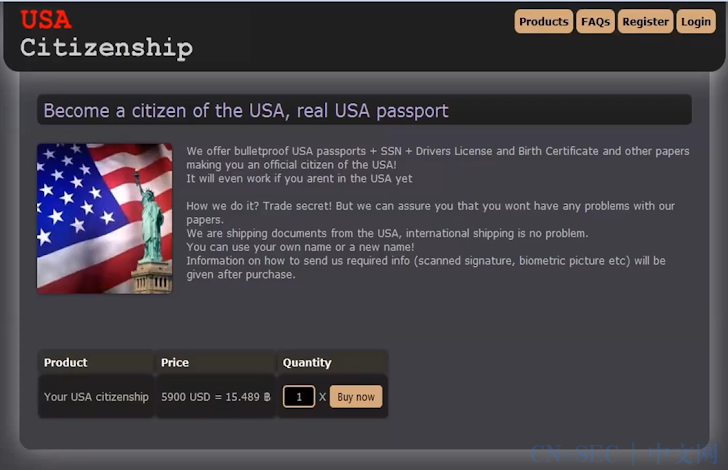
Marketplace for vendor search, including a warning about phishing attempts:
供应商搜索的市场,包括有关网络钓鱼尝试的警告:
How are Criminal Forums Managed? Creating Trust in an Untrusted Environment
犯罪论坛是如何管理的?在不受信任的环境中建立信任
Attackers attempt to exploit vulnerabilities and break into systems as a way to turn a profit. Just like any other commercial ecosystem, they use online forums to buy and sell hacking services. However, these forums need to create trust among members, while they themselves are built on crime.
攻击者试图利用漏洞并侵入系统,以此谋取利益。就像任何其他商业生态系统一样,他们使用在线论坛来购买和出售黑客服务。然而,这些论坛需要在成员之间建立信任,而它们本身却是建立在犯罪之上的。
Generally speaking, such forums were initially designed as follows:
一般来说,这些论坛最初设计如下:
-
Admin - Moderates the forum
管理员 - 负责管理论坛
-
Escrow - Facilitating payments among members
第三方担保 - 在会员之间方便支付
-
Black-list - An arbitrator for settling issues like payments and service quality
黑名单 - 作为解决支付和服务质量等问题的仲裁者
-
Forum Support - Various forms of assistance to encourage community engagement
论坛支持 - 各种形式的帮助以鼓励社区参与
-
Moderators - Group leads for different topics
版主 - 不同主题的小组负责人
-
Verified Vendors - Vendors that were vouched for, unlike some vendors who are scammers
验证供应商 - 获得背书的供应商,不像一些供应商是骗子
-
Regular Forum Members - The members of the group. They were verified before being allowed to enter the forum to filter out scammers, law enforcement agencies and other irrelevant or risky members.
常规论坛成员 - 小组的成员。在允许进入论坛之前,他们经过验证,以过滤出骗子,执法机构和其他不相关或有风险的成员。
The Path from Malware Infection To Corporate Data Leak in the Dark Web
从恶意软件感染到企业数据泄漏的路径在暗网中是如何体现的
Let's see how the different stages of attack are represented in the Dark Web, through an example of malware used to steal information for ransomware purposes:
让我们通过一个用于窃取信息以实施勒索软件的恶意软件示例,来看看暗网上攻击的不同阶段是如何表现的:
Pre-incident phases:
事前阶段:
1. Data Collection - Threat actors run worldwide infostealer malware campaigns and steal logs of compromised credentials and device fingerprints.
1. 数据收集 - 威胁行为者进行全球信息窃取恶意软件活动,窃取受损凭证和设备指纹的日志。
2. Data Suppliers - Threat actors supply data to Dark Web markets specializing in credentials and device fingerprinting from malware-infected computers.
2. 数据供应商 - 威胁行为者向专门从恶意软件感染的计算机中获取凭证和设备指纹的暗网市场供应数据。
3. Fresh Supply - The logs become available for purchase in the Dark Web market. The price of a log typically ranges from a few dollars to $20.
3. 新供应 - 这些日志可以在暗网市场上购买。日志的价格通常从几美元到20美元不等。
Active incident phases:
主动事件阶段:
4. Purchase - A threat actor specializing in initial network access purchases the logs and infiltrates the network to elevate access. Many times the information purchased includes more than credentials. It includes cookie sessions, device fingerprinting and more. This allows mimicking the victim's behavior to circumvent security mechanisms like MFA, making the attacks harder to detect.
