一,
BR reg

.text:000000000008D1E8 BL sub_8D1F8
.text:000000000008D1EC MOV X1, X0
.text:000000000008D1F0 ADD X1, X1, #0x38 ; '8'
.text:000000000008D1F4 BR X1

.text:000000000008D1FC STP X29, X30, [SP]
.text:000000000008D200 LDR X0, [SP,#8]

def antiBR1(start,end):
addr = start
while addr < end :
insn = idc.print_insn_mnem(addr)
op0 = idc.print_operand(addr,0)
op1 = idc.print_operand(addr,1)
# .text:000000000008B03C BL loc_8B04C
# .text:000000000008B040 MOV X1, X0
# .text:000000000008B044 ADD X1, X1, #0x38 ; '8'
# .text:000000000008B048 BR X1
# match 4 instructions
if insn == "BL" and (idc.print_insn_mnem(addr + 0xc).find("BR") != -1 or idc.print_insn_mnem(addr + 0x8).find("BR") != -1):
# find add
addr1 =addr
while 1:
str = get_instruction_at_address(addr1)
if str != None:
if str.find("ADD") != -1:
break
addr1 = addr1 + 4
opeValue = idc.get_operand_value(addr1,2)
print("find add: %x" % opeValue)
# patch addr B (addr +4 + opeValue)
code,count =ks.asm("B "+ hex(addr + 4 + opeValue),addr)
print(hex(addr))
ida_bytes.patch_bytes(addr, bytes(code))
addr = addr + 4

二
花指令

.text:000000000008D53C loc_8D53C ; CODE XREF: sub_8D170:loc_8D530↑j
.text:000000000008D53C MRS X1, NZCV
.text:000000000008D540 MOV X0, XZR
.text:000000000008D544 CMP X0, XZR
.text:000000000008D548 MSR NZCV, X0
.text:000000000008D54C B.NE loc_8D558
.text:000000000008D550 CLREX
.text:000000000008D554 BRK #3
.text:000000000008D558
.text:000000000008D558 loc_8D558 ; CODE XREF: sub_8D170+3DC↑j
.text:000000000008D558 MSR NZCV, X1




.text:000000000013DCE4 000 MOV X30, X17
.text:000000000013DCE8 000 SUB SP, SP, #0x50 ; 'P'
.text:000000000013DCEC 050 STP X29, X17, [SP,#0x50+var_10]
.text:000000000013DCF0 050 ADD X29, SP, #0x50+var_10
.text:000000000013DCF4 050 STUR X0, [X29,#-0x10]
.text:000000000013DCF8 050 STUR X1, [X29,#-0x18]
.text:000000000013DCFC 050 STR X0, [SP,#0x50+var_30]
.text:000000000013DD94 050 LDR X9, [SP,#0x50+var_30]
.text:000000000013DD98 050 LDR X10, [SP,#0x50+var_38]
.text:000000000013DD9C 050 STR X9, [X10,#8]

三
OLLVM

标准控制流平坦化
if(temp){
print("ok");
return 1
}
else{
print("no");
return 2
}
var flowState = 0;
while(1)
{
switch(flowState):
case 0:
if(temp){
flowState = 1
}
else{
flowState = 2
}
break
case 1:
print("ok");
flowState = 3
case 2:
print("no");
flowState = 4
case 3:
return 1
case 4:
return 0
}
1.计算支配节点
0
|
1
/
2 3
/ /
4 5 6
1: 1
2:0,1
3: 0,1
4:0,1,2
5:0,1,2,3
6:0,1,3
2.路径计算
0125
0135
0
flowState = 0
|
1
/
2 3
flowState = 1 flowState=2
/ /
4 5 6
| | |
1 1 1
状态指向计算
修改控制流
死代码消除
活跃变量分析
反混淆

计算支配节点
路径状态计算
状态指向计算
1 => 2
2 => 3
3 => 4
4 -> 5
修改控制流

死代码消除
活跃变量分析


1.计算支配节点
2.路径计算
3.路径状态计算
状态指向计算



修改控制流。
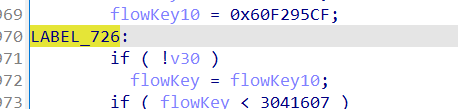

flowState2 =876832131267
flowState1 =312321312
if(..)
flowState = flowState1
else
flowState = flowState2
...
flowState2 =434876867
flowState1 =366512321312
if(..)
flowState = flowState1
else
flowState = flowState2
flowState2 =876832131267
flowState1 =312321312
goto lable_1
...
flowState2 =434876867
flowState1 =366512321312
lable_1:
if(..)
flowState = flowState1
else
flowState = flowState2

死代码消除
活跃变量分析
结果

对这2个感兴趣的可以看看这个 http://profs.sci.univr.it/~giaco/download/Watermarking-Obfuscation/unflatten.pdf
声明
看雪ID:method
https://bbs.kanxue.com/user-home-856431.htm
#
原文始发于微信公众号(看雪学苑):ARM64 目前主流的反混淆技术的初窥
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论