4. 购买 - 专门从初始网络访问购买日志的威胁行为者购买日志并渗透网络以提升访问权限。许多时候,购买的信息包括不仅是凭证,还包括cookie会话,设备指纹等。这允许模仿受害者的行为以规避MFA等安全机制,使攻击更难被检测。
5. Auction - The access is auctioned in a Dark Web forum and purchased by a skilled threat group.
拍卖 - 访问权限在暗网论坛上被拍卖,并被一个技术娴熟的威胁团体购买。
Etay Maor notes, "Auctions can be run as a competition or as "Flash", meaning a threat actor can purchase immediately without the competition. Serious threat groups, especially if they are backed by nation states or are large criminal gangs, can use this option to invest in their business."
Etay Maor指出,“拍卖可以作为竞争或“闪光”运行,意味着威胁行为者可以立即购买而无需竞争。严重的威胁组织,特别是如果它们得到国家支持或是大型犯罪团伙,可以使用此选项投资其业务。”
6. Extortion - The group executes the attack, placing ransomware in the organization and extorting it.
6. 敲诈 - 该组织执行攻击,在组织中放置勒索软件并勒索。
This path highlights the various areas of expertise within the criminal ecosystem. As a result, a multi-layered approach fueled by operationalizing threat data can alert and possibly prevent future incidents.
这一路径突出了犯罪生态系统内的各种专业领域。因此,由操作化威胁数据推动的多层次方法可以警示并可能预防未来事件。
The Role of HUMINT
HUMINT的作用
Automated solutions are indispensable for fighting cyber crime, but to fully understand this realm, human intelligence (HUMINT) is required as well. These are cyber crime officers, the actors from the law enforcement agencies who log into forums and act like trade actors. Engagement is an art, and also has to be an ART - Actionable, Reliable and Timely.
自动化解决方案对于打击网络犯罪是不可或缺的,但要全面了解这一领域,还需要人类情报(HUMINT)。这些是网络犯罪侦查员,即执法机构的人员,他们登录论坛并假扮成交易者。接触是一门艺术,而且必须是ART:可操作的(Actionable)、可靠的(Reliable)和及时的(Timely)。
Let's see some examples of the forums tracked by cyber crime officers and how they respond.
让我们看看一些由网络犯罪侦查员跟踪的论坛示例,以及他们是如何应对的。
In this example, an attacker is selling VPN logins:
在这个例子中,攻击者正在出售VPN登录:
The cyber-criminal officer will try to engage and understand which VPN or client this belongs to.
网络犯罪官员将试图参与并了解这属于哪个VPN或客户端。
In another example, an attacker is selling Citrix access to an IT infrastructure Solutions and Services Provider in the UK.
在另一个例子中,攻击者正在出售Citrix访问权给英国的IT基础设施解决方案和服务提供商。
A cyber crime officer might reach out as a potential buyer and ask for samples. Since the seller is acting from an economic point of view, and might not be in a good financial situation (coming from former-USSR countries), they will be willing to send samples to promote a sale.
网络犯罪官员可能会以潜在的买家身份联系并要求样品。由于卖家是从经济角度出发行事的,并且可能不处于良好的经济状况(来自前苏联国家),他们将愿意发送样品以促进销售。
Protecting Against Network Attacks
防范网络攻击
The Dark Web operates as an economic ecosystem, with buyers, sellers, supply and demand. Therefore, effective protection against network attacks requires a multi-layered approach for each stage of the attack, both pre-incident and throughout the incident itself. Such an approach includes the use of automated tools as well as HUMINT - the art of engaging with cyber criminals online to gather intelligence by mimicking the way they operate.
暗网作为一个经济生态系统运作,有买家,卖家,供应和需求。因此,对网络攻击的有效保护需要针对攻击的每个阶段采取多层次方法,包括事前阶段和事件本身。这种方法包括使用自动化工具以及HUMINT - 通过模仿他们的操作方式与网络犯罪分子在线交流以收集情报的艺术。
参考资料
[1]https://thehackernews.com/2024/07/humint-diving-deep-into-dark-web.html
关注我们
欢迎来到我们的公众号!我们专注于全球网络安全和精选双语资讯,为您带来最新的资讯和深入的分析。在这里,您可以了解世界各地的网络安全事件,同时通过我们的双语新闻,获取更多的行业知识。感谢您选择关注我们,我们将继续努力,为您带来有价值的内容。
原文始发于微信公众号(知机安全):HUMINT:深入暗网
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-















评论